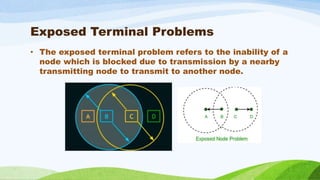
The document discusses routing protocols for Mobile Ad Hoc Networks (MANETs), focusing on the essential characteristics and challenges involved in their design. Key issues include node mobility, bandwidth constraints, error-prone channels, and resource limitations, while ideal routing protocols should be adaptive, distributed, and minimize overhead. Additionally, the document categorizes routing protocols based on various criteria, including their information update mechanisms and topology structure.