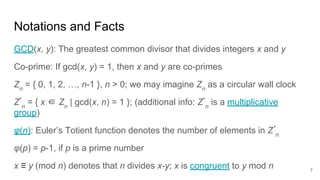
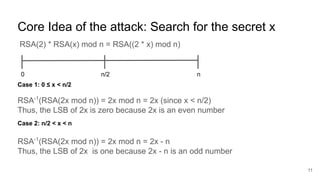
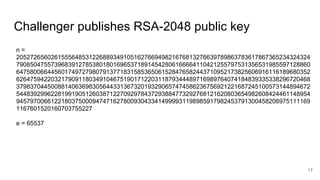
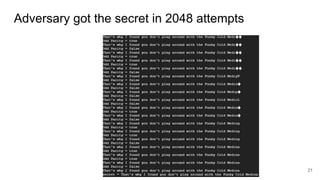
The document presents an interactive RSA game involving an adversary and a challenger, where the goal is to break RSA encryption by reconstructing a secret plaintext using an oracle that reveals the least-significant bit (LSB) of the secret. The adversary leverages homomorphic properties of RSA and the information gained through the oracle to halve the search space iteratively until the secret is revealed after a number of iterations proportional to the size of the RSA modulus. The document outlines the background, algorithm, and mechanics behind this cryptographic attack.