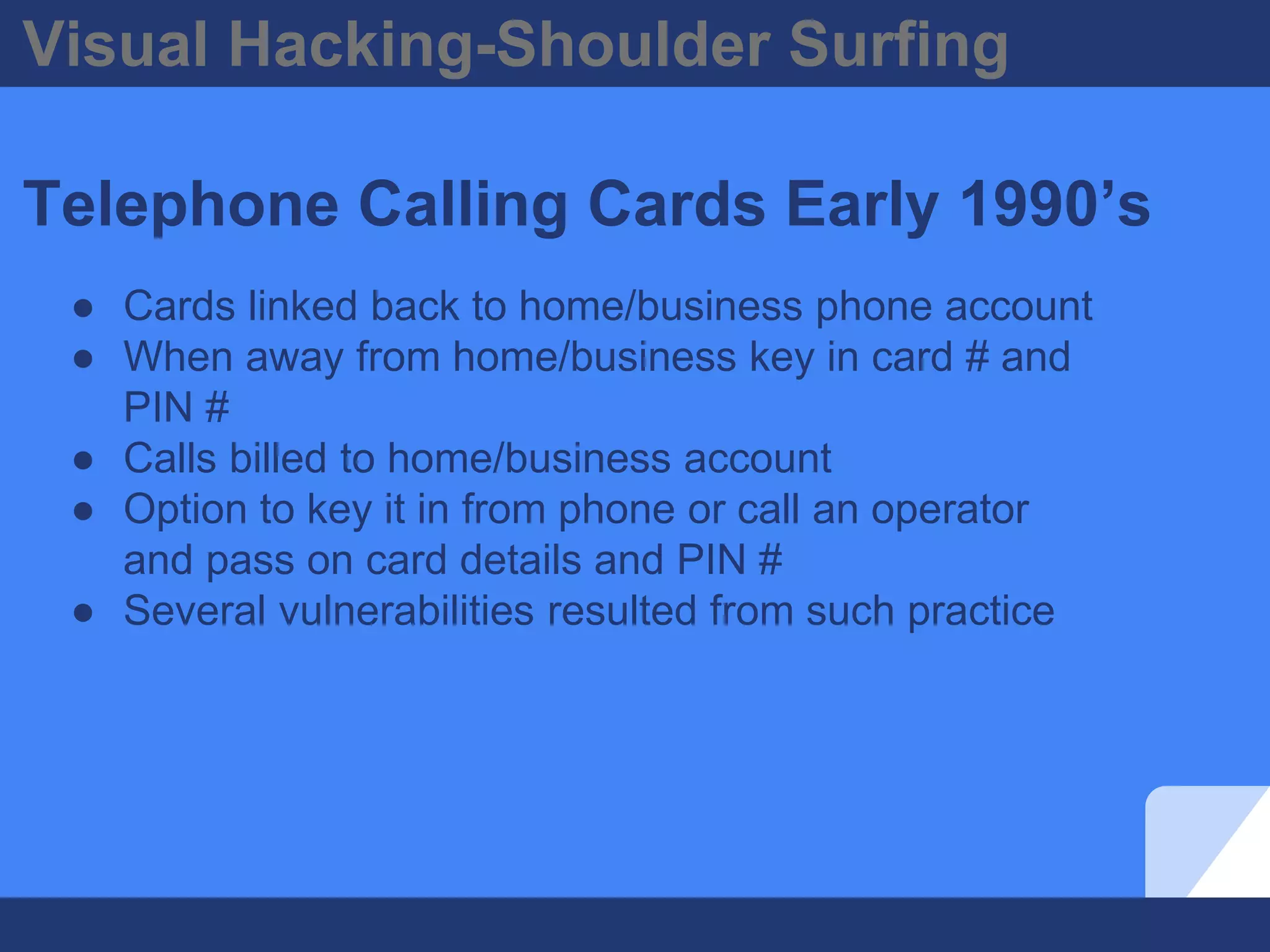
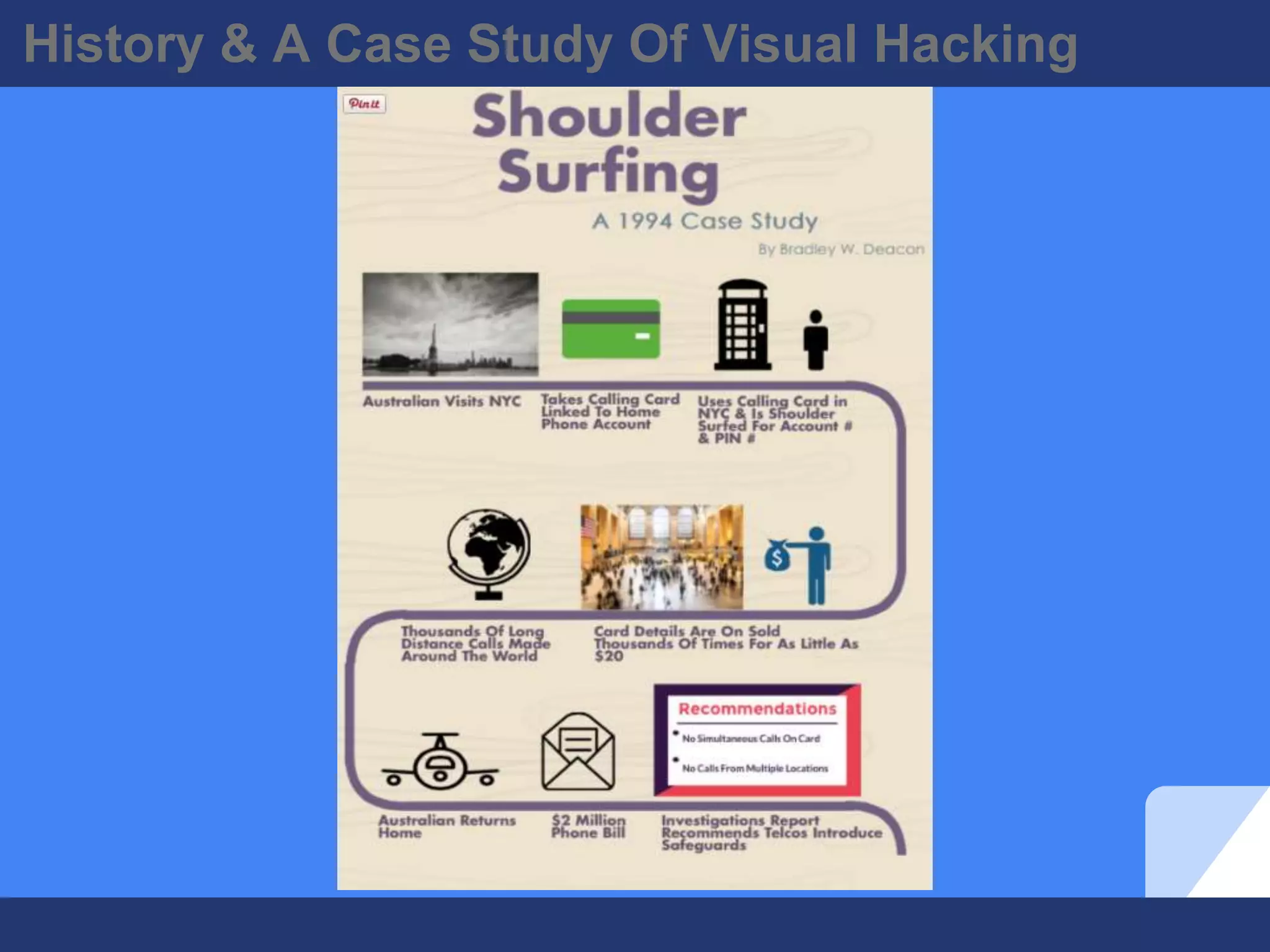
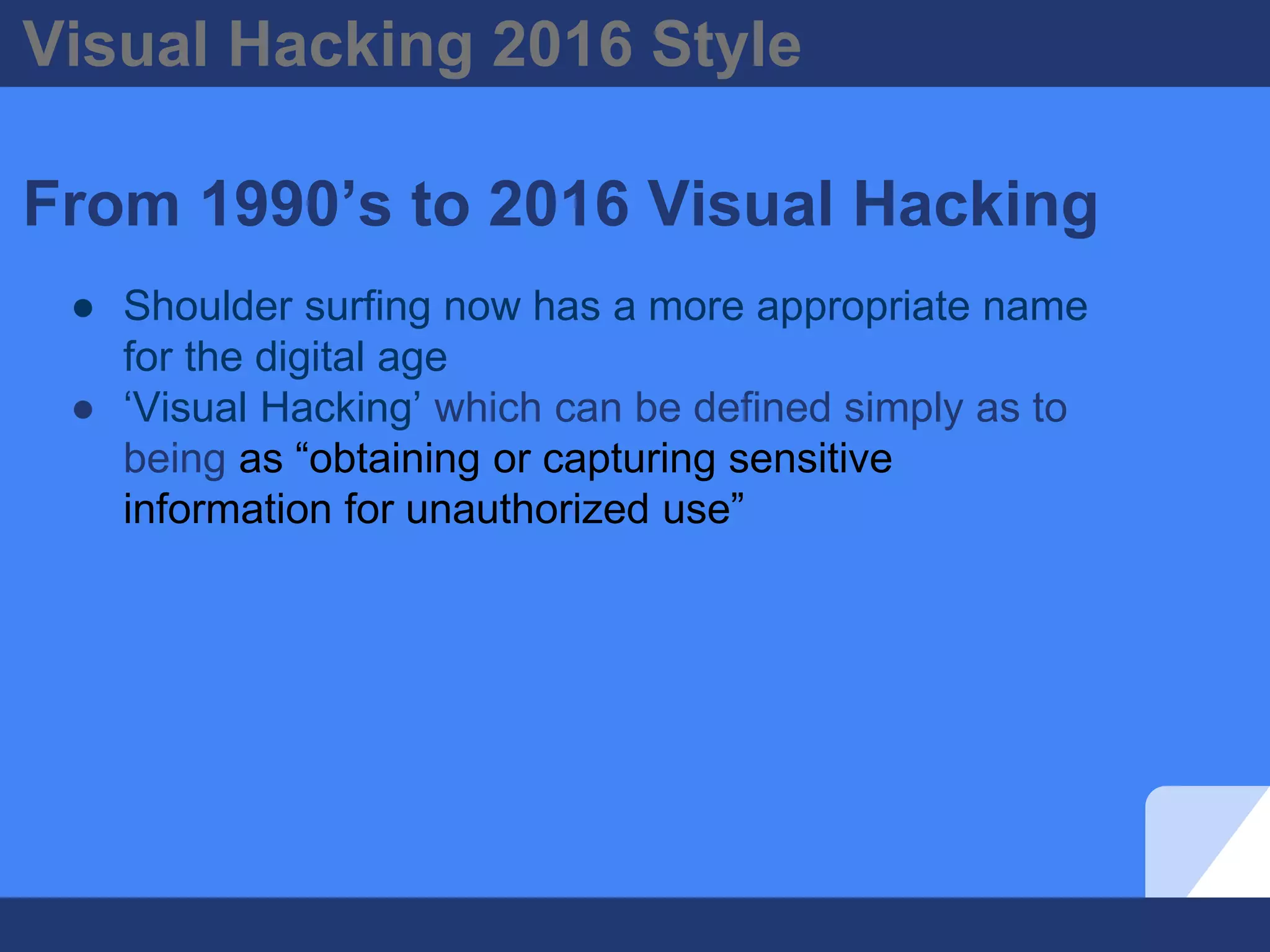
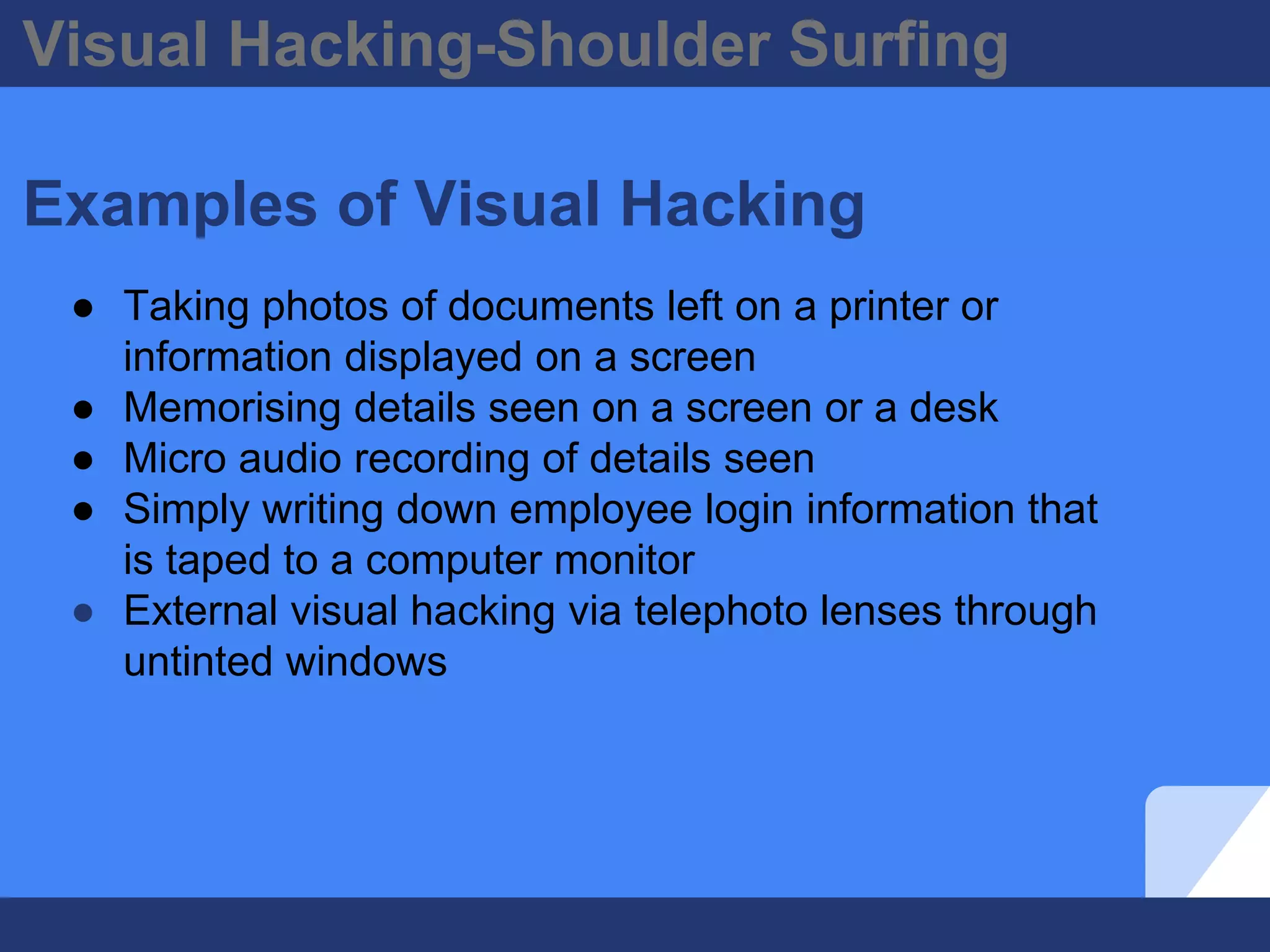
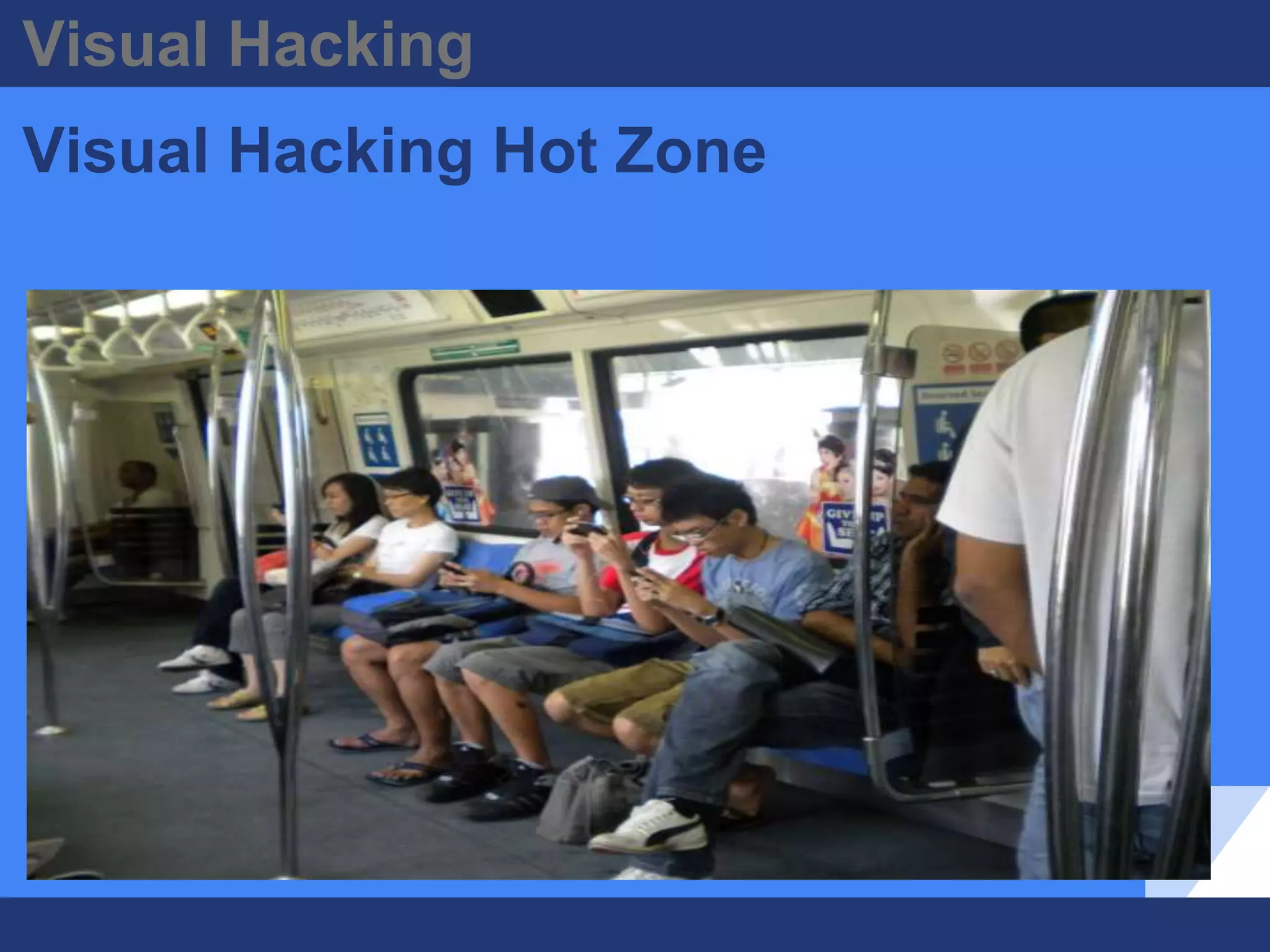
The document discusses visual hacking, specifically the act of obtaining sensitive information through unauthorized means, often referred to as 'shoulder surfing.' It highlights historical examples, vulnerability assessments, and modern implications of visual hacking in the digital age, emphasizing the importance of preventive measures such as visual privacy audits and employee awareness. Key recommendations for organizations include implementing visual privacy policies and safeguards, as the risk of visual hacking can come from anyone with access to the vicinity.