Embed presentation
Downloaded 238 times





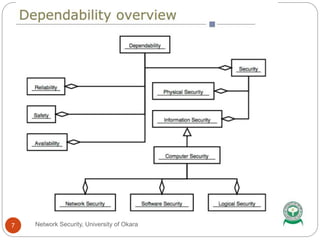



The document discusses network security terminology such as threats, attacks, risk analysis, and cryptography. It defines common threats like spoofing, tampering, repudiation, and denial-of-service attacks. The document also outlines the steps for performing risk analysis and includes an exercise asking questions about finding, removing, and preventing vulnerabilities.








