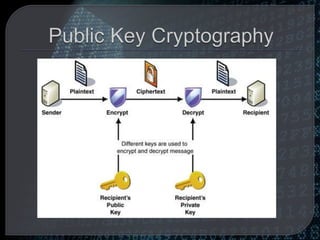
Cryptography is the practice of protecting information by converting it into an unreadable format. Only using a secret key can the information be converted back to a readable format. Throughout history, different encryption techniques have been developed including the Caesar cipher, the Vigenere cipher, and public key cryptography developed by Diffie and Hellman. Modern cryptography is used for purposes such as authentication, electronic money, secure network communication, anonymous remailers, and disk encryption. However, widespread use of unbreakable encryption could enable criminal activity and threaten national security and business interests.














![ Cryptography poses a threat to organizations and
individuals too. With encryption, an employee of a
company can sell proprietary electronic information to
a competitor without the need to photocopy and handle
physical documents.
Electronic information can be bought and sold on
"black networks" such as Black-Net [1] with complete
secrecy and anonymity -- a safe harbor for engaging in
both corporate and government espionage.
The keys that unlock a corporation's files may be lost,
corrupted, or held hostage for ransom, thus rendering
valuable information inaccessible.](https://image.slidesharecdn.com/cryptography-161029124415/85/Cryptography-17-320.jpg)
