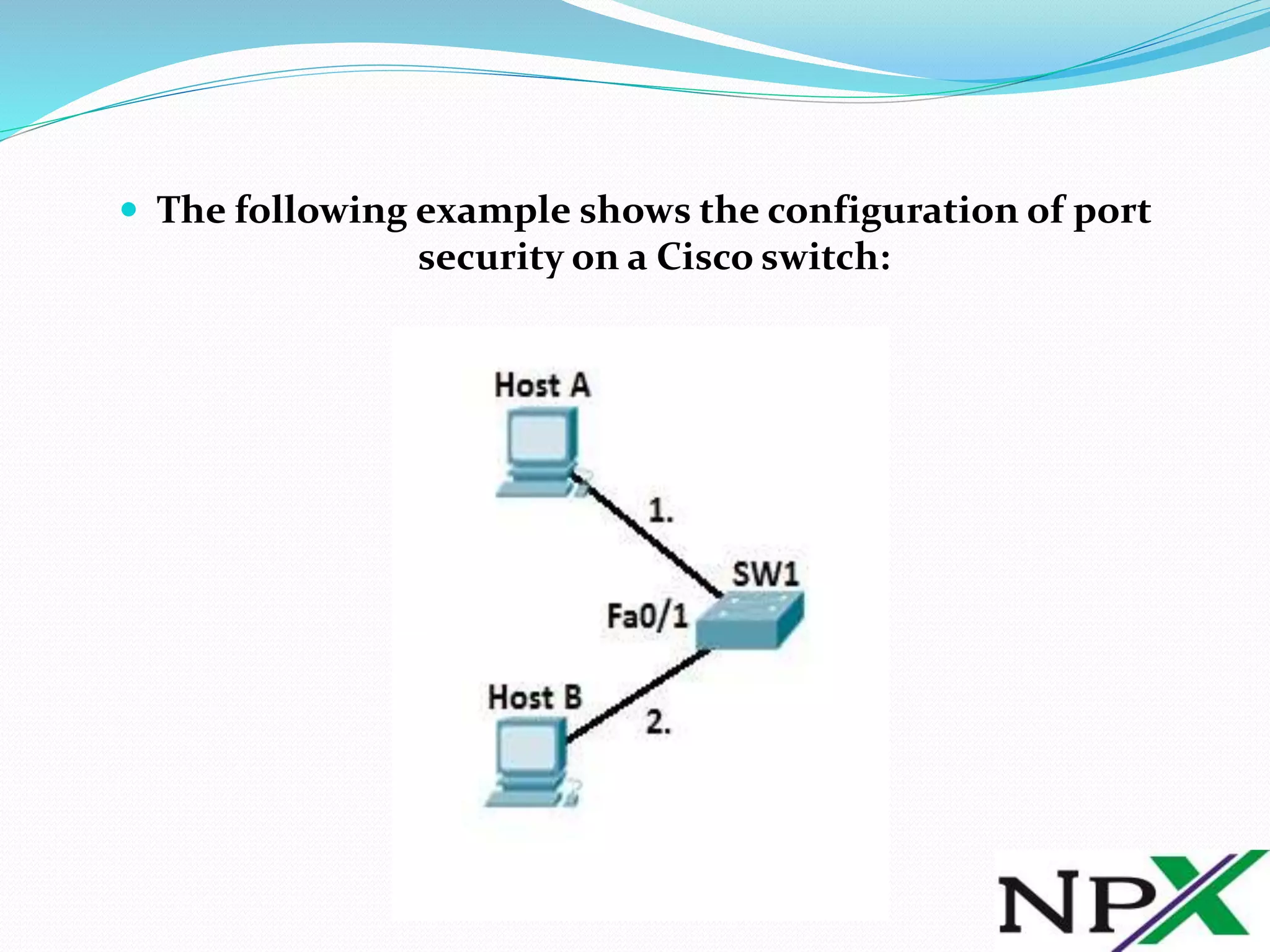
This document discusses port security on Cisco switches. It explains that by default all switch ports are open, allowing any device to connect. Port security allows restricting a port to only allow specific MAC addresses, preventing unauthorized access. It provides steps to configure port security by defining the port as an access port, enabling port security, and specifying allowed MAC addresses. It also describes optional settings like violation actions and maximum MAC addresses. An example configuration is given to demonstrate learning and blocking additional MACs on a port.