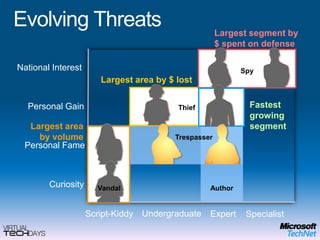
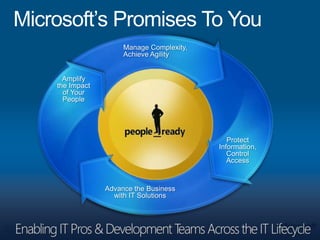
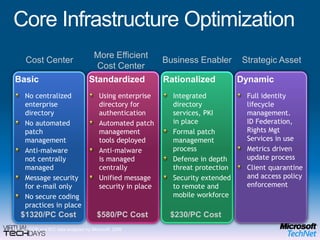
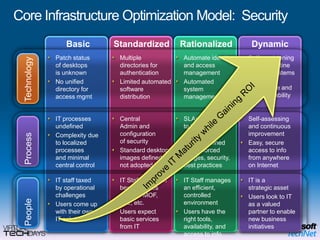
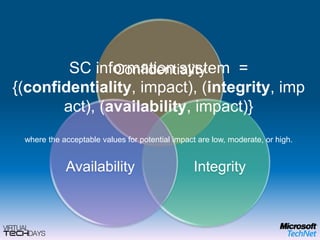
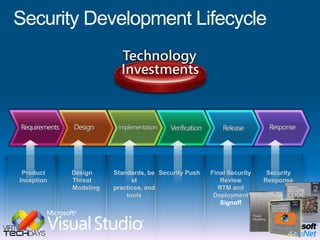
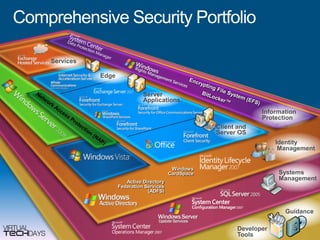
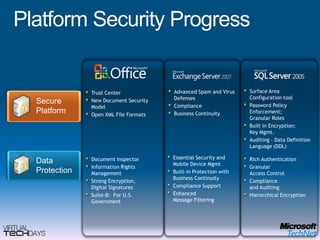
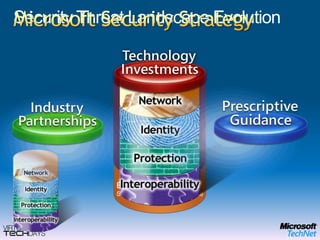
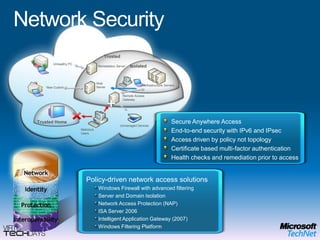
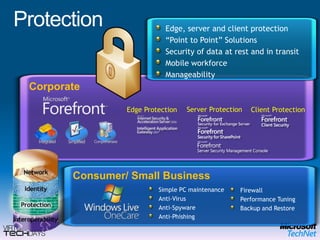
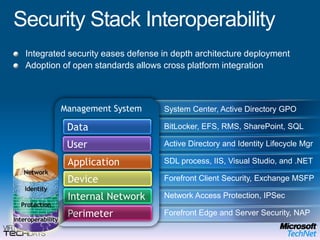
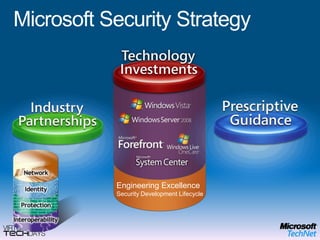
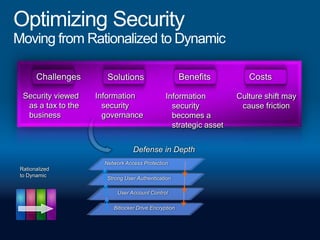
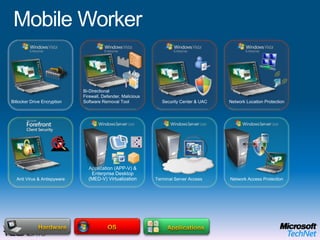
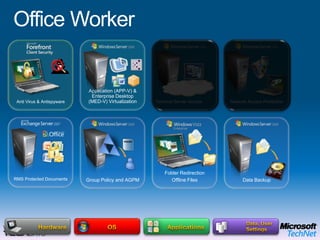
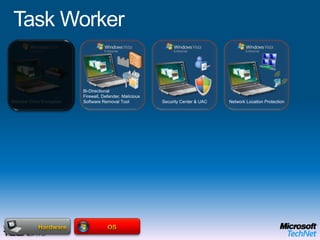
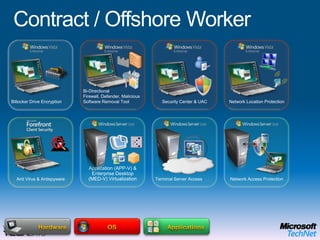
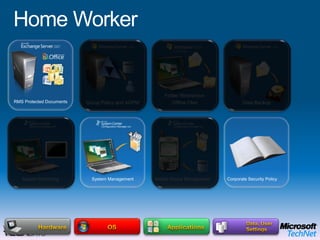
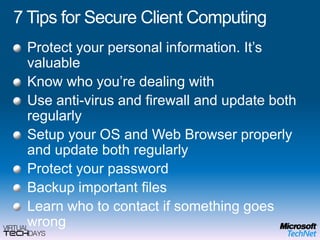
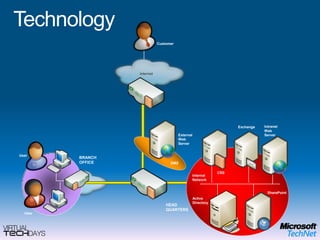
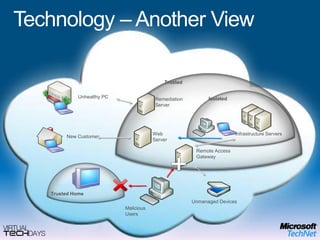
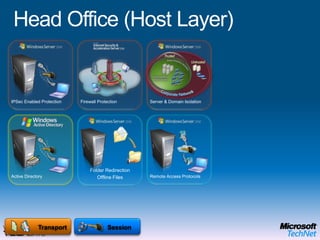
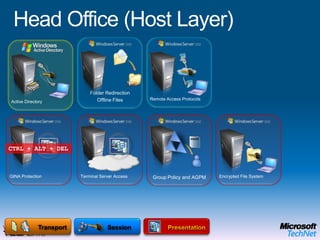
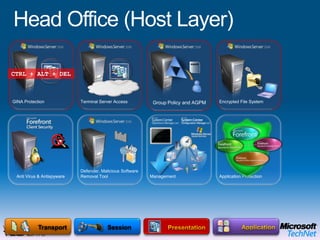
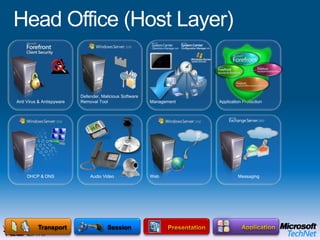
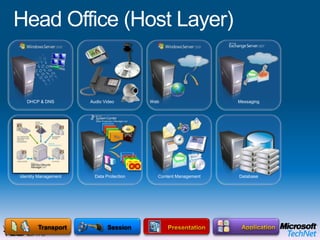
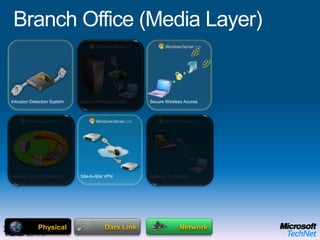
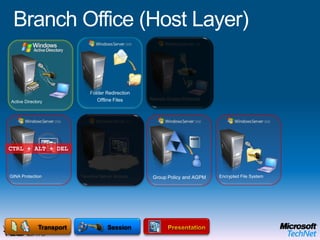
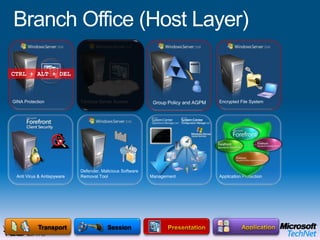
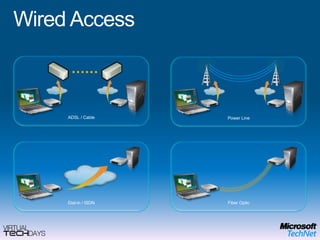
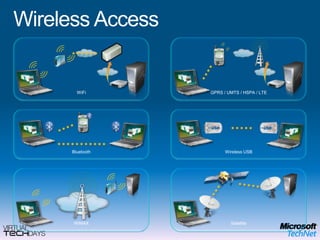
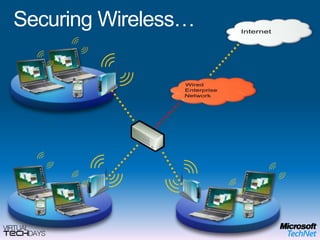
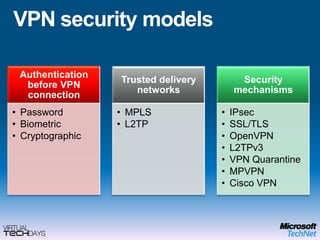
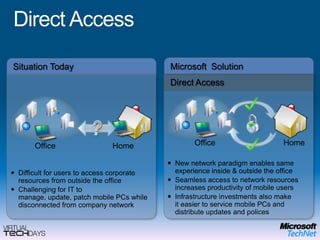
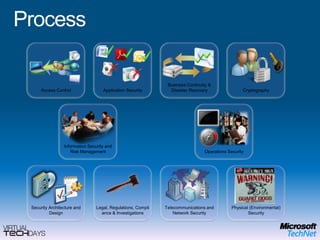
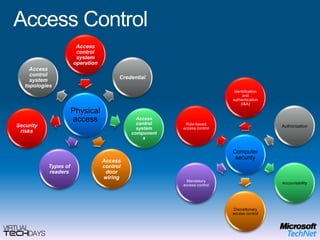
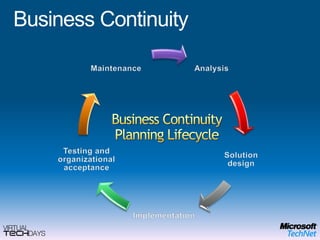
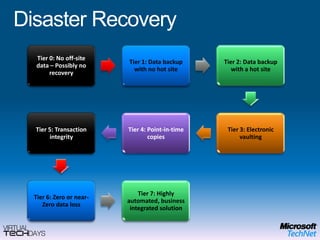
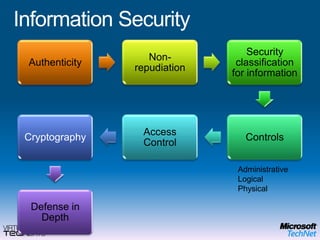
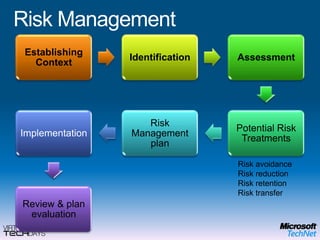
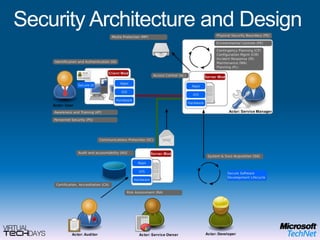
This document provides a high-level overview of platform security and the evolving security landscape. It discusses increasing demands for access and escalating security threats. It outlines the evolution of threats from local area networks to the internet era to today. It also discusses different types of attackers and their motivations. The document proposes addressing security threats by focusing on technology, processes, and people. It promotes an infrastructure optimization approach to security and discusses Microsoft's security strategy and development lifecycle.