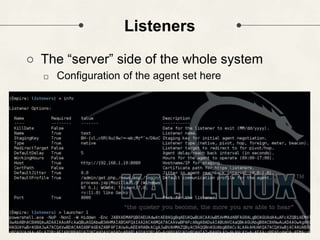
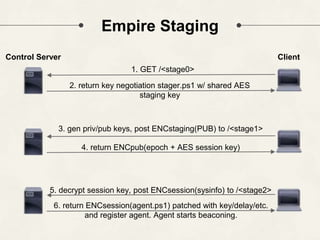
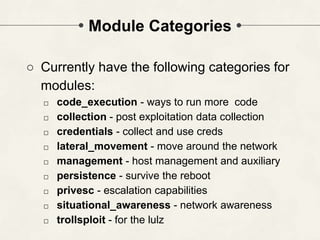
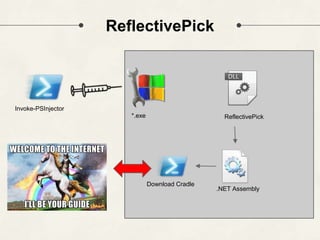
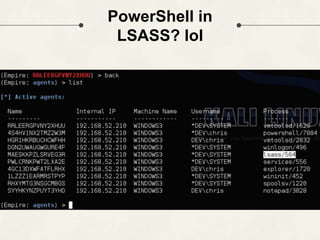
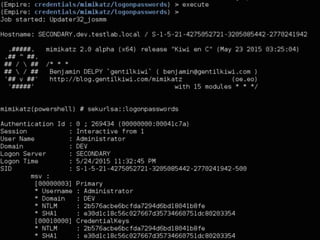
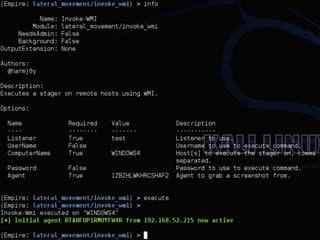
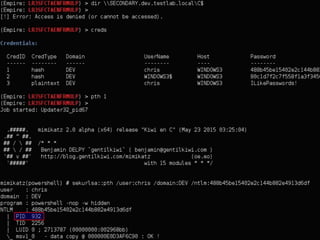
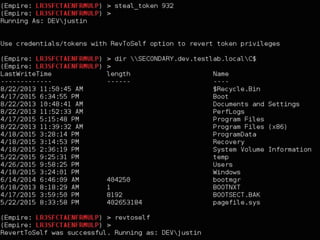
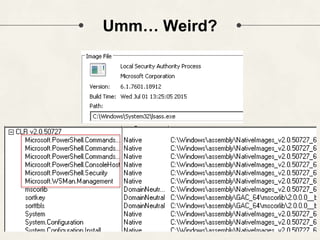
The document discusses PowerShell Empire, a PowerShell post-exploitation framework that aims to provide a flexible and extensible platform for integrating offensive PowerShell capabilities. It provides an overview of Empire's architecture, including its client-server design with a backend database, listeners for command and control, and modules for additional functionality. The document demonstrates Empire's capabilities through modules for process injection, privilege escalation, credential dumping, and lateral movement. It also discusses considerations for detecting and analyzing Empire agents on compromised systems.