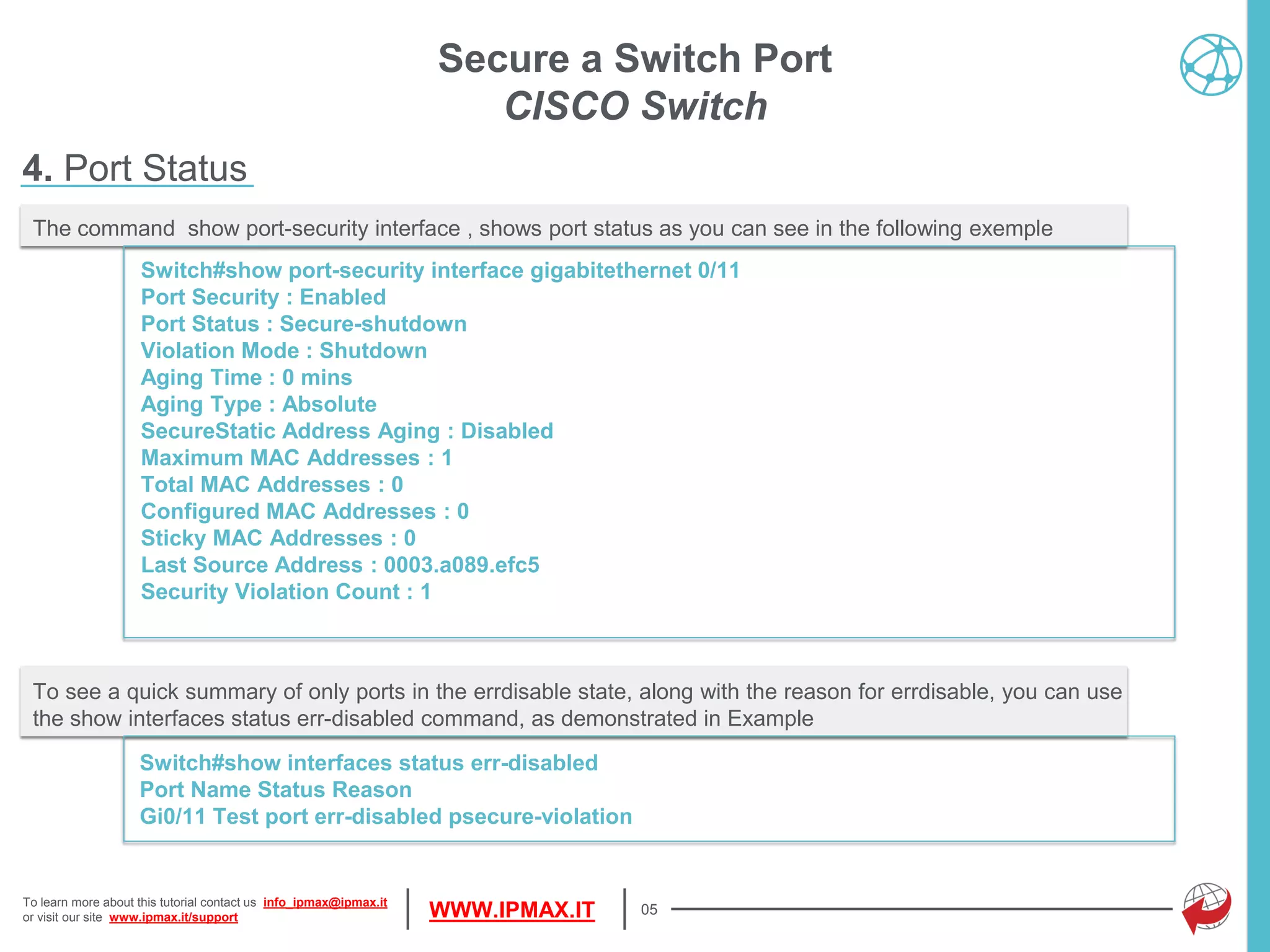
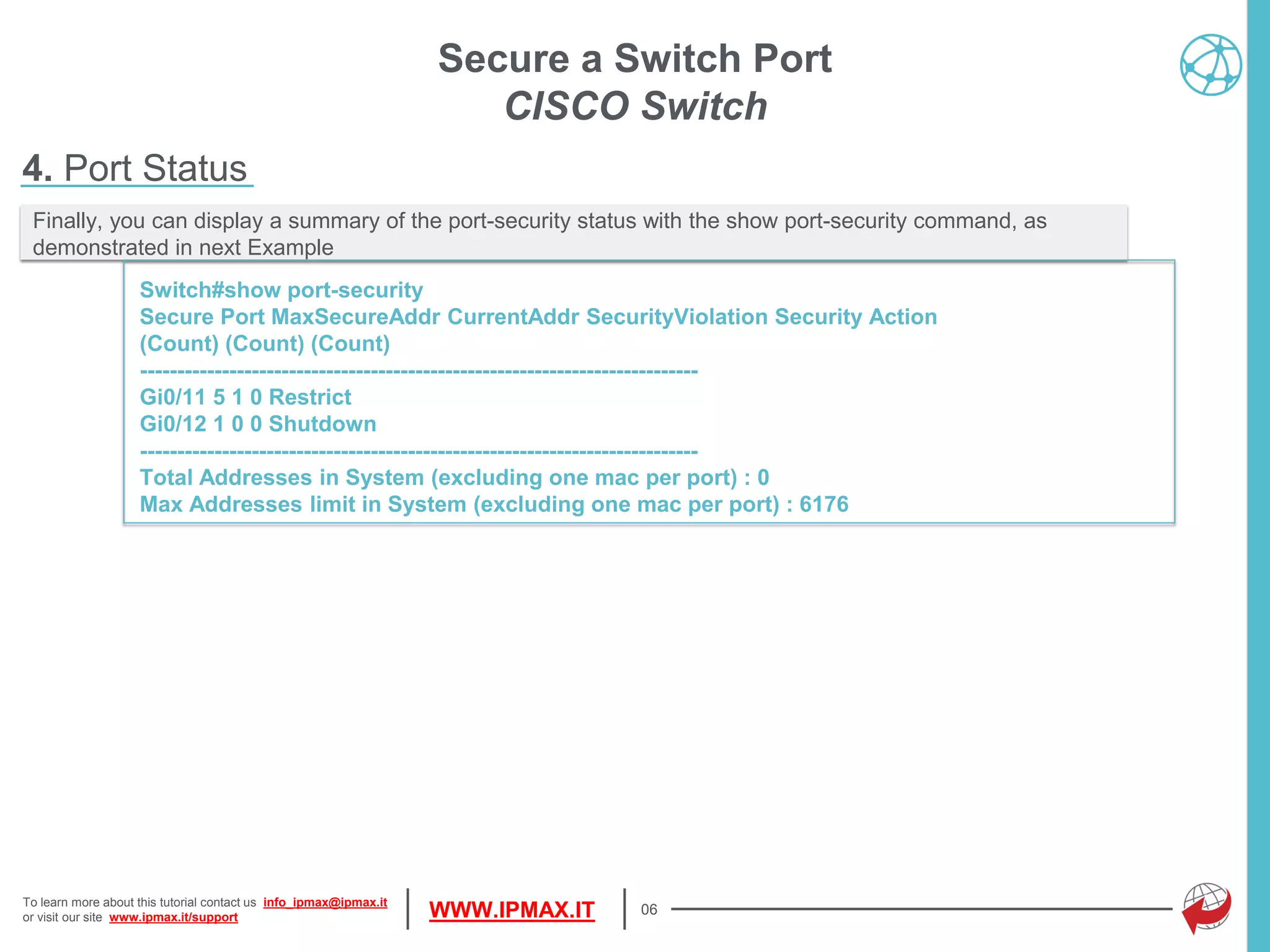
This document provides a tutorial on configuring port security on Cisco switches, detailing how to define allowed MAC addresses and set maximum address limits. It explains different modes of response to security violations, such as shutdown, restrict, or protect, and highlights the importance of monitoring interface statuses and security counts. The document also includes commands for enabling port security, managing MAC address learning, and viewing port security configurations.