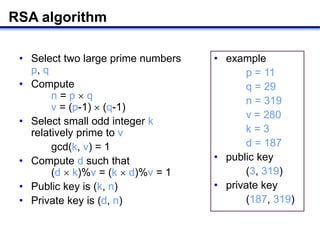
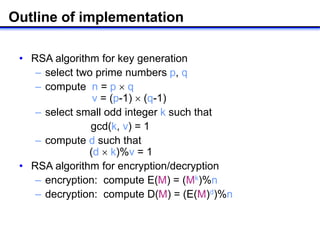
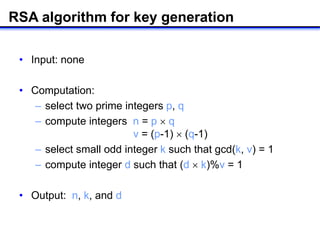
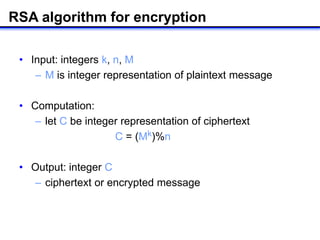
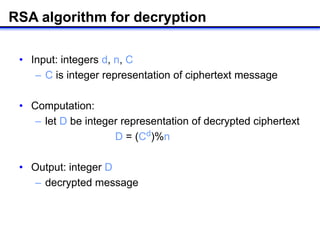
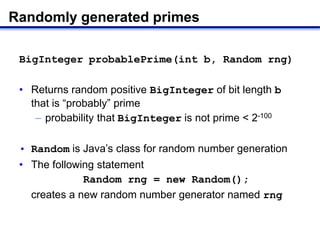
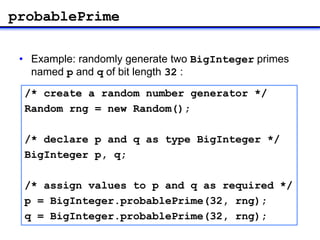
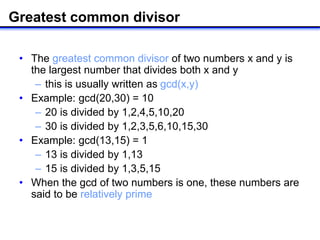
The document describes how to implement RSA encryption in Java using the BigInteger class. It discusses:
1) Generating random prime numbers p and q using BigInteger's probablePrime method.
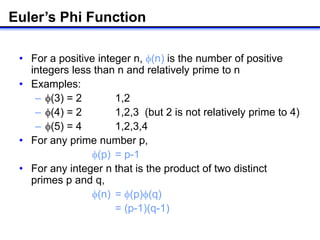
2) Computing n=p*q and φ(n)=(p-1)*(q-1) to get the public modulus and Euler's totient function.
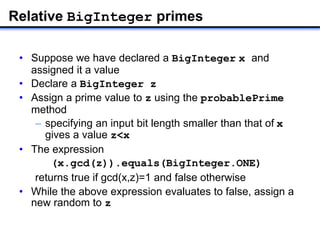
3) Finding a random integer k that is relatively prime to φ(n) using gcd.
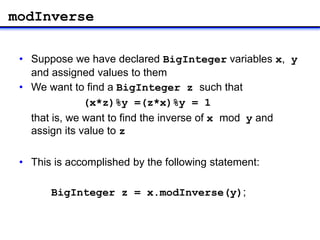
4) Computing the private exponent d as k's modular inverse modulo φ(n) using modInverse.