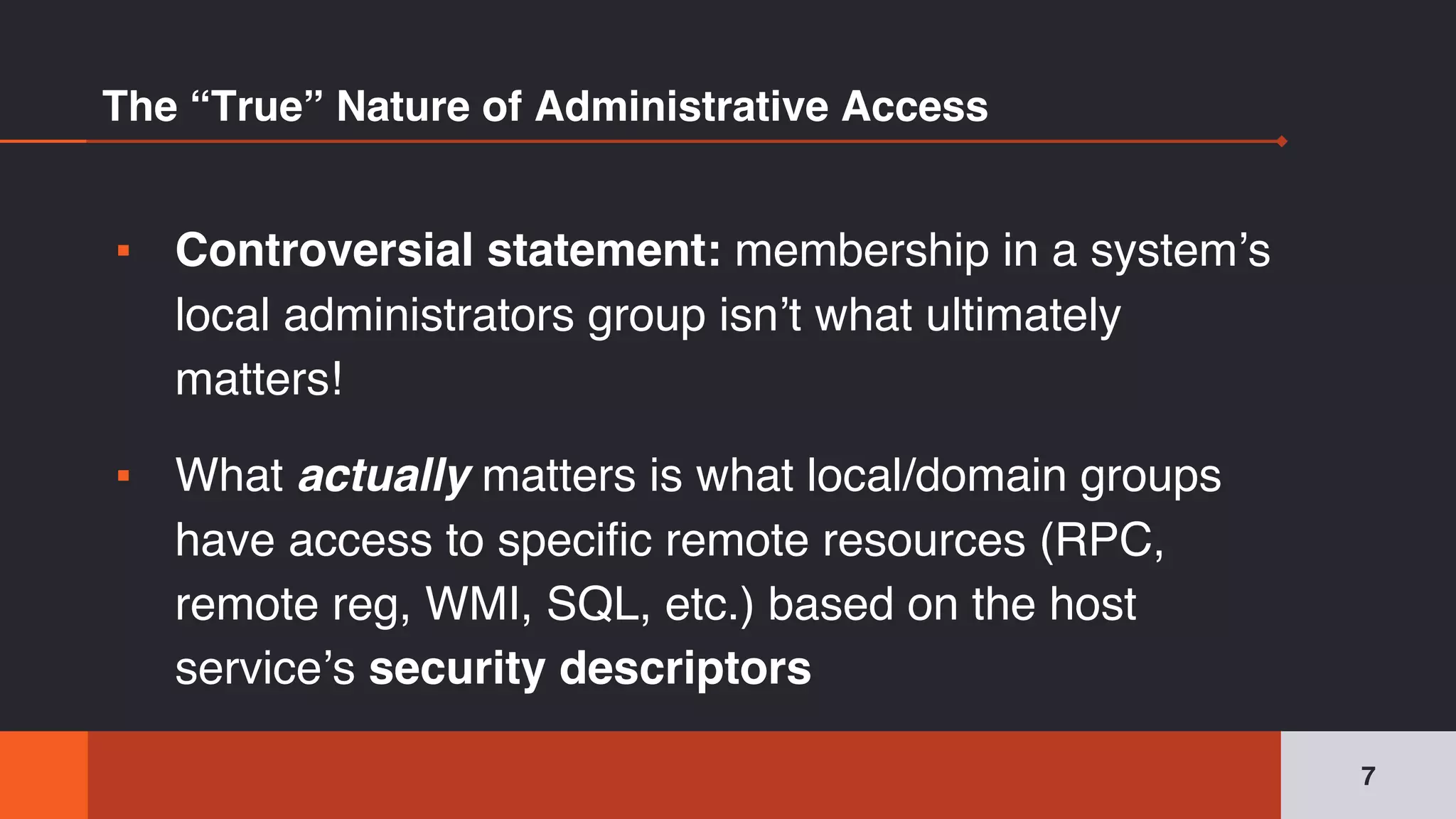
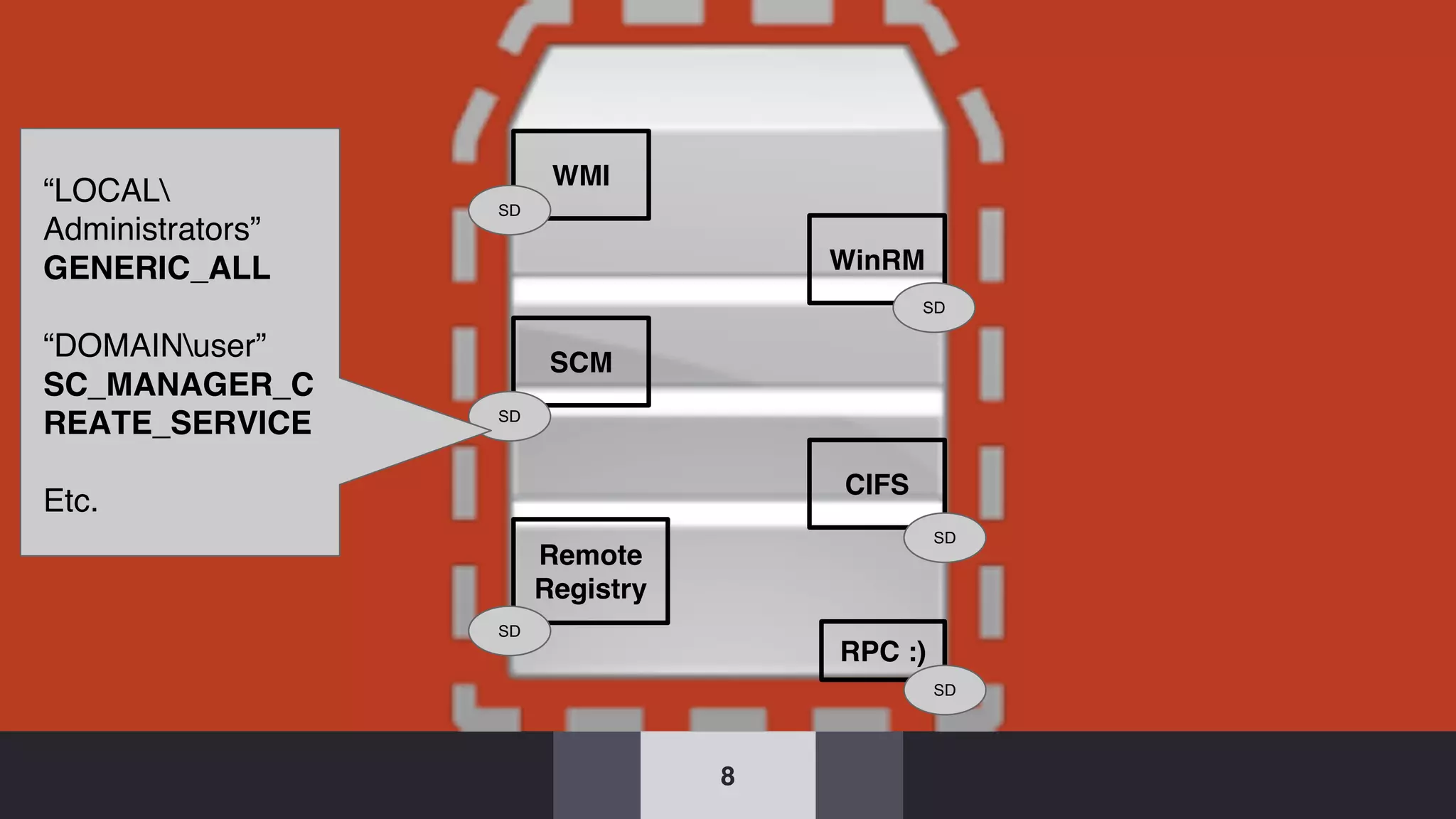
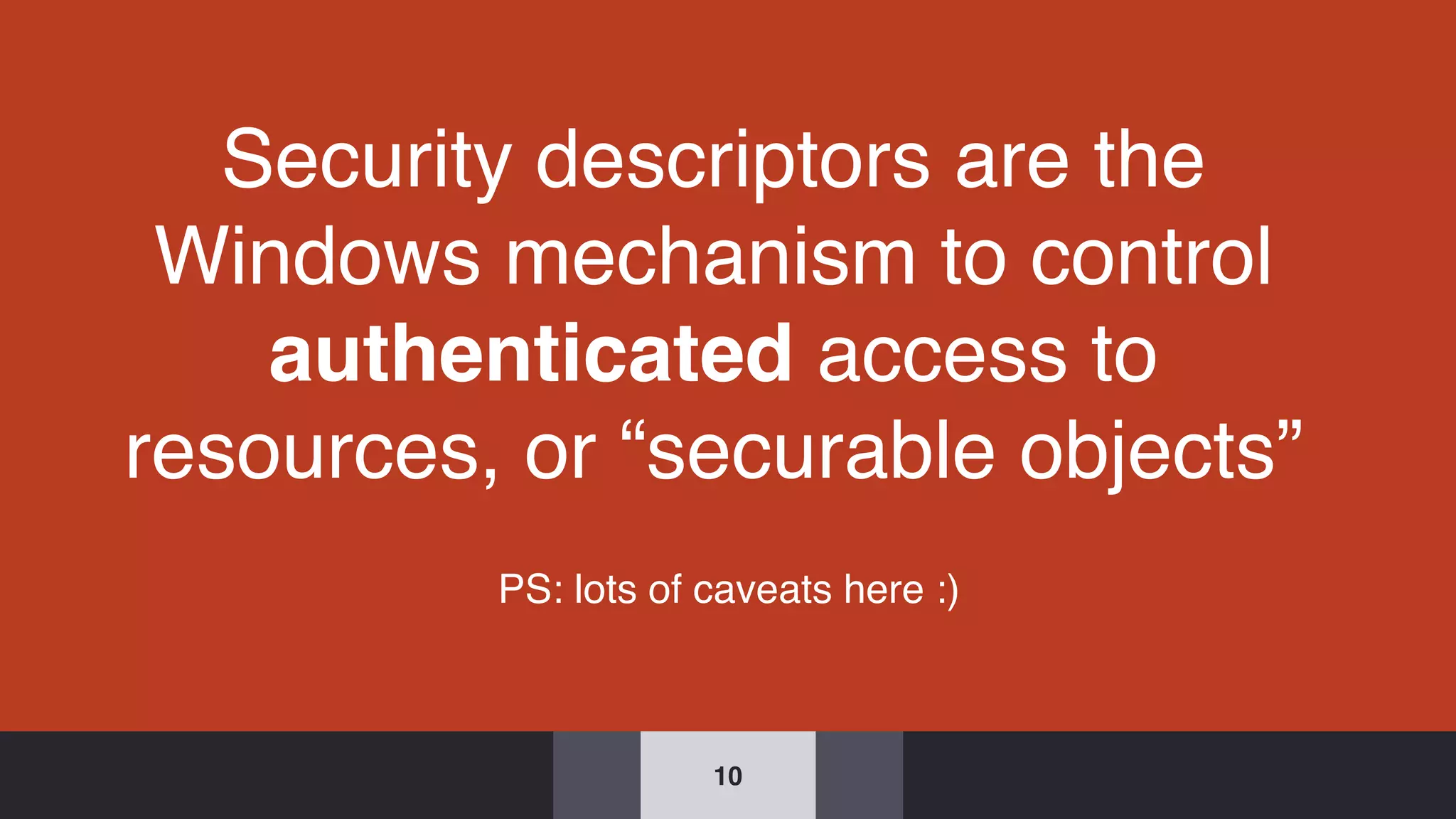
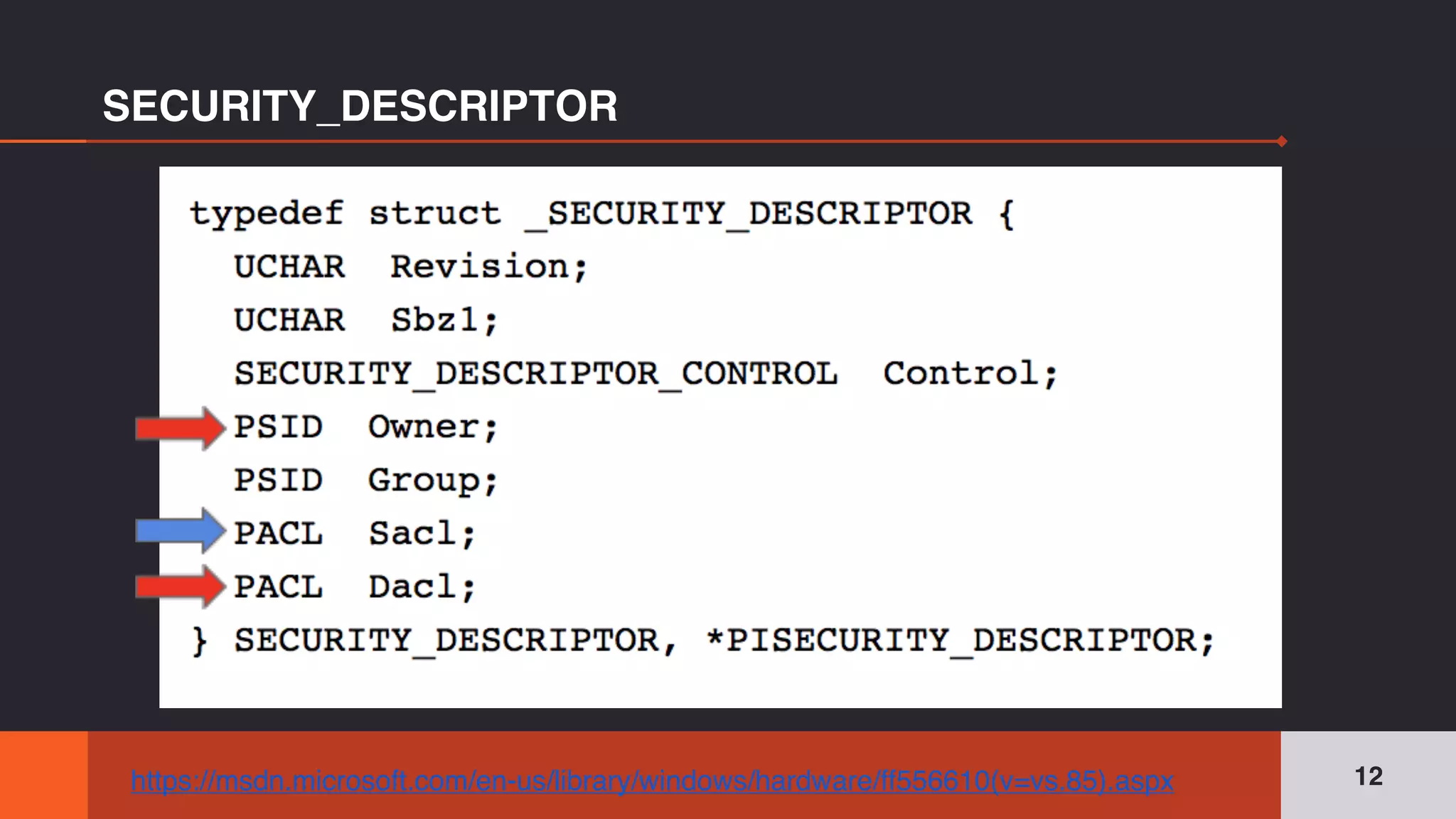
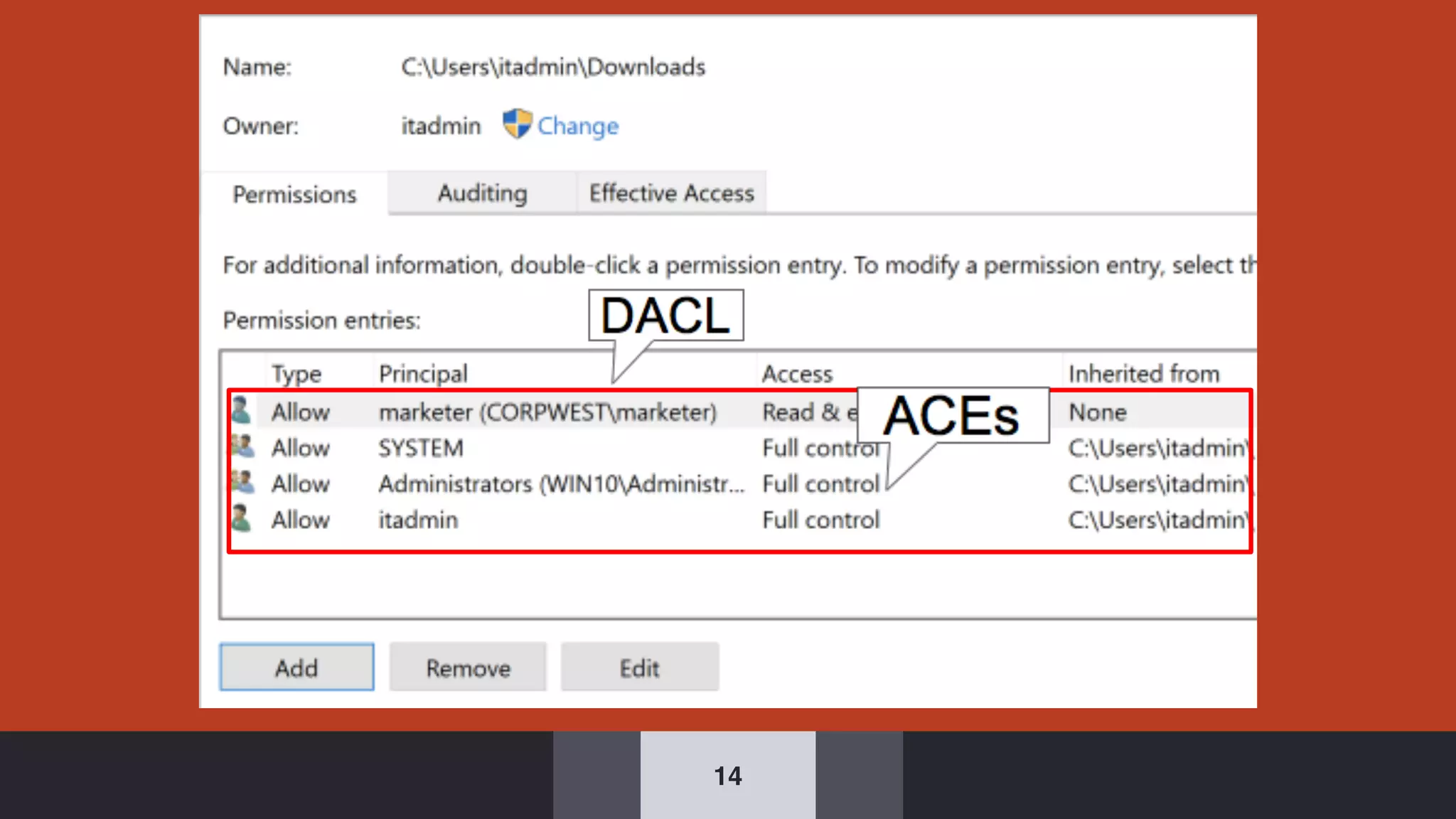
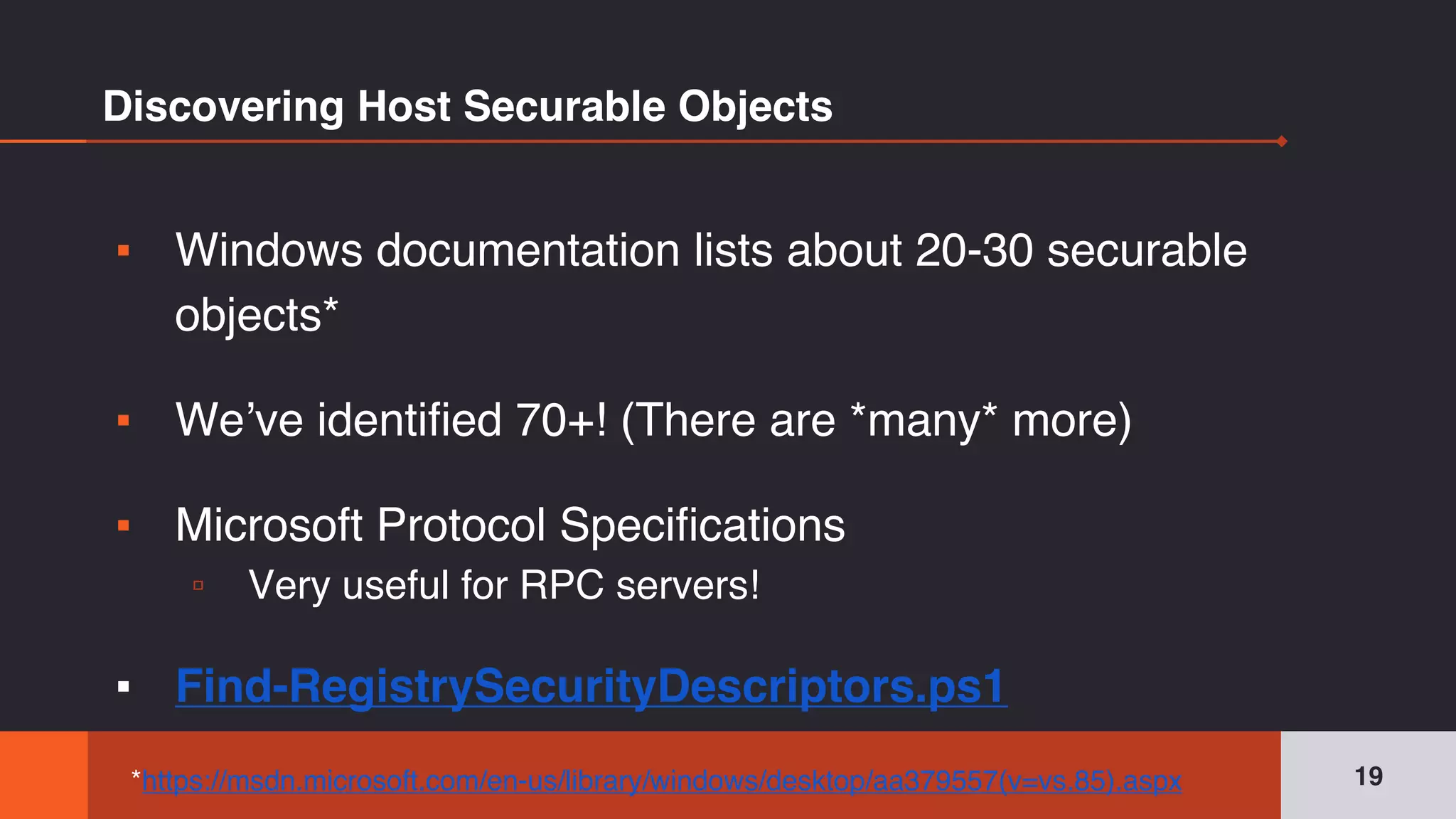
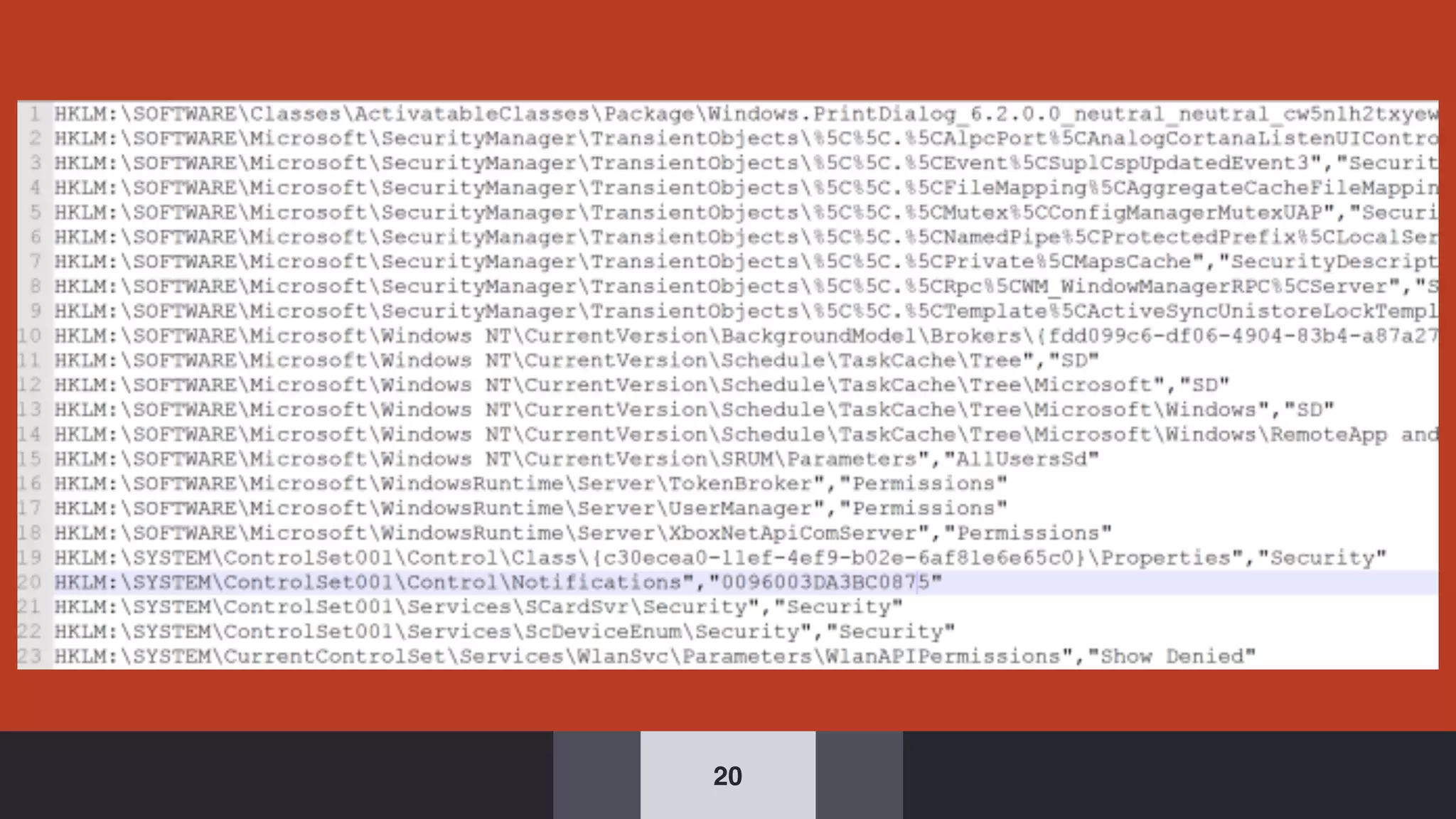
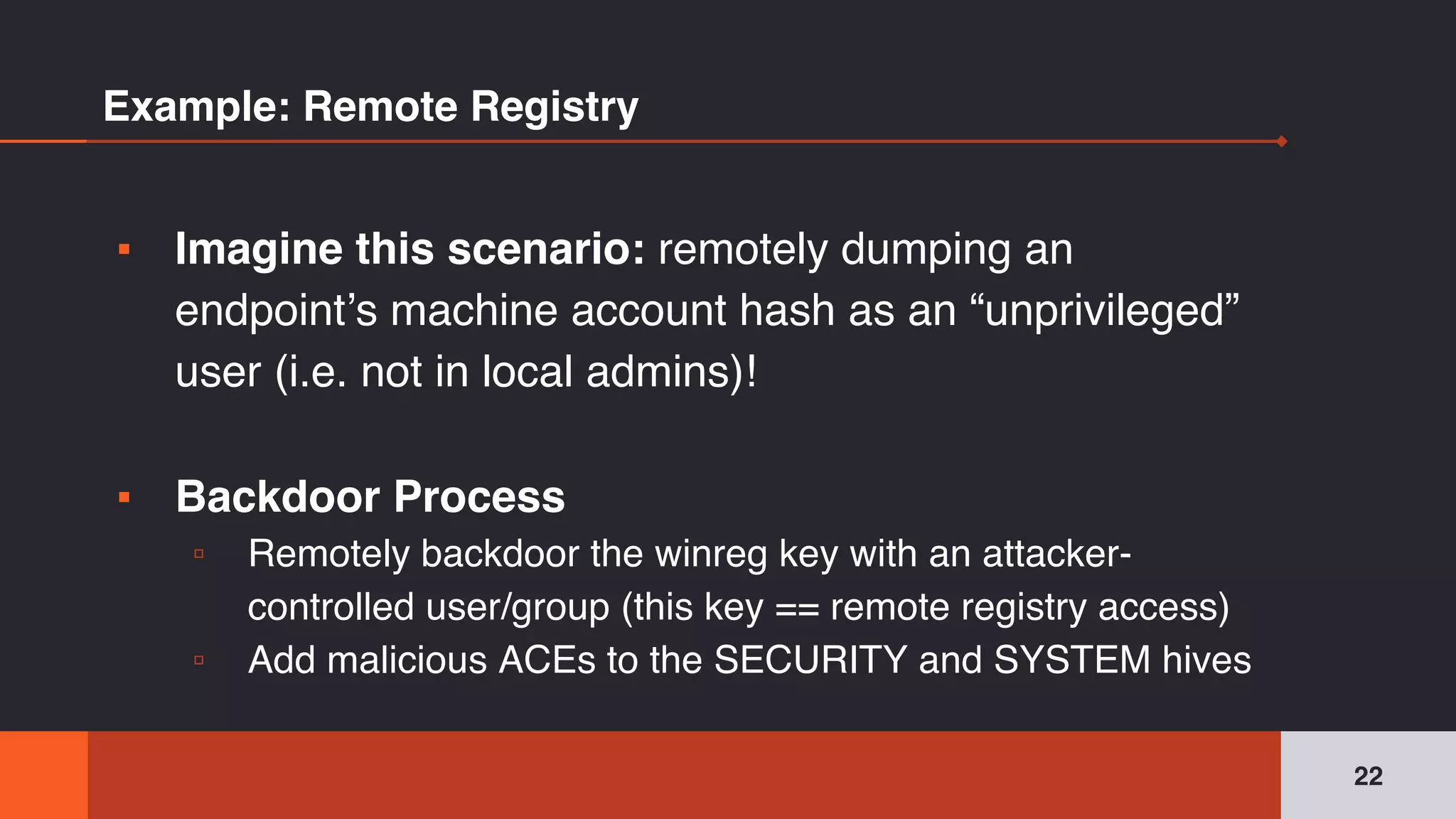
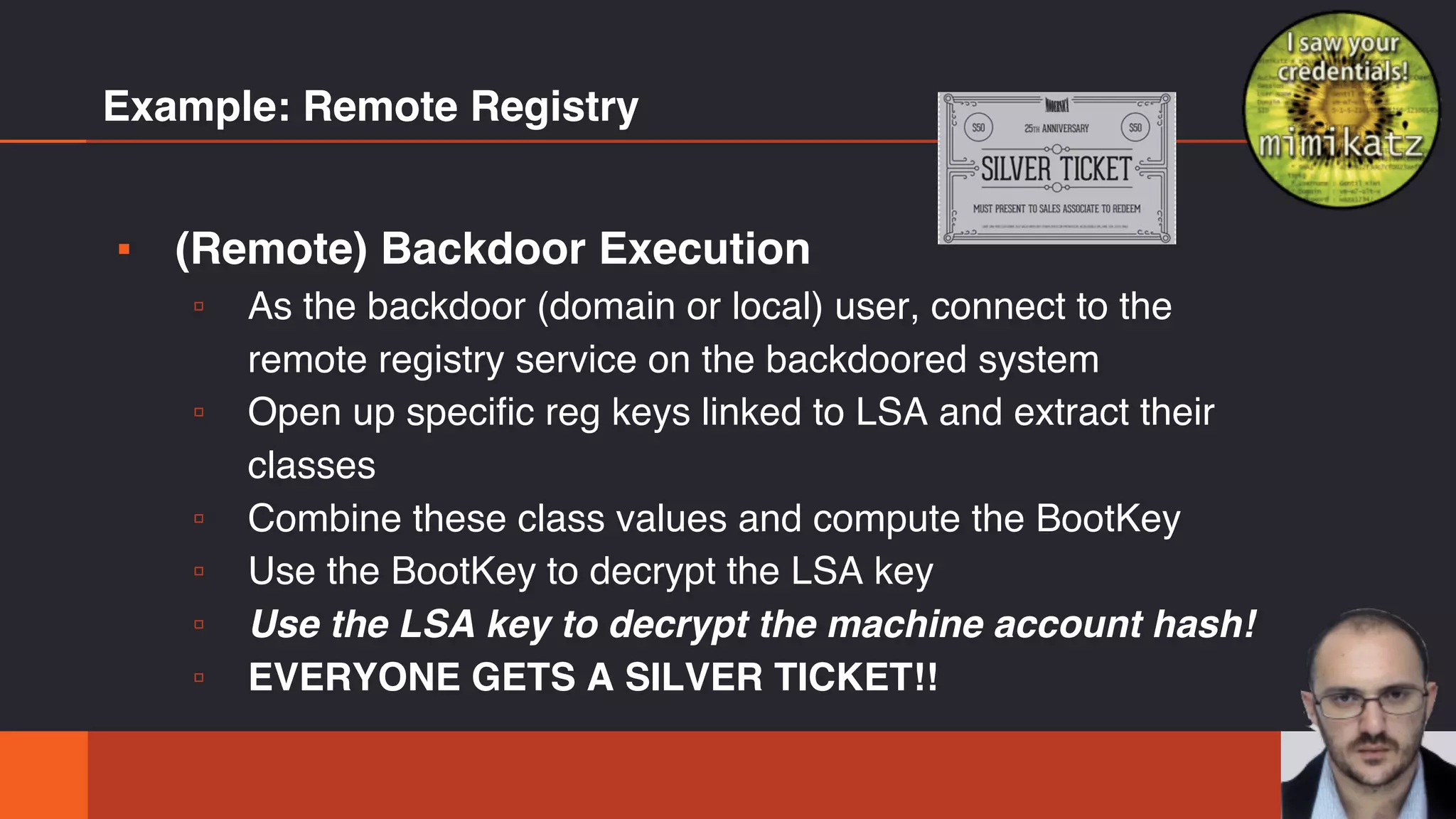
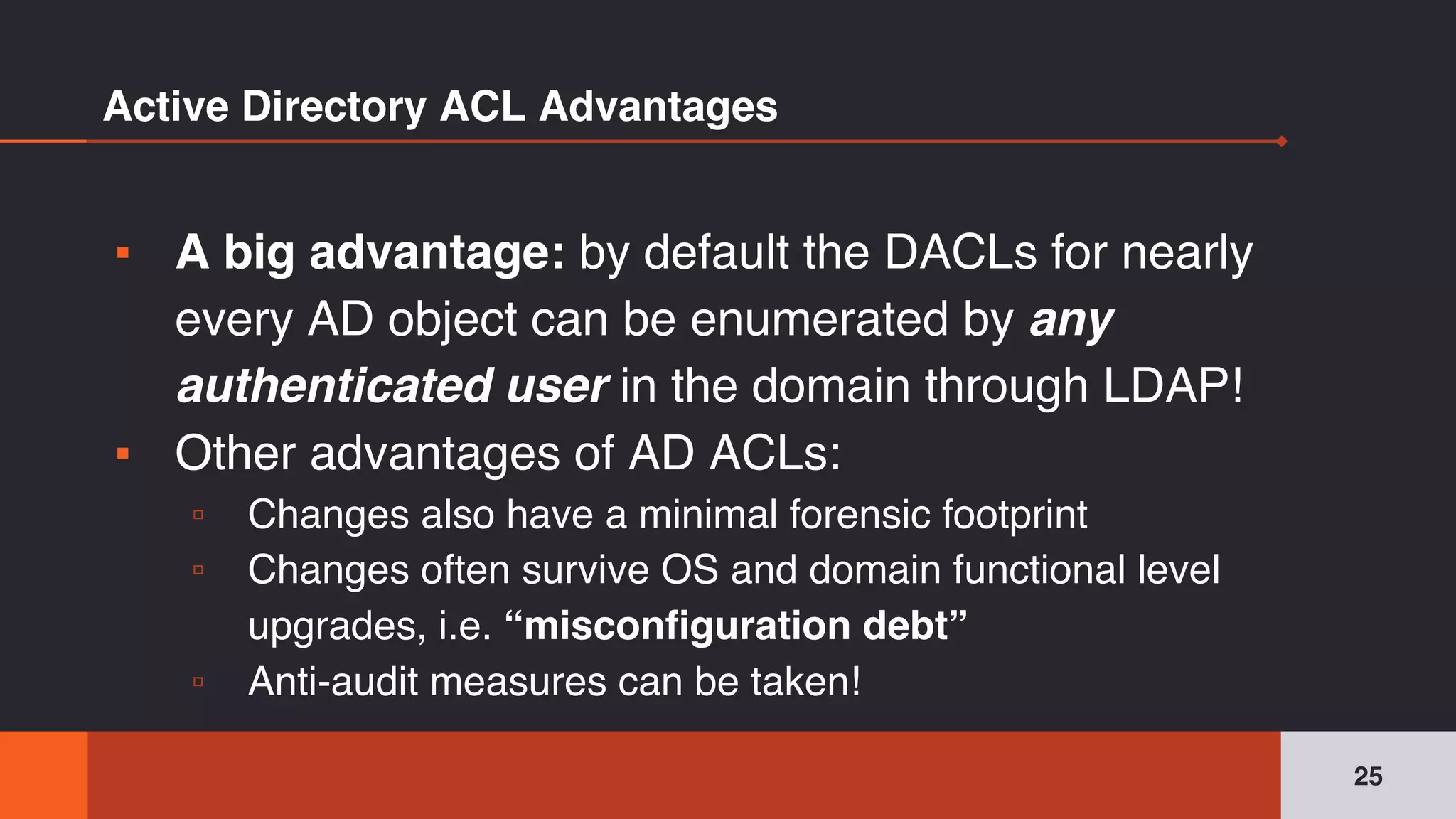
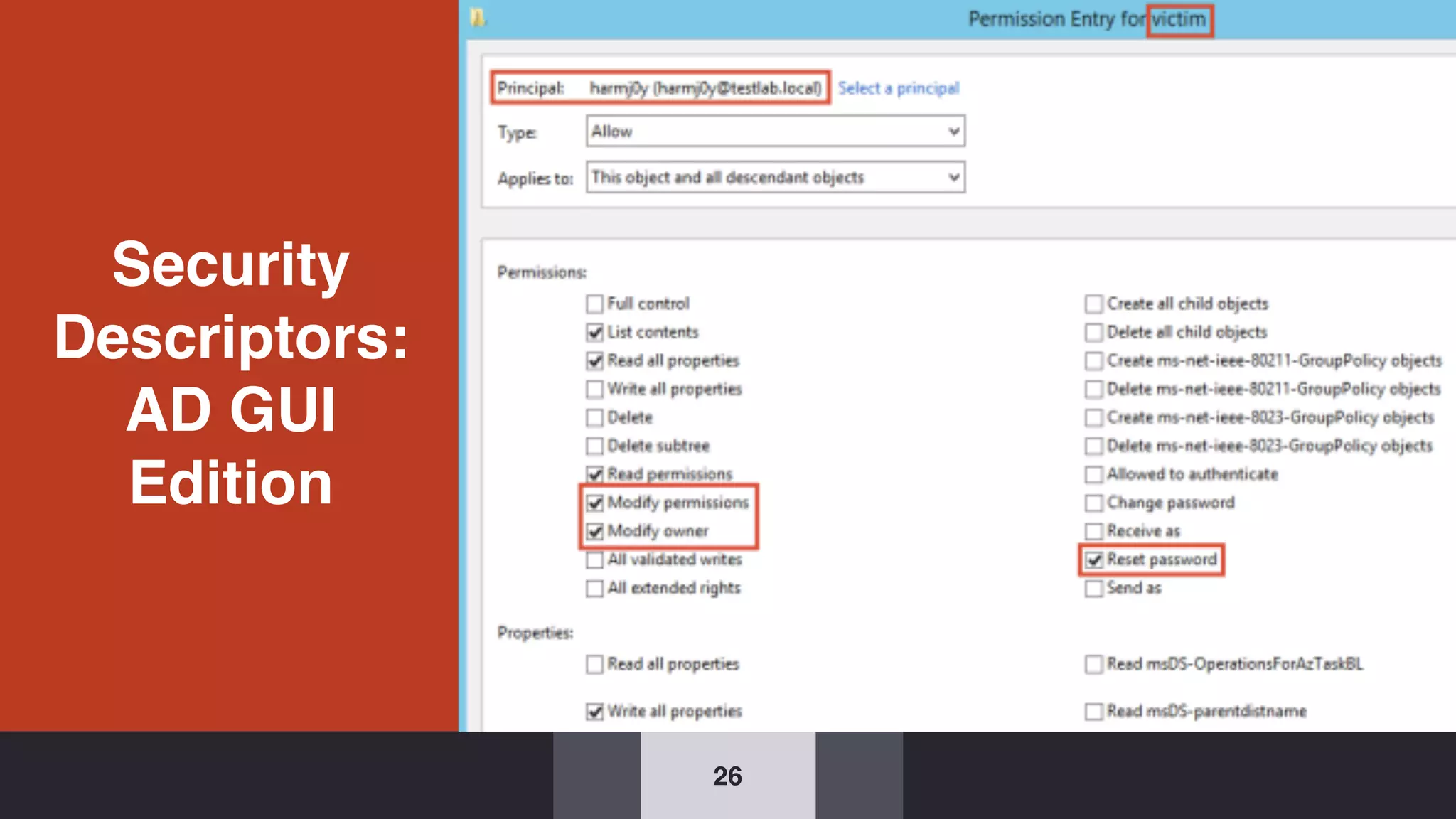
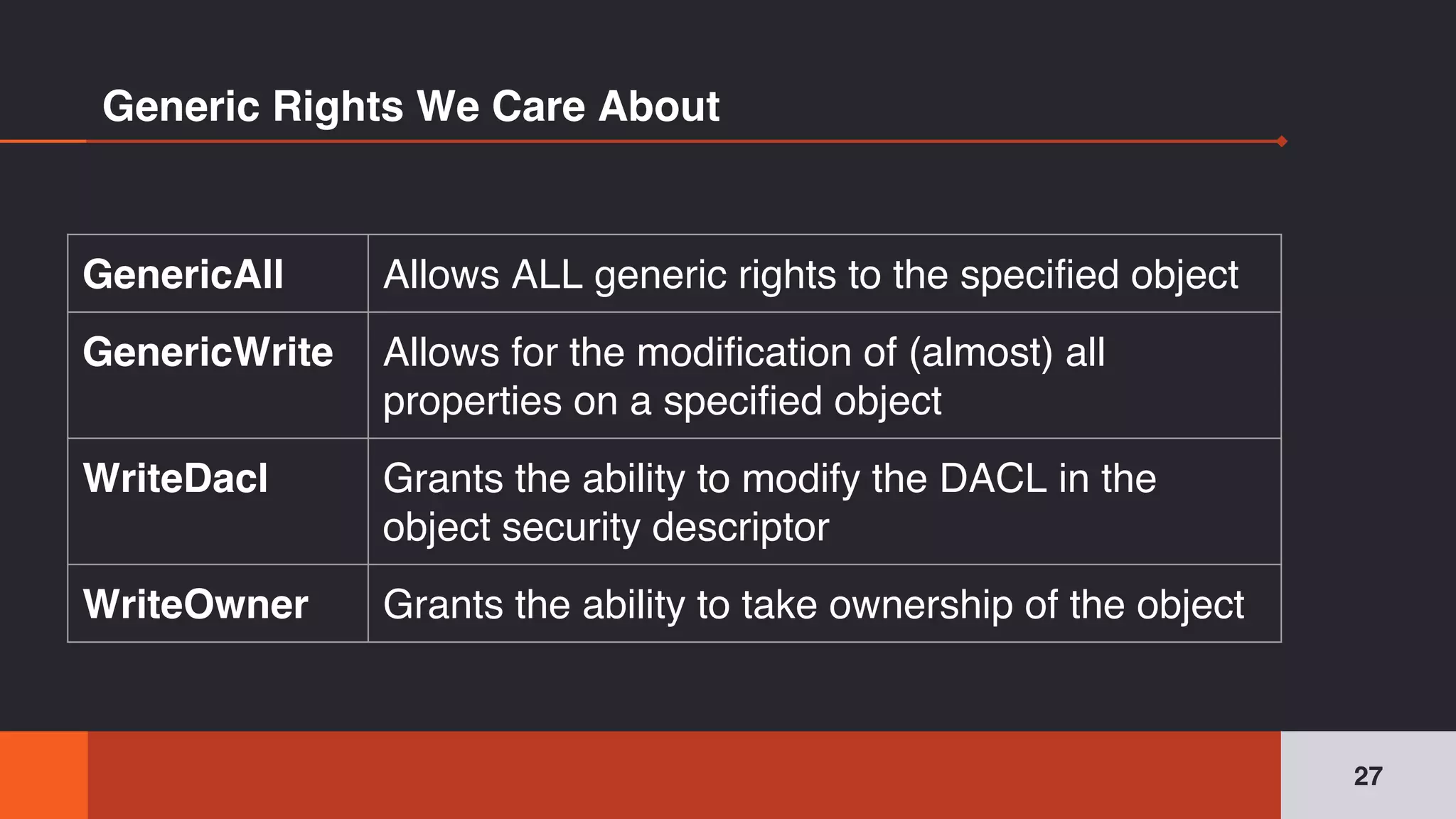
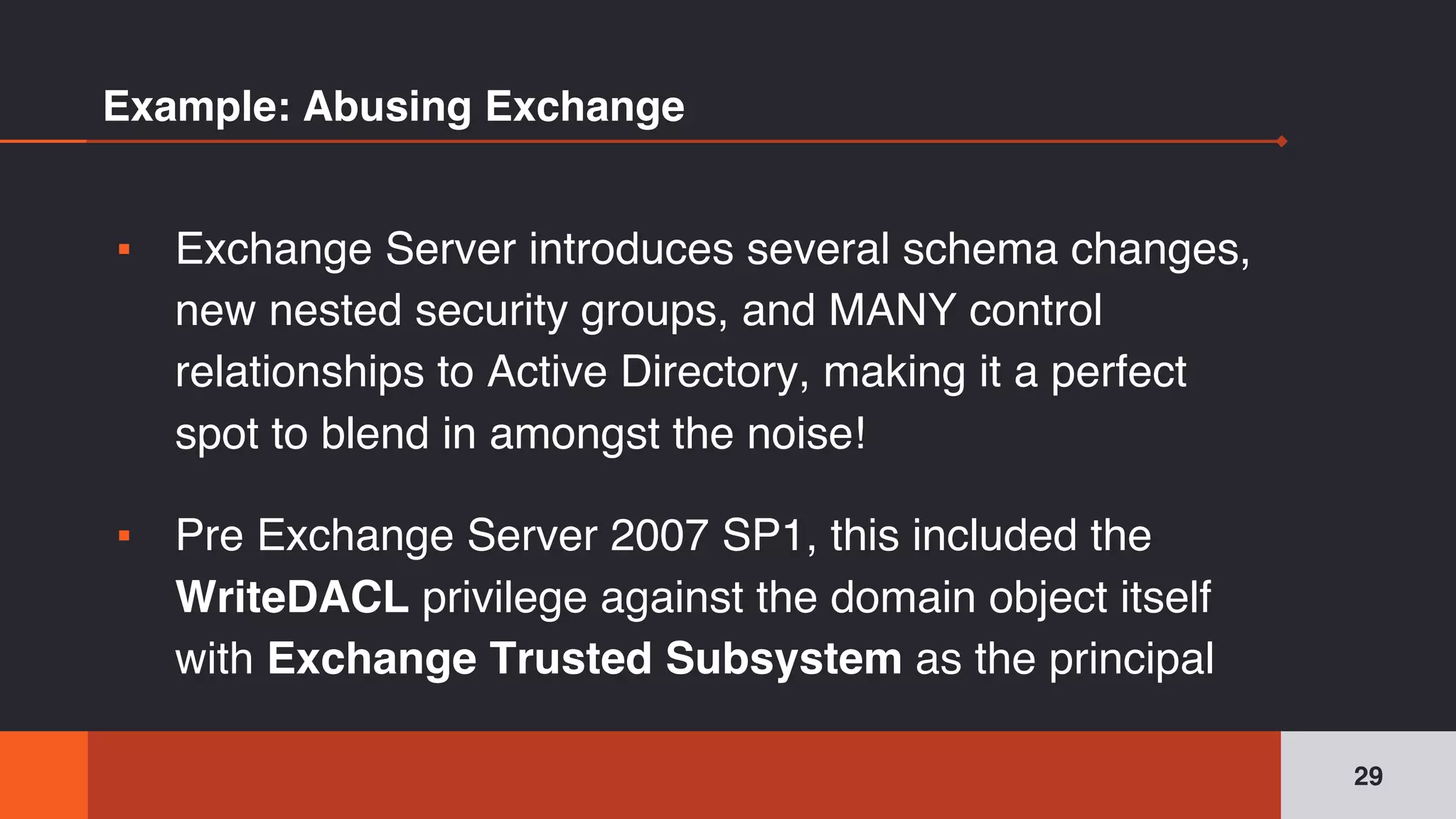
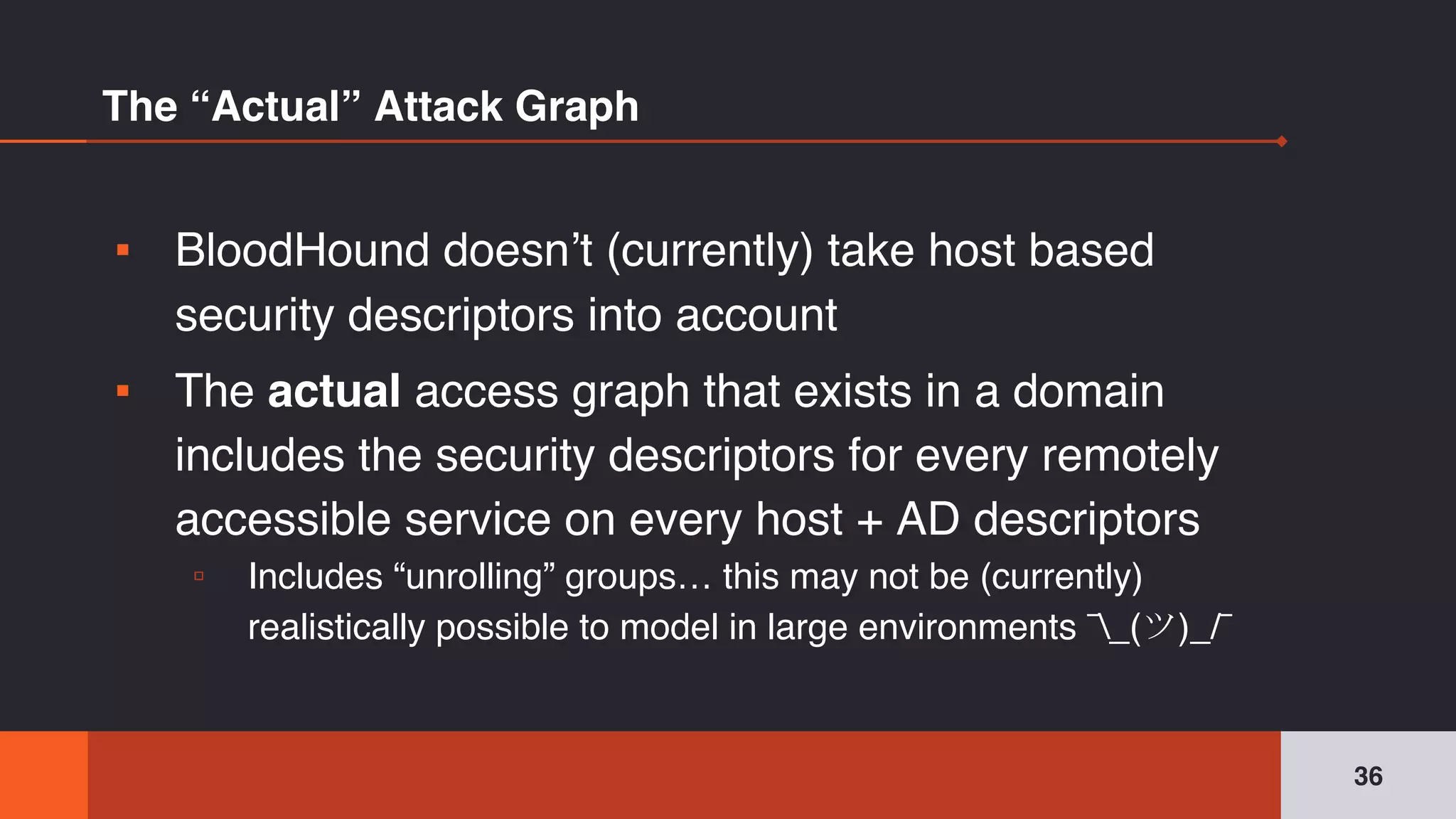
The document discusses the complexities and risks associated with Active Directory (AD) security, emphasizing that security descriptors play a crucial role in access management. It highlights how misconfigured or malicious changes to these descriptors can lead to escalation of privileges and backdoor access, complicating the security landscape within a domain. The authors argue that understanding and addressing these security descriptors is essential for safeguarding systems integrated with AD.


















![[DEMO]
41](https://image.slidesharecdn.com/sp4rkconactivedirectory-180407221345/75/The-Unintended-Risks-of-Trusting-Active-Directory-41-2048.jpg)


![44
[DEMO]](https://image.slidesharecdn.com/sp4rkconactivedirectory-180407221345/75/The-Unintended-Risks-of-Trusting-Active-Directory-44-2048.jpg)

![46
Questions?
You can find us at @SpecterOps:
▪ @harmj0y , @tifkin_ ,
@enigma0x3
▪ [will,lee,matt]@specterops.io](https://image.slidesharecdn.com/sp4rkconactivedirectory-180407221345/75/The-Unintended-Risks-of-Trusting-Active-Directory-46-2048.jpg)