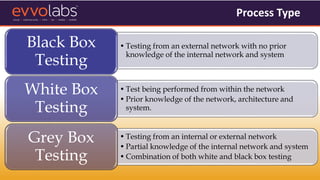
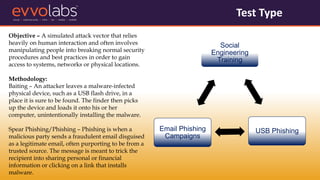
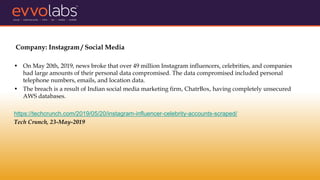
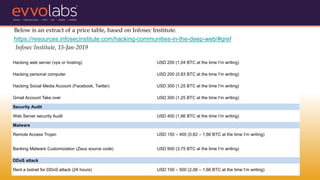
VAPT (Vulnerability Assessment and Penetration Testing) involves evaluating systems and networks to identify vulnerabilities, configuration issues, and potential routes of unauthorized access. It is recommended for SMEs due to common security issues like phishing and ransomware attacks targeting them. The document outlines the types of VAPT testing, why SMEs need it, example data breaches, and estimated costs of common cyber attacks and security services.