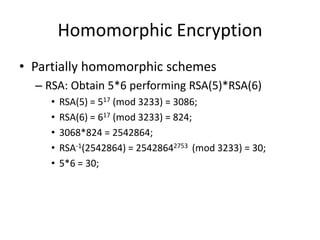
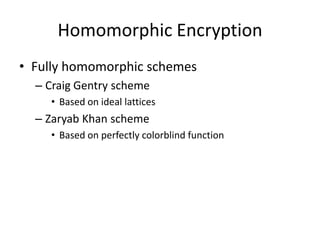
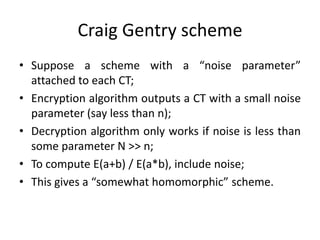
Homomorphic encryption allows computations to be carried out on encrypted data without decrypting it first. This summary discusses Craig Gentry's scheme for fully homomorphic encryption based on ideal lattices. The scheme works by encrypting bits as ciphertexts with small noise that grows with computations. A bootstrapping procedure called re-crypt reduces the noise to keep ciphertexts decryptable. While promising for applications like cloud computing, the scheme has high computational costs that scale poorly with security level. Current research aims to make homomorphic encryption more efficient and practical.


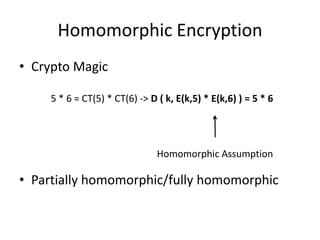

![Craig Gentry scheme (integers)
• Key: odd integer p > 2N
• Encryption algorithm: given a bit b -> E(b) = c = b +
2x + kp, where x is in [-n/2,n/2] and k is an integer
chosen from some range
• Decryption algorithm: b = (c mod p) mod 2, where (c
mod p) is the noise and belongs to [-n,n]
• Decryption works if b + 2x ∈ [-N,N] ⊂[-p/2,p/2]](https://image.slidesharecdn.com/homomorphic-130320052226-phpapp01/85/Homomorphic-Encryption-9-320.jpg)
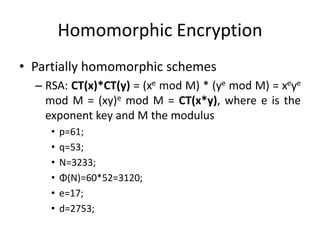
![Craig Gentry scheme (integers)
• Graig Gentry scheme’s homomorphic assumptions
– Addiction: c1 + c2 = b1+ b2 + 2(x1+x2) + (k1+k2)p =
b1 xor b2 + 2x + kp
• Decryption works if (b1+2x1) + (b2+2x2) is in [-
N,N]
– Multiplication: c1*c2 = b1*b2 + 2(b1x2 + b2x1 +
2x1x2) + kp = b1*b2 + 2x + kp
• Decryption works if (b1+2x1) * (b2+2x2) is in [-
N,N]](https://image.slidesharecdn.com/homomorphic-130320052226-phpapp01/85/Homomorphic-Encryption-10-320.jpg)