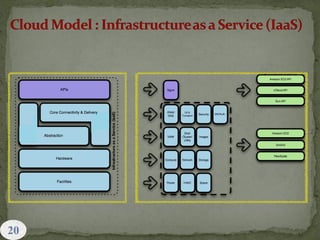
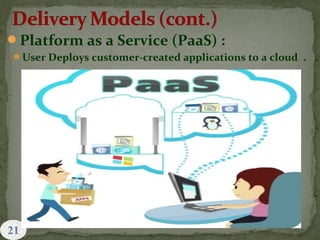
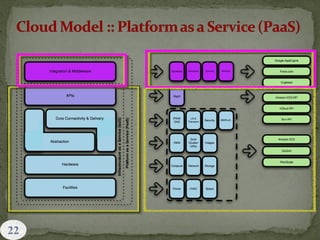
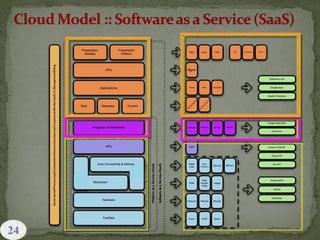
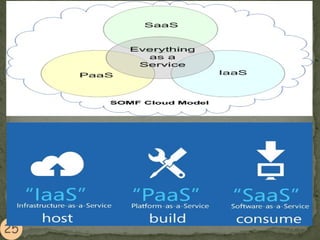
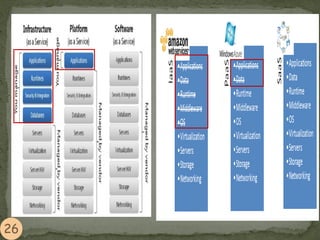
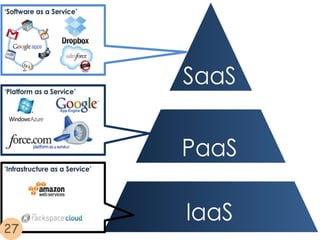
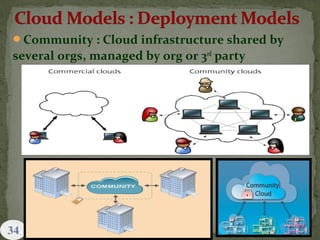
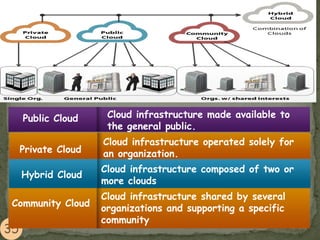
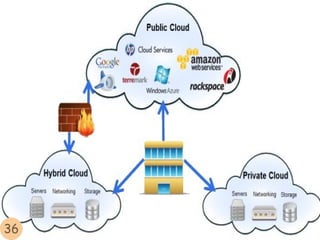
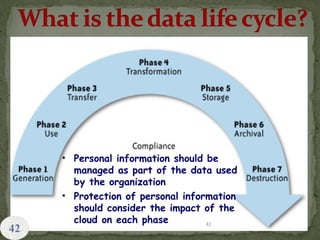
This document provides an overview of cloud computing. It begins with an introduction and defines cloud computing, discussing its history and key attributes. It then covers the different cloud models including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). The document also discusses cloud security and privacy concerns, outlining various security threats and solutions. It concludes by emphasizing the importance of cloud computing and its future.











![Security is the necessary steps to protect a person
or property from harm. (direct action - indirect
action). [Reference: Lecture Notes]
Privacy rights are related to collection, use,
disclosure, storage, and destruction of personal
data , PII (Personally Identifiable Information).](https://image.slidesharecdn.com/cloudcomputingfinal-show-150301172343-conversion-gate01/85/Cloud-computing-final-show-39-320.jpg)



![1. Threat #1: Abuse and Nefarious Use of Cloud Computing
2. Threat #2: Insecure Interfaces and APIs
3. Threat #3: Malicious Insiders
4. Threat #4: Shared Technology Issues
5. Threat #5: Data Loss or Leakage
6. Threat #6: Account or Service Hijacking
7. Threat #7: Unknown Risk Profile
[Reference: CSA: Top Threats to Cloud Computing V1.0
Prepared by the Cloud Security Alliance March 2010]
44](https://image.slidesharecdn.com/cloudcomputingfinal-show-150301172343-conversion-gate01/85/Cloud-computing-final-show-44-320.jpg)




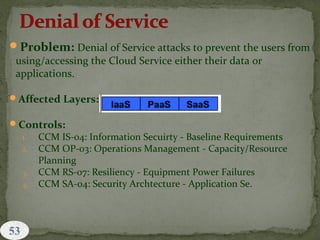
![1. Threat #1: Data Breaches (aka: Leakage)
2. Threat #2: Data Loss
3. Threat #3: Account or Service Hijacking
4. Threat #4: Insecure Interfaces and APIs
5. Threat #5: Denial of Service
6. Threat #6: Malicious Insiders
7. Threat #7: Abuse and Nefarious Use of Cloud Computing
8. Threat #8: Unknown Risk Profile
9. Threat #9: Shared Technology Issues
[Reference: CSA, Top Threats Working Group, "The Notorious
Nine", Cloud Computing Top Threats in 2013, February
2013]
52](https://image.slidesharecdn.com/cloudcomputingfinal-show-150301172343-conversion-gate01/85/Cloud-computing-final-show-52-320.jpg)