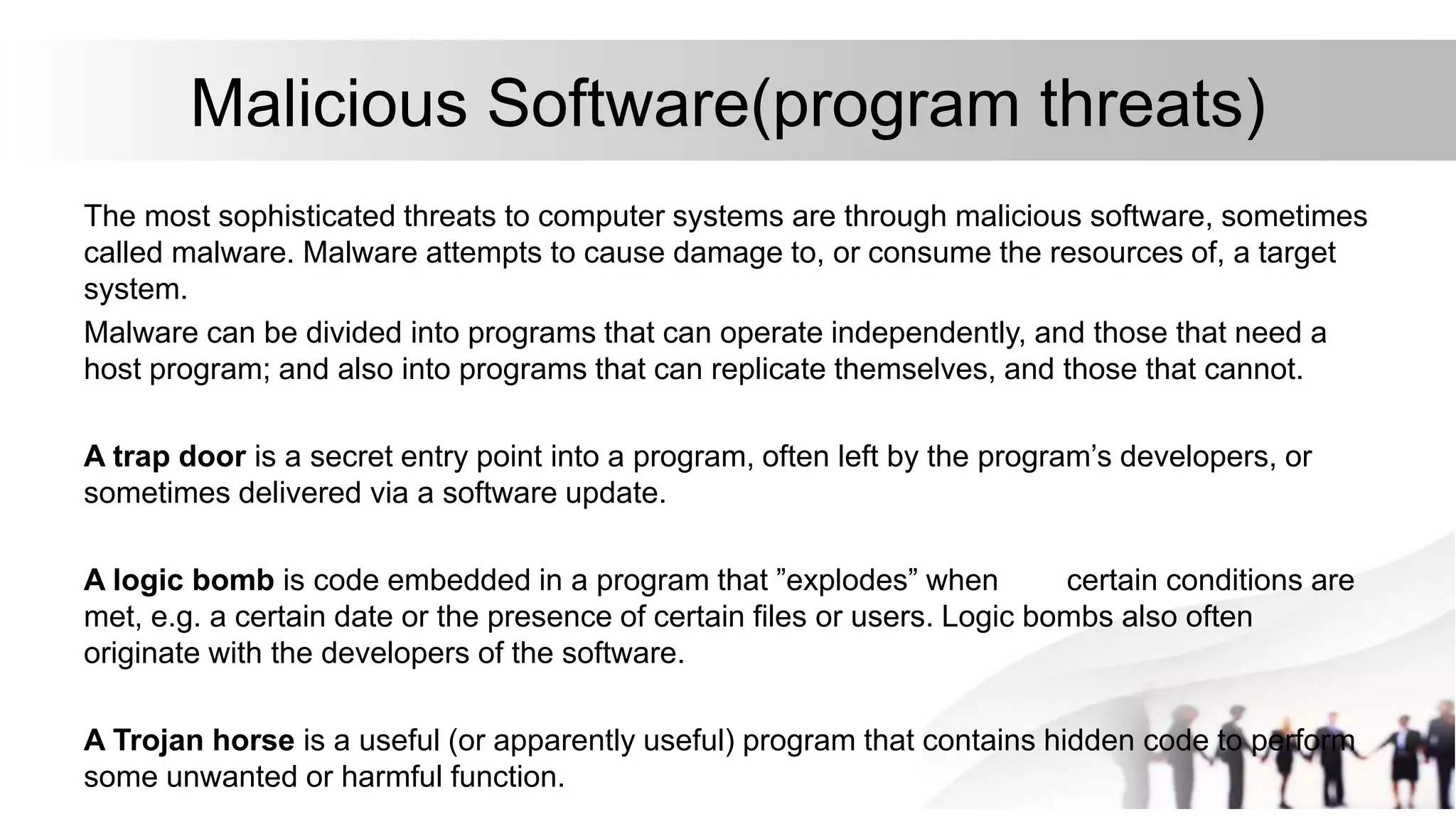
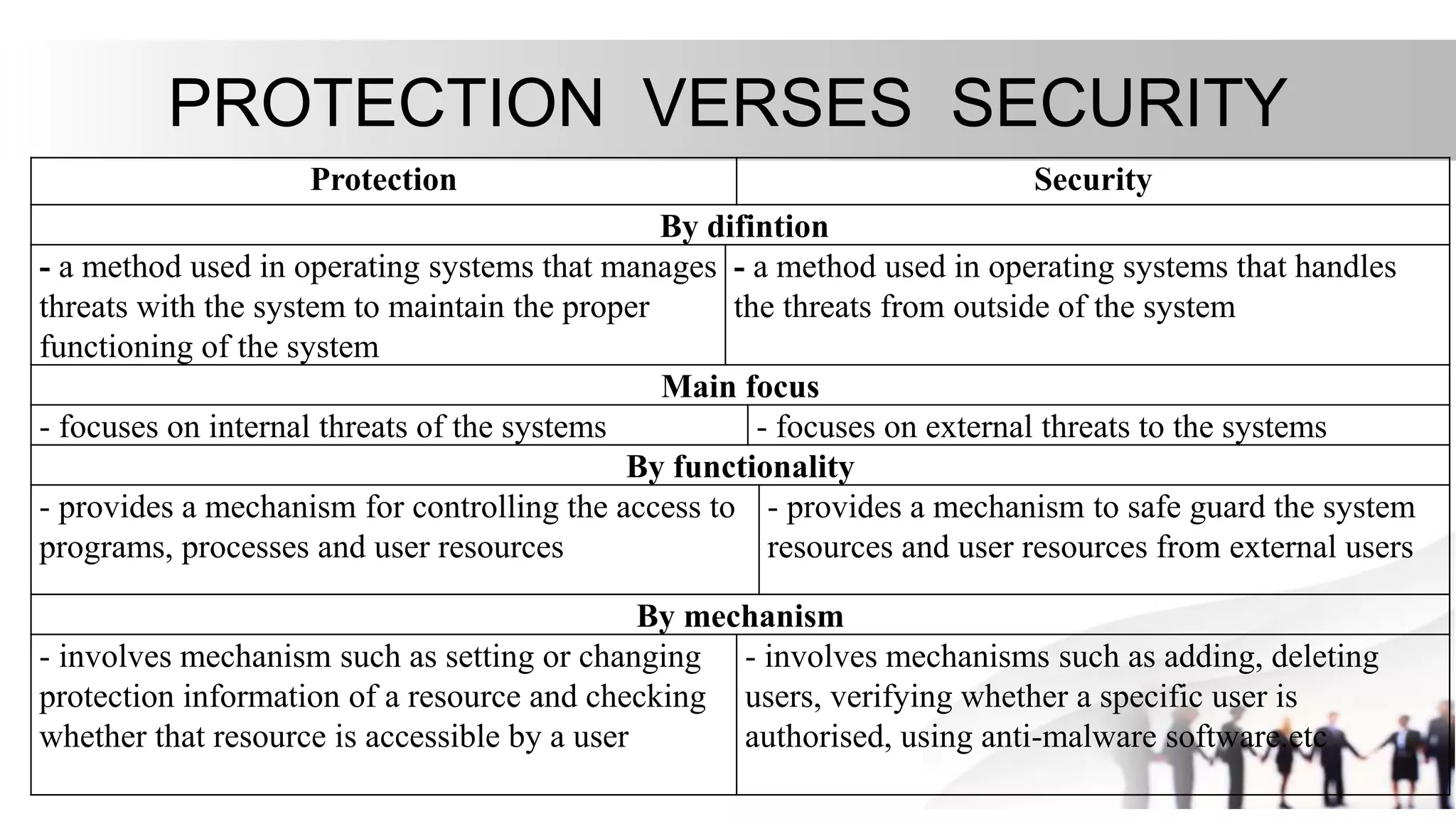
1. Protection and security are mechanisms used in operating systems to control access to resources and safeguard them from threats. Protection focuses on internal threats while security addresses external threats.
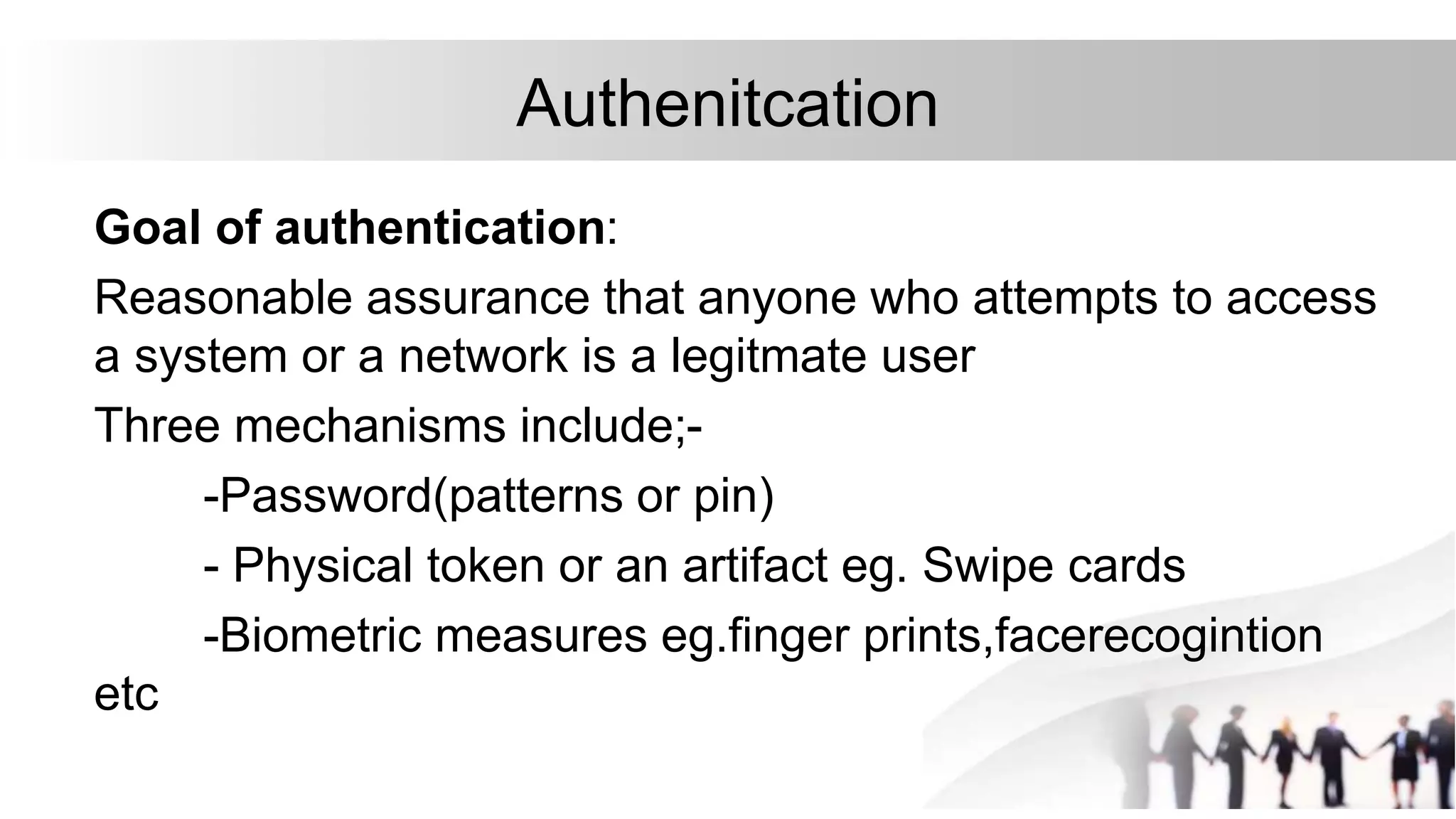
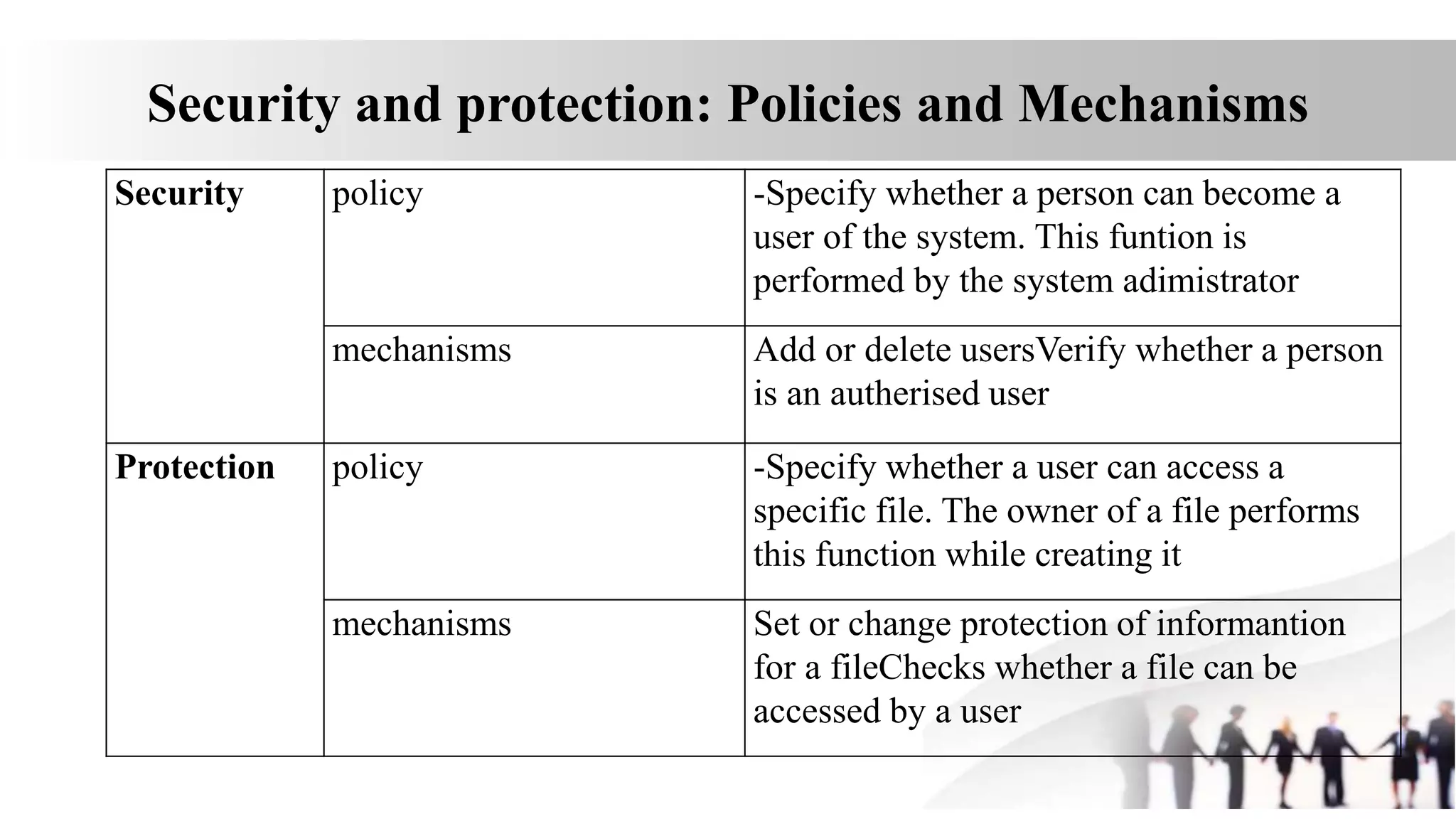
2. Protection involves setting and changing access permissions for resources and checking access for users. Security involves authenticating users, adding/removing them, and using anti-malware software to protect from external threats.
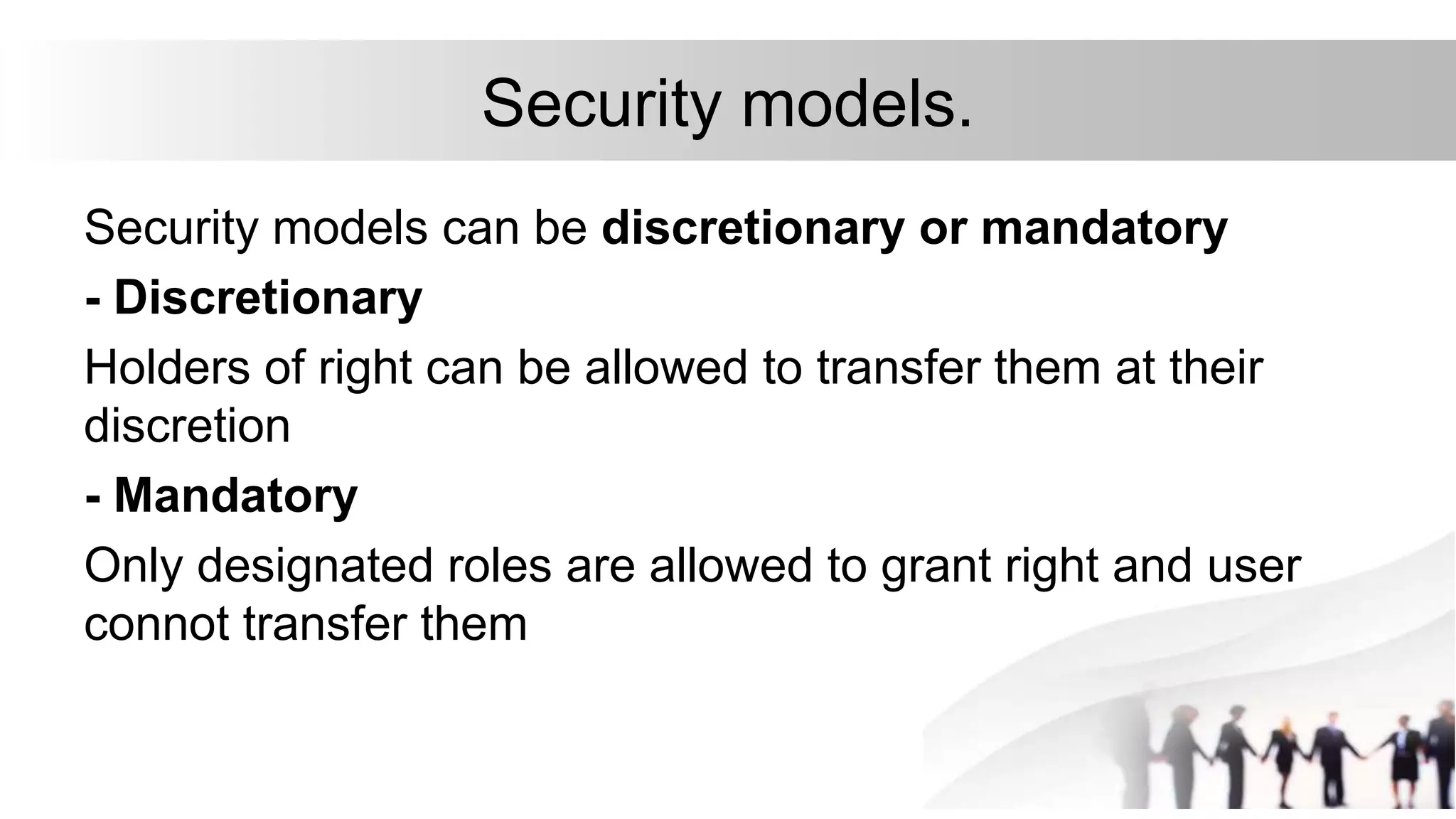
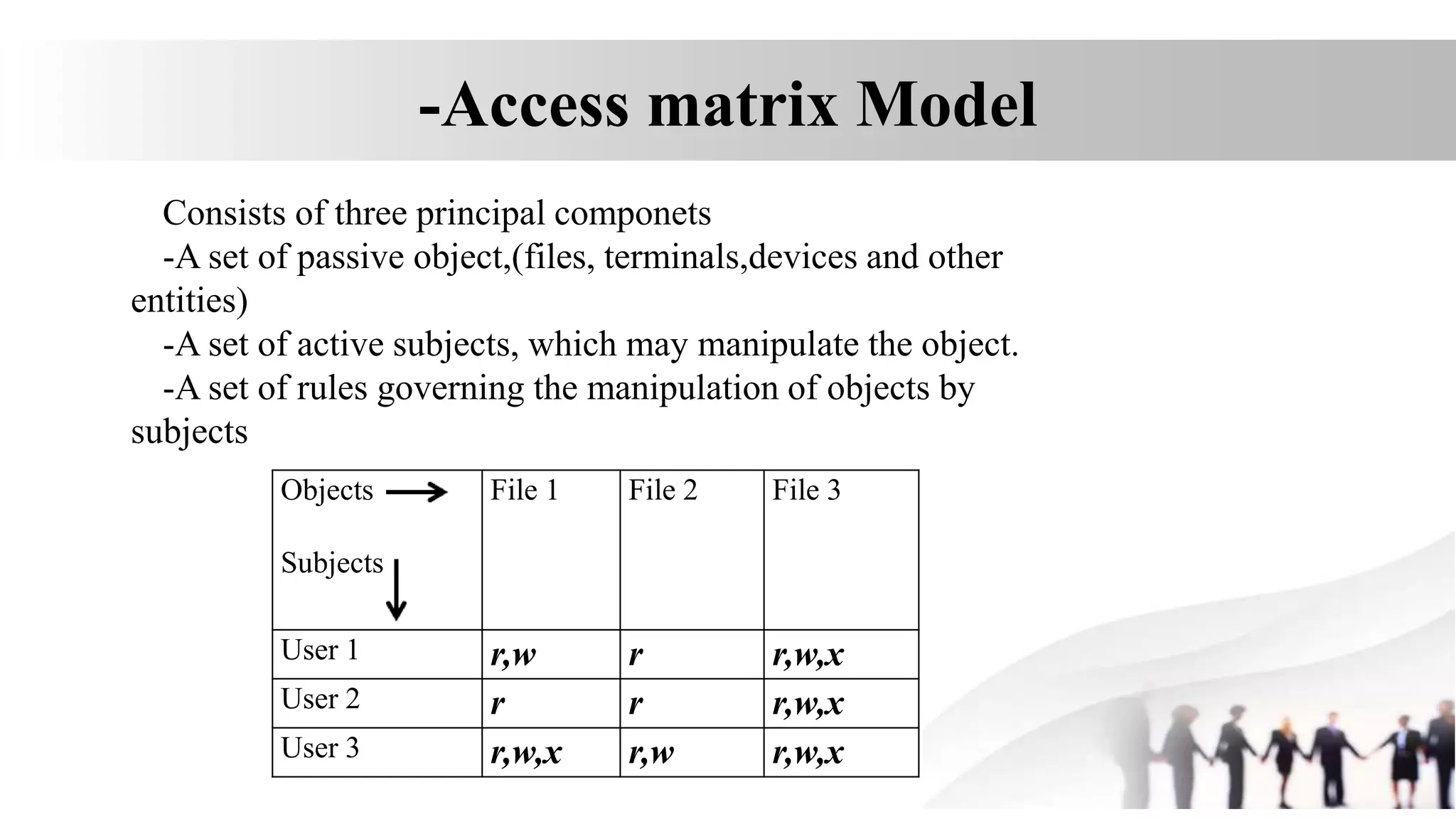
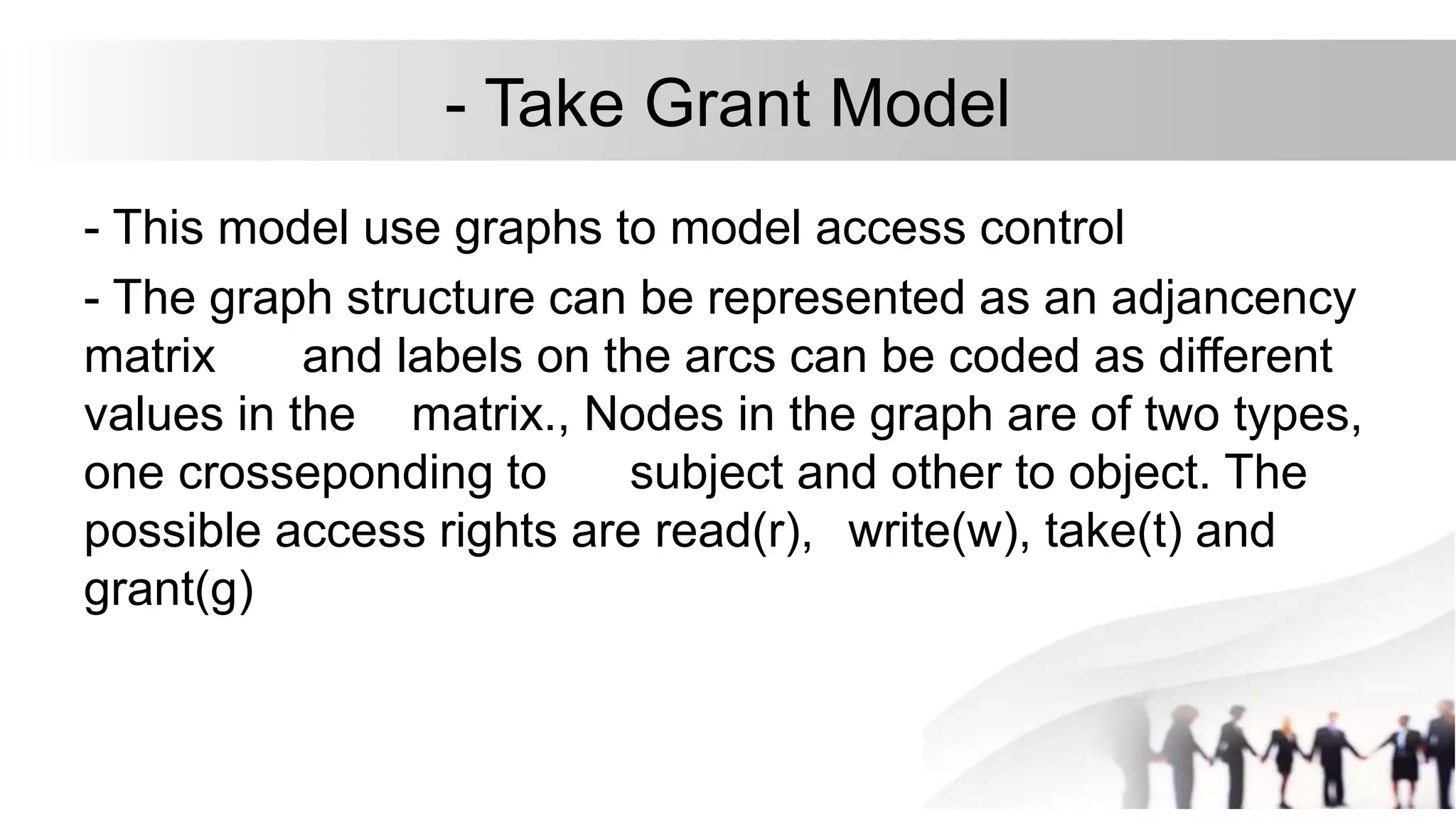
3. A security model like the access matrix model defines the set of subjects, objects, and access rules to represent an organization's security policy for controlling access between users and resources.