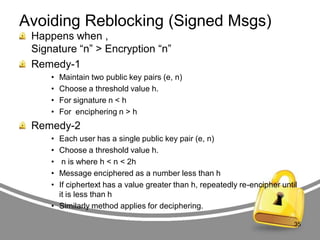
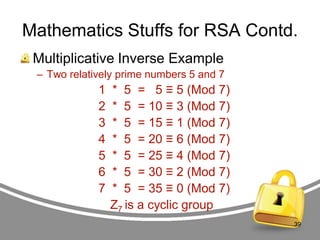
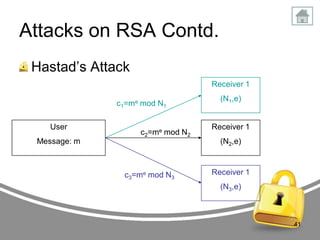
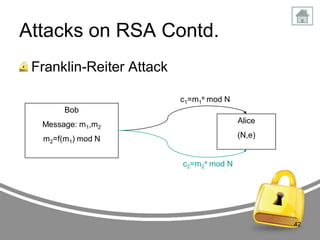
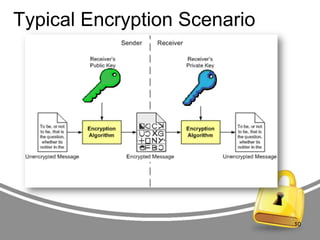
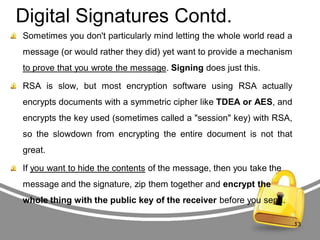
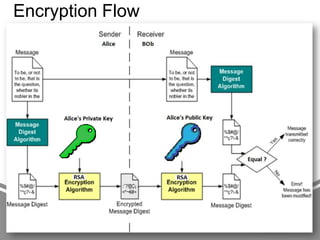
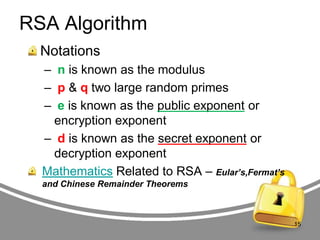
The document presents an in-depth analysis of RSA, a public-key cryptography method invented by Rivest, Shamir, and Adleman. It outlines the RSA algorithm, including the processes for key generation, encryption, and decryption, as well as the significance of digital signatures for authentication and integrity. The paper also examines security implications, potential attacks on RSA, and provides examples of its application in information security.







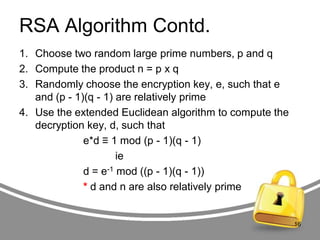
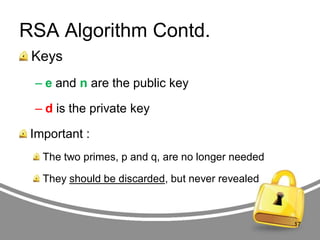
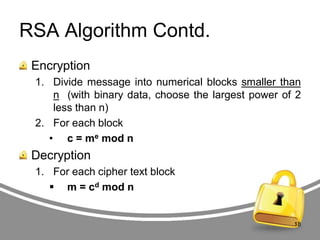
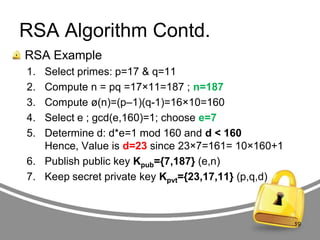
![RSA Algorithm Contd.
message „M‟= 88 (88<187)
Encryption: [c = me mod n]
• C = 887 mod 187 = 11
C = 11
Decryption: [m = cd mod n]
• M = 1123 mod 187 = 88
M = 88
If message is 8888 then ?
20](https://image.slidesharecdn.com/presentation-rsa-131024073333-phpapp01/85/Presentation-about-RSA-20-320.jpg)