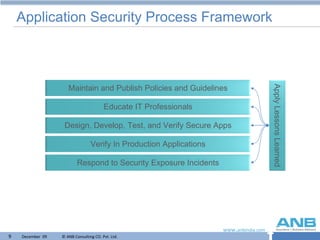
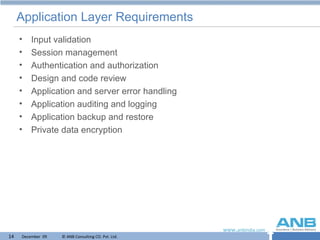
The document discusses the importance of conducting application security reviews to identify vulnerabilities. It outlines best practices for application security such as input validation, access controls, encryption, and ongoing patching and monitoring. The presentation notes that many applications are found to have significant security flaws and that securing both applications and infrastructure is needed for effective security.


















![Un-validated Input Attack Exploitation of implied trust relations Instead of: [email_address] Attacker inputs: ////////////////////////////////////////////////// Exploits lack of boundary checkers on back-end application](https://image.slidesharecdn.com/applicationsecurityreview5dec09final-12610604861927-phpapp01/85/Application-Security-Review-5-Dec-09-Final-21-320.jpg)

