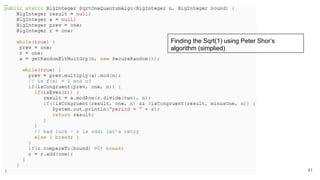
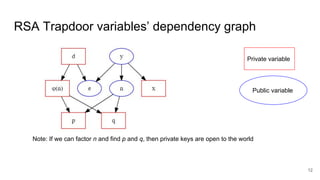
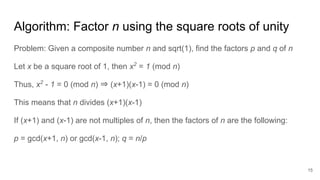
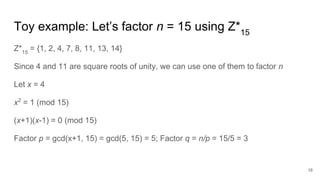
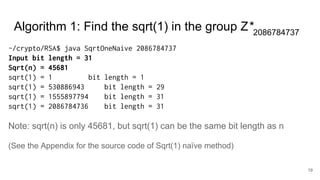
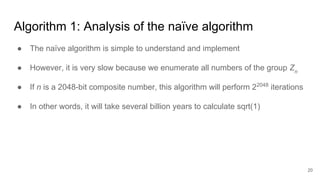
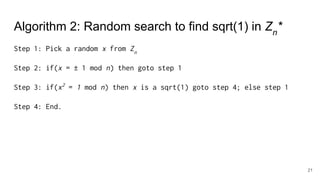
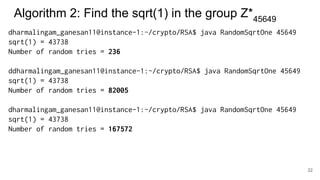
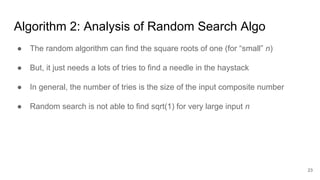
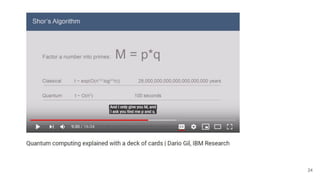
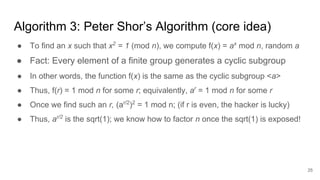
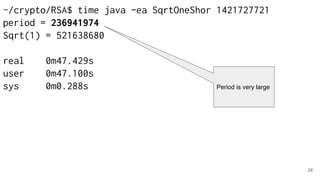
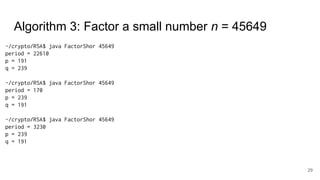
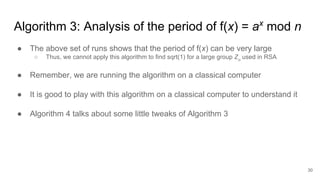
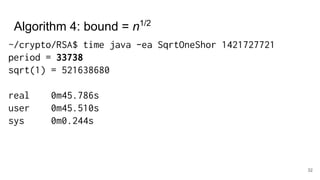
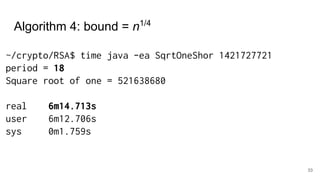
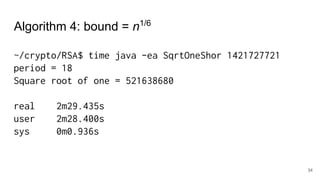
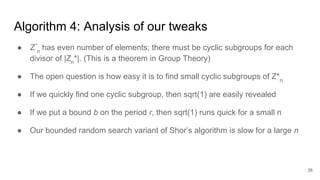
The document discusses breaking RSA encryption by computing square roots of unity using classical computing methods and Peter Shor’s quantum algorithm. It introduces various algorithms for finding square roots of unity in finite groups, their mathematical background, and potential applications in cryptography. Additionally, it includes a demonstration of these algorithms and their effectiveness in factoring composite numbers.


















![39
import java.math.BigInteger;
import java.security.SecureRandom;
public class SqrtOneNaive implements IBigIntConstants
{
public static void main(String[] args)
{
/* Error handling is omitted */
BigInteger n = new BigInteger(args[0]);
BigInteger x = zero;
while(x.compareTo(n) <= 0) {
// is square(x) = 1 (mod n)?
if(x.multiply(x).mod(n).equals(one)) {
System.out.println(x + " is the square root of one ");
}
x = x.add(one);
}
}
}
Implementation of naïve Sqrt(1) algorithm](https://image.slidesharecdn.com/computingthesquarerootsofunitytobreakrsa-190330042902/85/Computing-the-Square-Roots-of-Unity-to-break-RSA-using-Quantum-Algorithms-39-320.jpg)
![40
public static void main(String[] args)
{
BigInteger n = new BigInteger(args[0]); // Error handling code is removed
BigInteger x;
while(true) {
// Pick a random element from Zn
x = BigIntUtil.getRandomElt(n, new SecureRandom());
// We don't want non-trivial roots '1' or '-1'.
// If x = -1 (mod n) or x = 1 (mod n), then we have to restart.
if(x.add(one).mod(n).equals(zero) ||
x.subtract(one).mod(n).equals(zero)) { continue; }
if(x.multiply(x).mod(n).equals(one)) {
System.out.println(x + " is the square root of one ");
System.out.println("Number of random tries = " + counter);
break;
}
}
}
Implementation of random Sqrt(1) algorithm](https://image.slidesharecdn.com/computingthesquarerootsofunitytobreakrsa-190330042902/85/Computing-the-Square-Roots-of-Unity-to-break-RSA-using-Quantum-Algorithms-40-320.jpg)