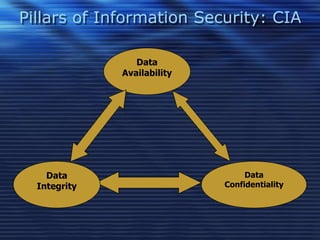
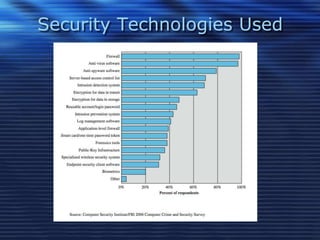
This document discusses information security and recommends security measures. It defines information security as protecting data from unauthorized access, use, disclosure, disruption or destruction. It notes that information is critical for businesses and governments store huge amounts of confidential data that needs protection. Common security threats include computer viruses, hacking, social engineering and denial of service attacks. The document recommends using strong passwords, keeping software updated, being wary of suspicious emails, backing up data, and protecting information in all forms to maintain the pillars of information security - confidentiality, integrity and availability of data.