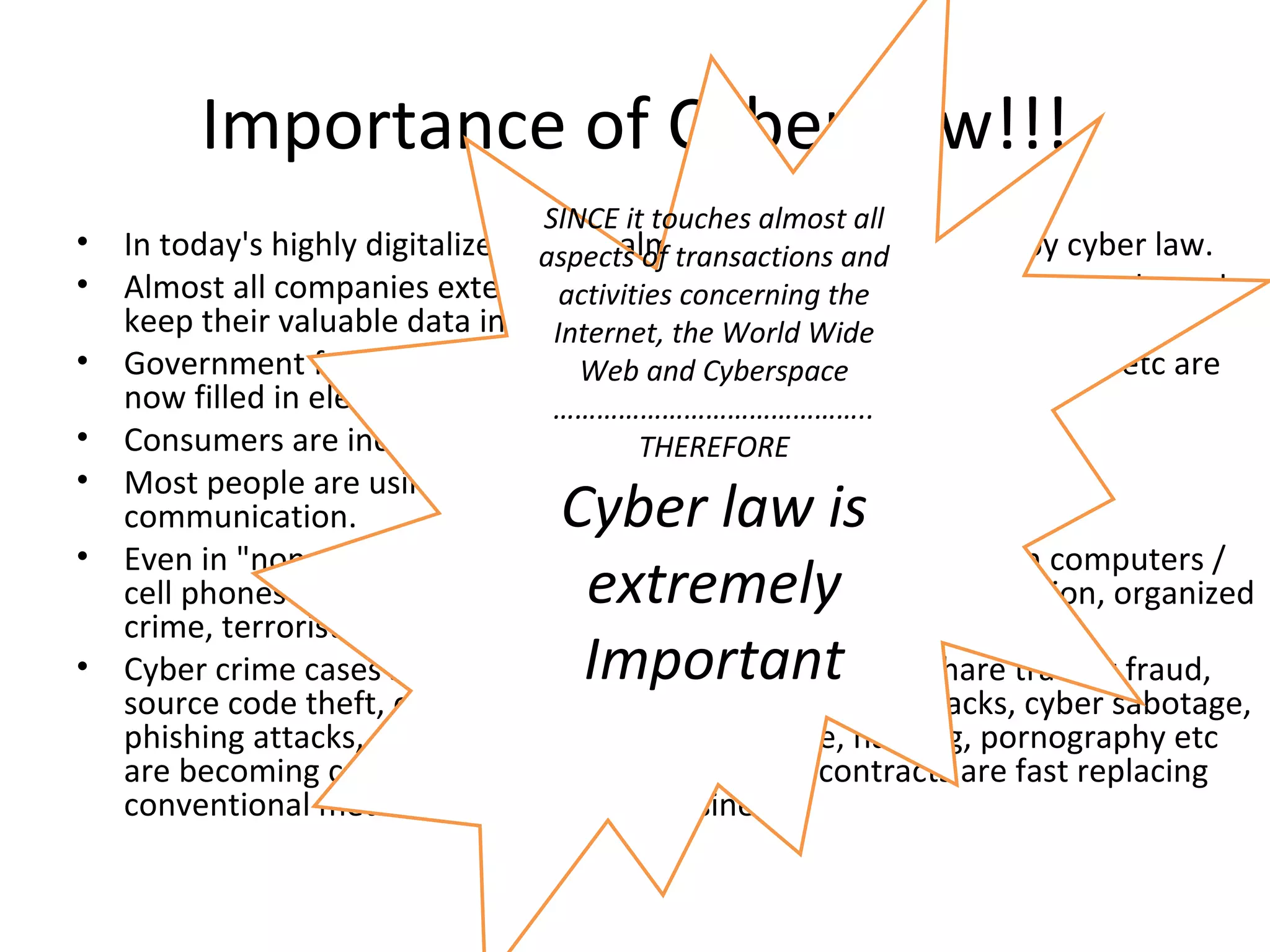
Cyber law is needed to regulate criminal and immoral behavior in cyberspace. Existing laws were developed before the internet and do not adequately address modern issues. A supportive legal infrastructure with relevant cyber laws is required to enable e-commerce and regulate new types of cyber crimes that have emerged with technology. Cyber law is important because it impacts almost all digital transactions and online activities in today's highly connected world.