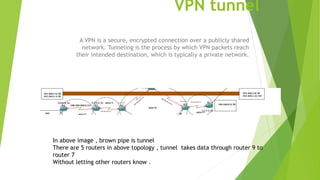
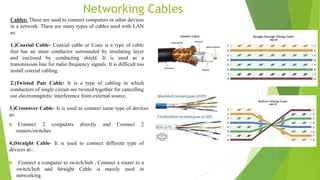
The document provides an overview of networking concepts and components. It begins with basic definitions of networks and networking. It then describes common networking devices like hubs, switches, routers, and network cards. It covers networking cables, IPv4 addressing, routing protocols like RIP and EIGRP, redistribution between protocols, ACLs, NAT, VPN tunnels, and Frame Relay. It concludes with an example implementation of a VPN tunnel between two routers.







![Types of Routing
Static routing - network administrator configures information
about remote networks manually. They are used to reduce overhead
and for security.
R1(config)#ip route network [mask]
{address | interface}[distance] [permanent]
Dynamic routing - information is learned from other routers, and
routing protocols adjust routes automatically.
Default routing:A default route defines where packets will be sent
if no specific route for the destination network is listed in the
routing table. If no default route is set, the router will discard all
packets with destination addresses not found its routing table.](https://image.slidesharecdn.com/basicintroductiontotechnology1-230916033825-b0250c55/85/Basic-Introduction-to-Technology-networking-pdf-9-320.jpg)