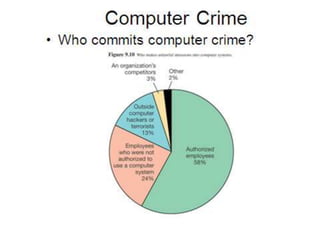
Cyber laws and cyber crimes are discussed. Cyber law refers to legal issues related to communications technology and the internet. The Information Technology Act was passed in 2000 in India to recognize electronic transactions and facilitate electronic filing. Cyber crimes include hacking, data theft, spreading viruses, identity theft, and email spoofing. The IT Act and Indian Penal Code sections apply to cyber crimes and outline punishments such as imprisonment and fines. Cyber laws are needed to tackle cyber crimes and protect intellectual property rights in today's internet-reliant world.