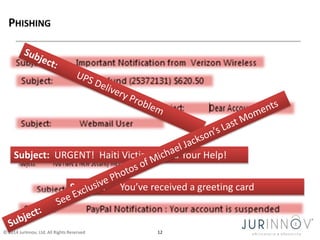
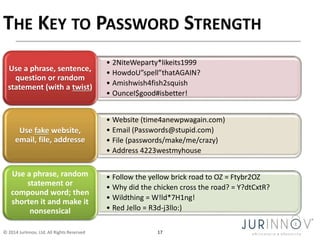
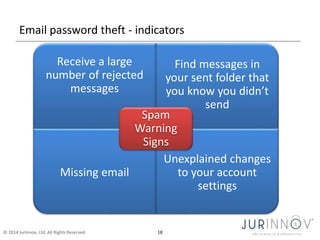
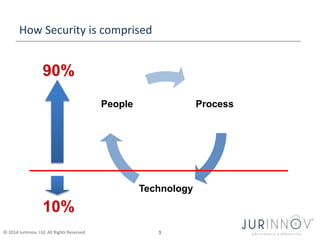
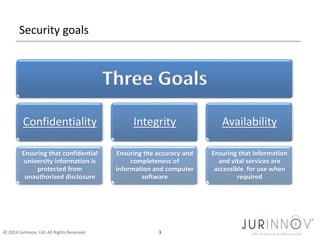
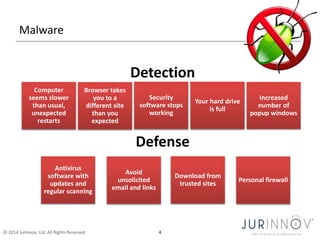
The document discusses the importance of security awareness, emphasizing the roles of process, technology, and people in maintaining security. It highlights key security goals such as confidentiality, integrity, and availability, while also addressing issues like phishing, identity theft, and password protection. Recommendations include proper data handling, vigilant online behavior, and employing security measures to protect sensitive information.



![Remove the opportunity
• Location of office equipment
– Printers & fax machines
• Lock it down
– Office doors
– File cabinets, sensitive documents, personal items
– Computers
• Windows OS: Ctrl-Alt-Delete [enter] or Windows L
• Macs: Shift (⇧) + Command (⌘) + Q
• Password-protected screensaver or Time-out
• Don’t leave the computer unattended when logged into an account with
sensitive data (i.e., payroll, email, personal info)
– Phones
© 2014 JurInnov, Ltd. All Rights Reserved 6](https://image.slidesharecdn.com/securityawareness-untangledchurchtechnologyconference-nov2014-141109132144-conversion-gate01/85/Untangled-Conference-November-8-2014-Security-Awareness-7-320.jpg)