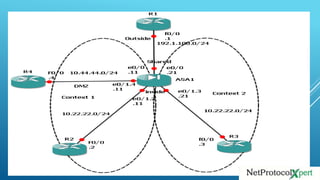
The document discusses configuring a Cisco ASA firewall for multiple security contexts. It provides 6 tasks to configure interface allocations and network addressing for two contexts called ASA-C1 and ASA-C2. It also covers configuring NAT and static routes between the inside networks and external networks to allow traffic to flow through the ASA firewall.