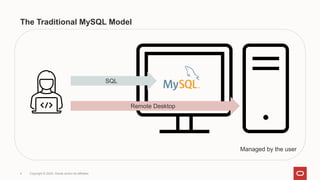
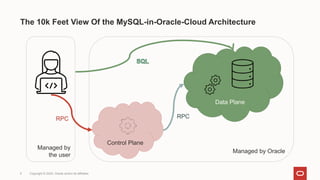
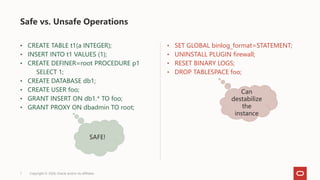
The document discusses MySQL server security in a cloud context, highlighting differences from traditional on-premise security models. It emphasizes the need for granularity in user privileges, advocating for system_user privileges and partial revokes to enhance control over database operations. The content also addresses principles for building a secure cloud security model, ensuring stability and visibility for end users while preventing actions that could destabilize the server.