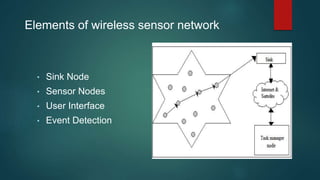
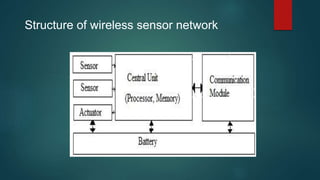
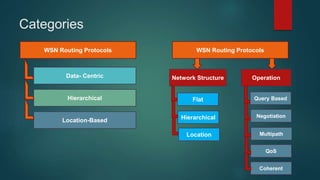
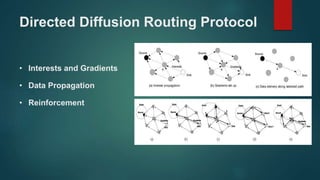
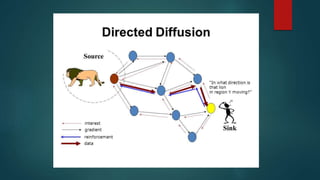
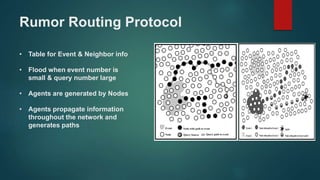
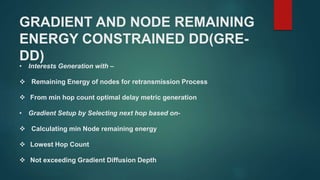
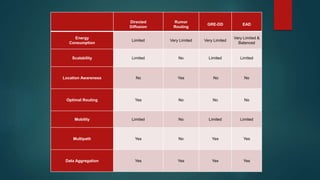
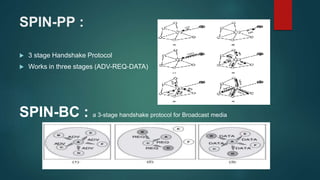
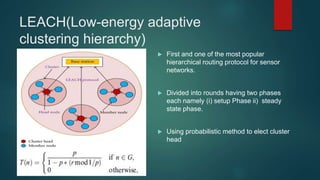
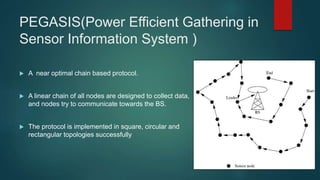
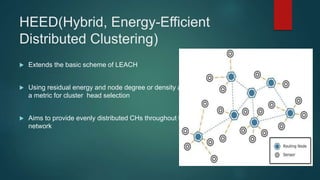
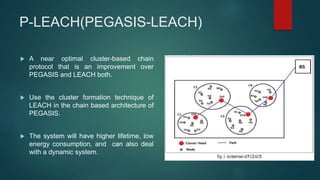
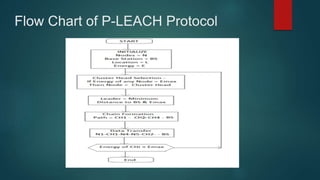
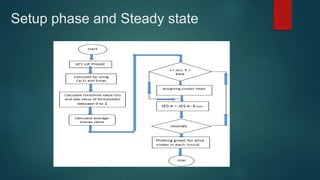
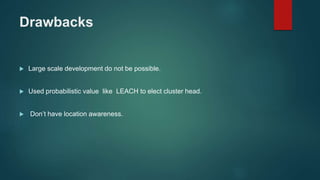
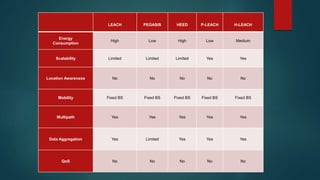
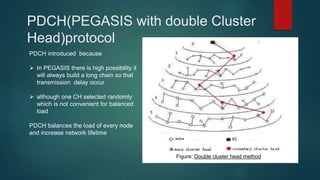
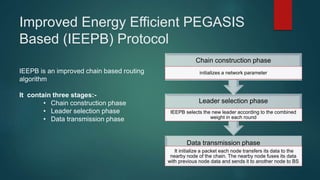
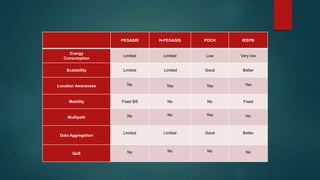
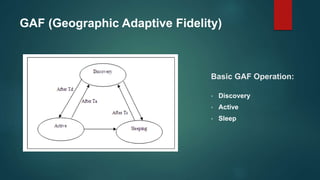
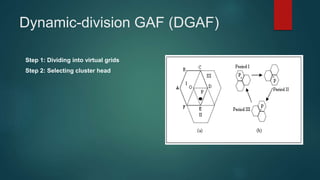
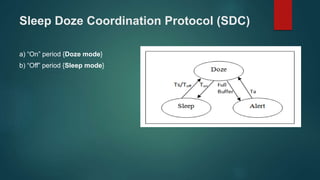
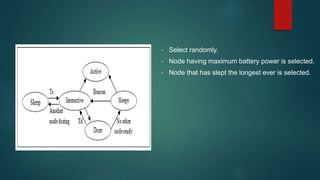
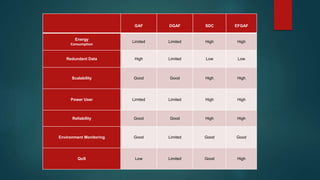
The document provides an overview of routing protocols in wireless sensor networks. It discusses several categories of routing protocols including data-centric, hierarchical, and location-based. For hierarchical routing protocols, it summarizes LEACH, PEGASIS, HEED, P-LEACH, H-LEACH, and other variants that aim to improve energy efficiency. It provides brief descriptions of how each protocol operates and highlights drawbacks. The document also summarizes several data-centric routing protocols including Directed Diffusion, Rumor Routing, and their limitations.