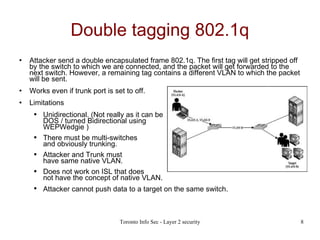
The document discusses various Layer 2 security vulnerabilities and attack methods, including CAM table overflow, VLAN hopping, and DHCP attacks, highlighting the risks posed by insider threats and local attackers. It outlines the challenges in securing Layer 2, such as the limitations of traditional security measures and techniques for mitigating these attacks. Additionally, the document lists best practices for securing Layer 2 networks, including disabling unused ports, configuring port security, and utilizing DHCP snooping.
![Layer 2 Security Toronto Information Security Sami Kamel [email_address] February 2008](https://image.slidesharecdn.com/network-security-layer-2-1207440008294423-9/75/Network-Security-Layer-2-1-2048.jpg)