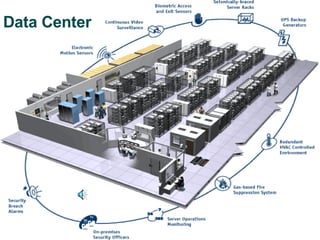
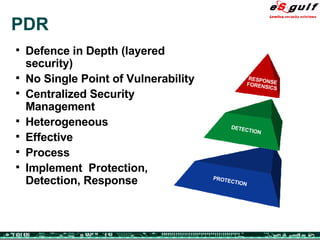
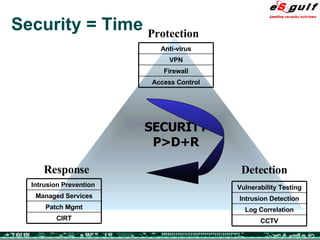
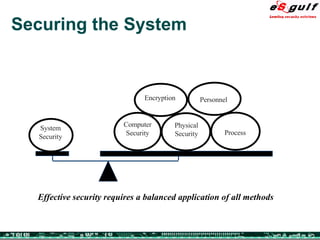
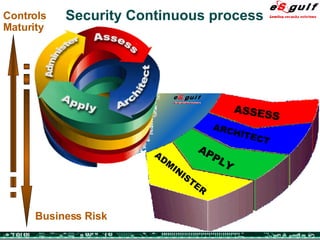
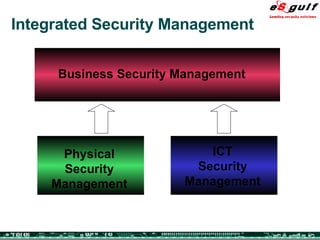
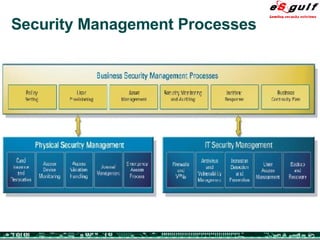
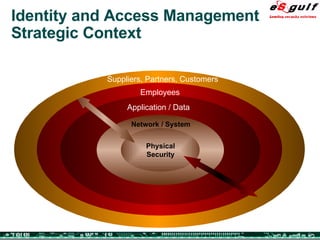
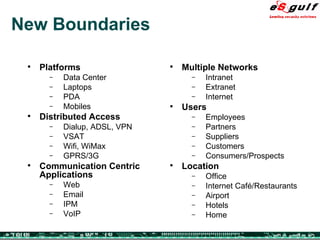
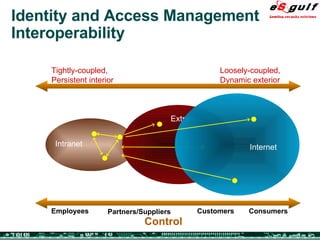
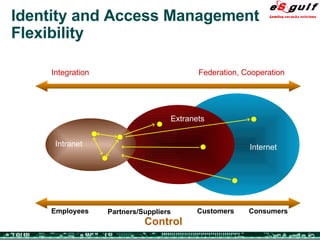
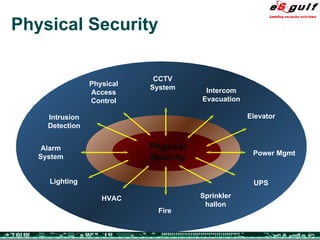
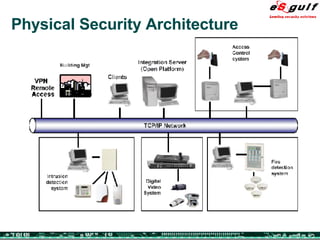
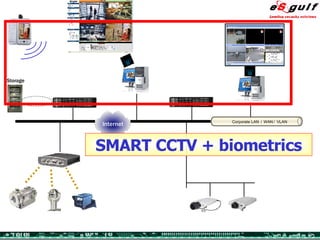
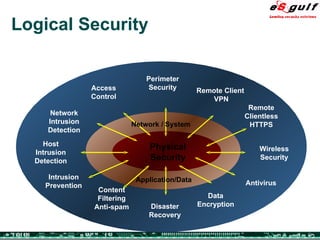
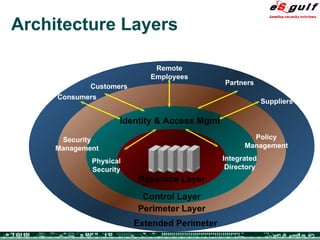
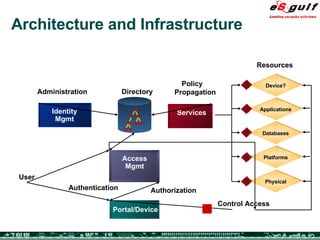
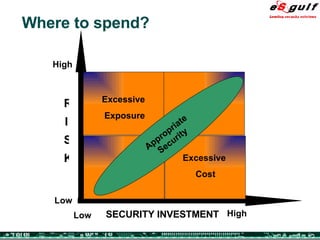
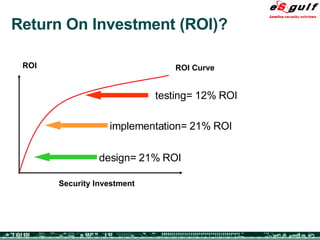
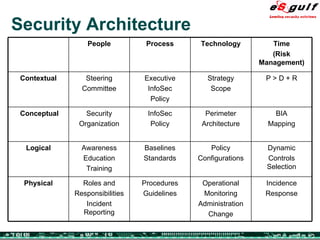
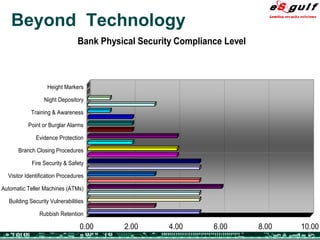
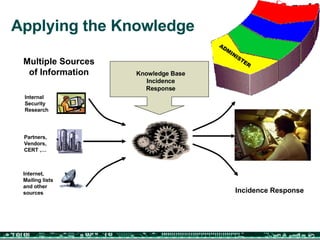
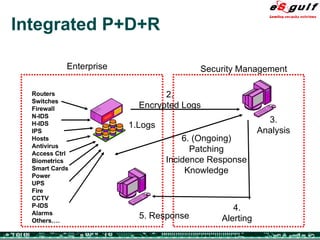
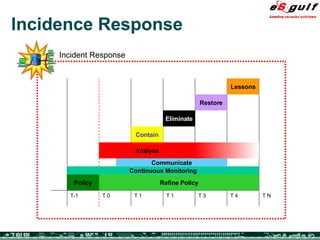
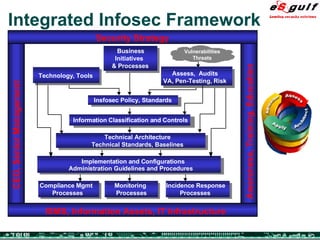
The document discusses the integration of physical and logical security, focusing on the need for a cohesive approach that protects both physical assets and information systems. It outlines various security challenges, including human errors and technological vulnerabilities, while emphasizing the importance of layered security and continuous monitoring. Additionally, it highlights the benefits of integrated security management for reducing vulnerabilities, cost savings, and enhancing overall business security.