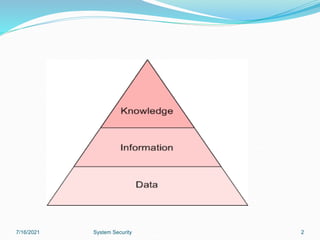
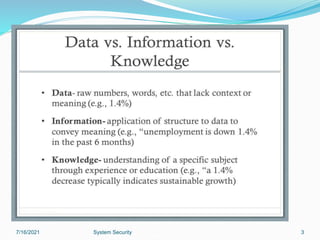
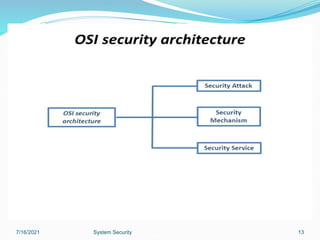
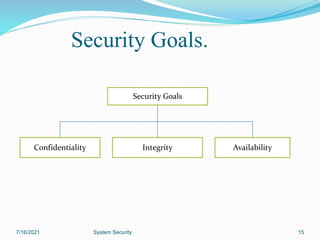
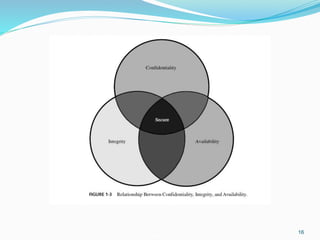
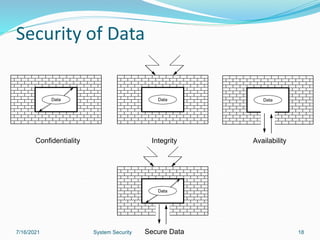
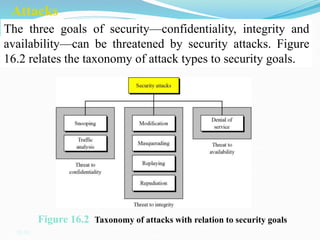
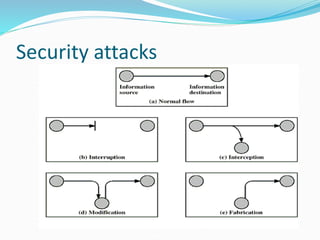
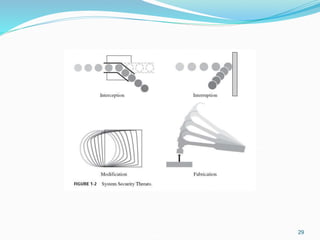
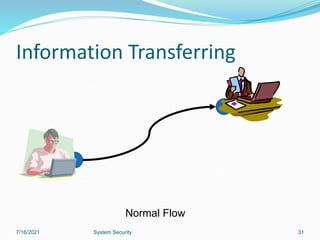
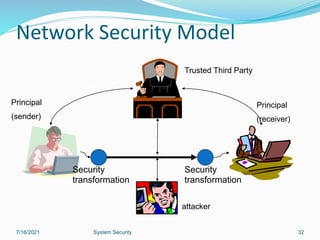
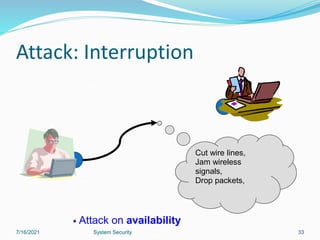
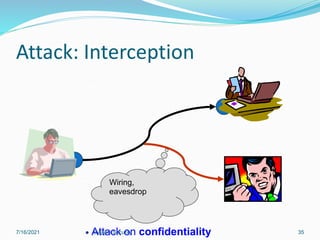
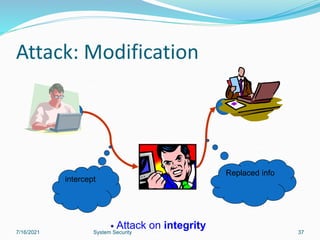
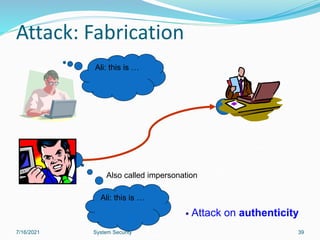
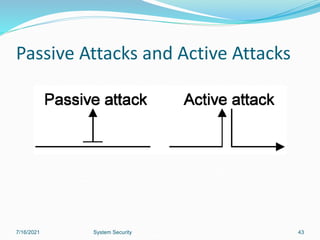
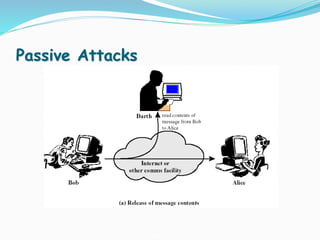
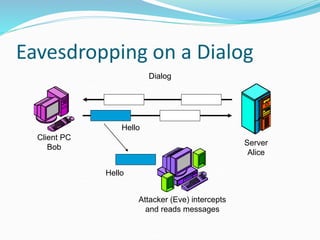
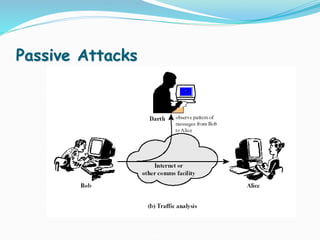
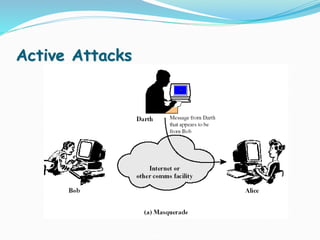
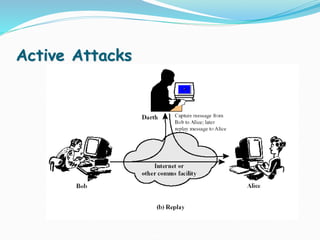
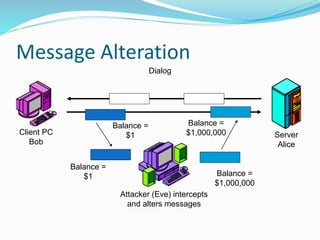
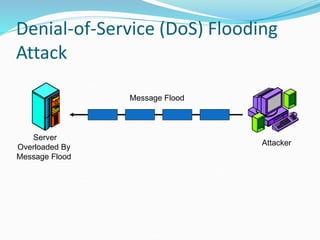
This document discusses information security and system security. It defines information, information security, and the goals of security including confidentiality, integrity and availability. It describes different types of attacks such as interruption, interception, modification and fabrication. It explains passive attacks like eavesdropping and traffic analysis, as well as active attacks including masquerade, replay, message modification, and denial of service. The document outlines why computer security is needed and covers topics like vulnerabilities, threats, and controls to protect against various security risks.