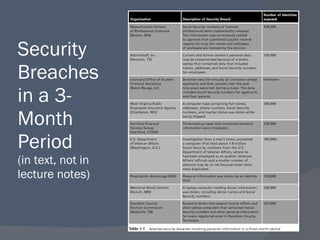
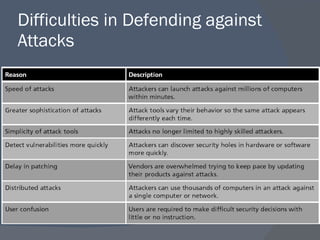
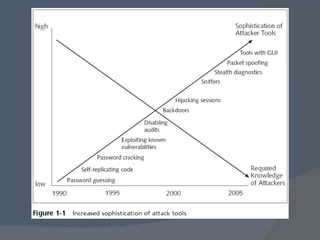
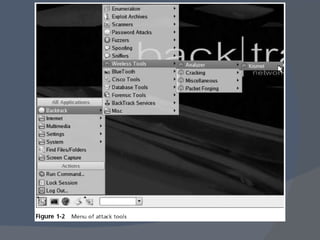
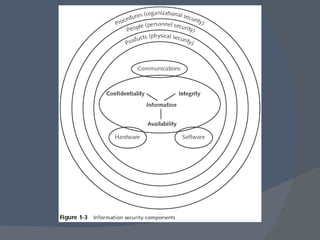
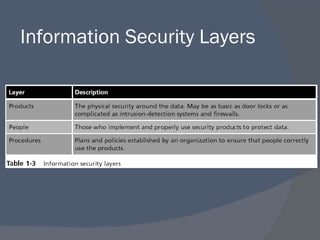
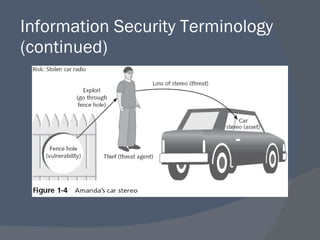
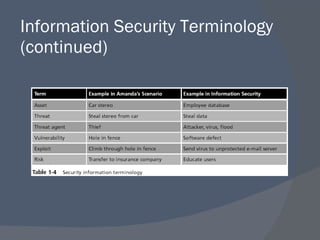
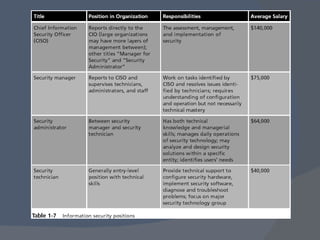
The document outlines a network security program offering courses on fundamental security concepts, ethical hacking, and advanced techniques aimed at preparing students for certification. It discusses various types of cyber threats, the motivations behind attacks, and defenses against them, emphasizing the importance of layered security and the role of certification in advancing security careers. Additionally, it covers several critical security laws and the impact of data breaches on organizations.


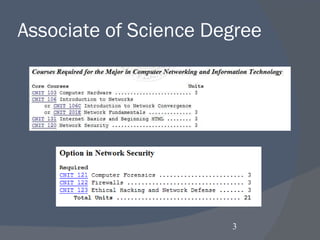







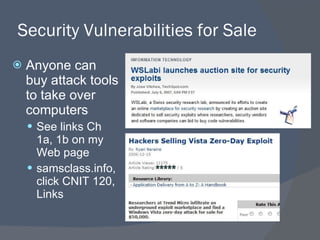


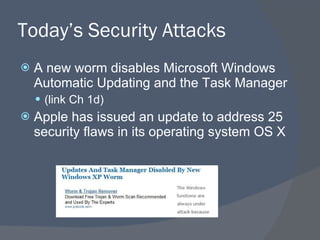

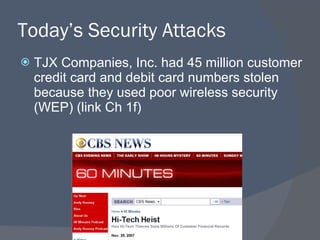
![Worm infects 1.1 million PCs in 24 hours “ On Tuesday there were 2.5 million, on Wednesday 3.5 million and today [Friday], eight million” See links Ch 1g, 1l](https://image.slidesharecdn.com/ch01-100129134204-phpapp01/85/Ch01-Introduction-to-Security-17-320.jpg)