This document provides an introduction to cryptography. It discusses the basic terms, notations, and structures of cryptography including private and public key cryptography examples. It also discusses modern secret key ciphers, encryption, attacks on ciphers, and the design of private key ciphers. The document contains examples of the Caesar cipher and a toy example of private and public key cryptography. It outlines principles of private key encryption and applications of modern cryptography.











![CSE2500 System Security and Privacy 19
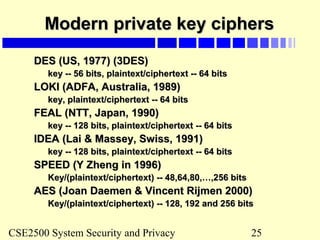
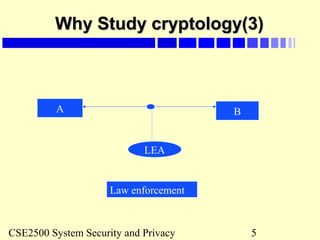
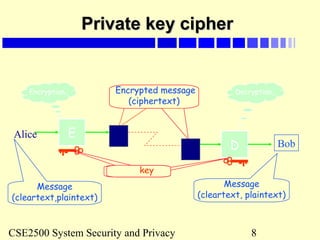
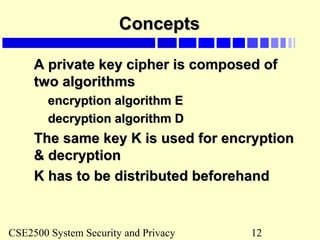
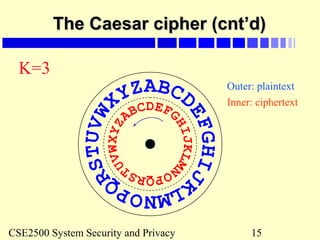
Toy example of private keyToy example of private key
cryptography (TPC)cryptography (TPC)
Assume that a message is broken into 64-bit blocks and eachAssume that a message is broken into 64-bit blocks and each
64-bit block of plaintext is encrypted separately:64-bit block of plaintext is encrypted separately:
Key space are combinations of numerical digits – max: 7Key space are combinations of numerical digits – max: 7
digits-digits-
(eg: key = [1]; or key = [1,3], or key = [1,4,2]).(eg: key = [1]; or key = [1,3], or key = [1,4,2]).
Assume that all 8 bits of a byte is used and key digits startAssume that all 8 bits of a byte is used and key digits start
from left to right.from left to right.
Encryption: Each plaintext block is first shifted by the numberEncryption: Each plaintext block is first shifted by the number
of binary digits before the last non-zero digit of the key. It isof binary digits before the last non-zero digit of the key. It is
then exclusive-ored with the key starting from the first byte ofthen exclusive-ored with the key starting from the first byte of
the block, repeatedly to the end of the block (the key moves athe block, repeatedly to the end of the block (the key moves a
distance of its size from left to right of the plaintext block).distance of its size from left to right of the plaintext block).
Decryption: do the reverse of encryption: the cipher-text isDecryption: do the reverse of encryption: the cipher-text is
exclusive-ored and then shifted.exclusive-ored and then shifted.
0 0 0=
1 1 0=
0 1 1=
1 0 1=
: exclusive: exclusive oror](https://image.slidesharecdn.com/cryptography-130825152452-phpapp01/85/Cryptography-19-320.jpg)
![CSE2500 System Security and Privacy 20
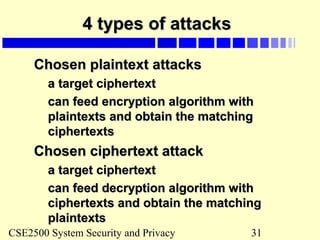
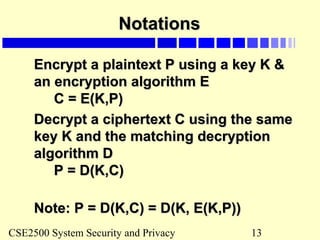
Using TPCUsing TPC
Use TPC to encrypt the plaintext “12345”, keyUse TPC to encrypt the plaintext “12345”, key
= [1,4,2]= [1,4,2]
Use TPC to encrypt the plaintext “TREATYUse TPC to encrypt the plaintext “TREATY
IMPOSSIBLE”; key = [4];IMPOSSIBLE”; key = [4];
Use TPC to encrypt the plaintext “100Use TPC to encrypt the plaintext “100
dollars”, key = [2,4];dollars”, key = [2,4];](https://image.slidesharecdn.com/cryptography-130825152452-phpapp01/85/Cryptography-20-320.jpg)