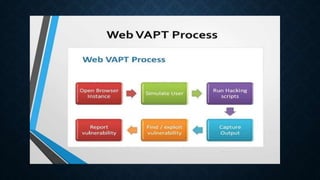
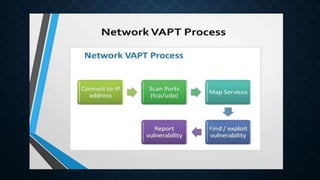
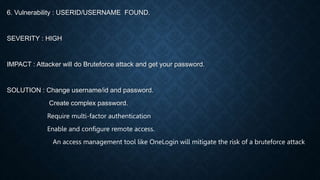
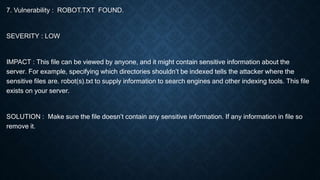
The document provides information on vulnerability assessment and penetration testing. It defines vulnerability assessment as a systematic approach to finding security issues in a network or system through manual and automated scanning. Penetration testing involves exploring and exploiting any vulnerabilities that are found to confirm their existence and potential damage. The document outlines the types of testing as blackbox, graybox, and whitebox. It also lists some common tools used for testing like Nmap, ZAP, Nikto, WPScan, and HostedScan. Finally, it provides examples of specific vulnerabilities found and their solutions, such as outdated themes/plugins, backup files being accessible, and SQL injection issues.