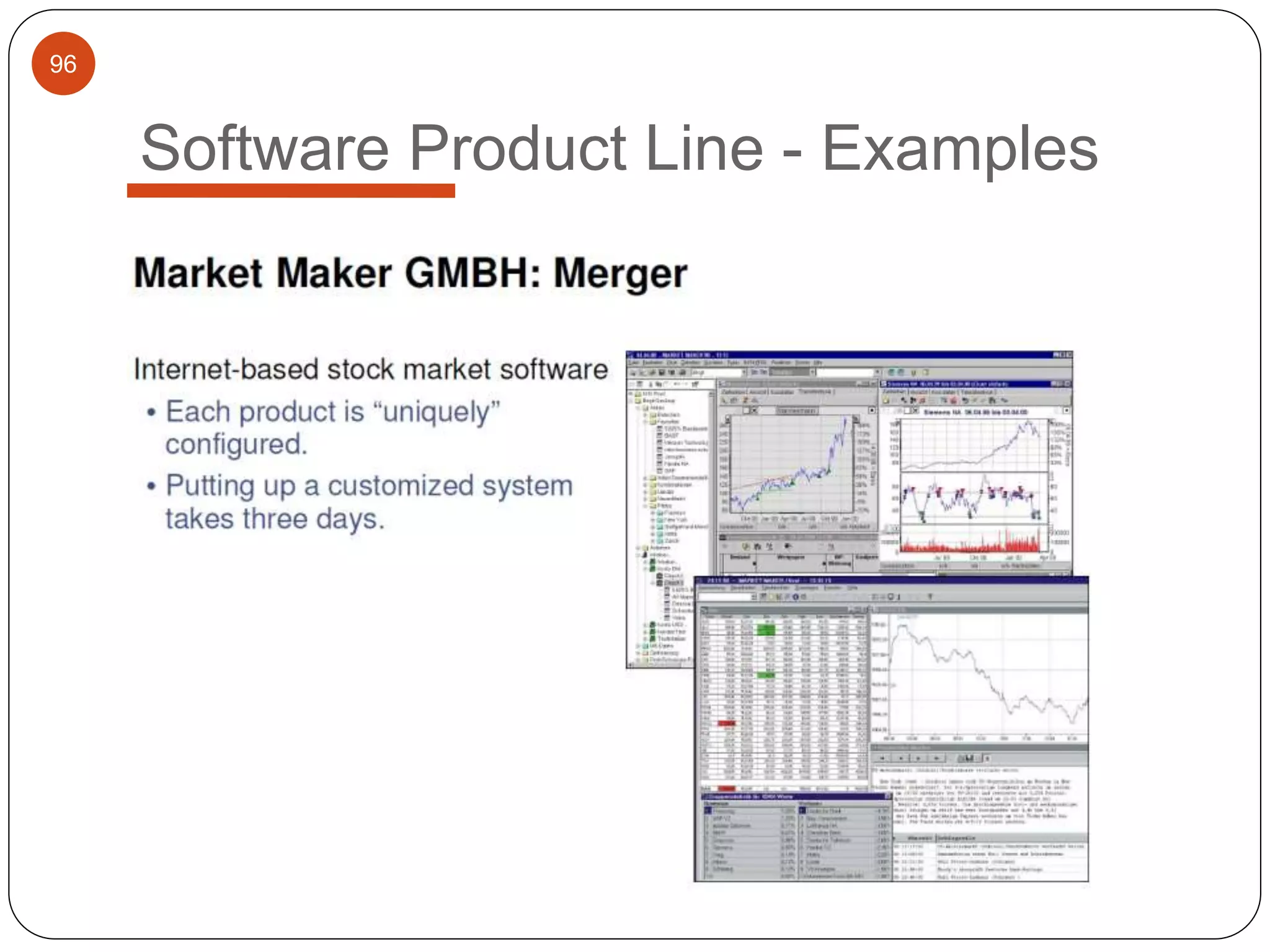
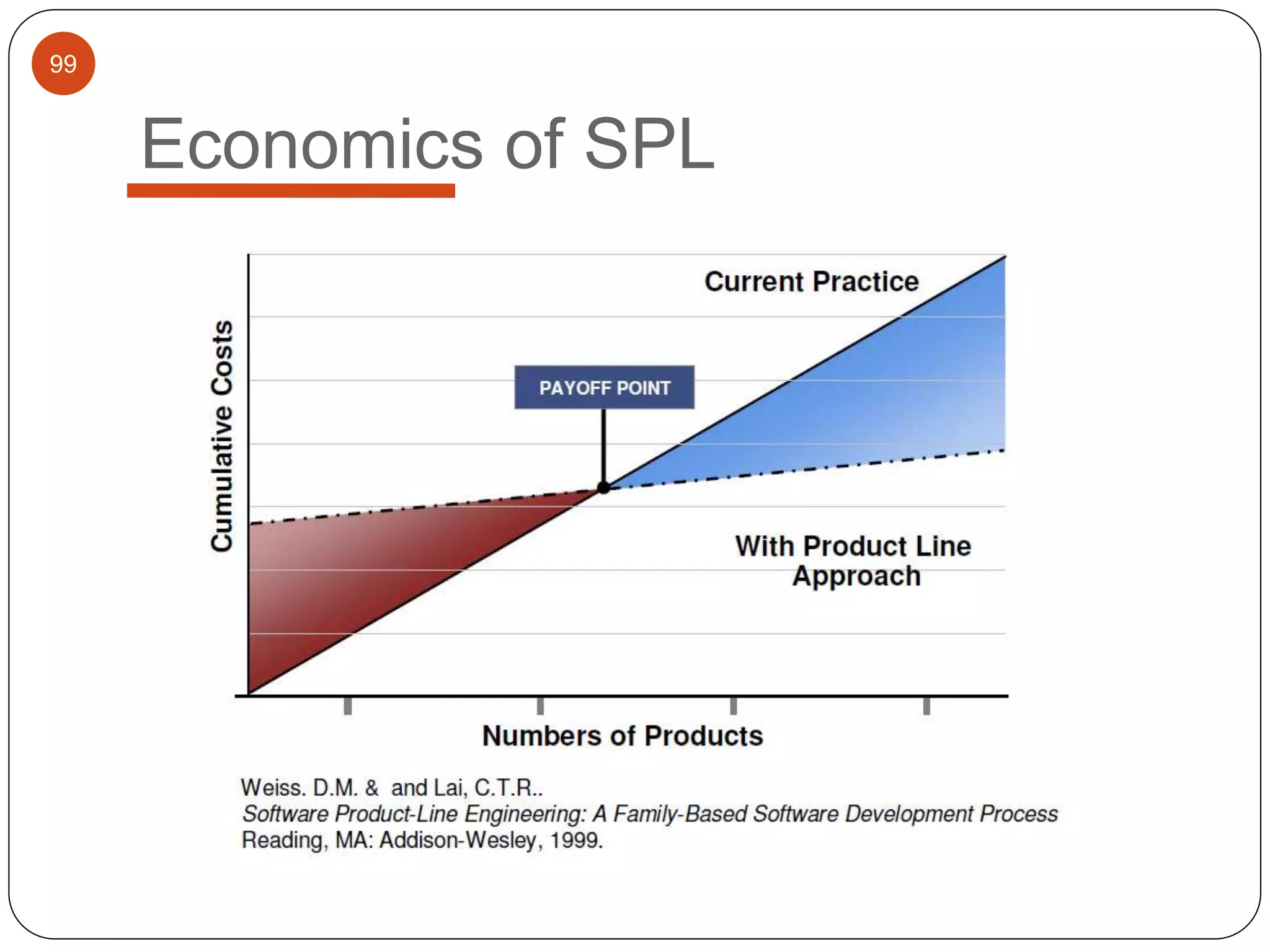
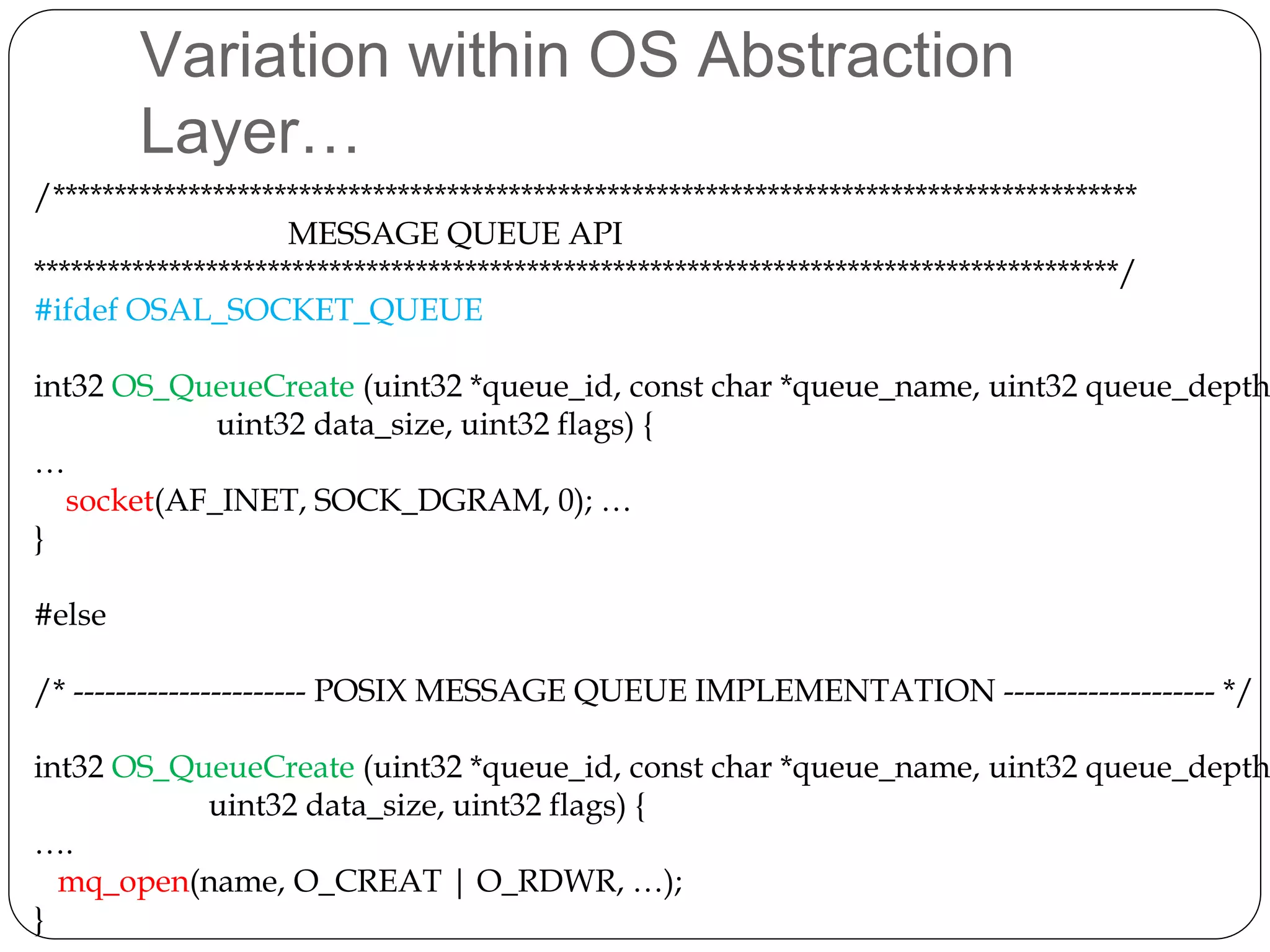
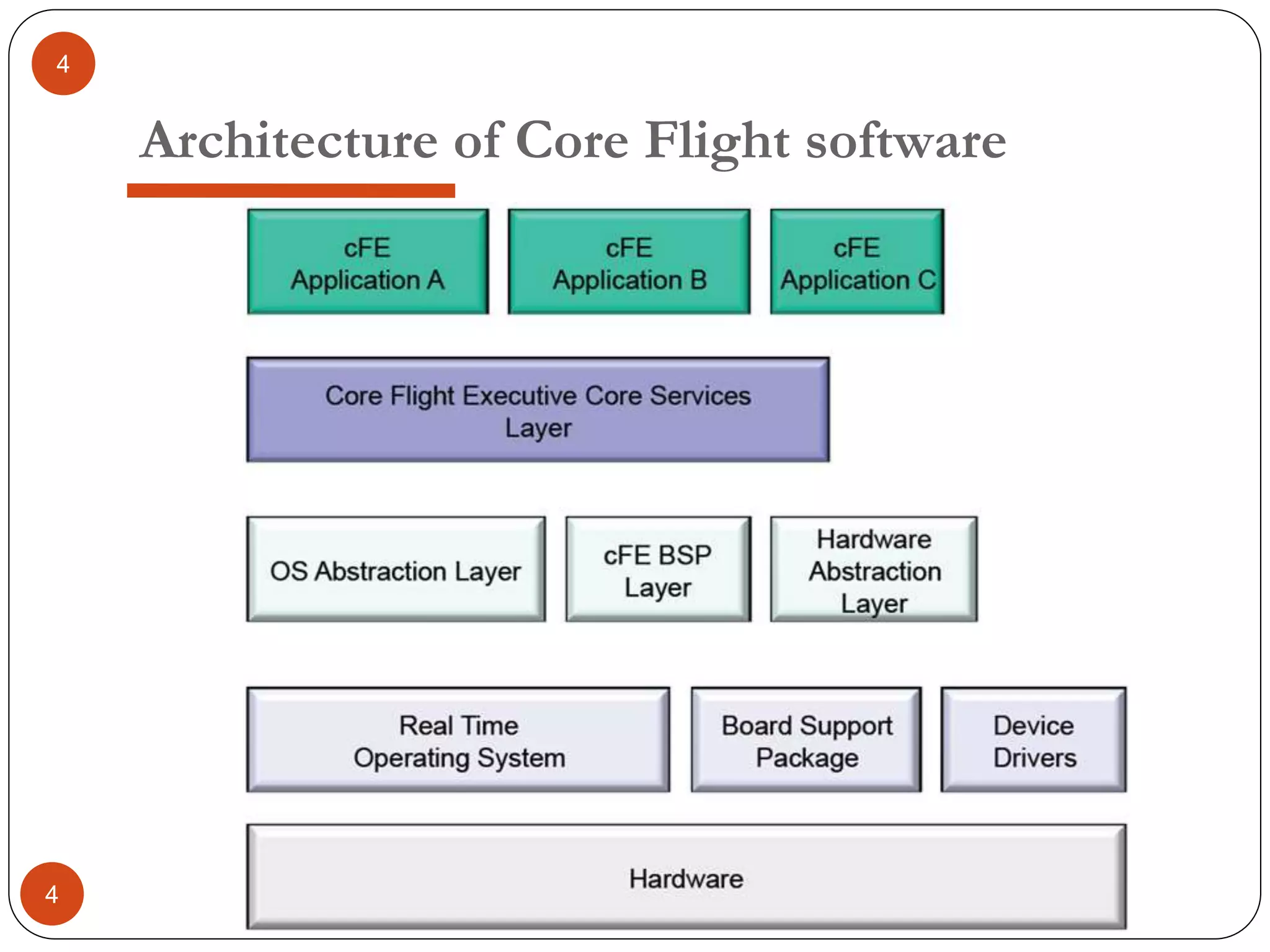
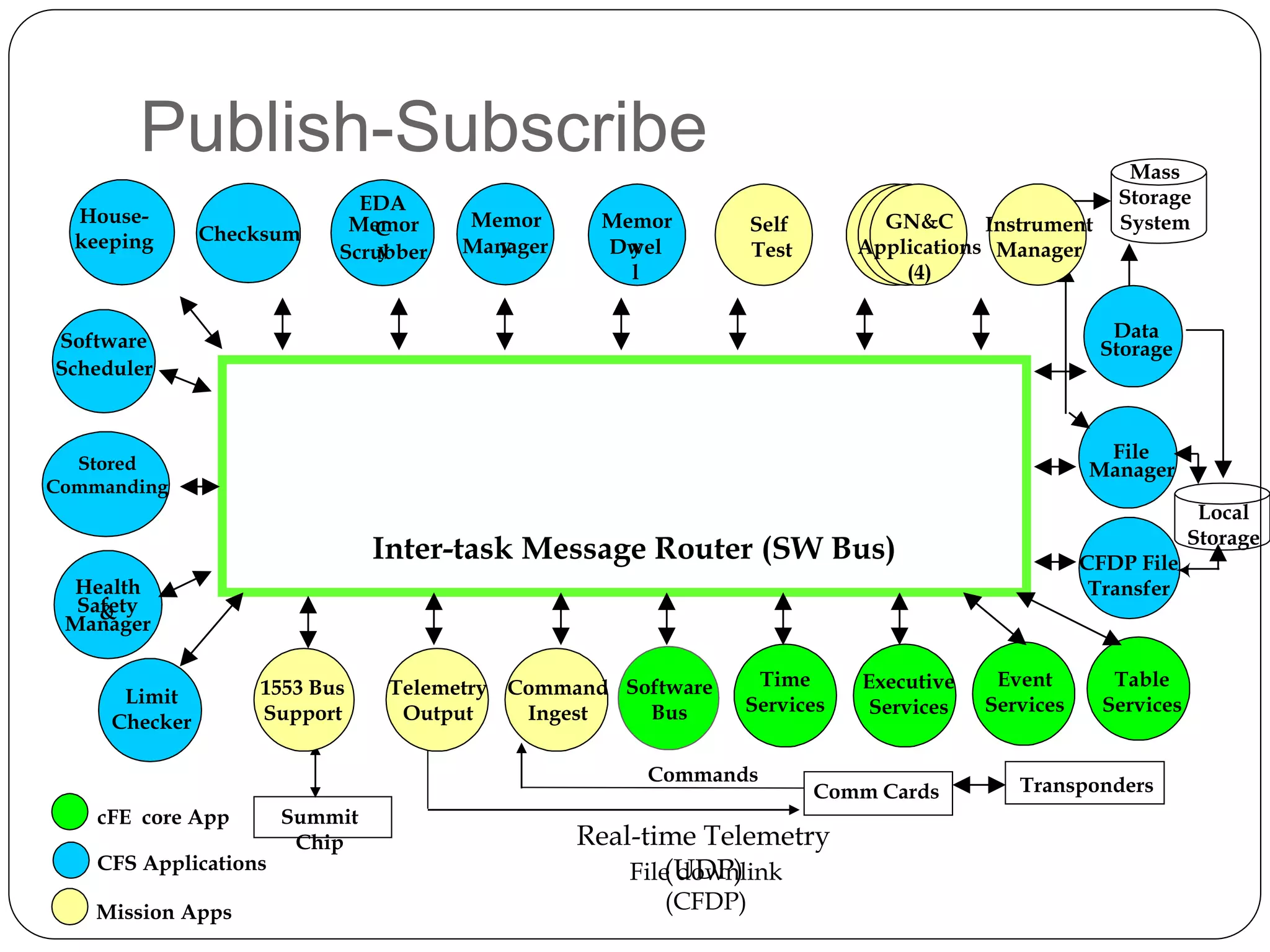
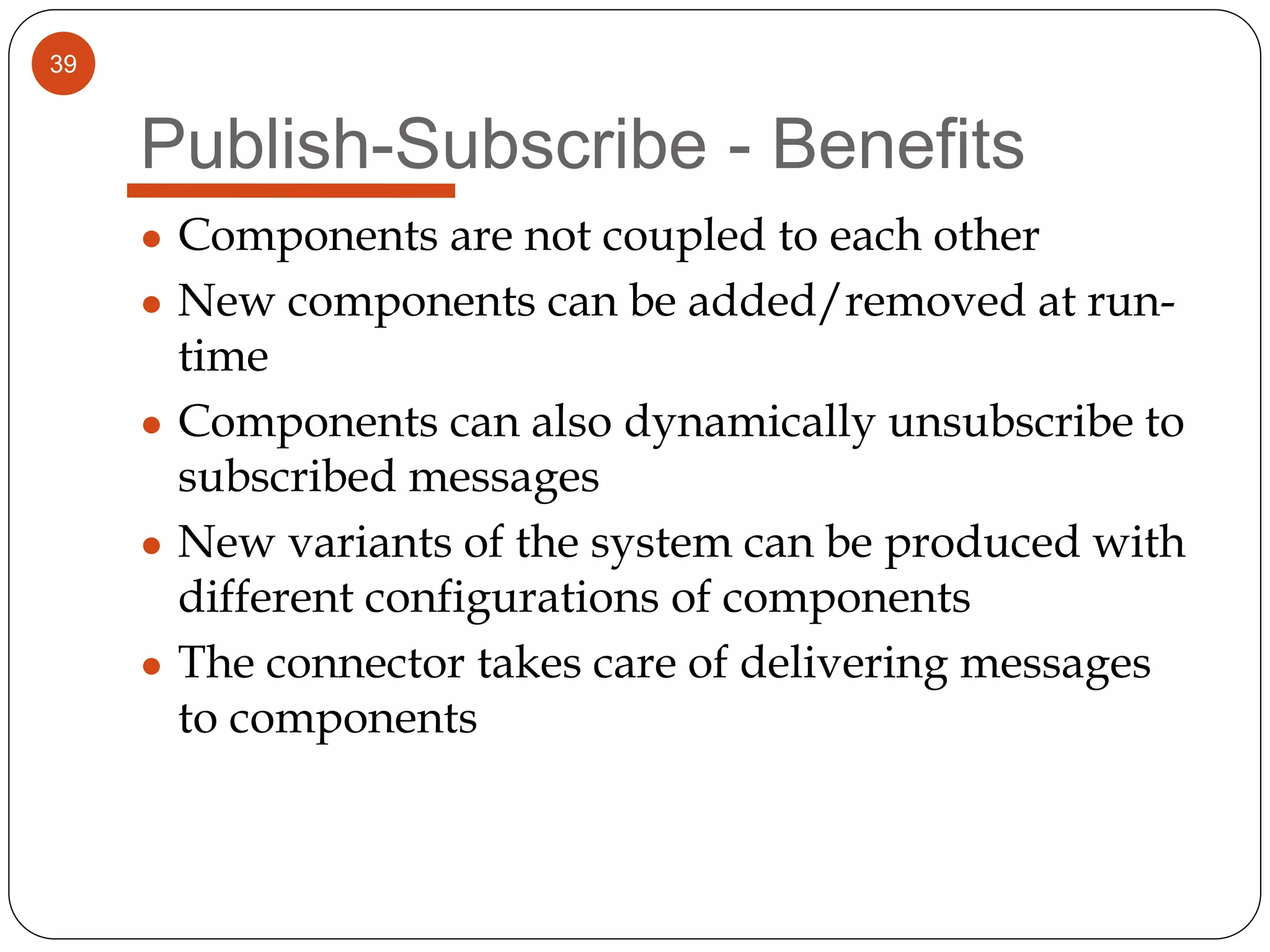
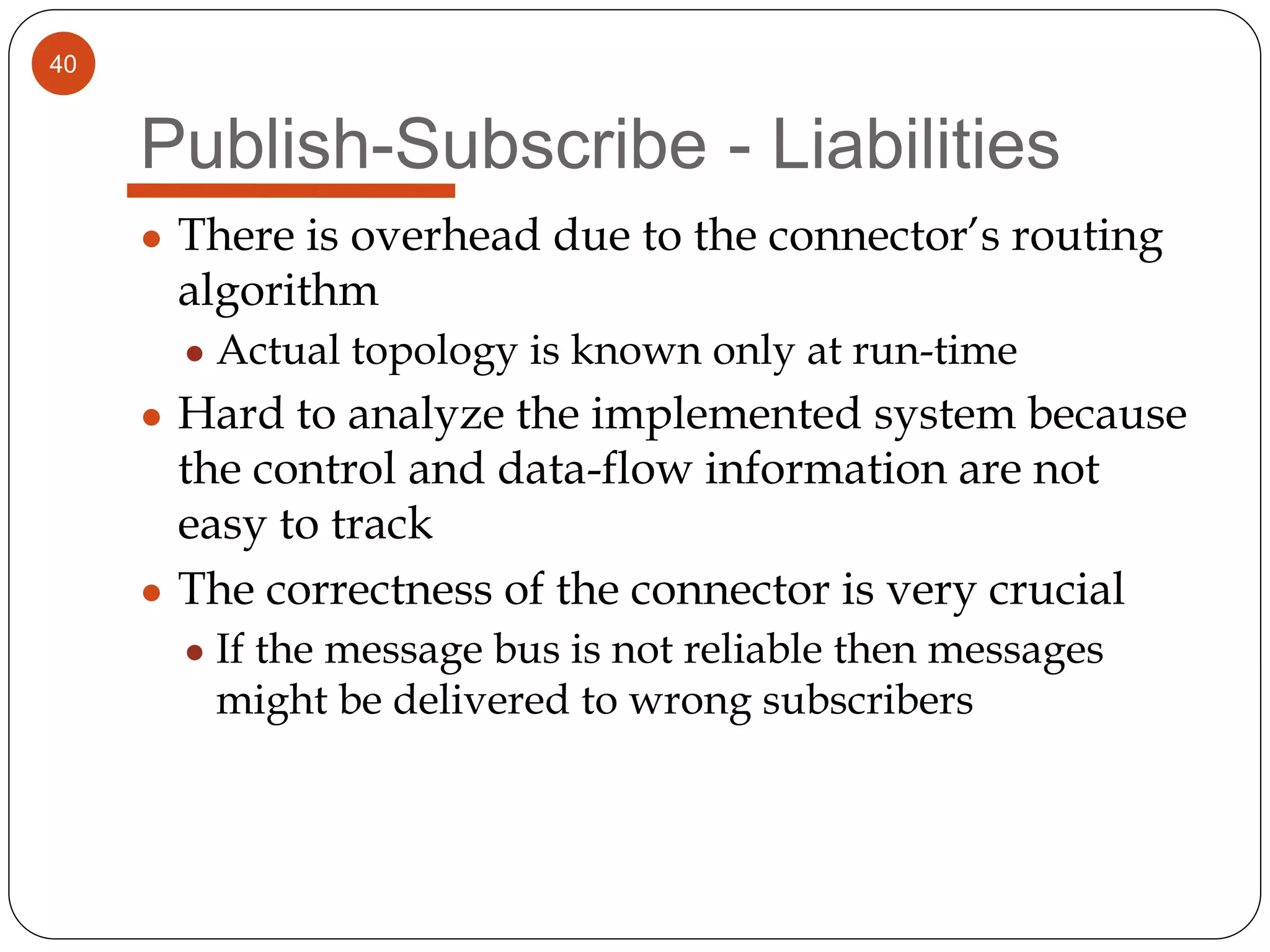
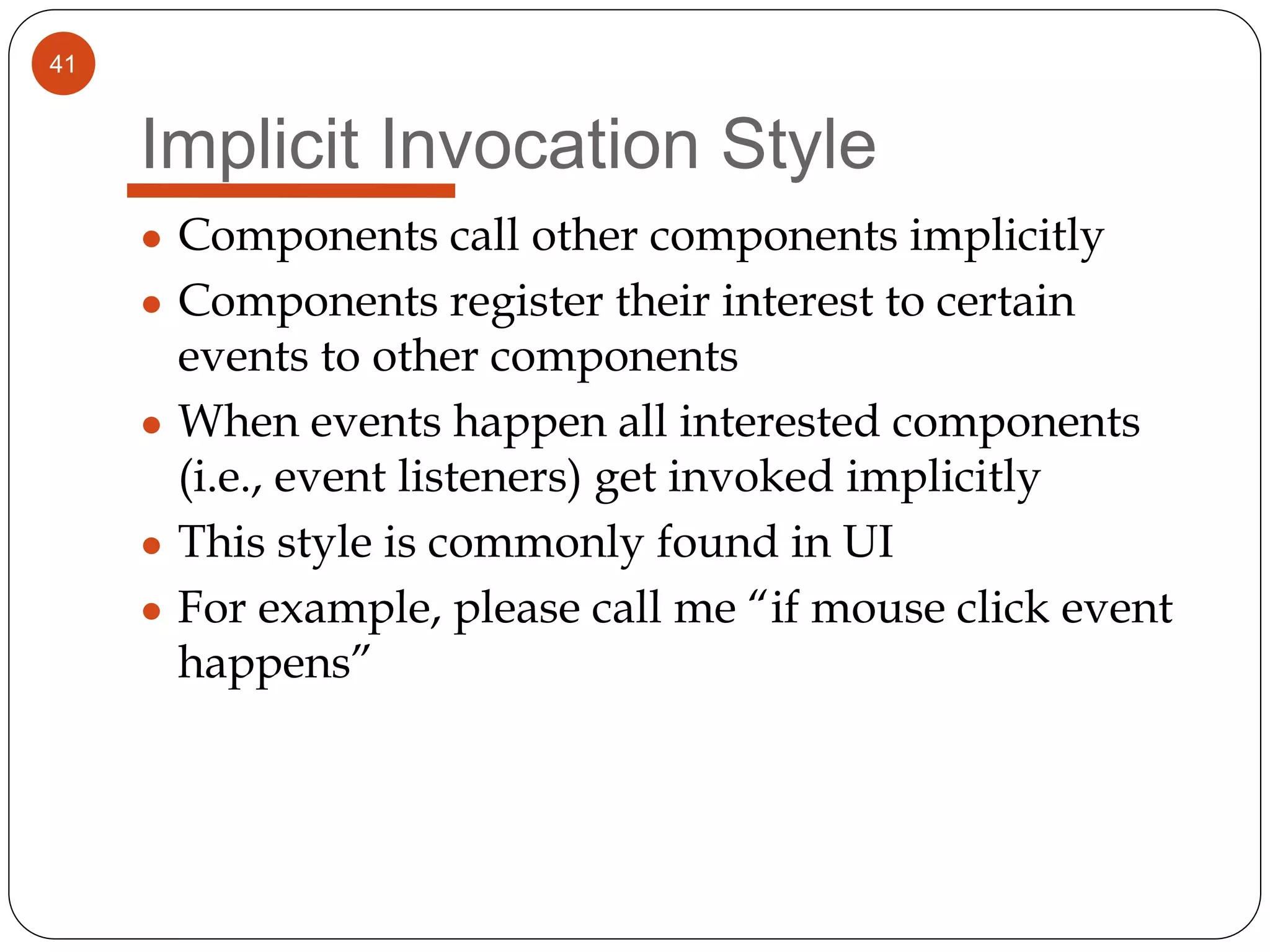
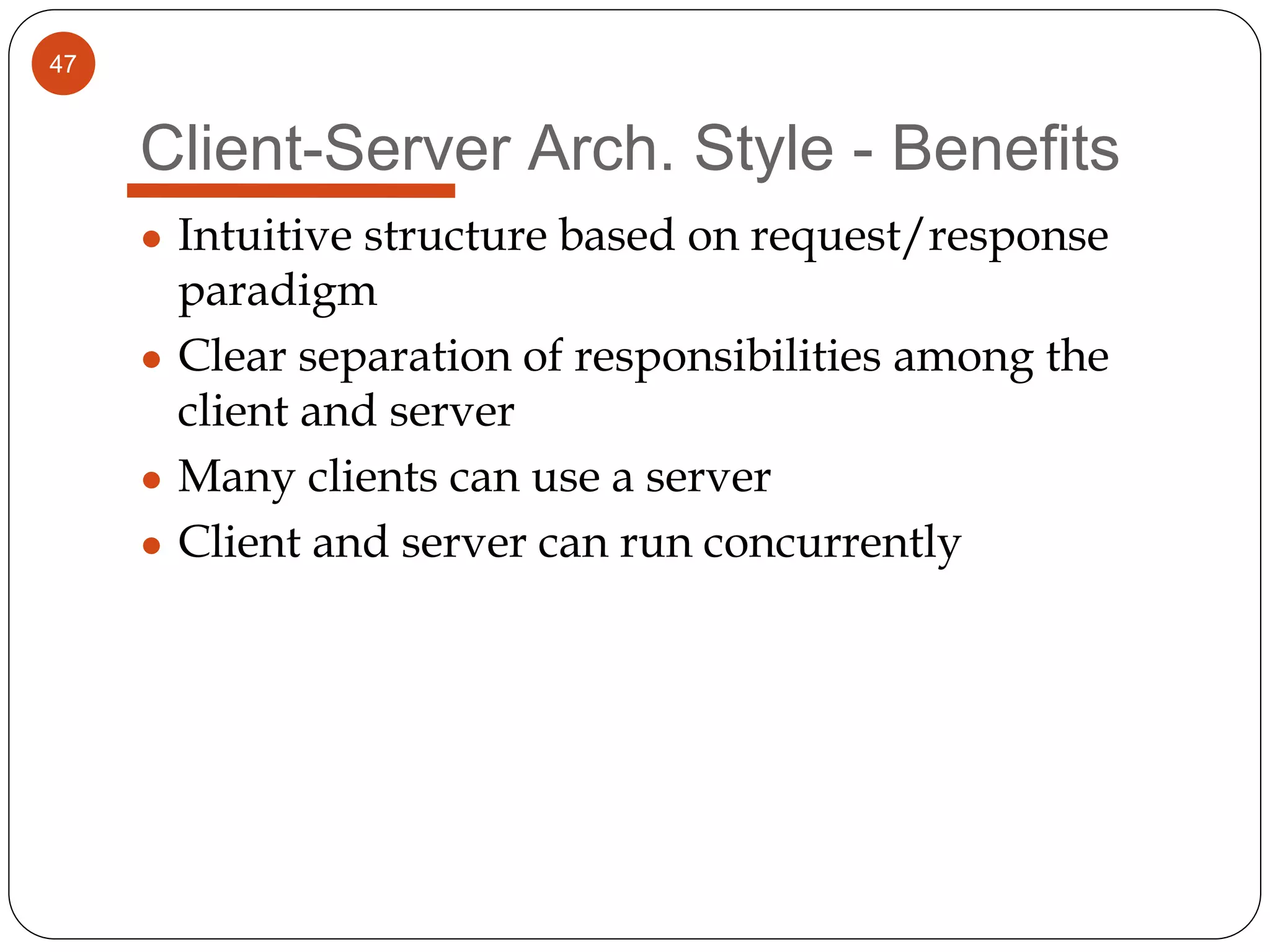
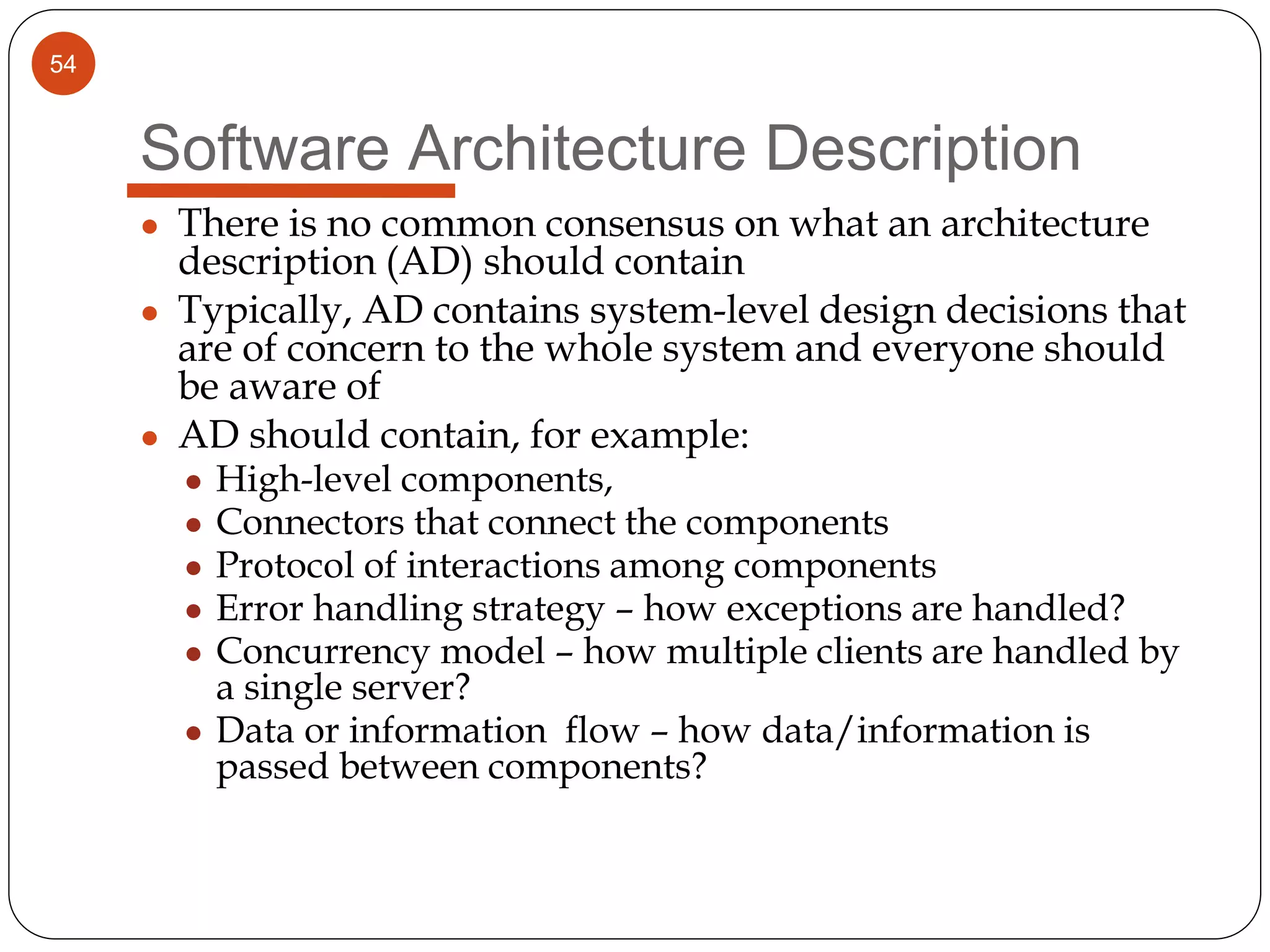
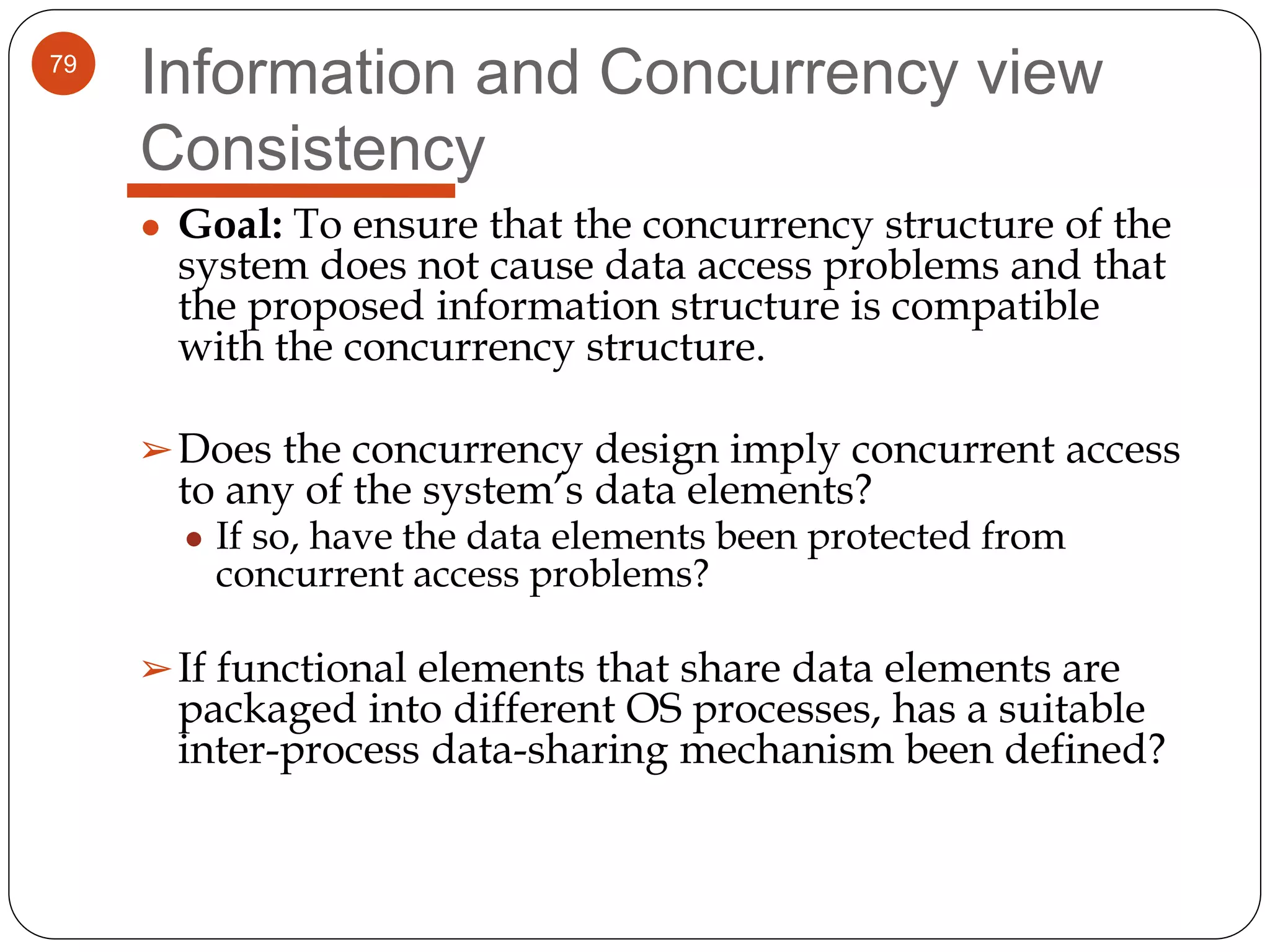
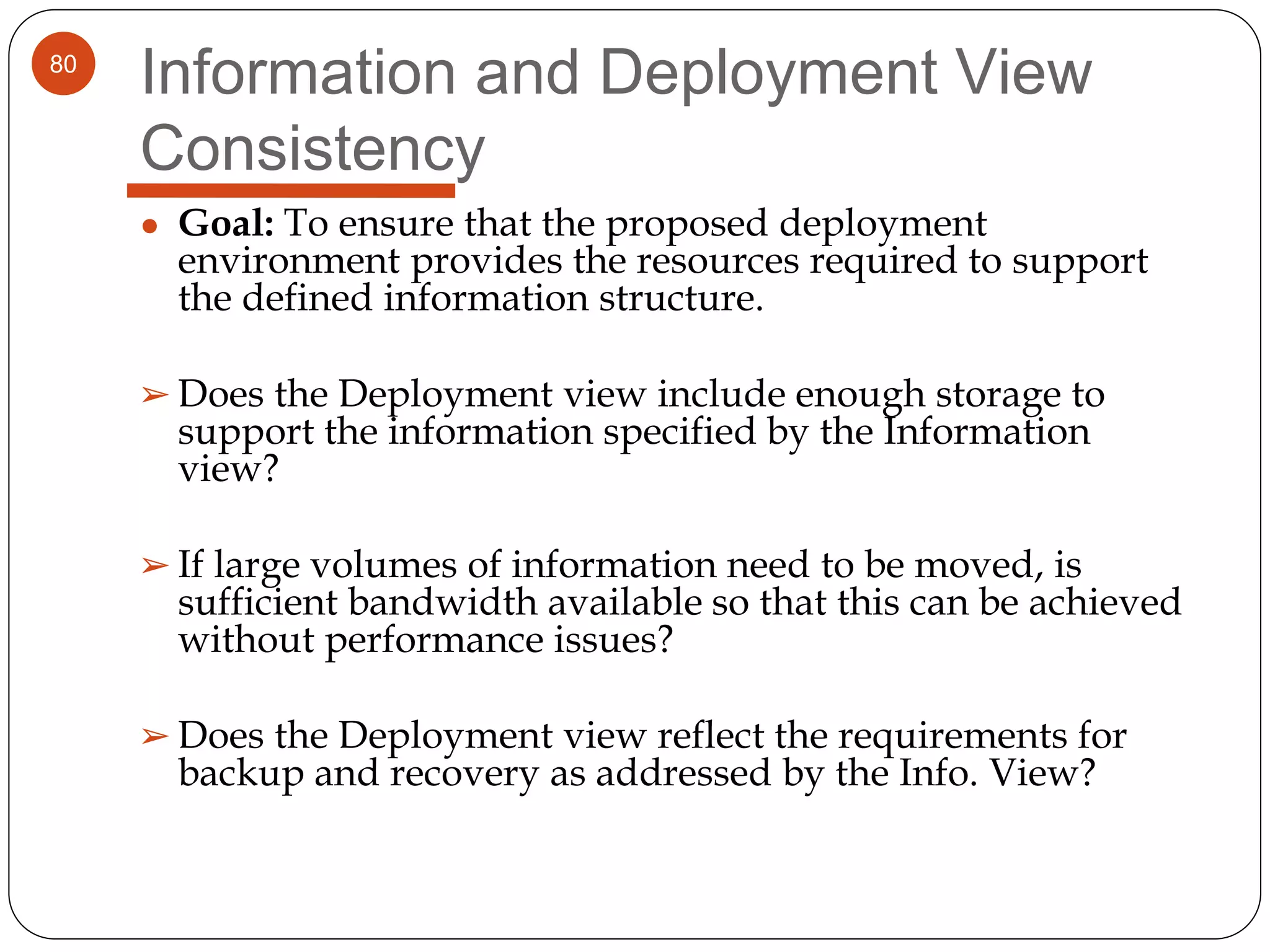
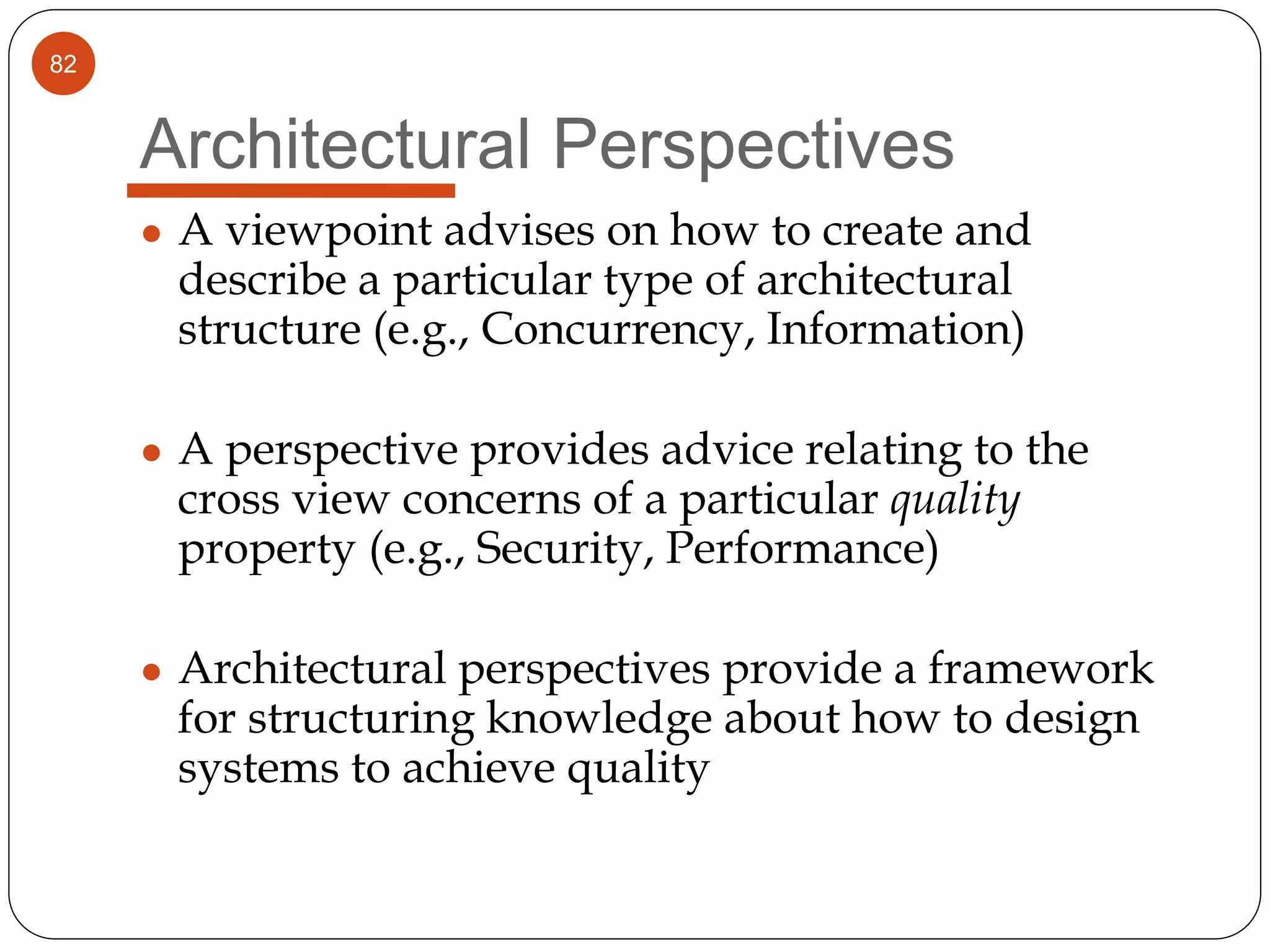
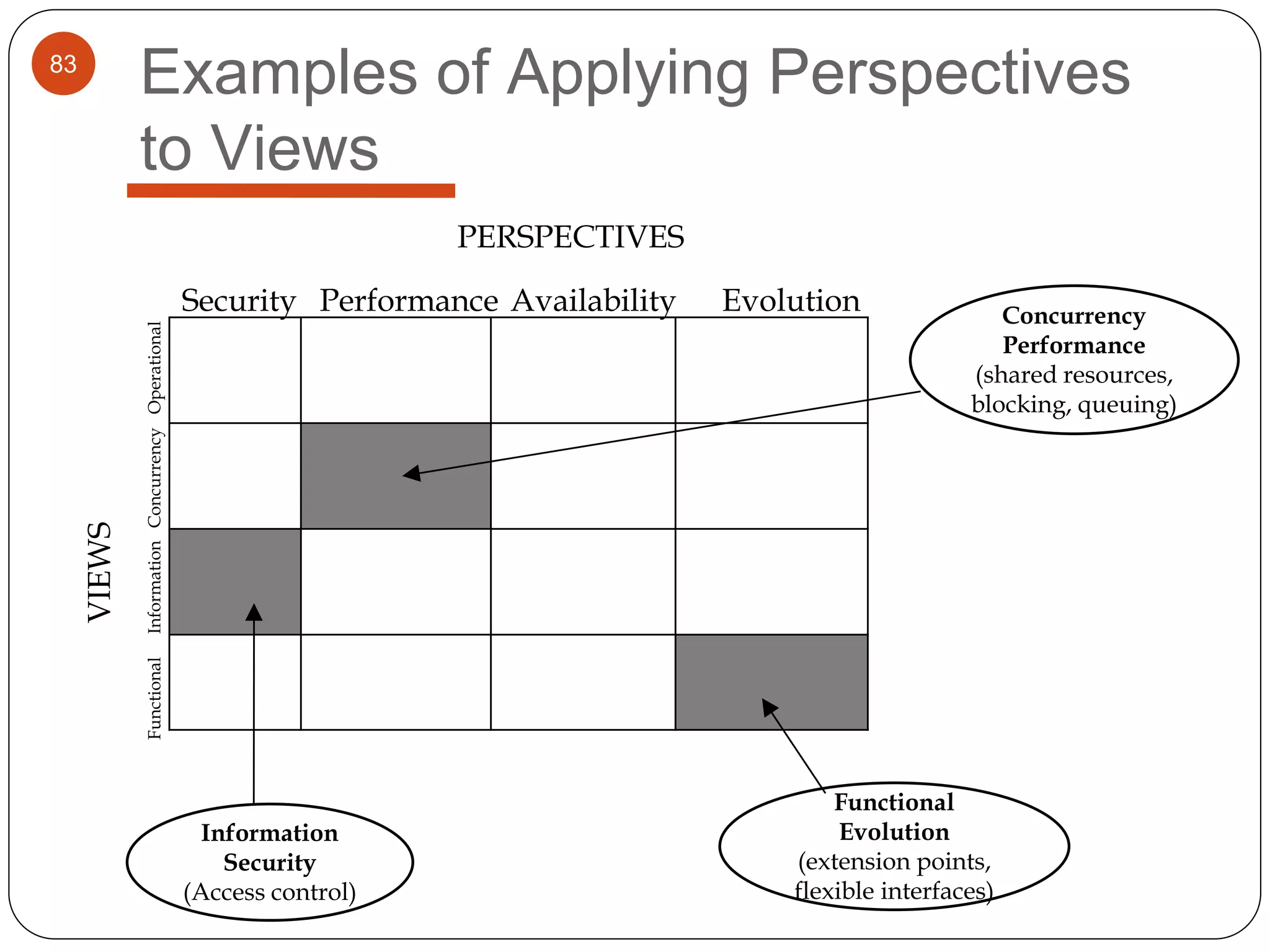
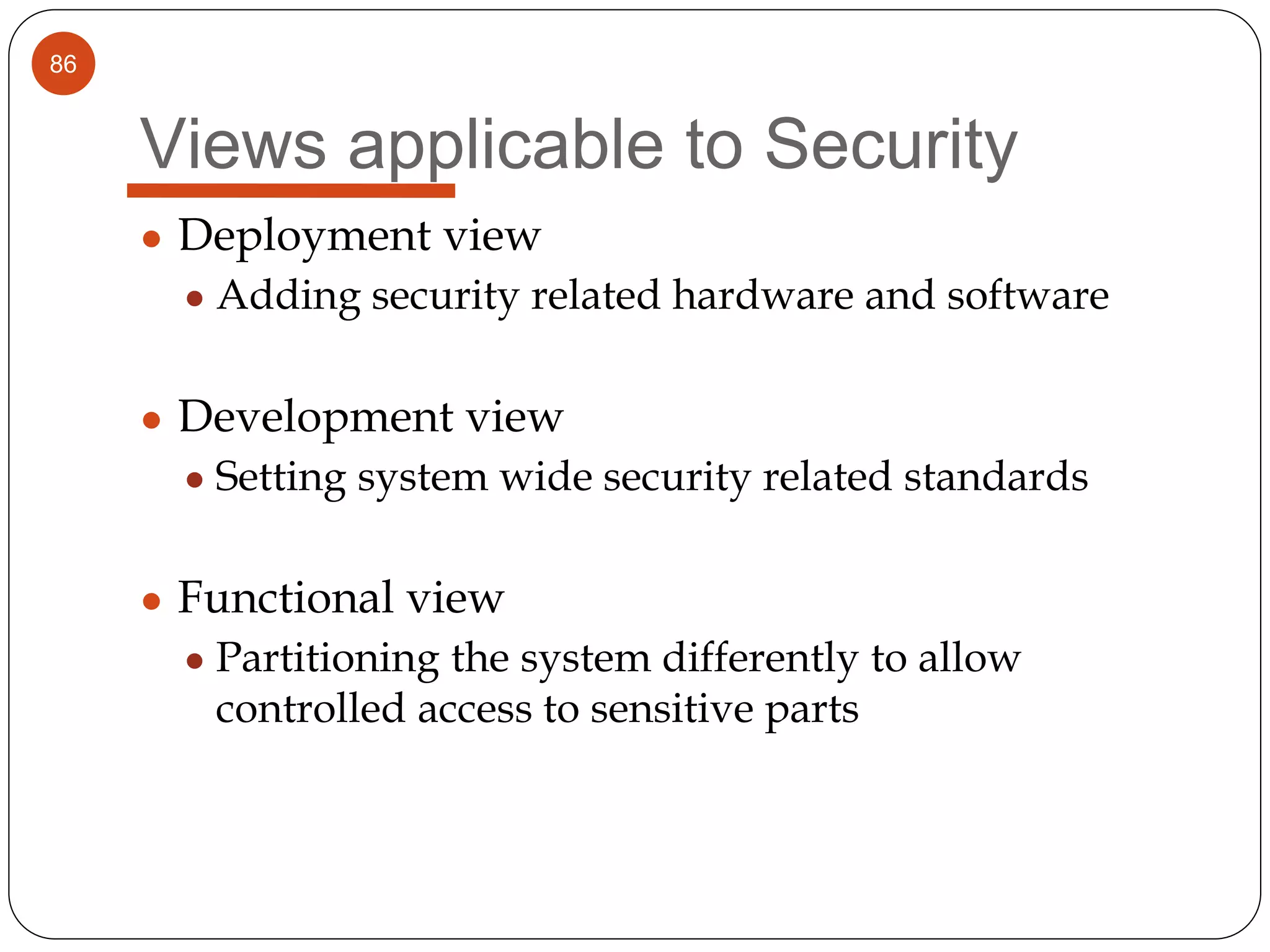
The document provides an overview of software architecture. It discusses software architecture versus design, architectural styles like layered and pipe-and-filter styles, software connectors like coordinators and adapters, and using architecture for project management, development and testing. Architectural styles from different domains like buildings are presented as analogies for software architecture styles. The benefits of architectural styles for explaining a system's structure and enabling development of system families are highlighted.




































![Using Perspectives
Analyse and
Understand Key
requirements
Create a Candidate
Architecture
Apply Perspectives Modify Architecture
Perform “Formal”
Architectural
Evaluation
(e.g., Scenario-based
methods ATAM,
SAAM)
[Unacceptable
properties]
[acceptable properties]](https://image.slidesharecdn.com/swalecture-171009012535/75/Software-Architecture-91-2048.jpg)