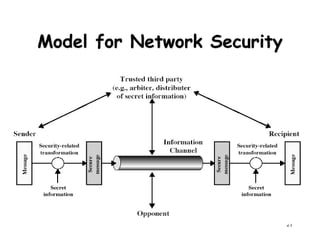
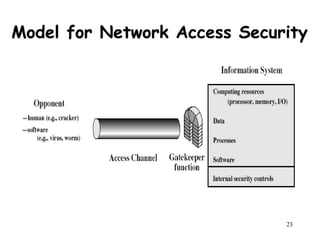
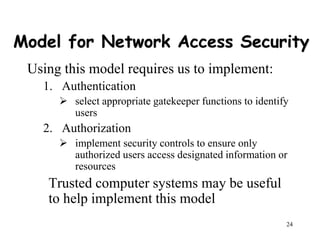
This document provides an overview of network security for a course, including discussing cryptography algorithms and protocols, network security applications and tools, system security issues, and standards for internet security. The course will cover topics such as encryption, digital signatures, key exchange, and network security protocols and applications. Students will complete homework assignments, projects implementing cryptography and a secure messaging system, and exams.