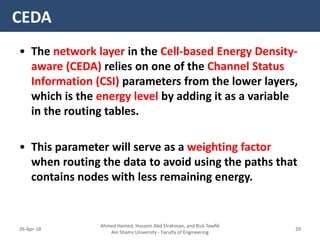
CEDA
Agenda
Ahmed Hamed, Hussein Abd Elrahman, and Rizk Tawfik
Ain Shams University - Faculty of Engineering
2826-Apr-18
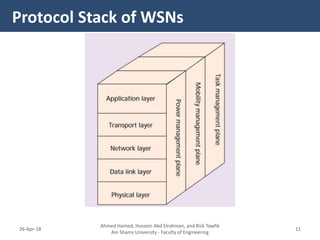
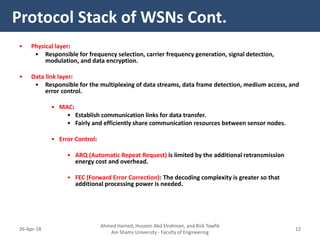
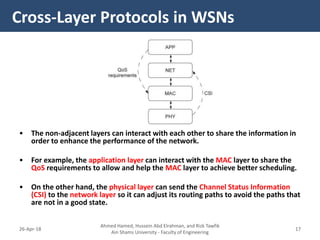
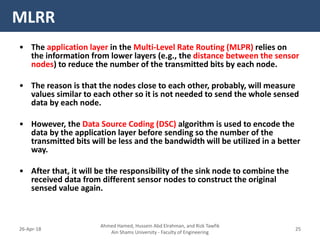
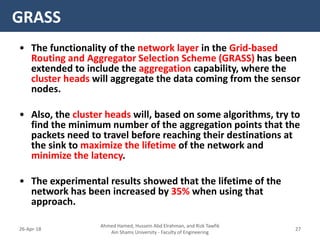
�- The Cross-layer Energy-Delay Aware (CEDA) protocol aims to optimize energy consumption and end-to-end delay in WSNs.
- It allows interaction between the network layer, MAC layer, and physical layer to share information that can help optimize the protocol's objectives.
- For example, the physical layer shares link quality and energy level information with the MAC layer to help in channel allocation. The network layer considers this along with routing to minimize delay.
- Simulation