The document discusses primality testing, which determines whether a number is prime, highlighting its importance in cryptography, particularly the RSA algorithm. Various techniques such as naive algorithms, Fermat's theorem, and the Rabin-Miller probabilistic primality test are presented, along with their time complexities and examples. It also details the RSA encryption and decryption process using prime numbers and their derived keys.







![Algorithms (Cont.)
Rabin-Miller’s Probabilistic Primality Algorithm
The Rabin-Miller’s Probabilistic Primality test was
by Rabin, based on Miller’s idea. This algorithm
provides a fast method of determining of primality
of a number with a controllably small probability
of error.
Given (b, n), where n is the number to be tested
for primality, and b is randomly chosen in [1, n-1].
Let n-1 = (2^q)*m, where m is an odd integer.
B^m = 1(mod n)
∃i∈[0, q-1] such that b^(m2)^i = -1(mod n)](https://image.slidesharecdn.com/primality-170506130138/85/Primality-8-320.jpg)



![RSA in action (cont.):
2. Set public key to send the message.
public key (e, n)
such that: gcd(φ(n), e) = 1; [1<e< φ(n)]
sender uses public key to encrypt the
message before sending it to the
recipient.](https://image.slidesharecdn.com/primality-170506130138/85/Primality-12-320.jpg)

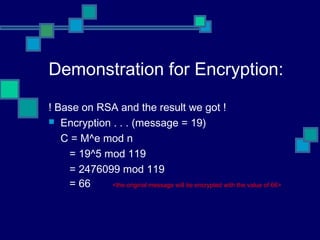
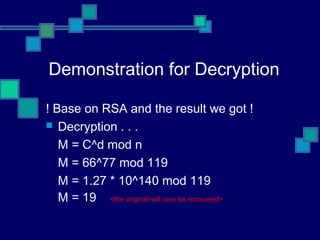
![Demonstration for RSA:
Pick 2 primes: p=7, q=17
n = p*q
n = 119
Compute:
φ(n) = φ(119)
= φ(7*17)
= φ(7) * φ(17)
= 6 * 16
= 96
Find e such that gcd(φ(n), e) = 1; [1<e< φ(n)]
gcd(e, 96) = 1
e = 5 ⇒ public key(e, n) ⇐
Find d such that ed = 1mod φ(n)
5d = 1mod96
5d = 96 * k +1, where k is some constant
5d = 96 * 4 + 1, assume k = 4
5d = 385
d = 77 ⇒ private key(d, n) ⇐](https://image.slidesharecdn.com/primality-170506130138/85/Primality-14-320.jpg)