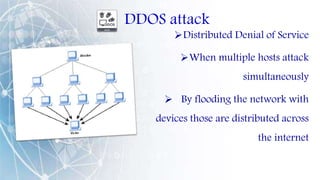
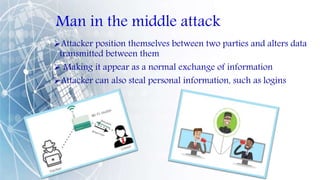
This document provides an overview of cyber security. It defines cyber security as protecting networks, devices, programs and data from damage, unauthorized access or attacks delivered over the internet. It discusses the importance of cyber security for protecting data from theft or misuse and safeguarding systems from viruses. Various cyber attacks are outlined such as malware attacks, phishing, password attacks, hacking, and denial of service attacks. Common security mistakes like poor password management and opening unknown email attachments are also summarized. The document concludes by emphasizing that awareness is key to staying safe and secure from cyber threats.