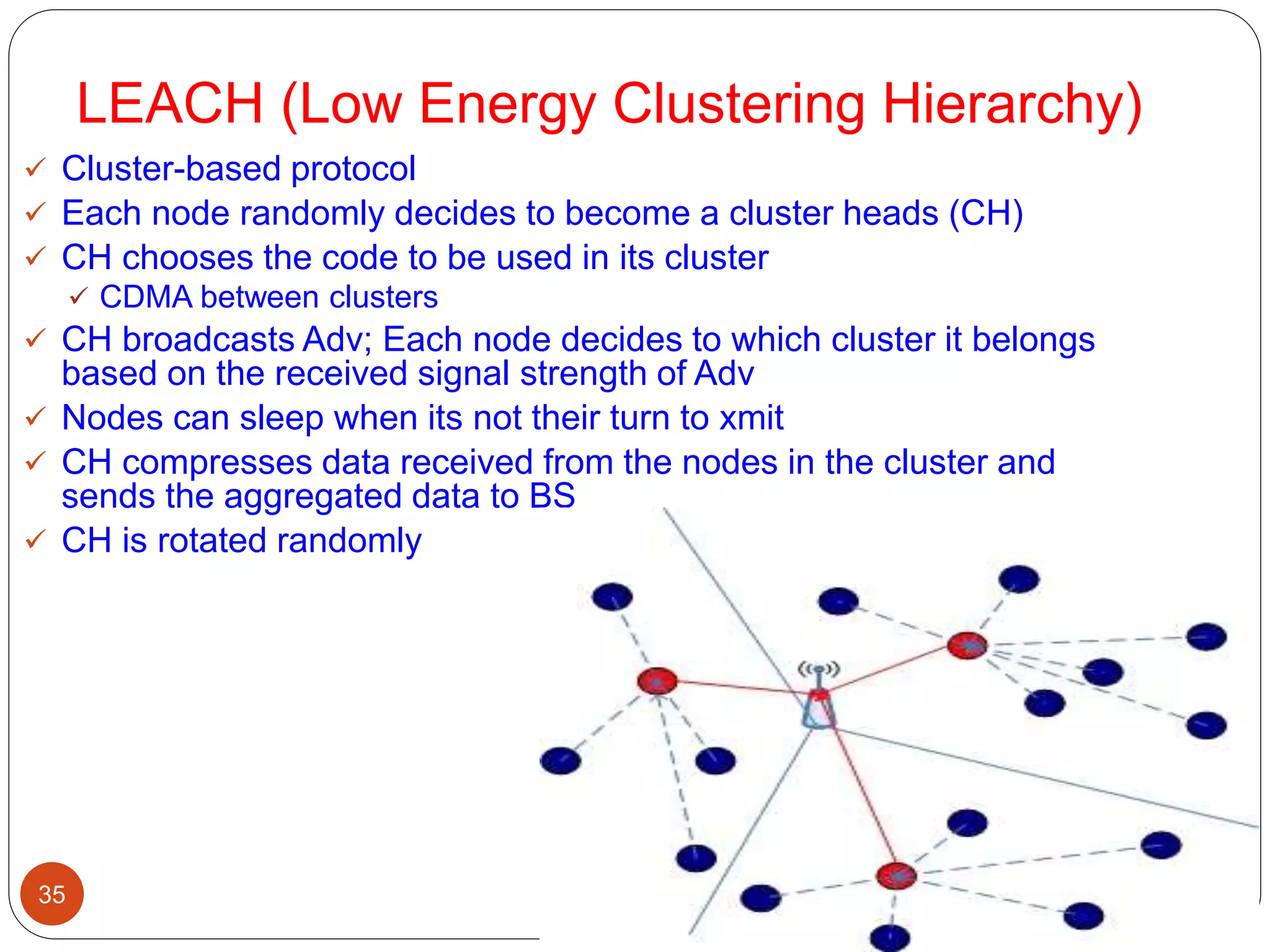
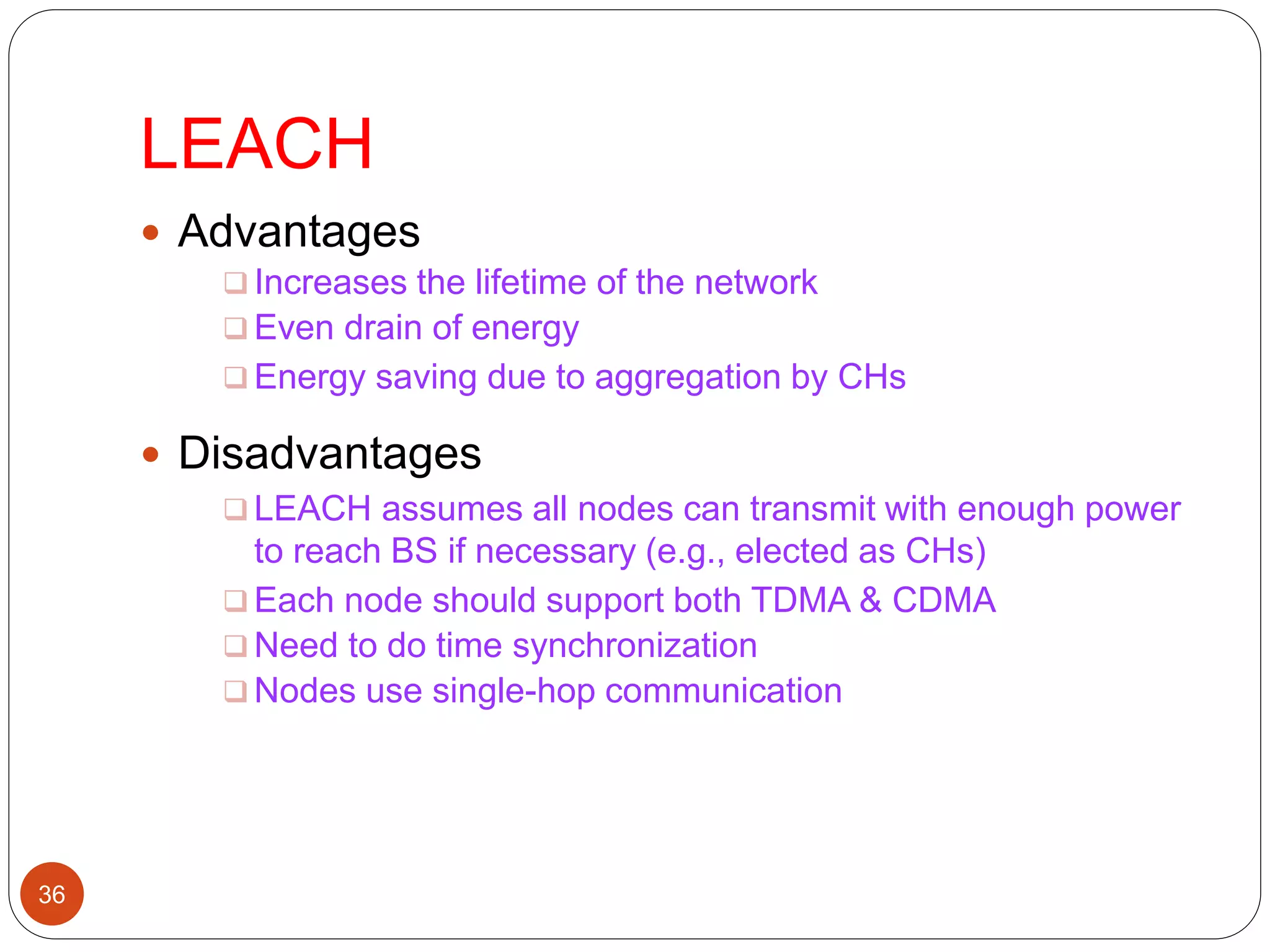
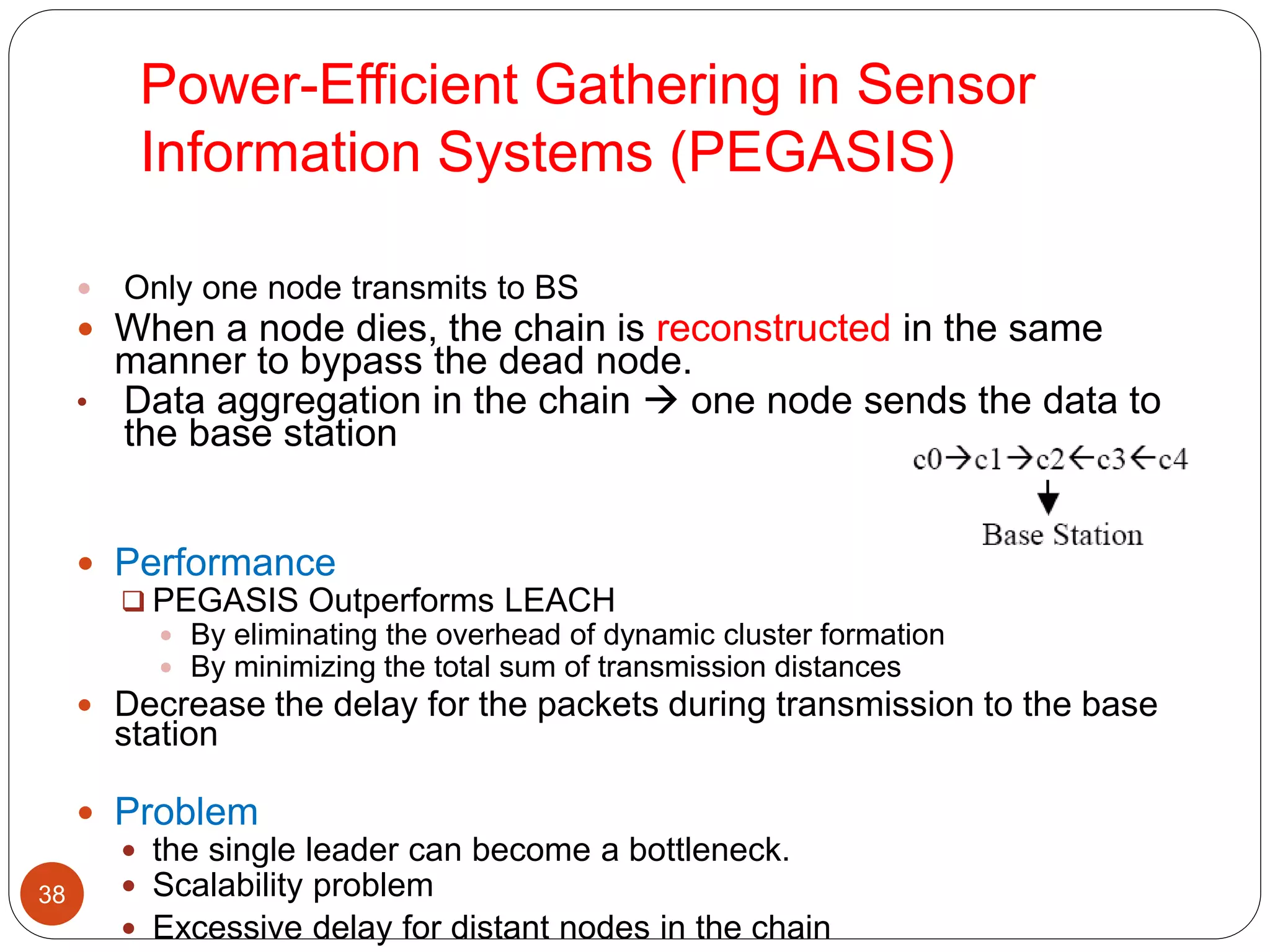
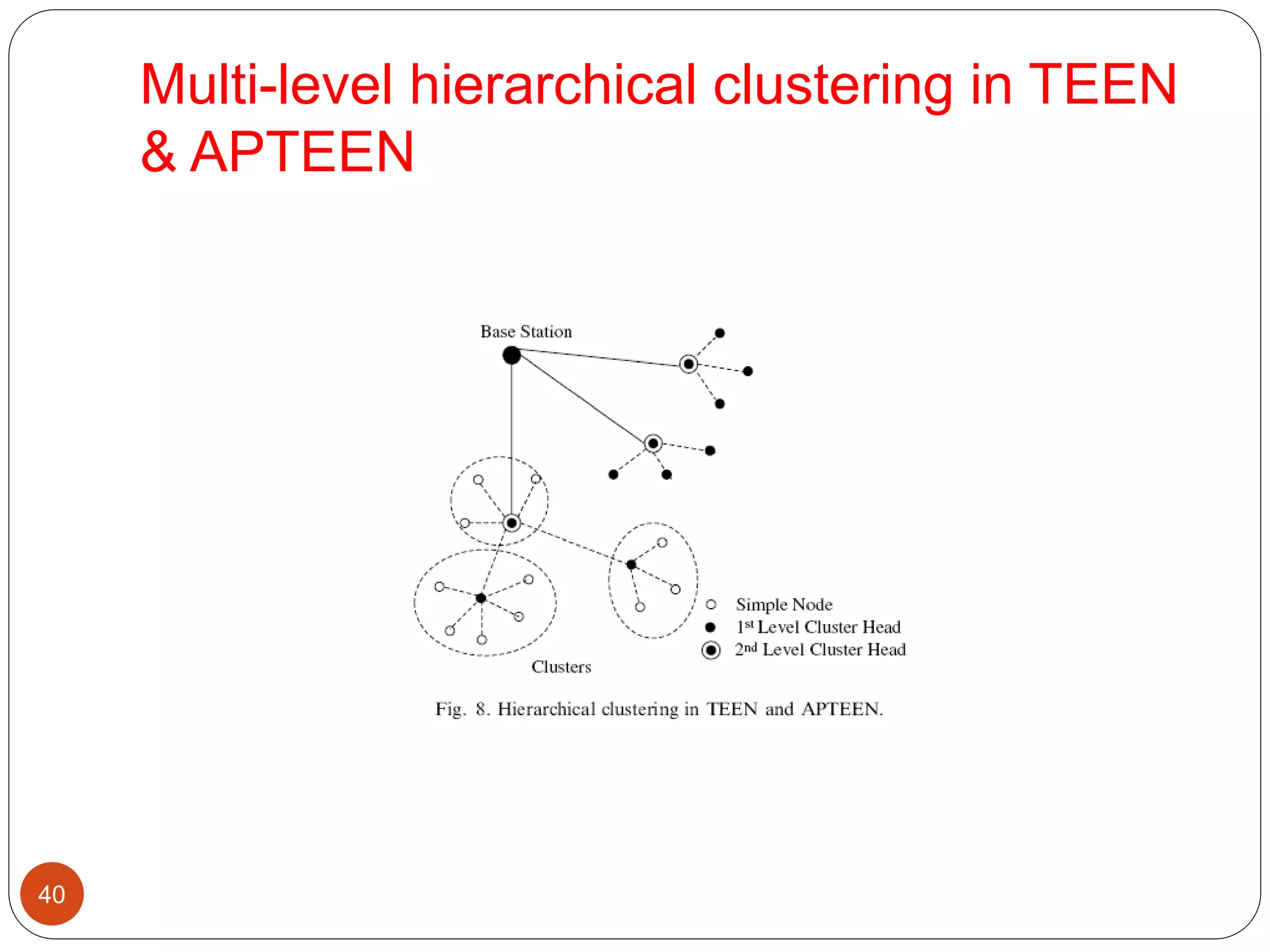
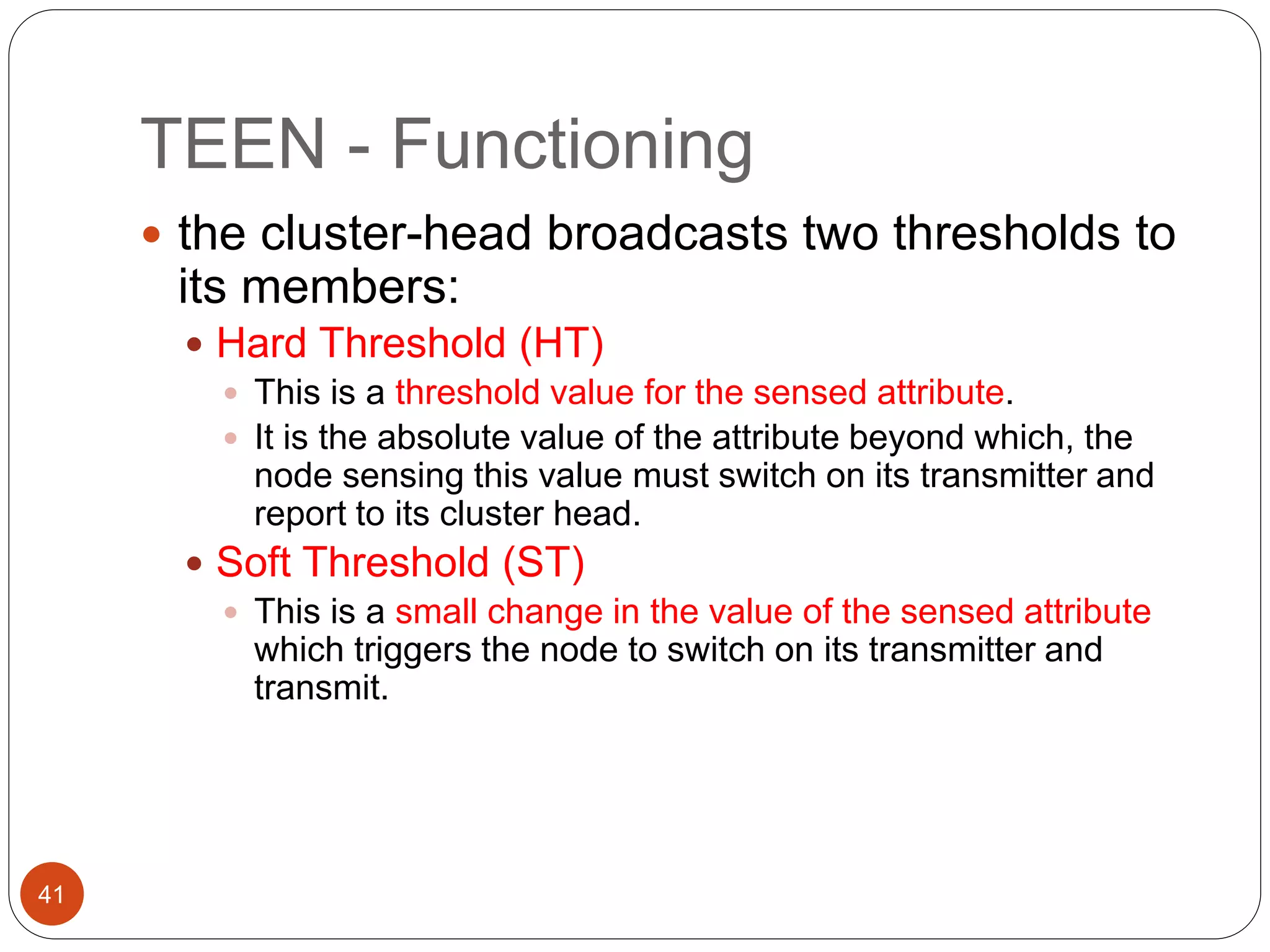
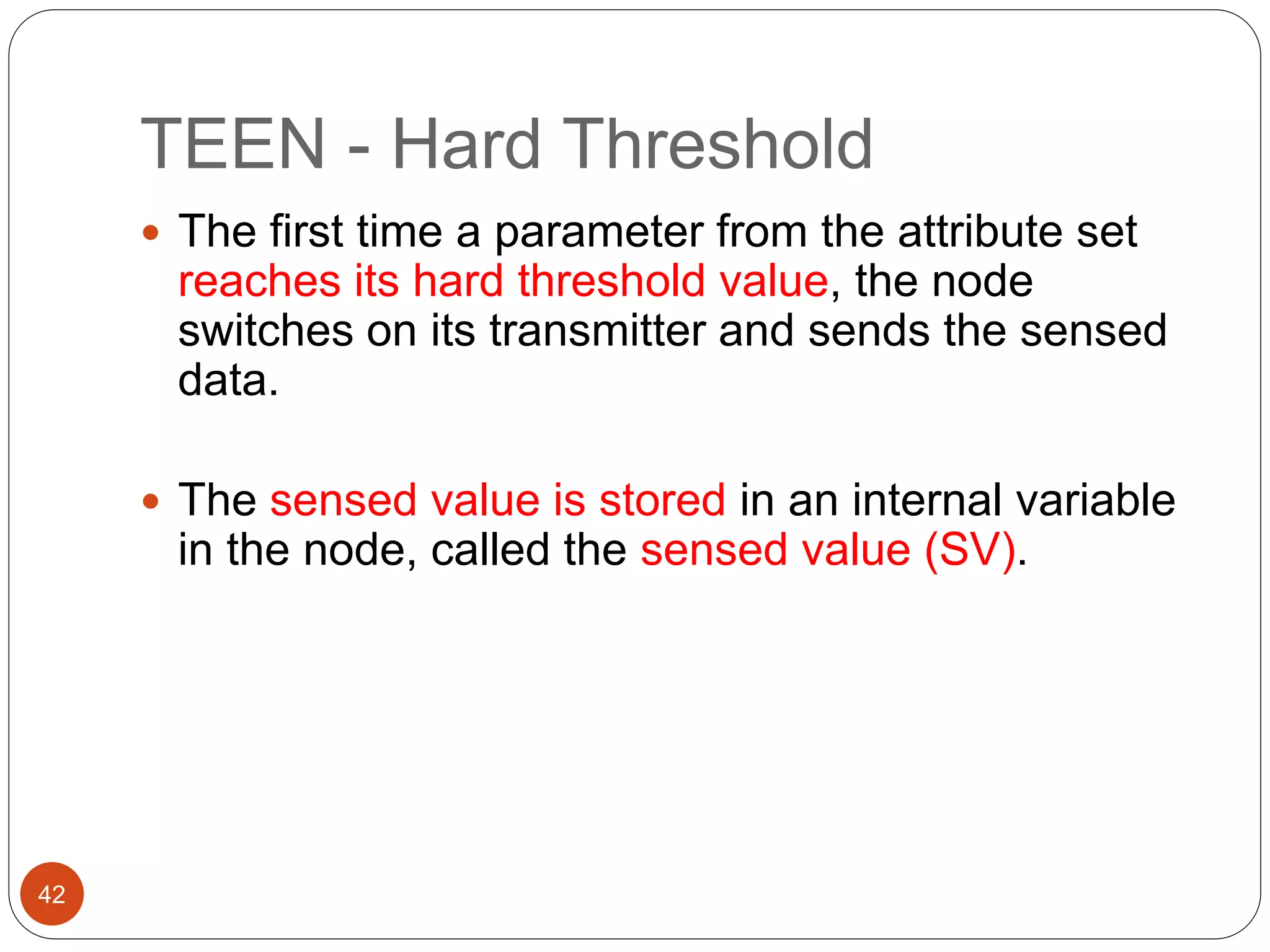
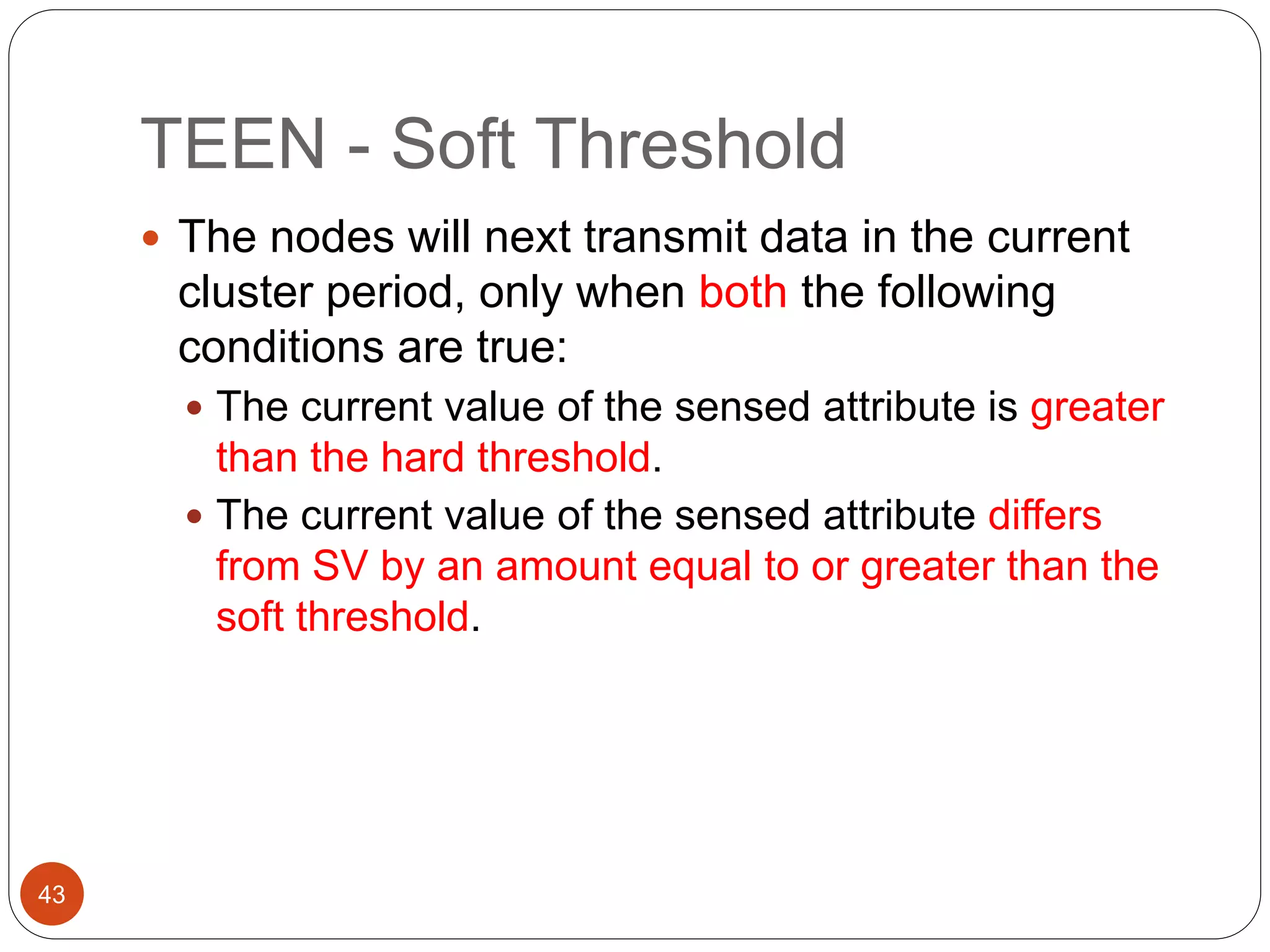
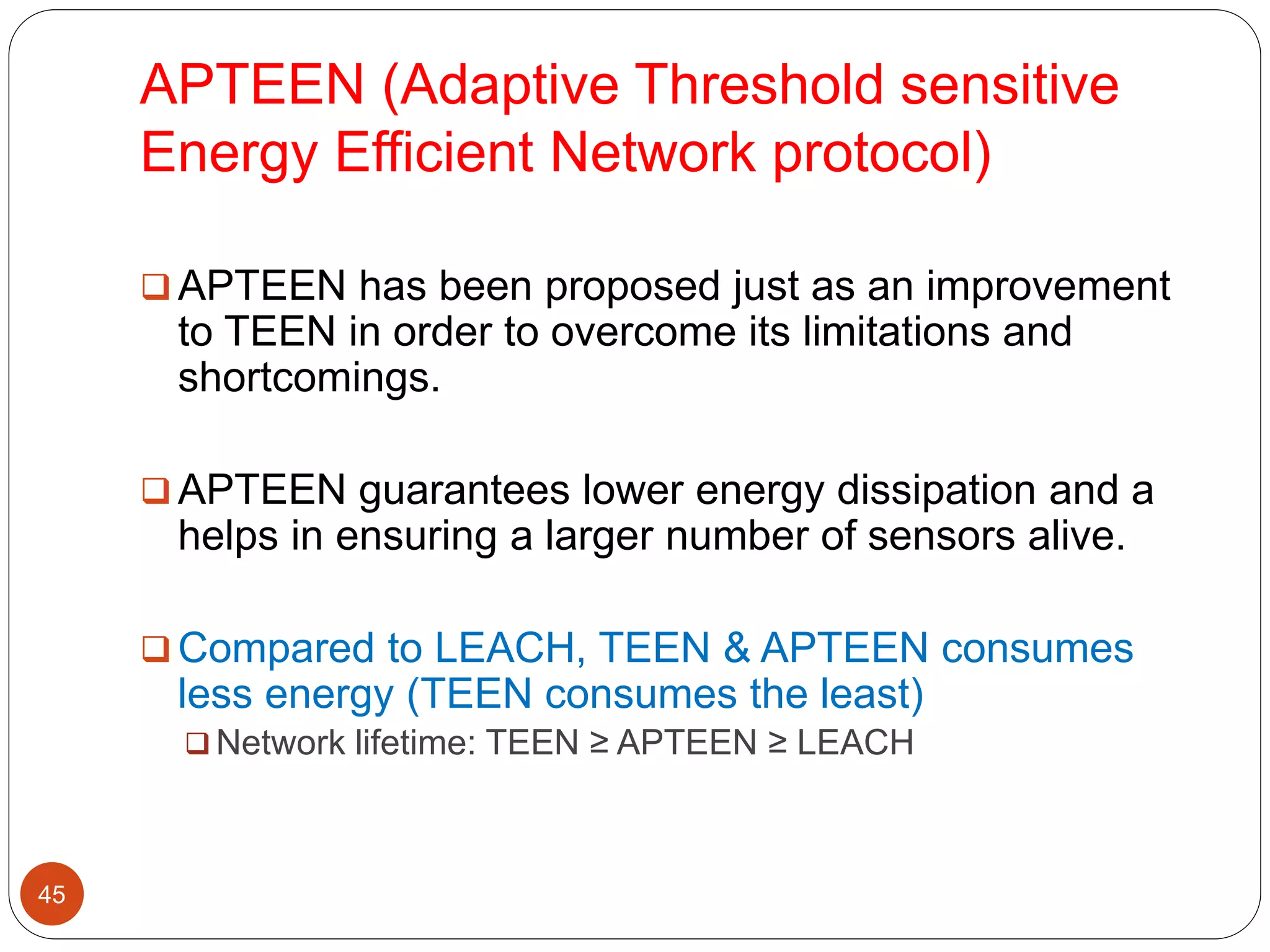
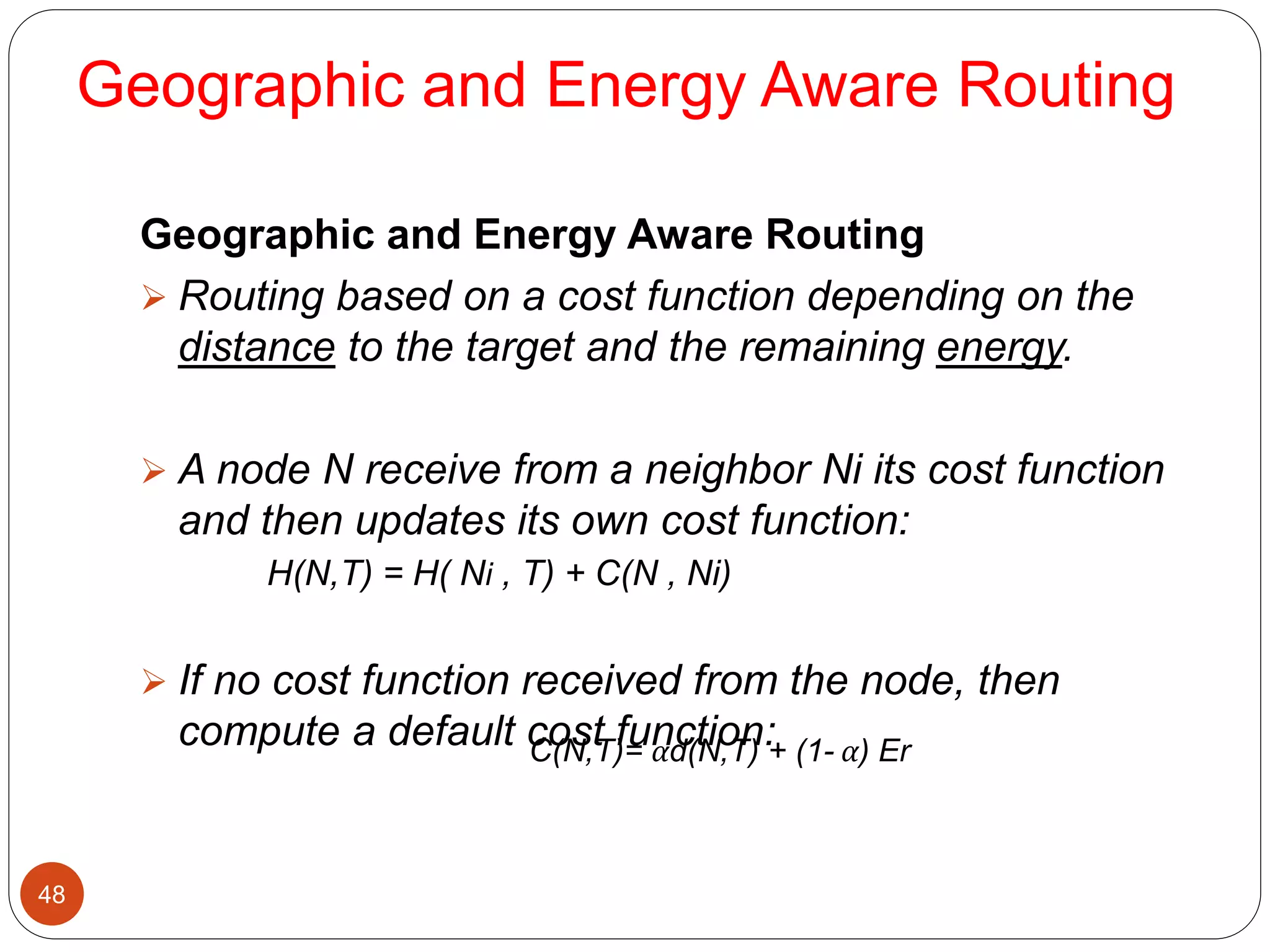
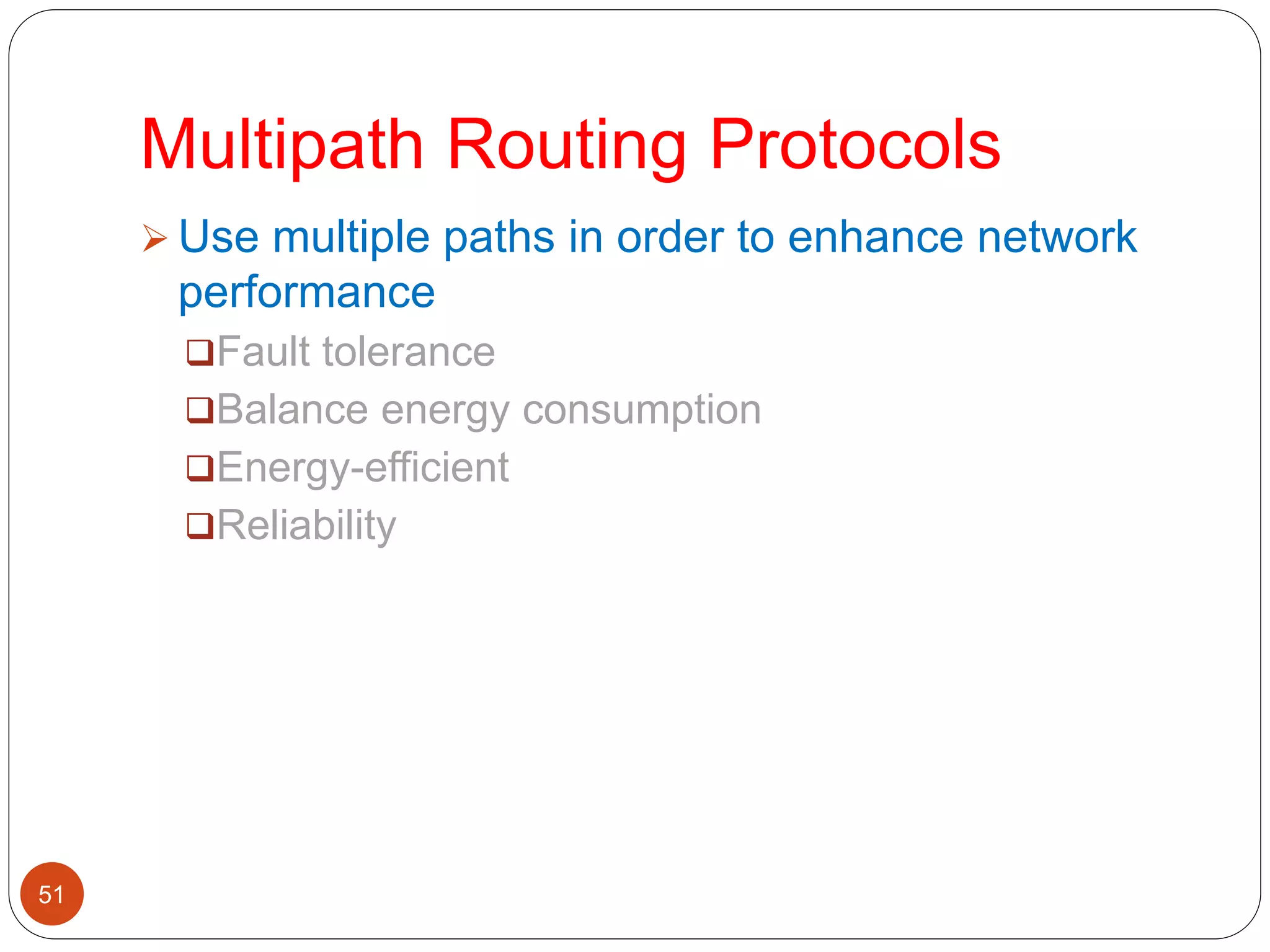
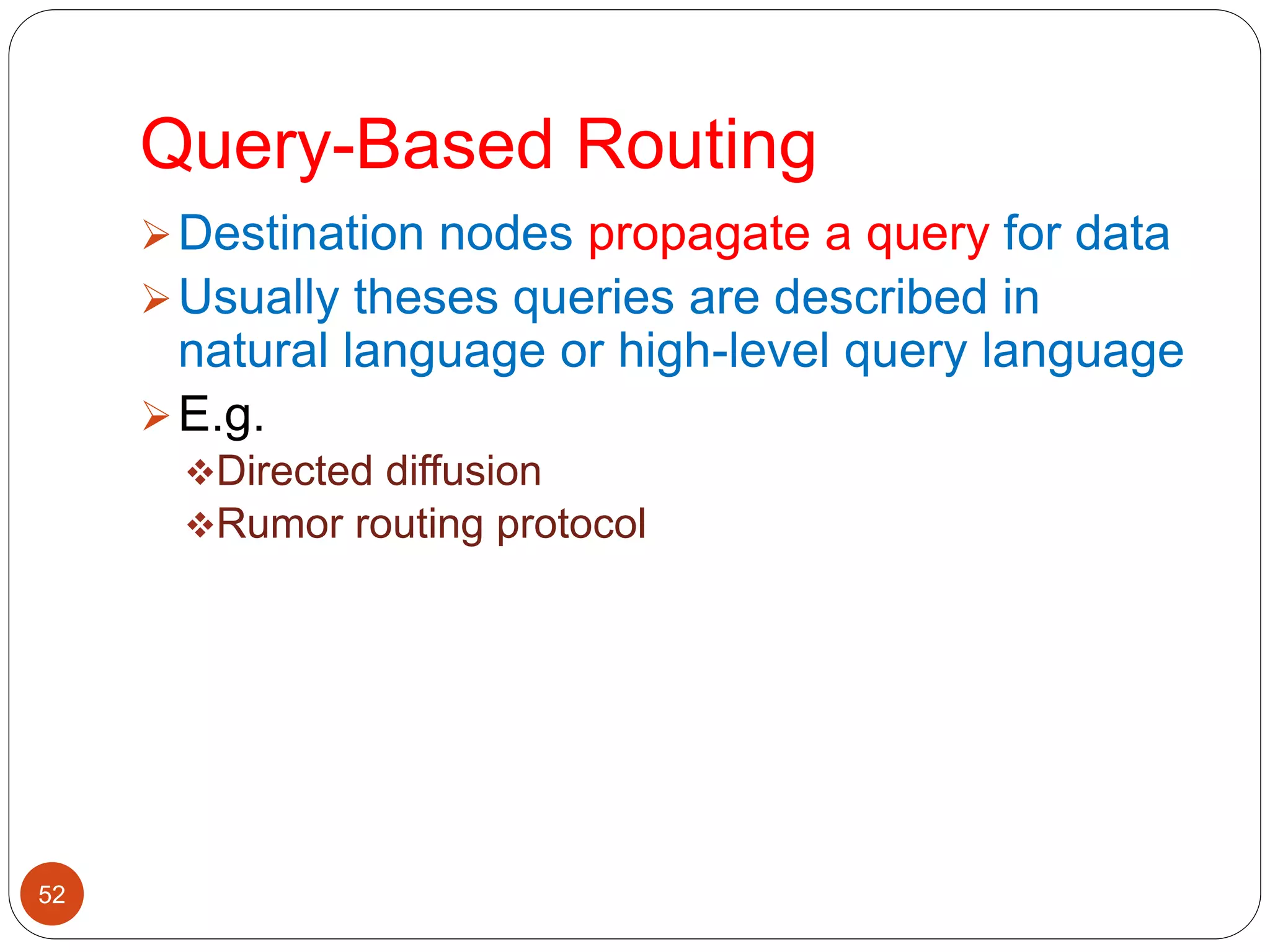
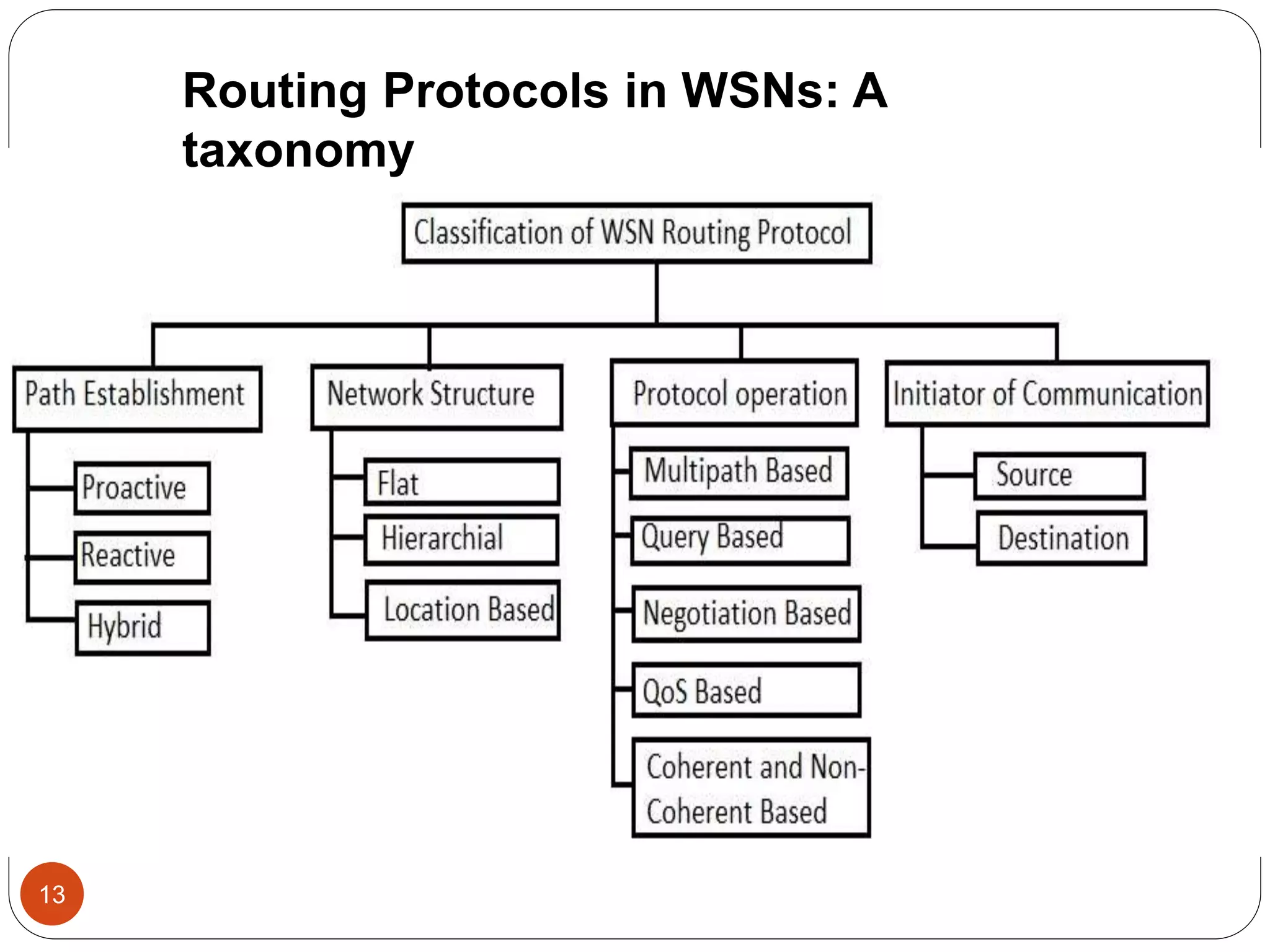
This document discusses routing protocols in wireless sensor networks. It begins with an introduction to routing challenges in WSNs such as limited energy, processing, and storage in sensor nodes. It then covers different routing techniques including flat routing protocols like SPIN, directed diffusion, and rumor routing. Hierarchical routing protocols discussed include LEACH, PEGASIS, TEEN, and APTEEN. Finally, it briefly mentions location-based routing and the GEAR protocol.





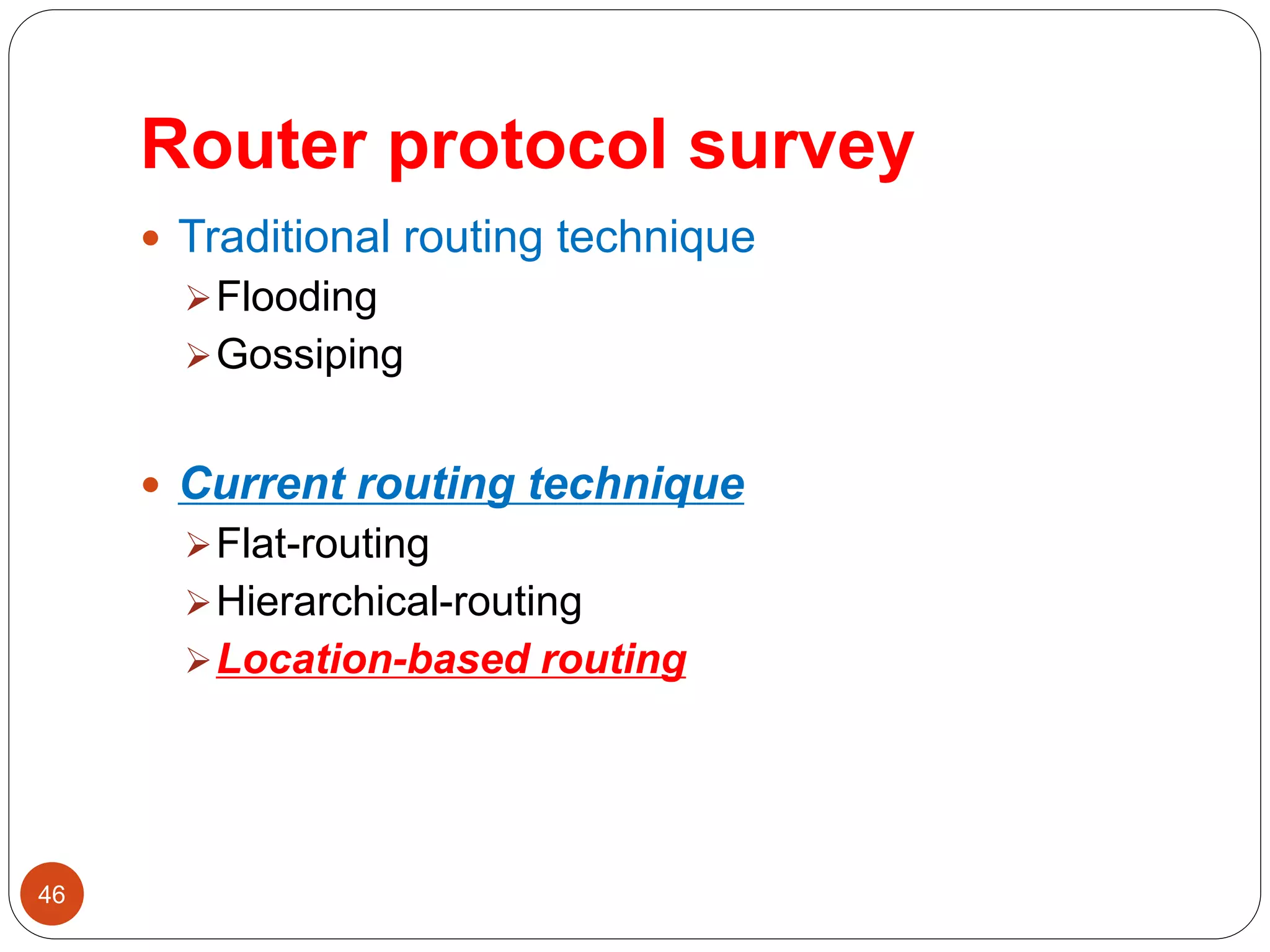
![Routing protocol survey
15
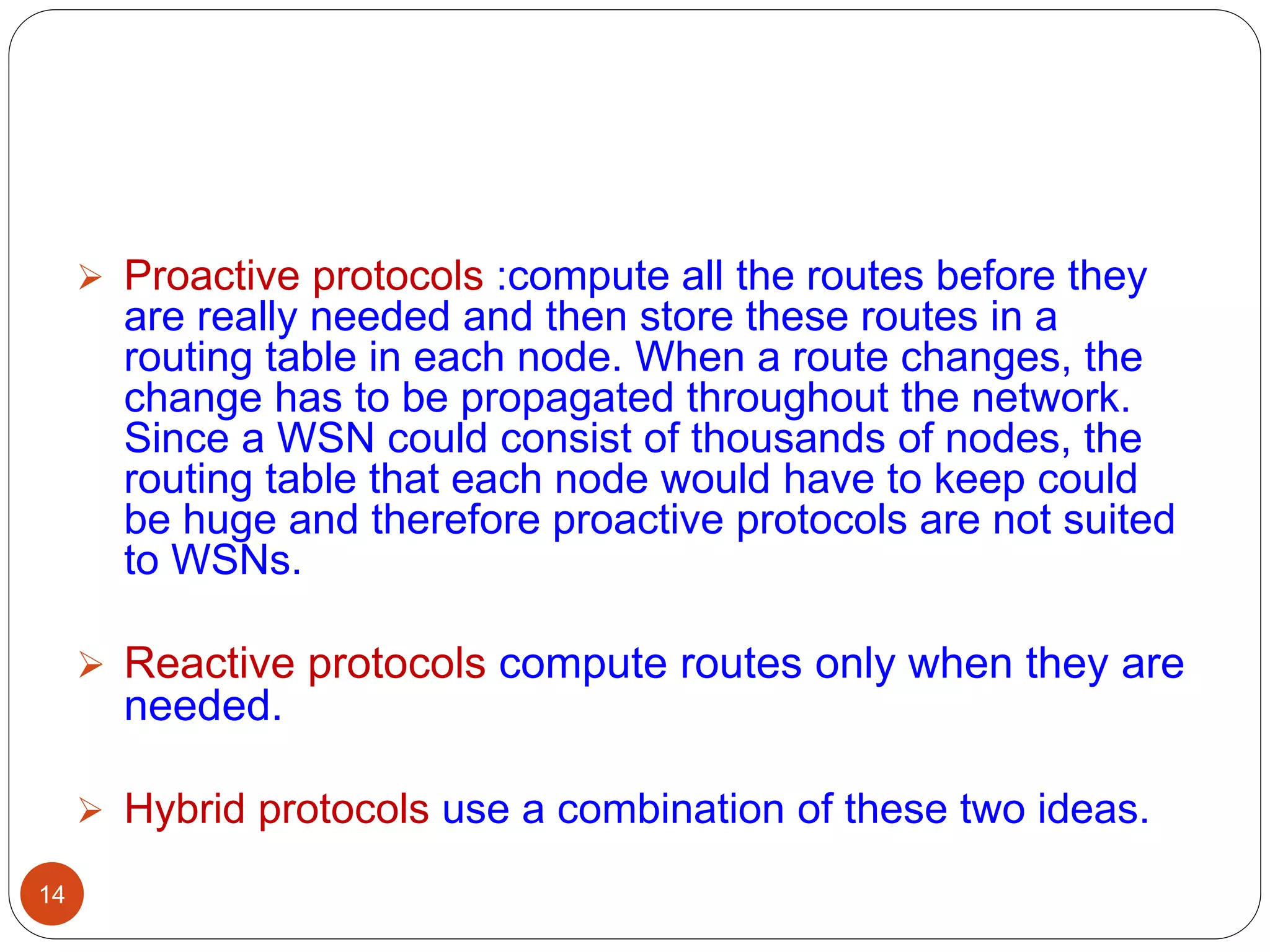
Traditional technique
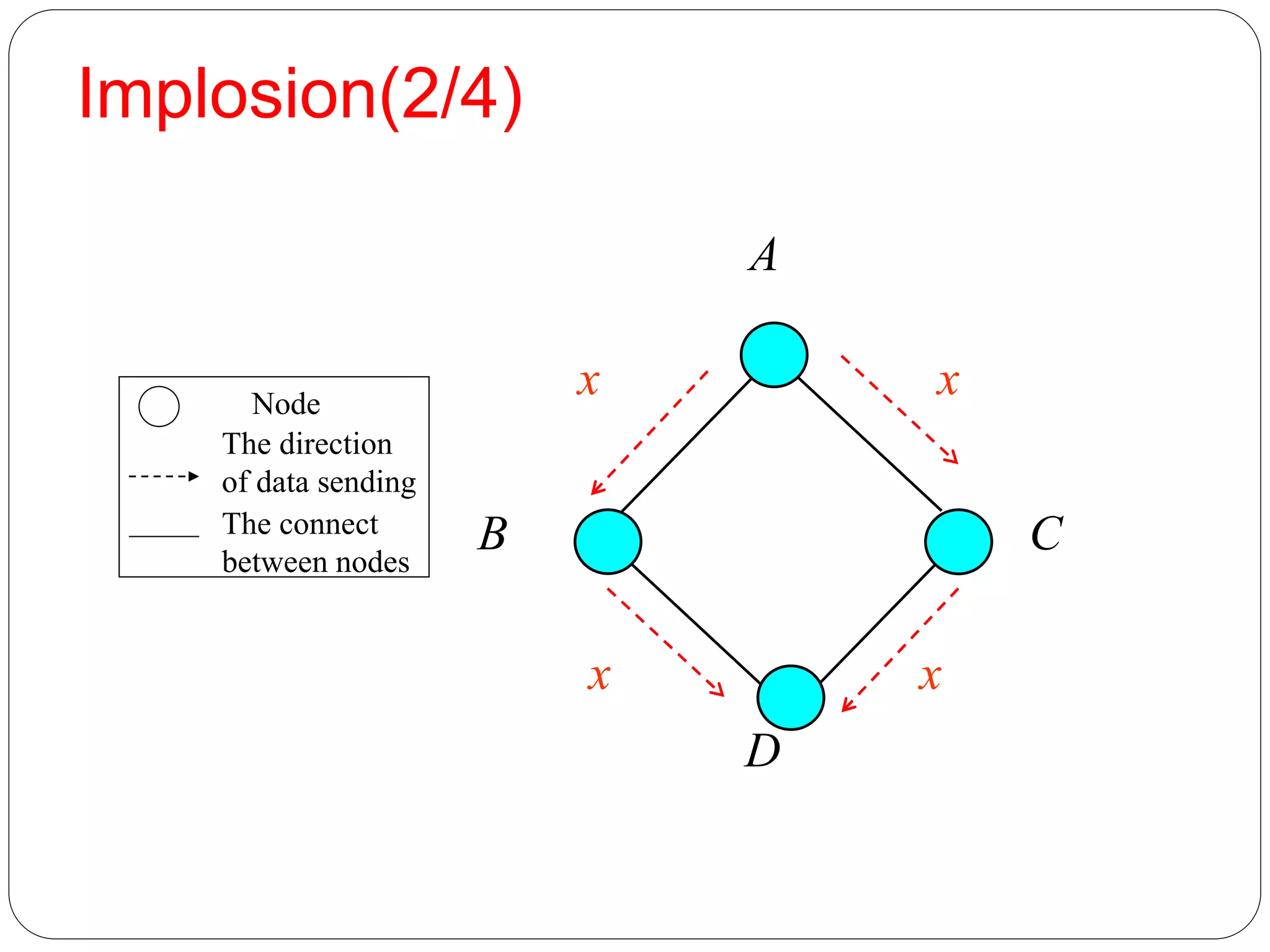
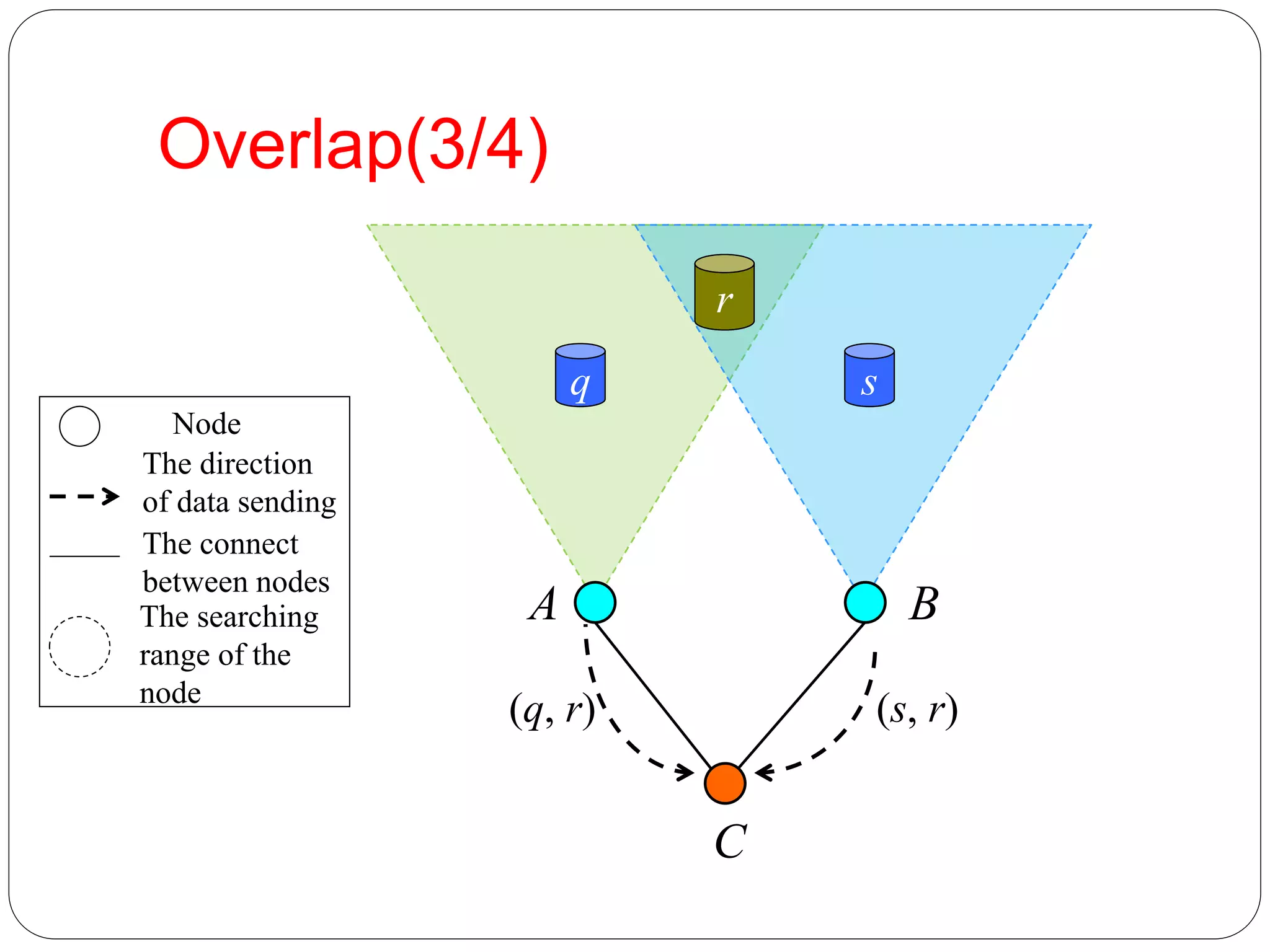
Flooding
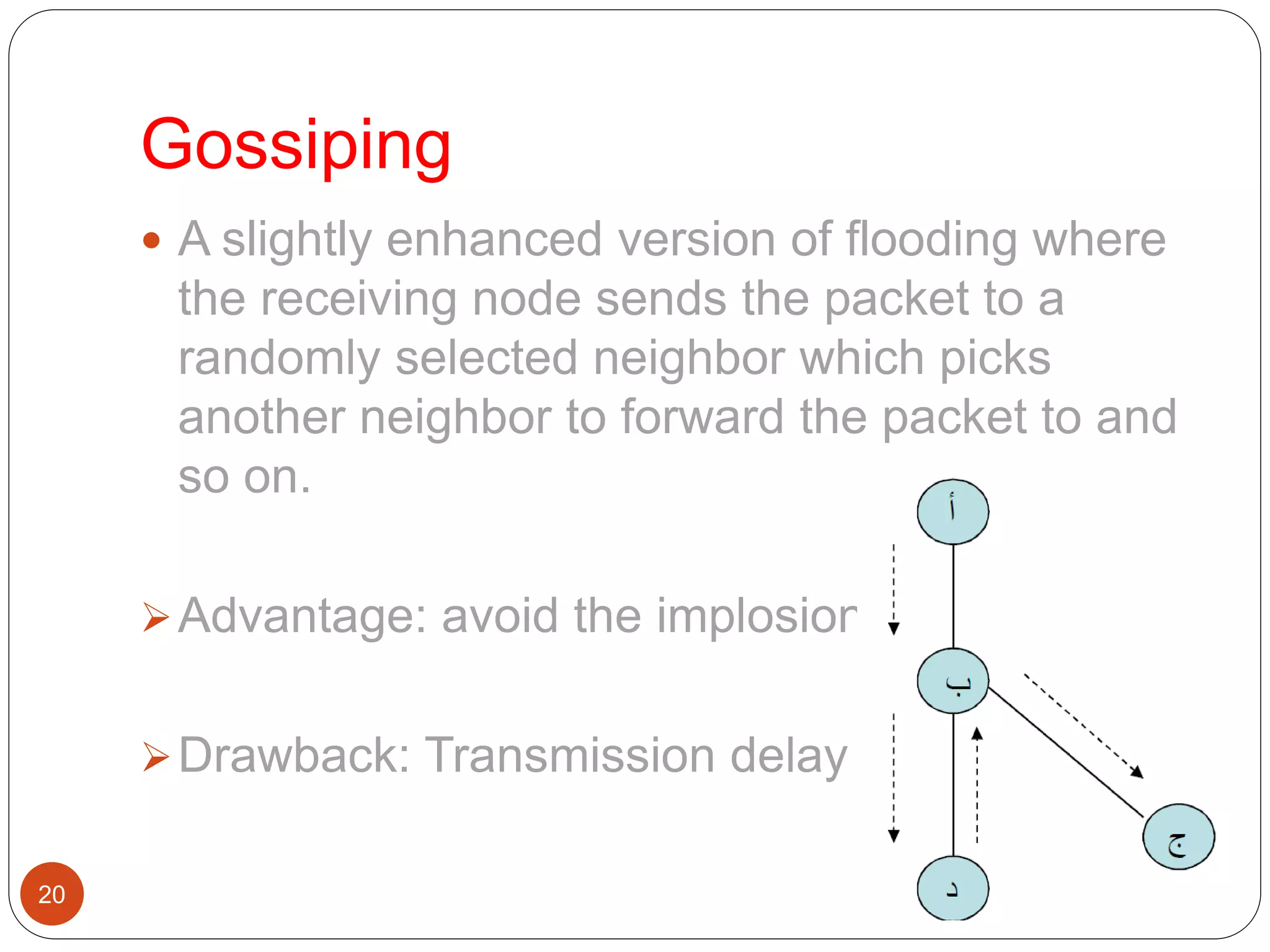
Gossiping
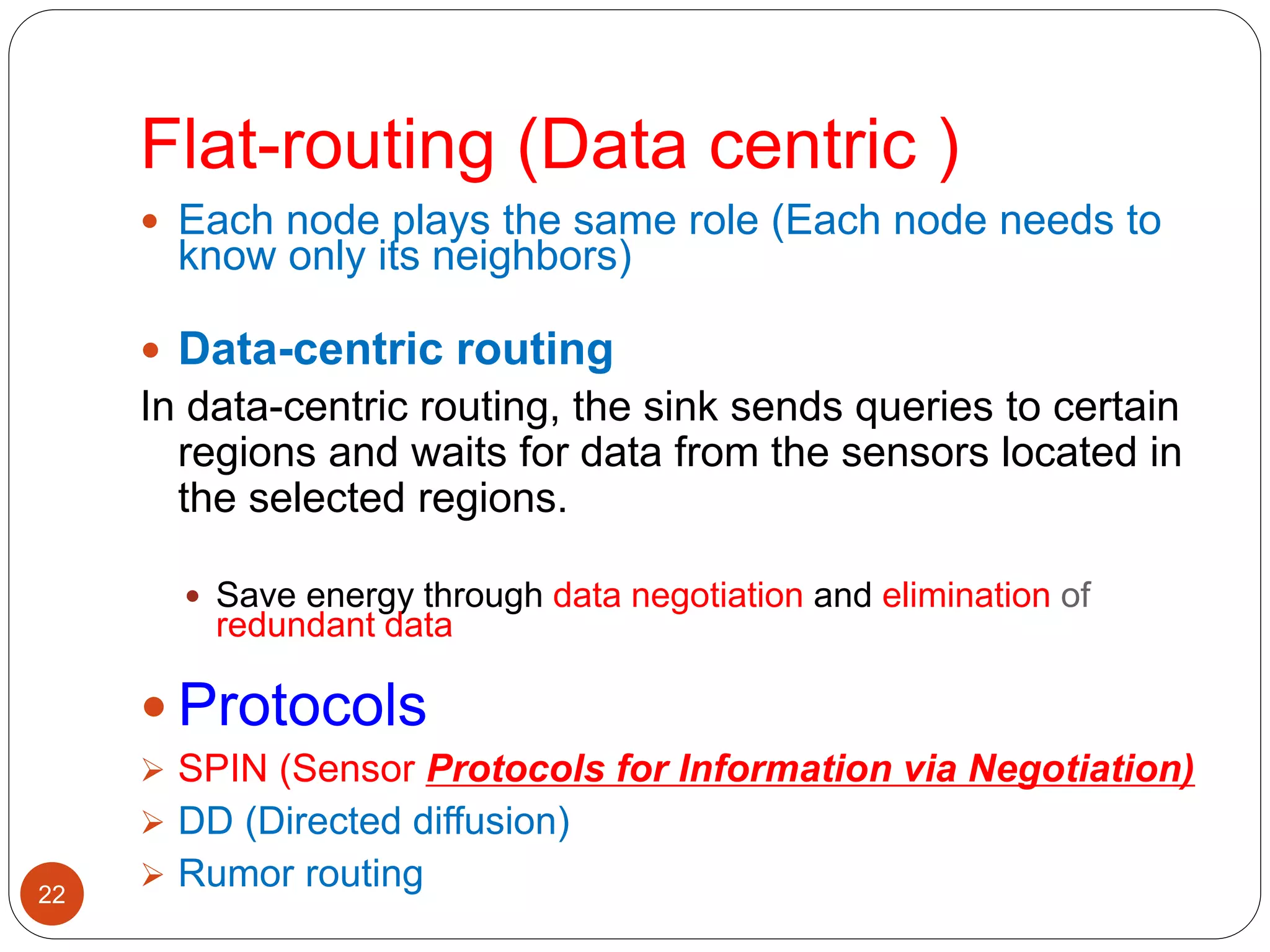
Current routing technique
Flat-routing
Hierarchical-routing
Location-based routing
[1]Ian F. Akyildiz, Weilian Su, Yogesh Sankarasubramaniam, and Erdal Cayirci Georgia Institute of Technology” A Survey on Sensor Networks” IEEE
Communications Magazine • August 2002](https://image.slidesharecdn.com/routing-150301174003-conversion-gate01/75/Routing-15-2048.jpg)


![Router protocol survey
21
Traditional routing technique
Flooding
Gossiping
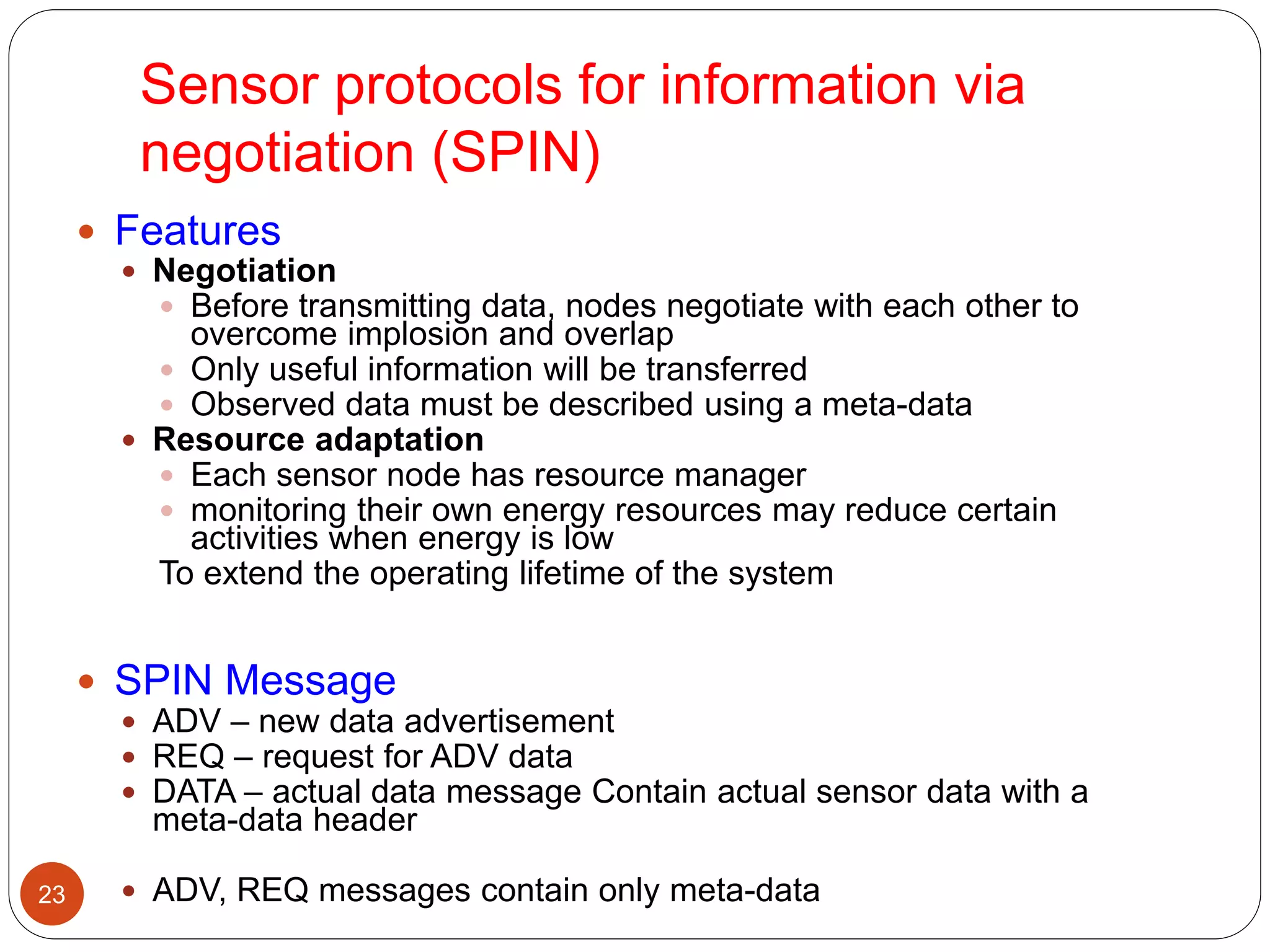
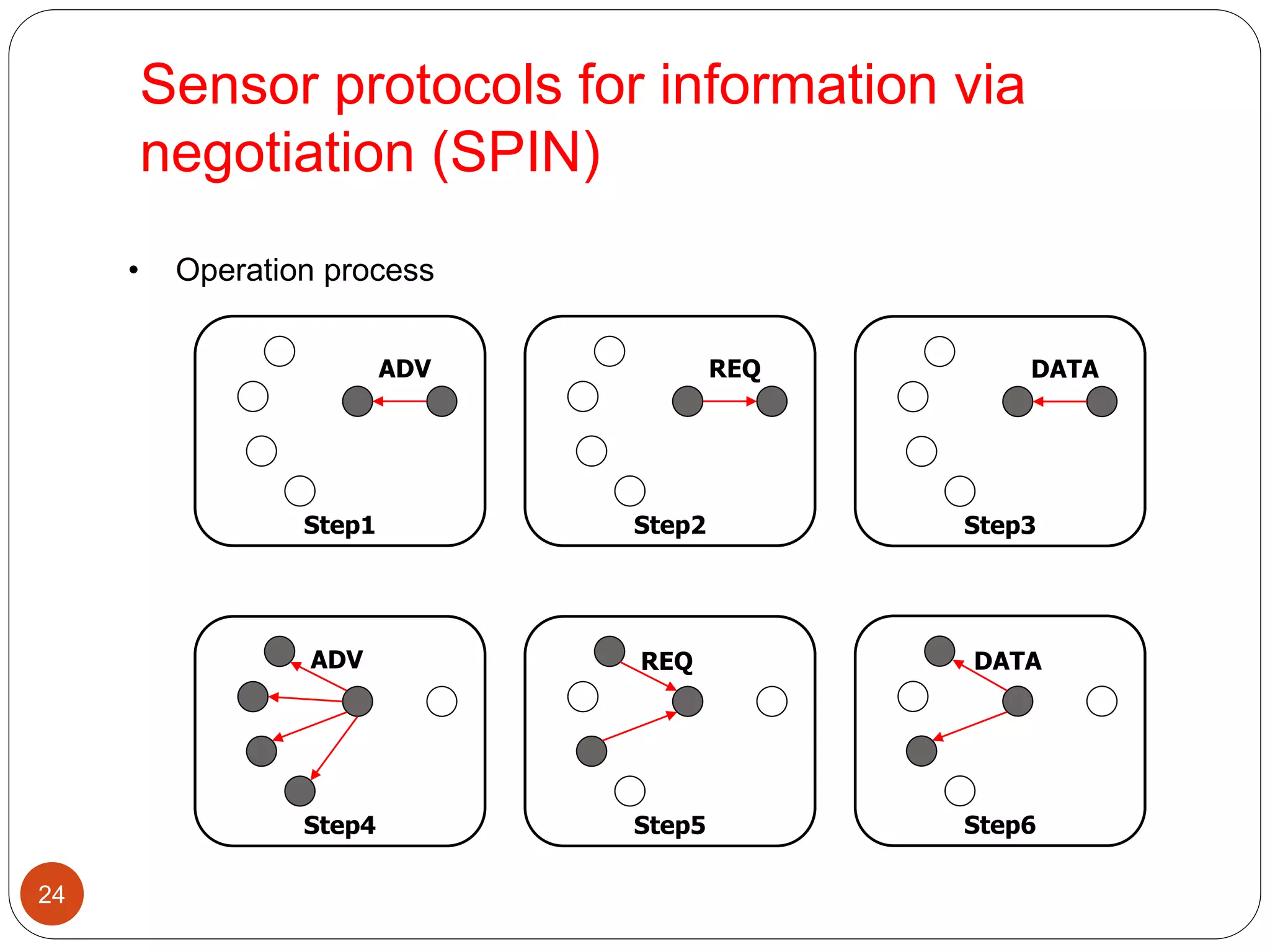
Current routing technique[1]
Flat-routing
Hierarchical-routing
Location-based routing
[1]JAMAL N. AL-KARAKI, AHMED E. KAMAL,” ROUTING TECHNIQUES IN WIRELESS SENSOR NETWORKS: A SURVEY”,
IEEE Wireless Communications • December 2004](https://image.slidesharecdn.com/routing-150301174003-conversion-gate01/75/Routing-21-2048.jpg)