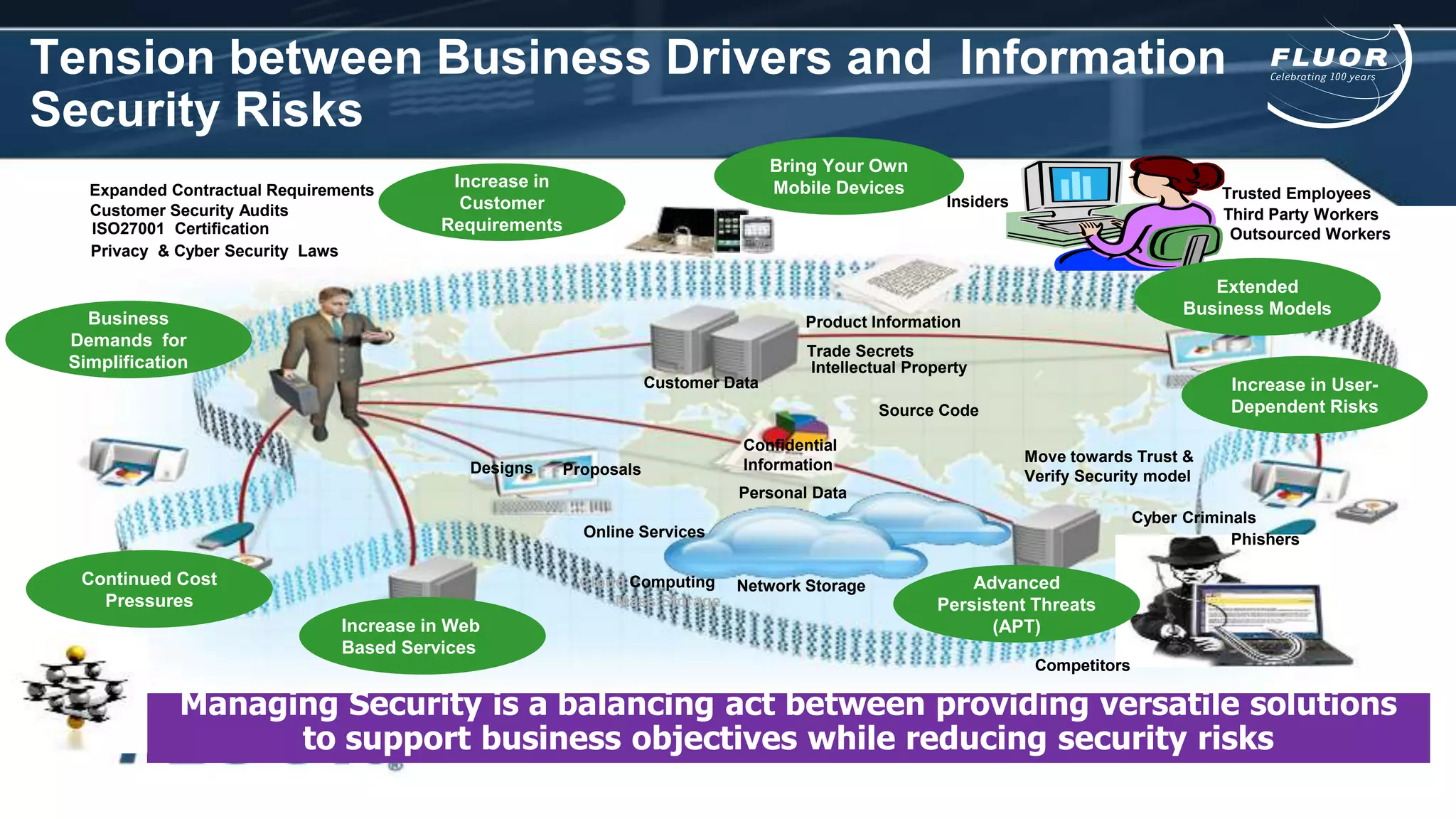
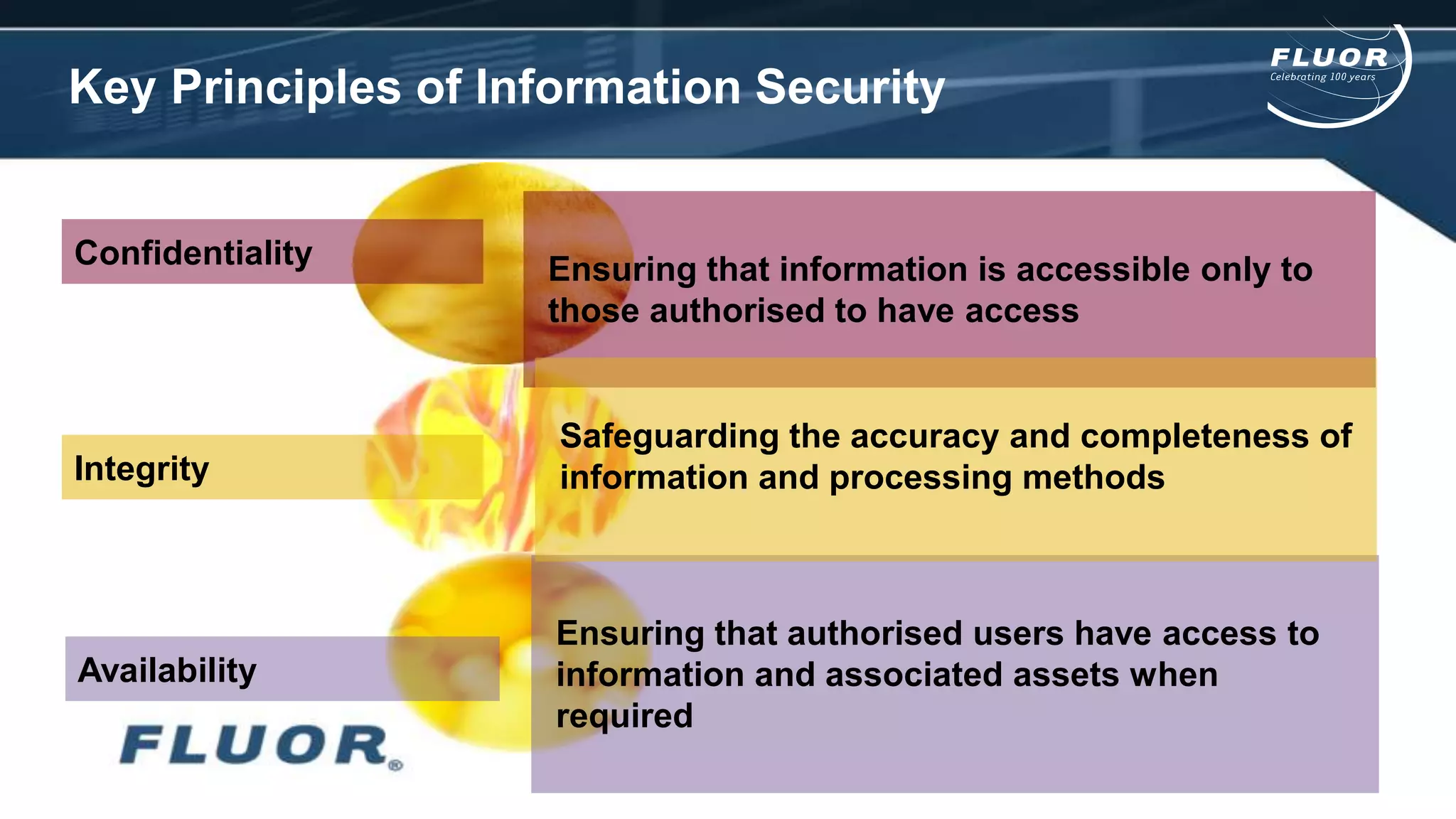
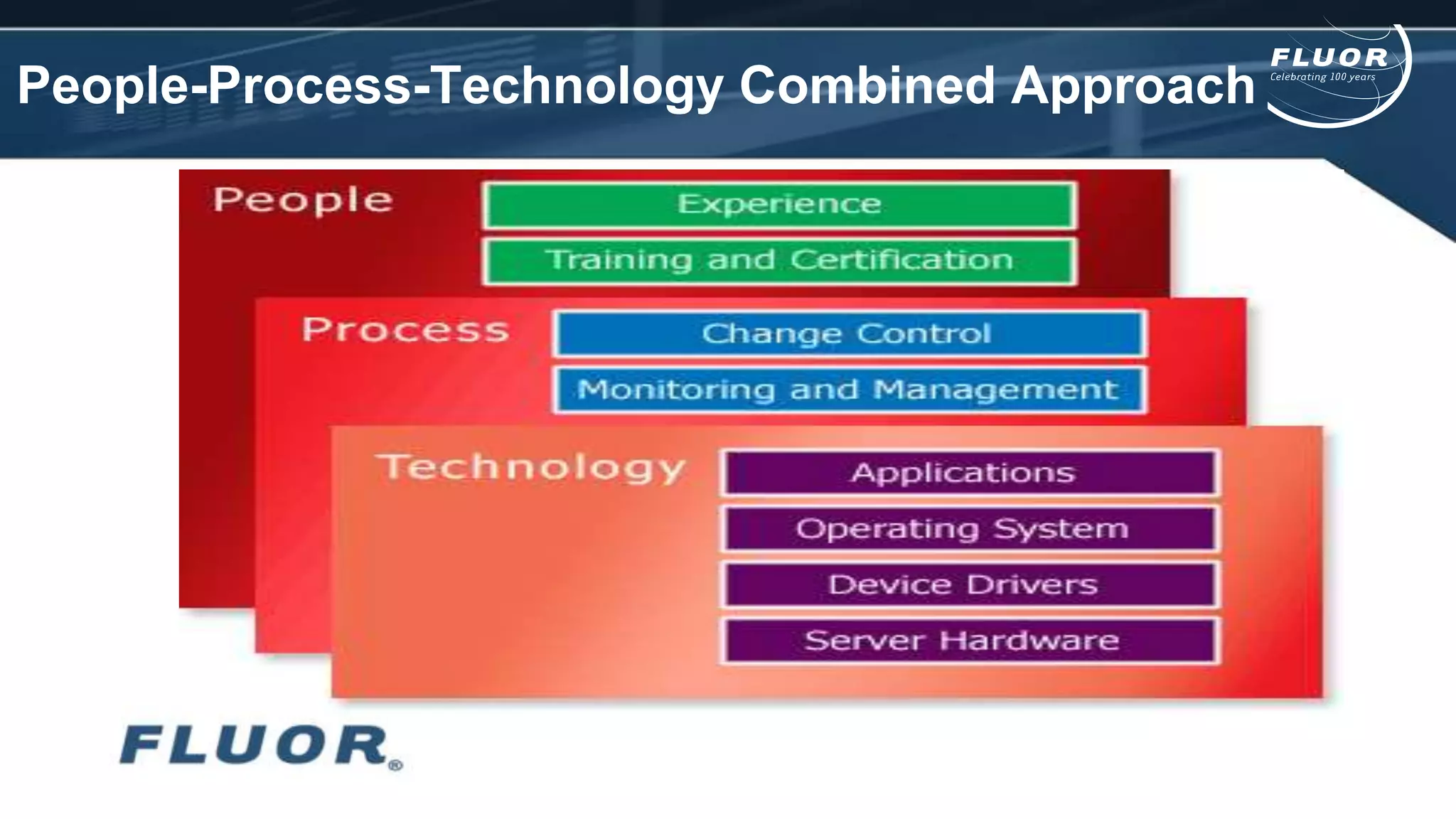
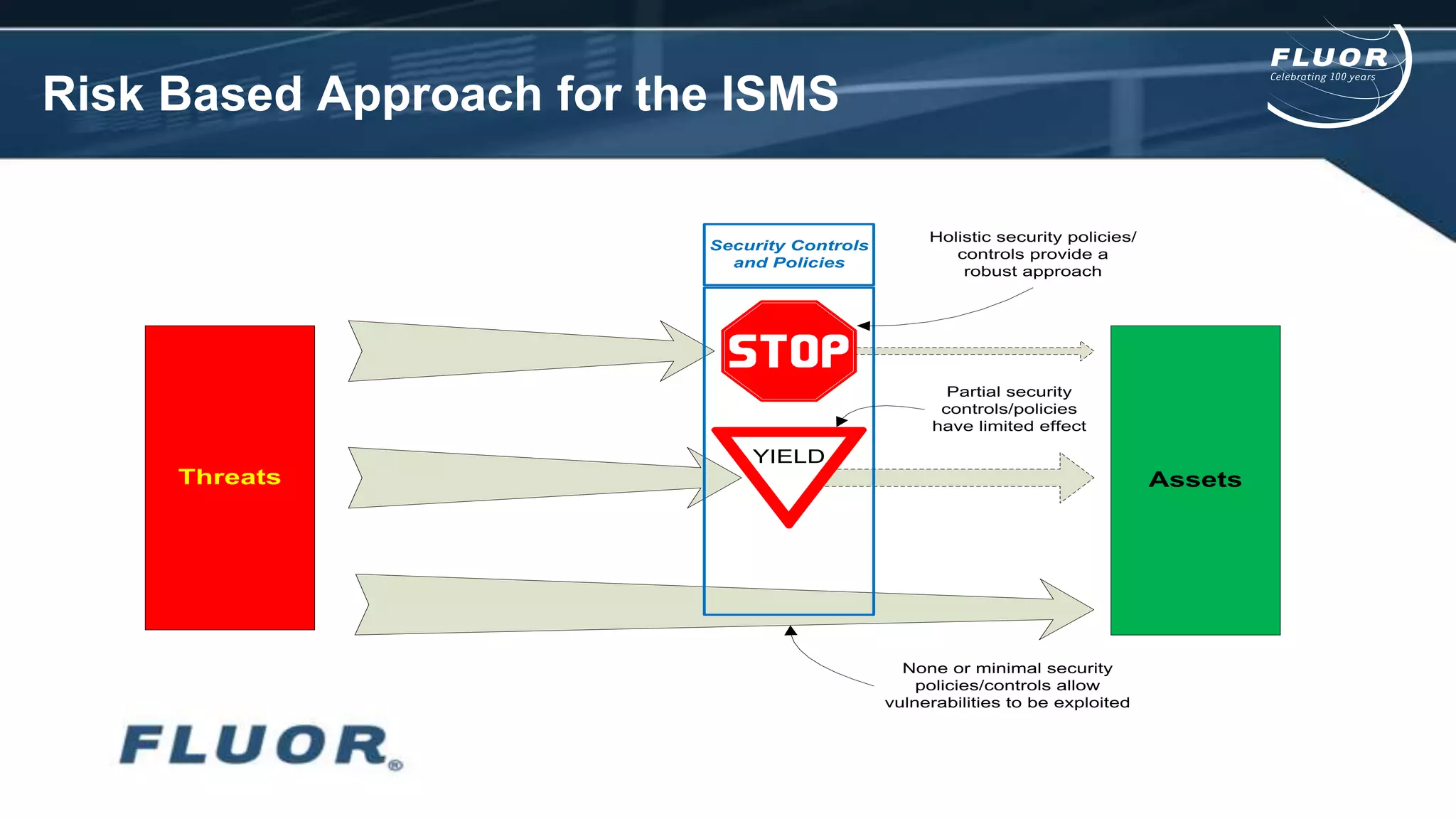
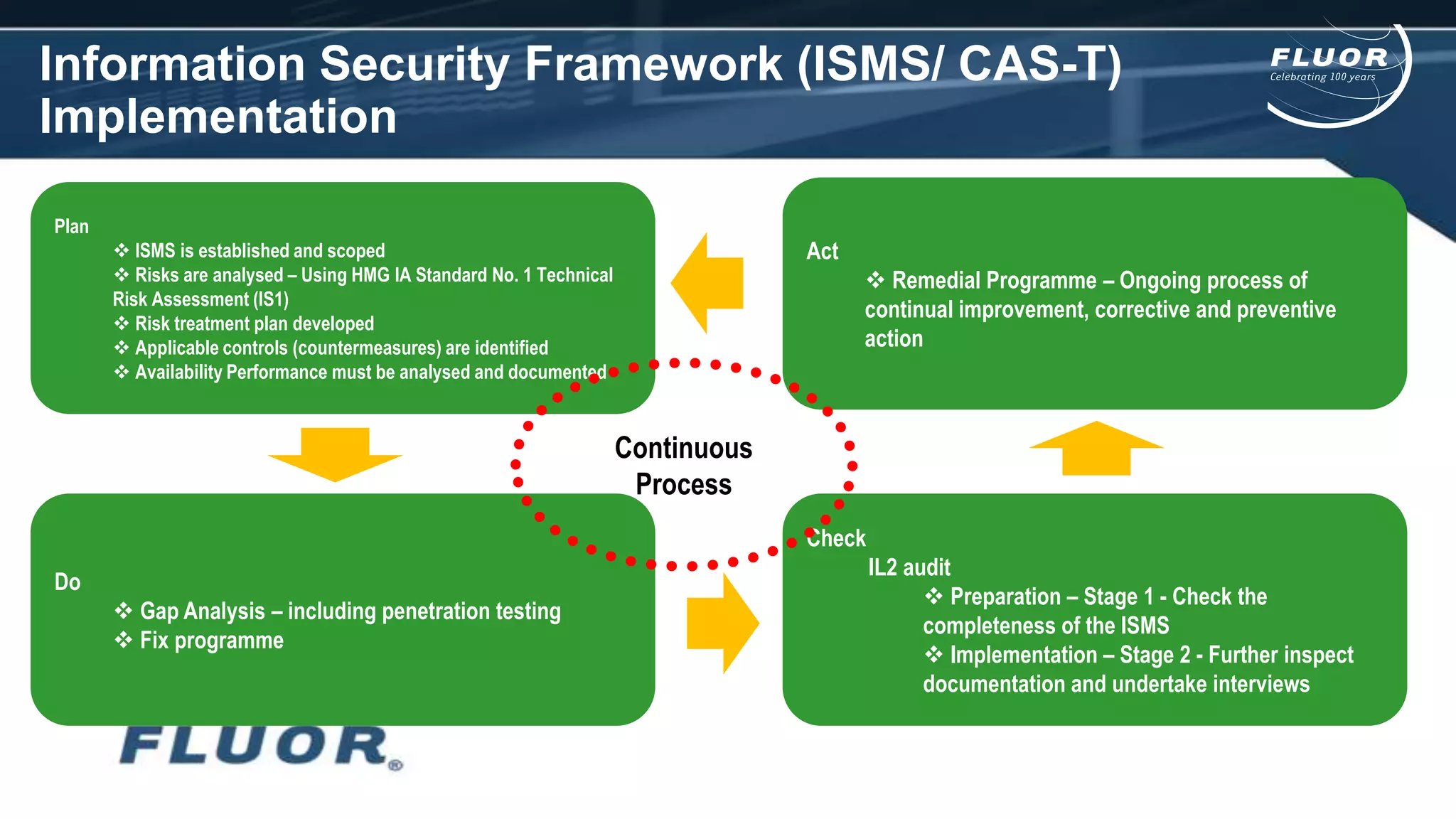
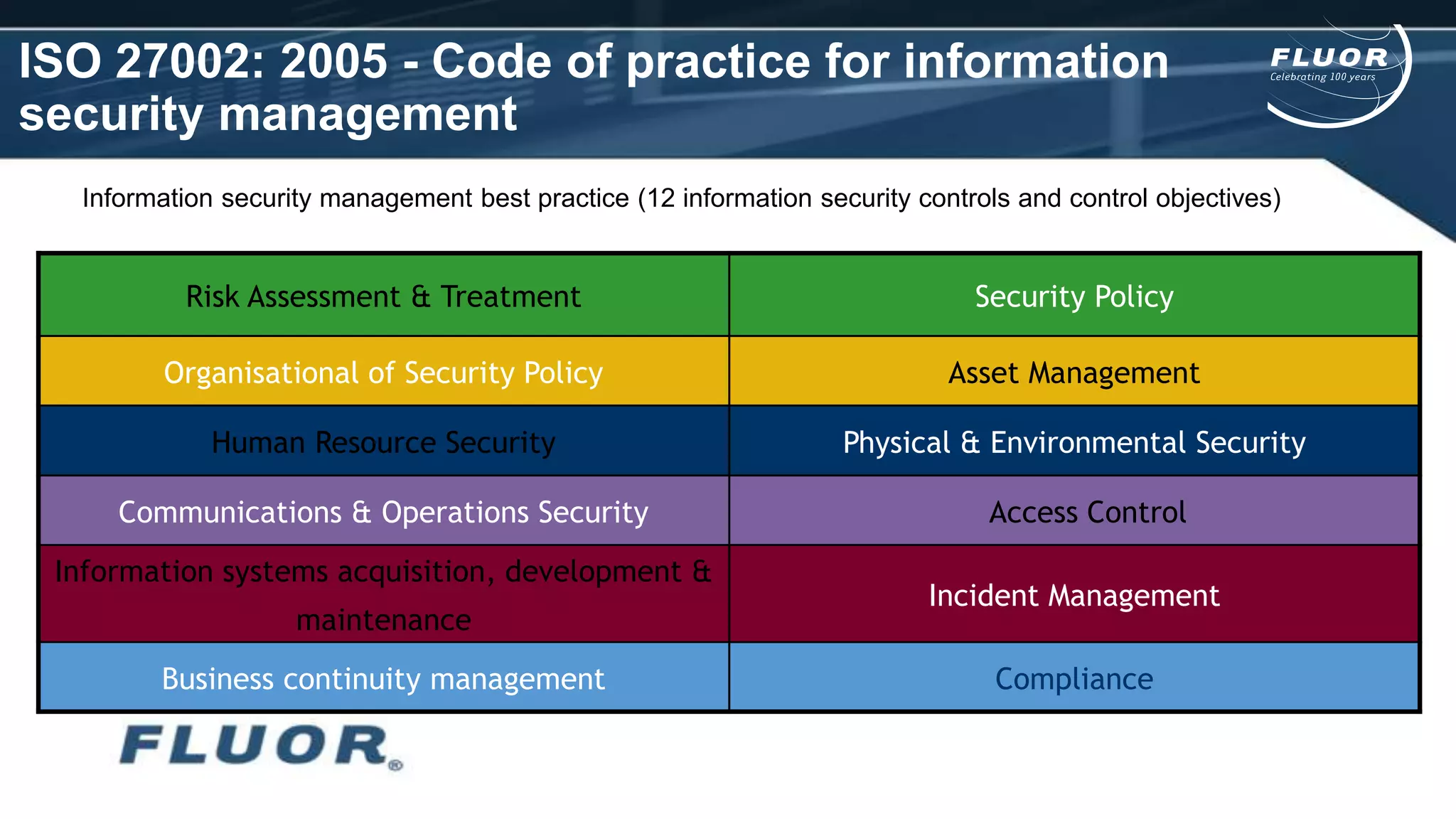
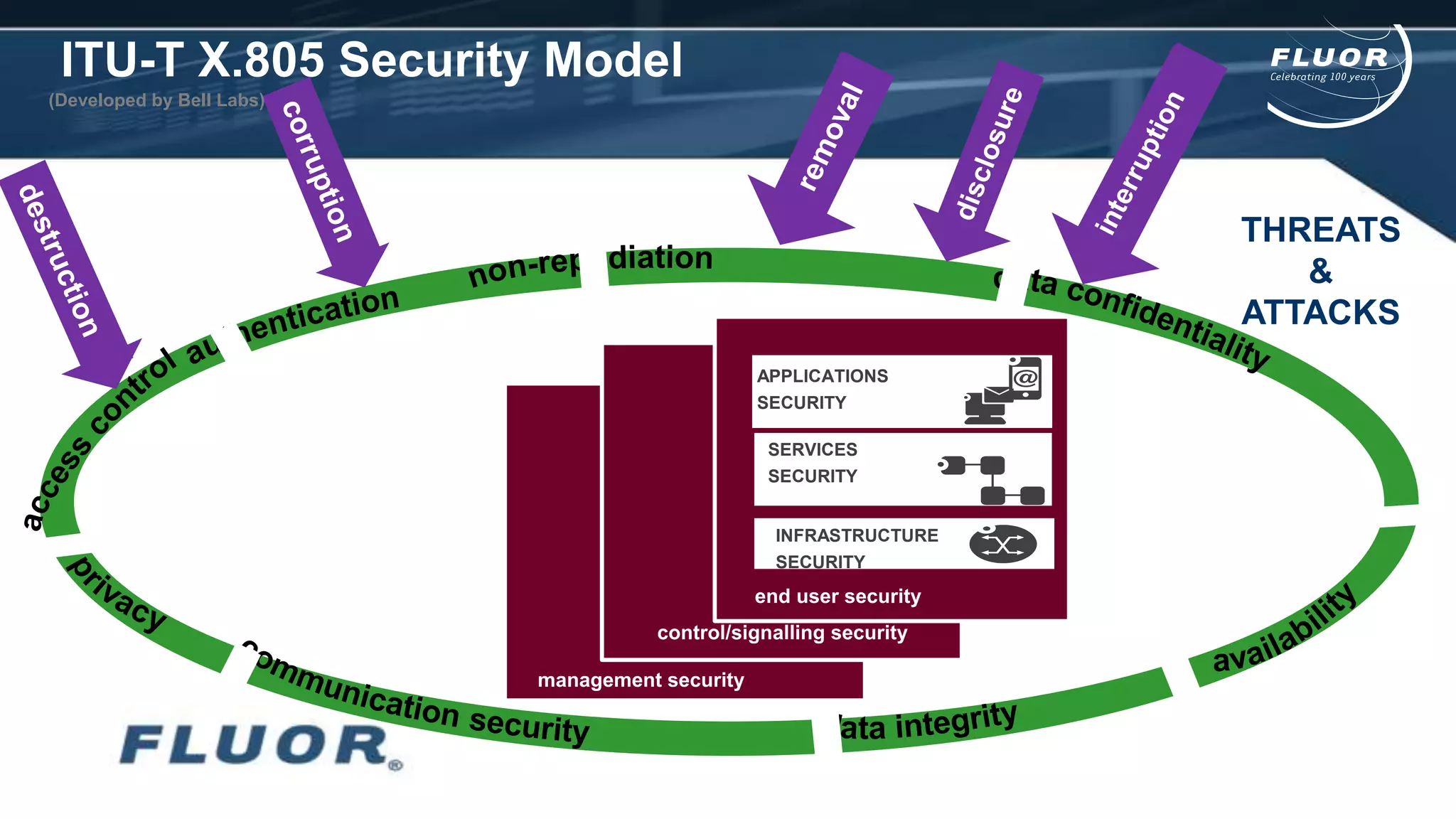
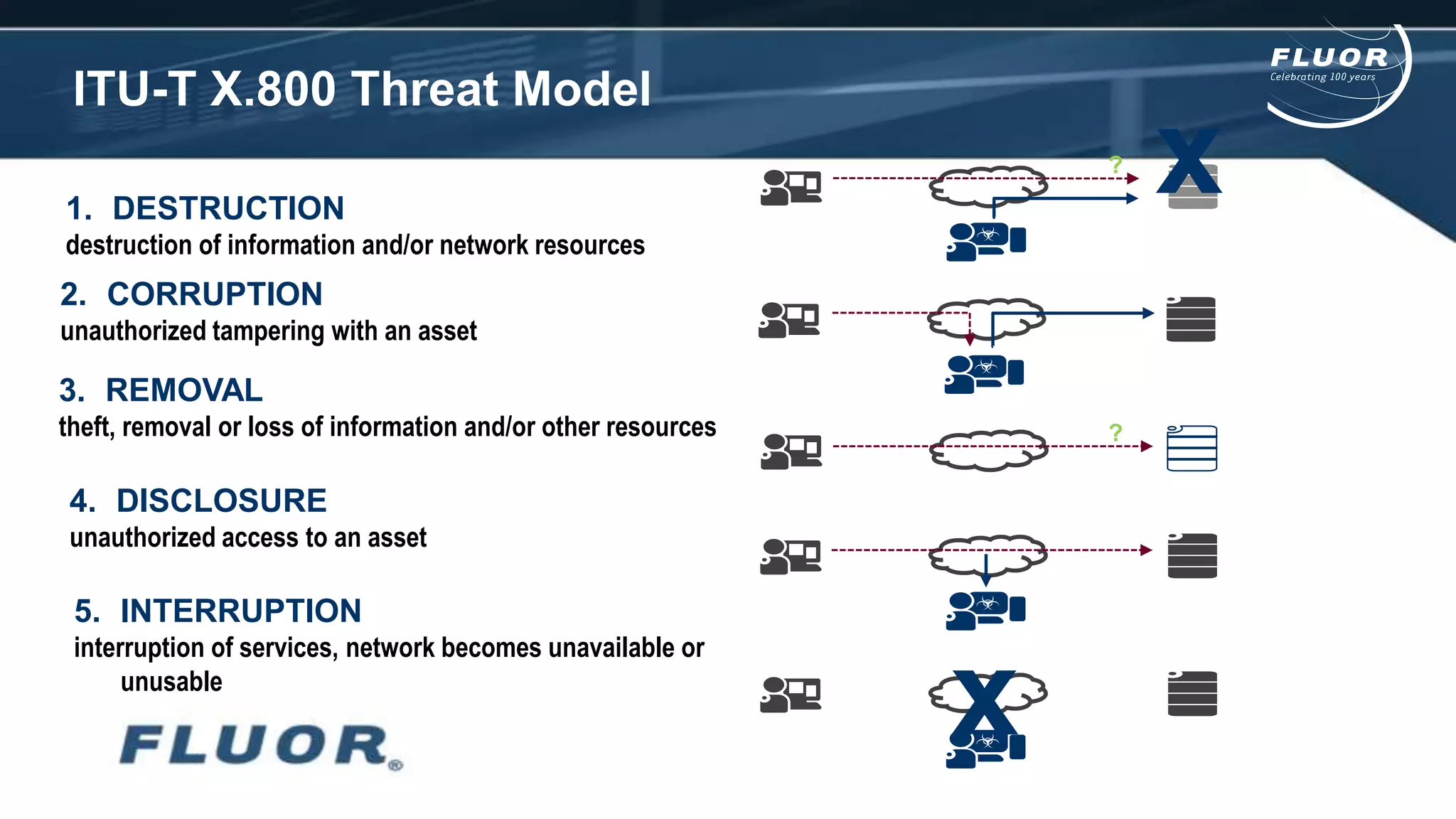
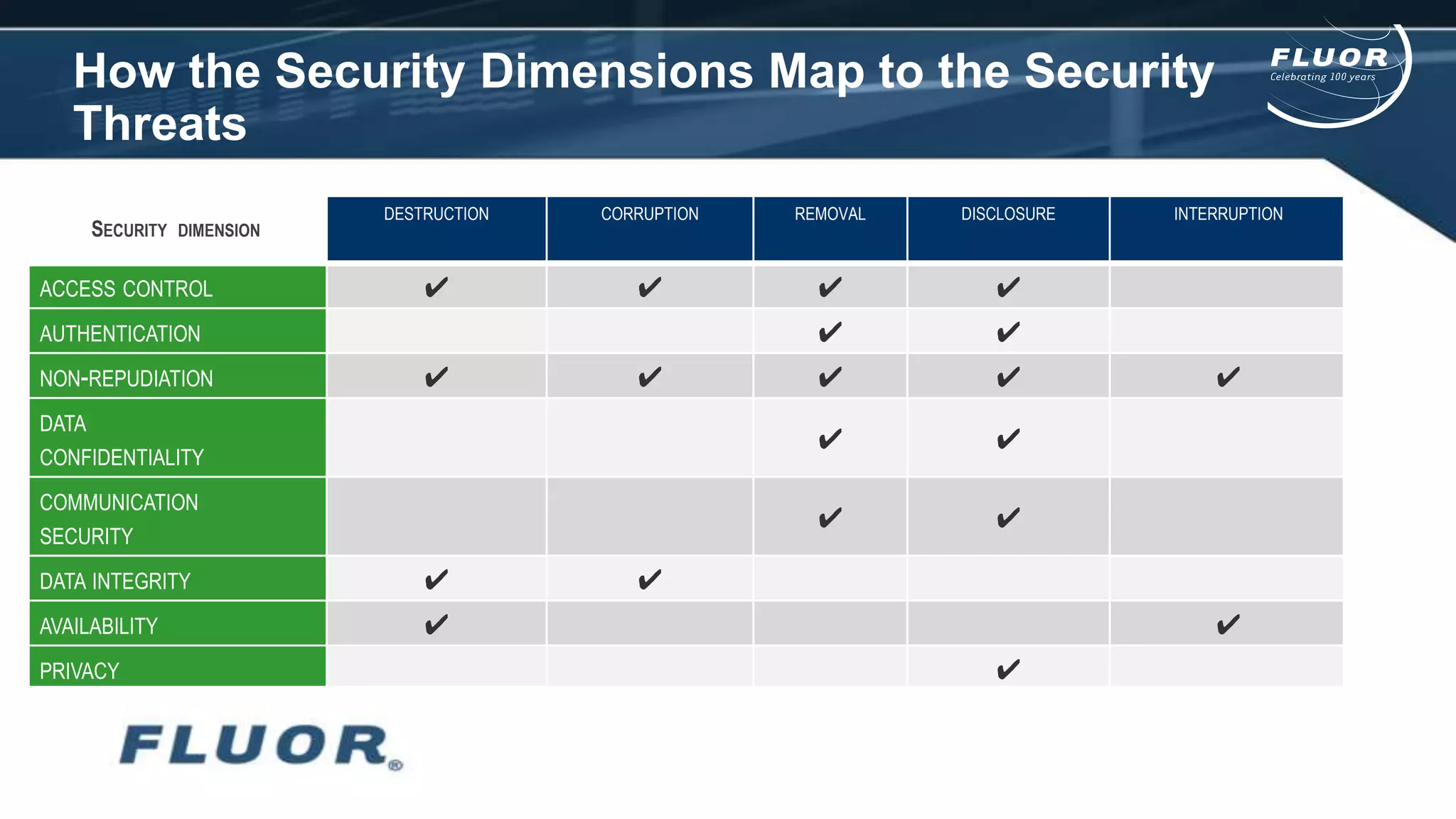
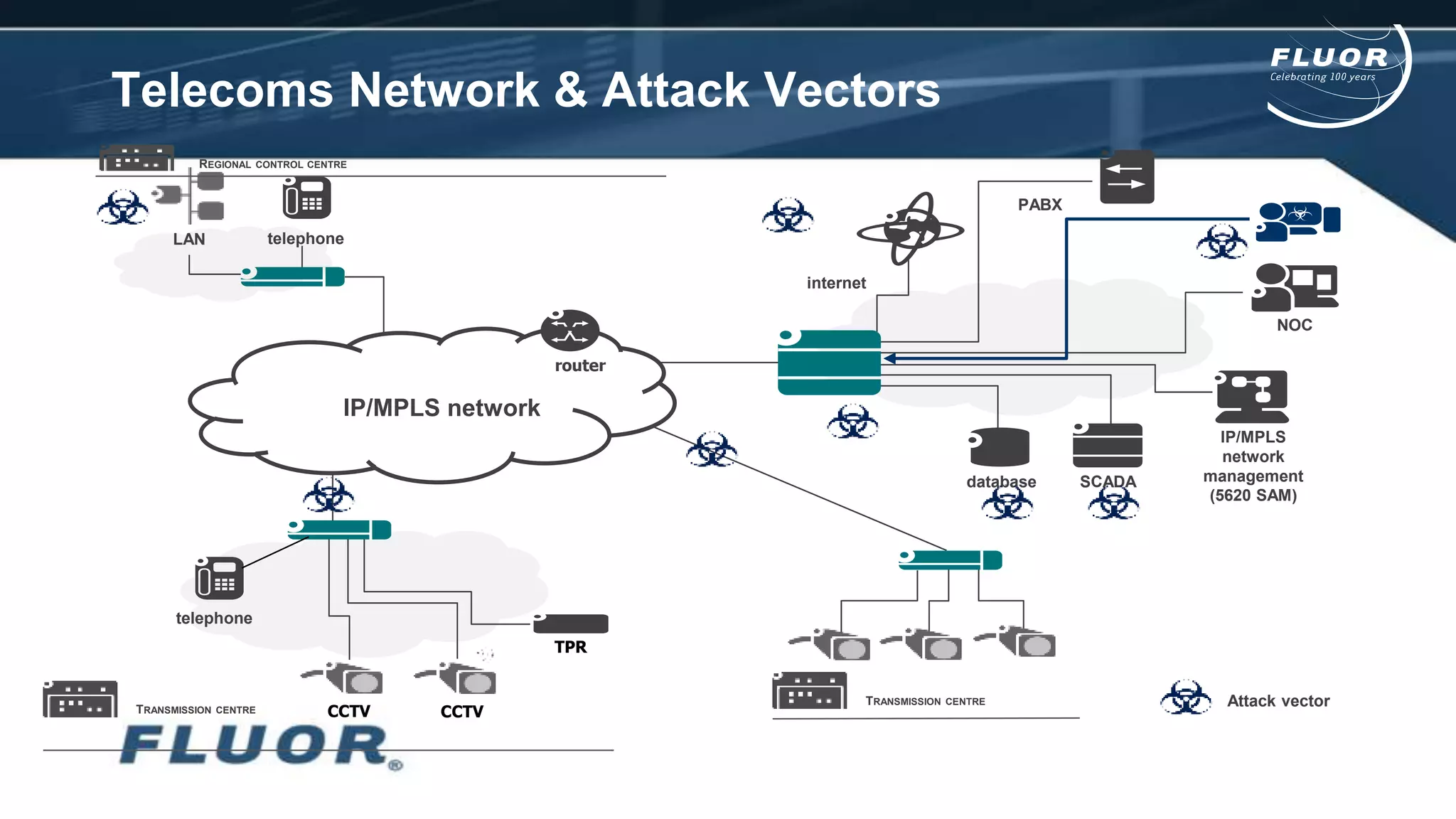
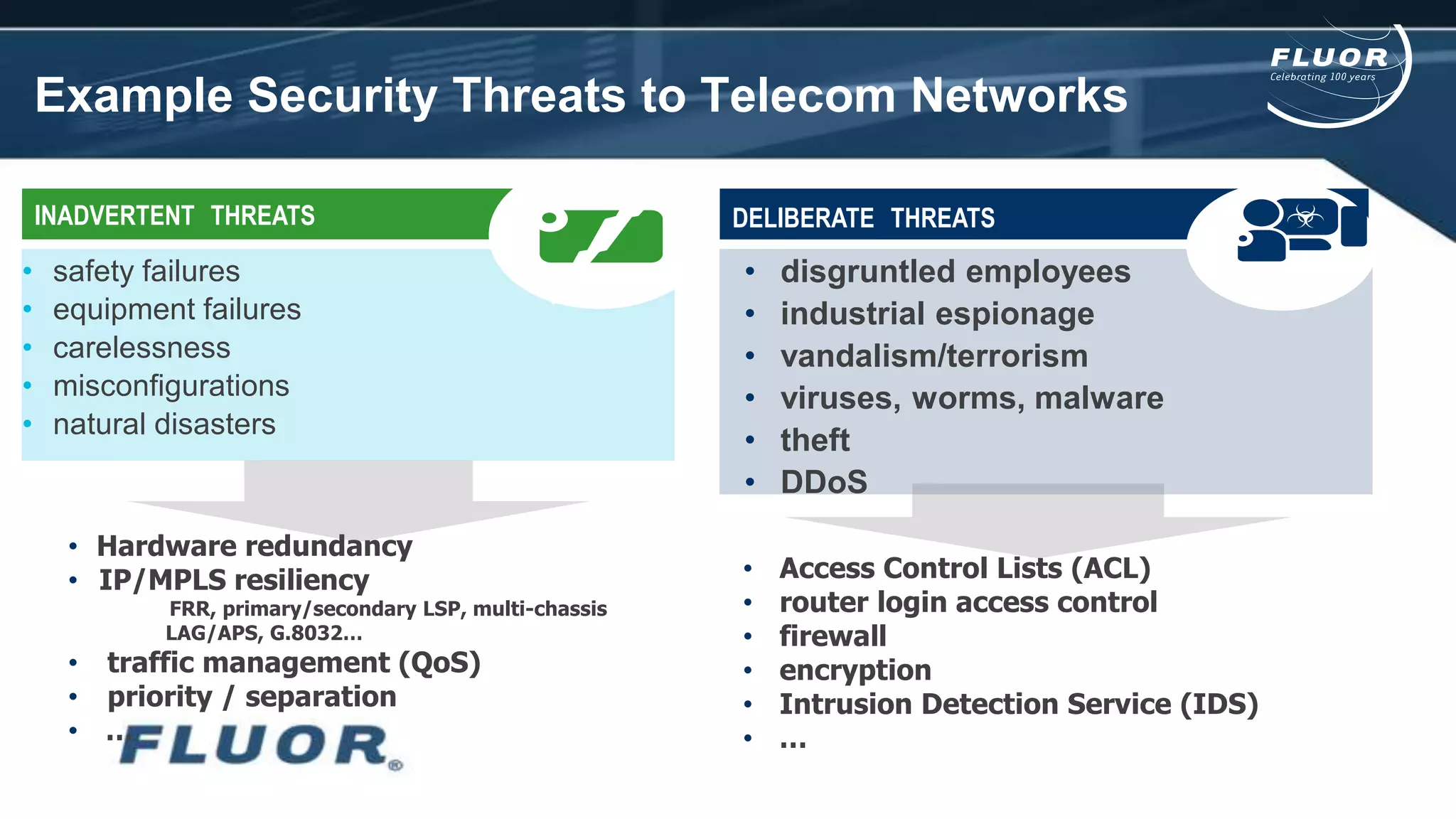
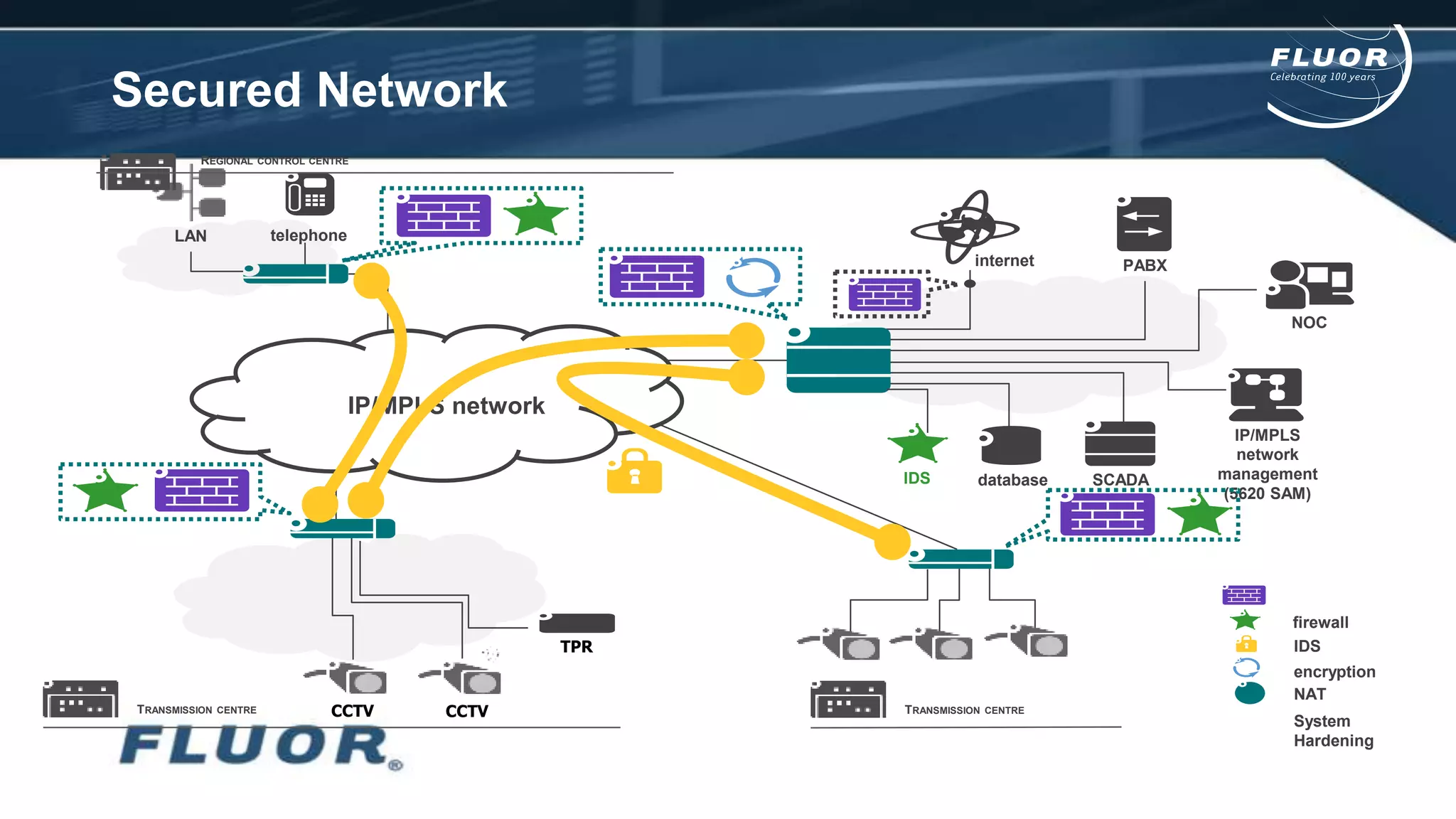
This document discusses information security risks and implementation on an IP/MPLS network. It outlines the tension between business needs and security risks, and key principles of information security including confidentiality, integrity and availability. It recommends a people-process-technology approach and risk-based information security management system following ISO 27001 and 27002 best practices. Various security threats to telecommunications networks are analyzed and addressed through encryption, firewalls, intrusion detection systems and network hardening. The conclusion emphasizes building a robust security governance structure, adopting a risk-based approach, following good practices, managing both technical and non-technical controls, and promoting security awareness.