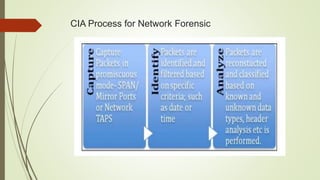
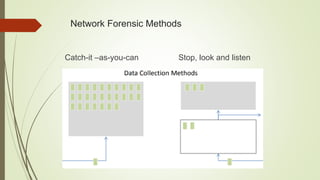
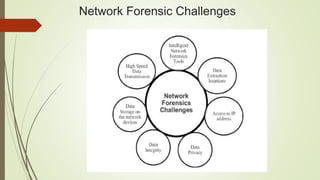
The document discusses network forensics as a branch of digital forensics that involves monitoring and analyzing network traffic to gather evidence and detect intrusions. It outlines the steps in network forensic examination, including identification, preservation, collection, examination, analysis, presentation, and incident response, as well as methods applicable across various network protocols. It also highlights the functions and advantages of network forensic analysis tools while noting challenges in developing intelligent tools for specific traffic analysis.