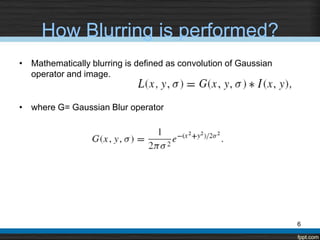
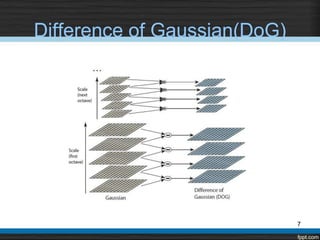
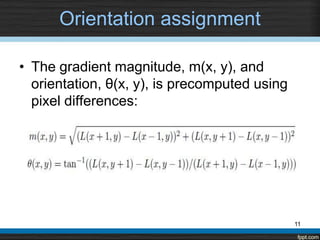
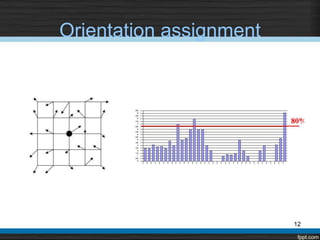
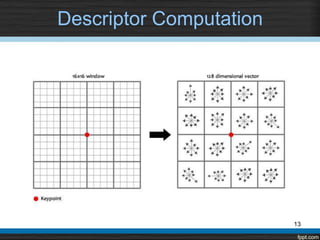
The document describes using the Scale Invariant Feature Transform (SIFT) algorithm for sub-image matching. It discusses rejecting the chain code algorithm and instead using SIFT. It then explains the various steps of SIFT including creating scale-space and Difference of Gaussian pyramids, extrema detection, noise elimination, orientation assignment, descriptor computation, and keypoints matching.