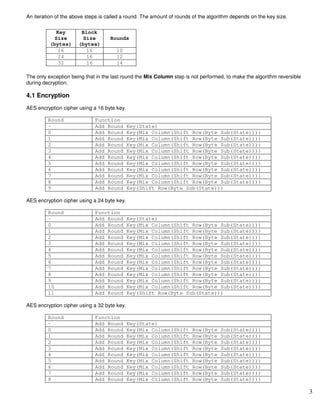
The document provides an overview of the Advanced Encryption Standard (AES) algorithm. It defines key terms like block, state, and XOR used in AES. It then describes the AES algorithm which works by repeating rounds that include byte substitution, shifting rows, mixing columns, and adding a round key. The number of rounds depends on the key size, being 10 for a 16-byte key and 14 for a 32-byte key. Encryption and decryption are similar processes performed in reverse order.