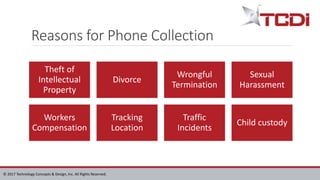
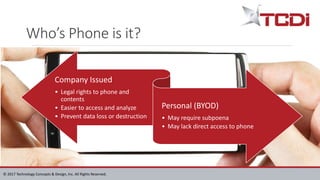
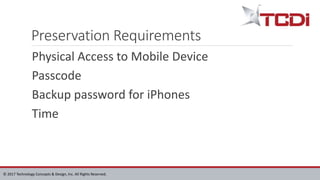
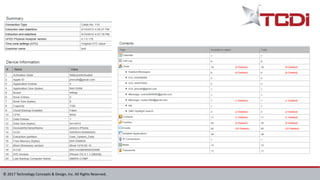
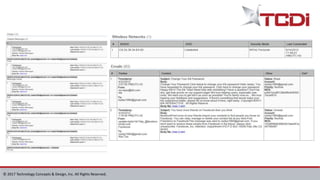
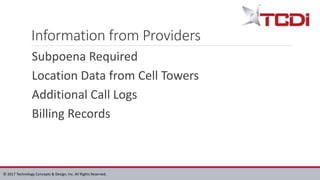
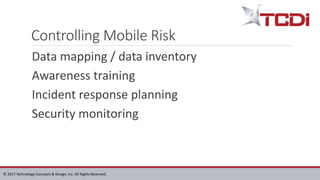
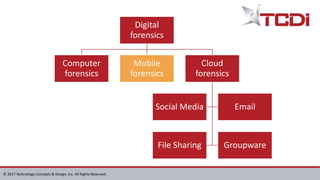
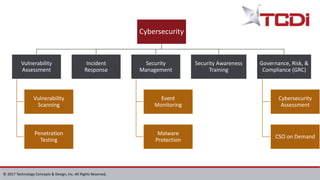
Technology Concepts & Design, Inc. (TCDI) specializes in digital forensics, cybersecurity, and e-discovery, providing services since 1988 with a focus on mobile forensics. The document outlines various aspects of mobile forensics, including reasons for phone collection, analysis considerations, and security risks associated with mobile devices in enterprises. TCDI highlights the importance of risk management, digital forensics processes, and the necessity of maintaining security compliance to protect sensitive corporate and customer data.