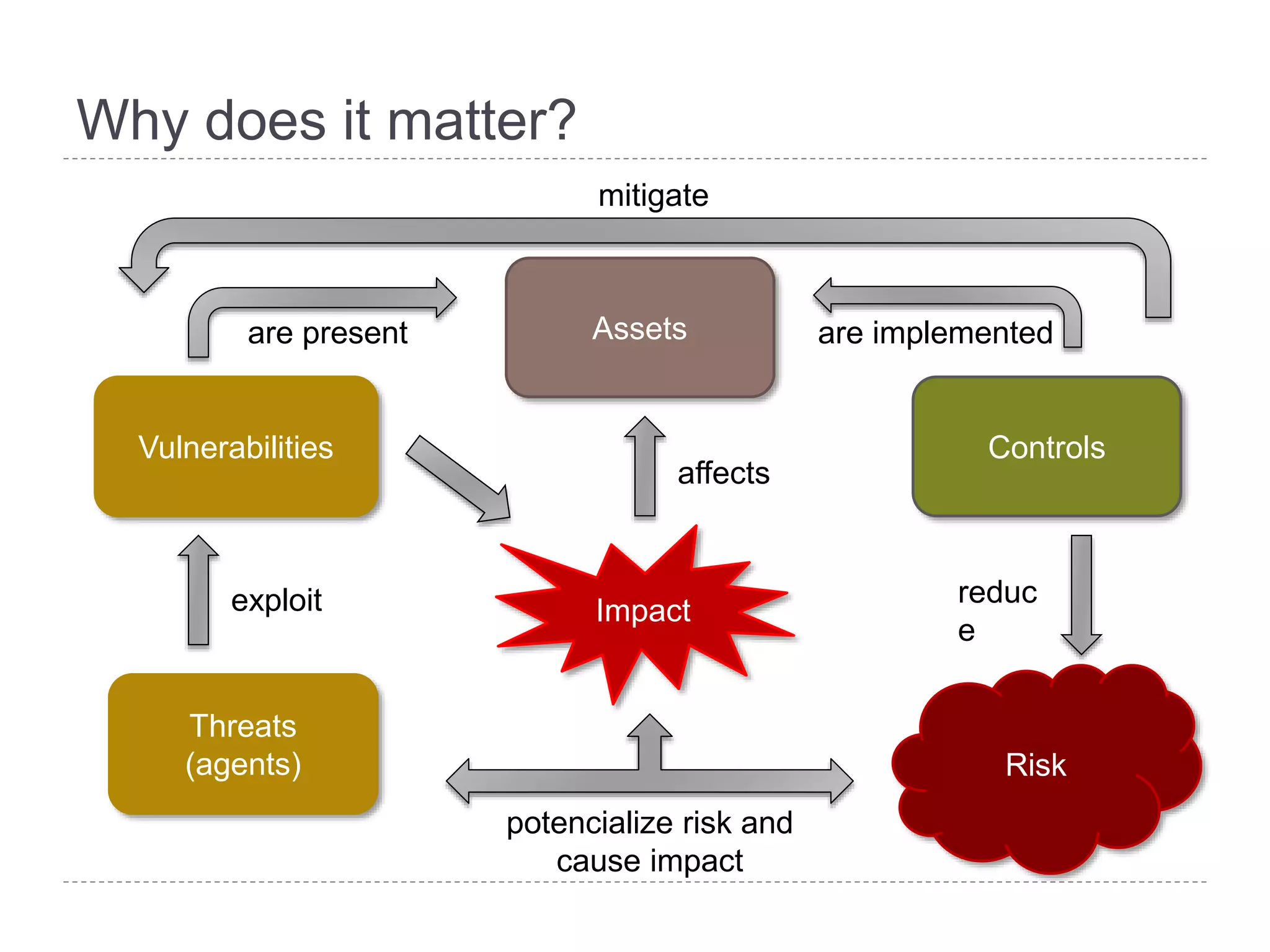
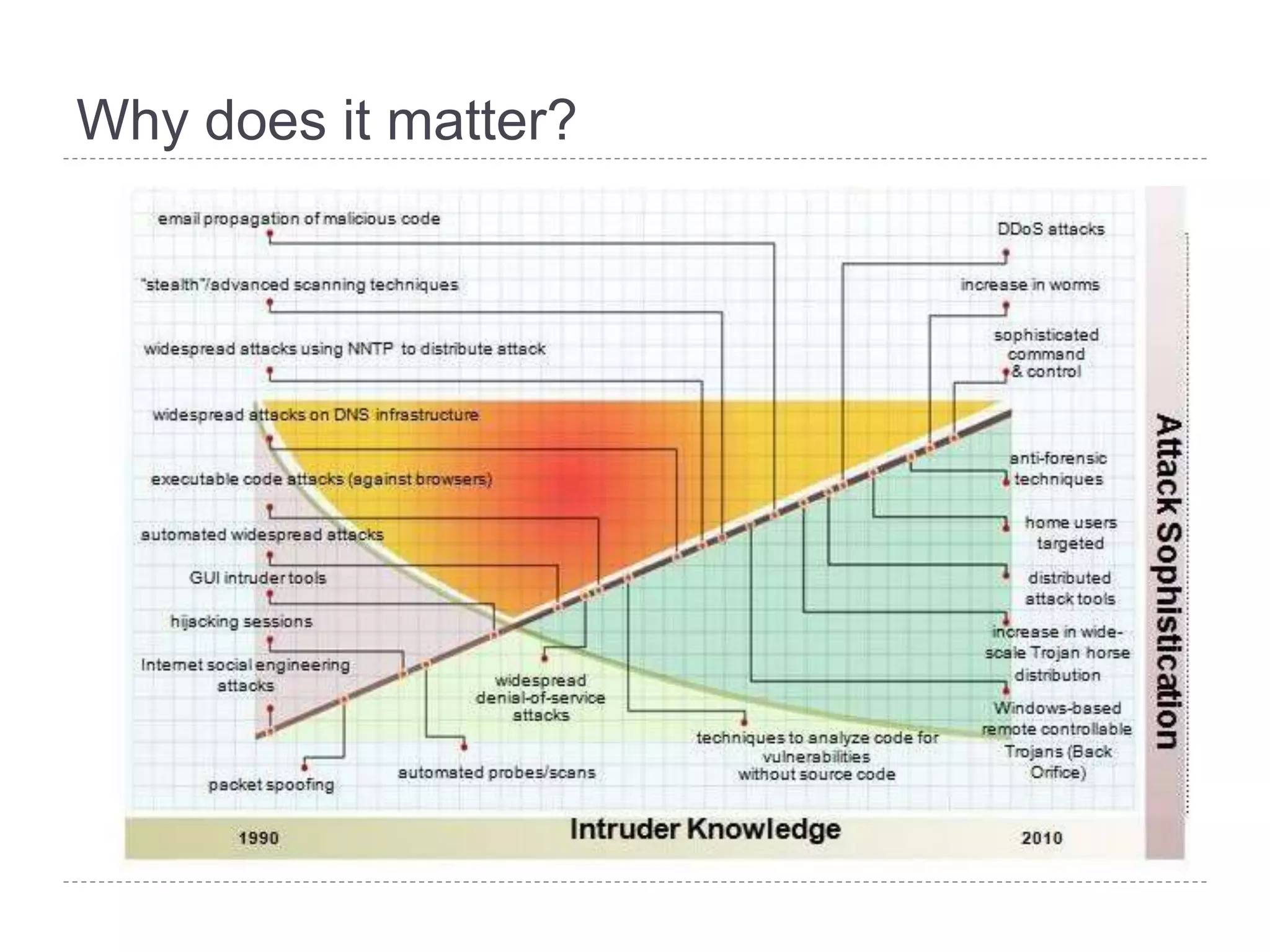
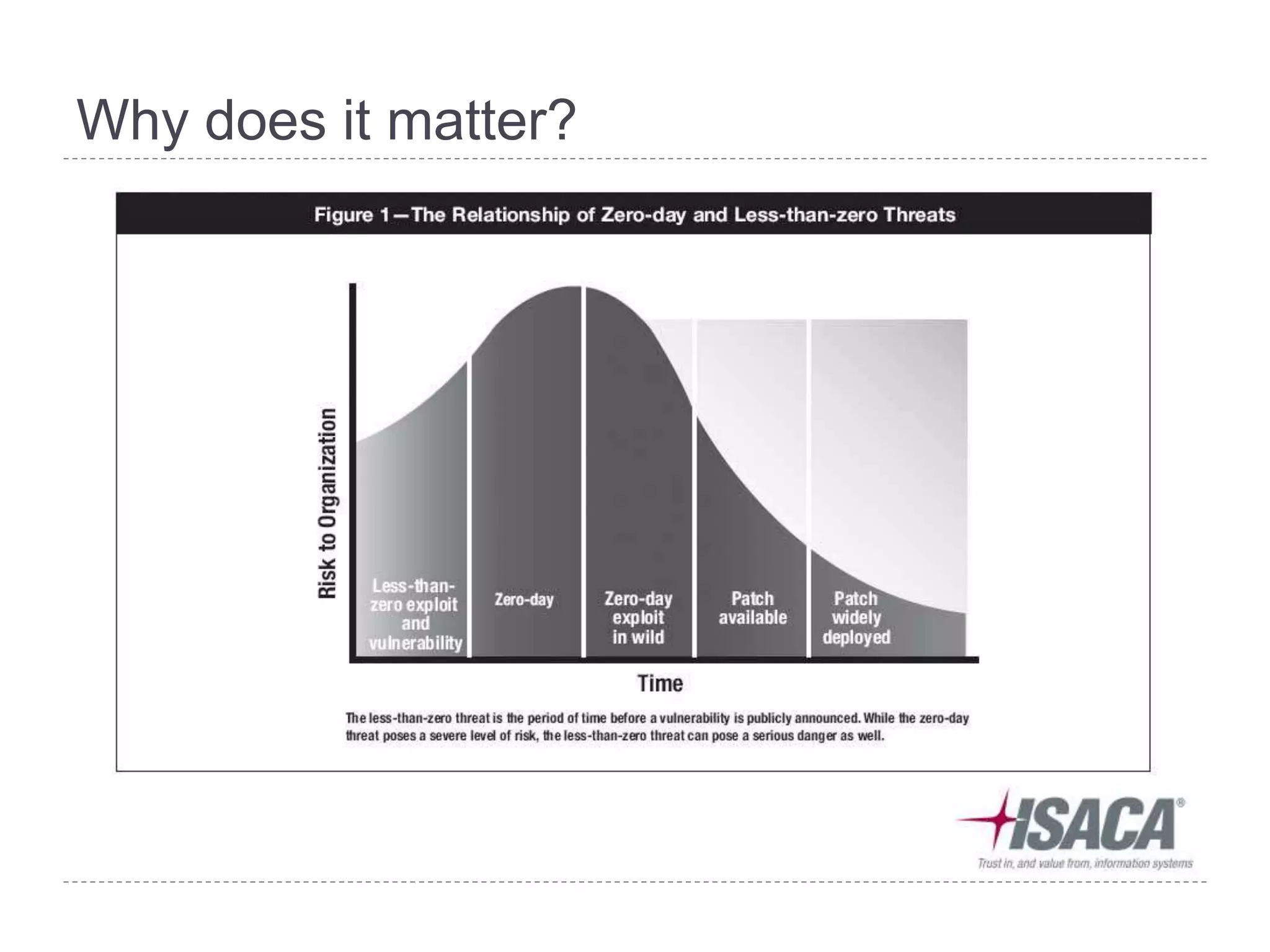
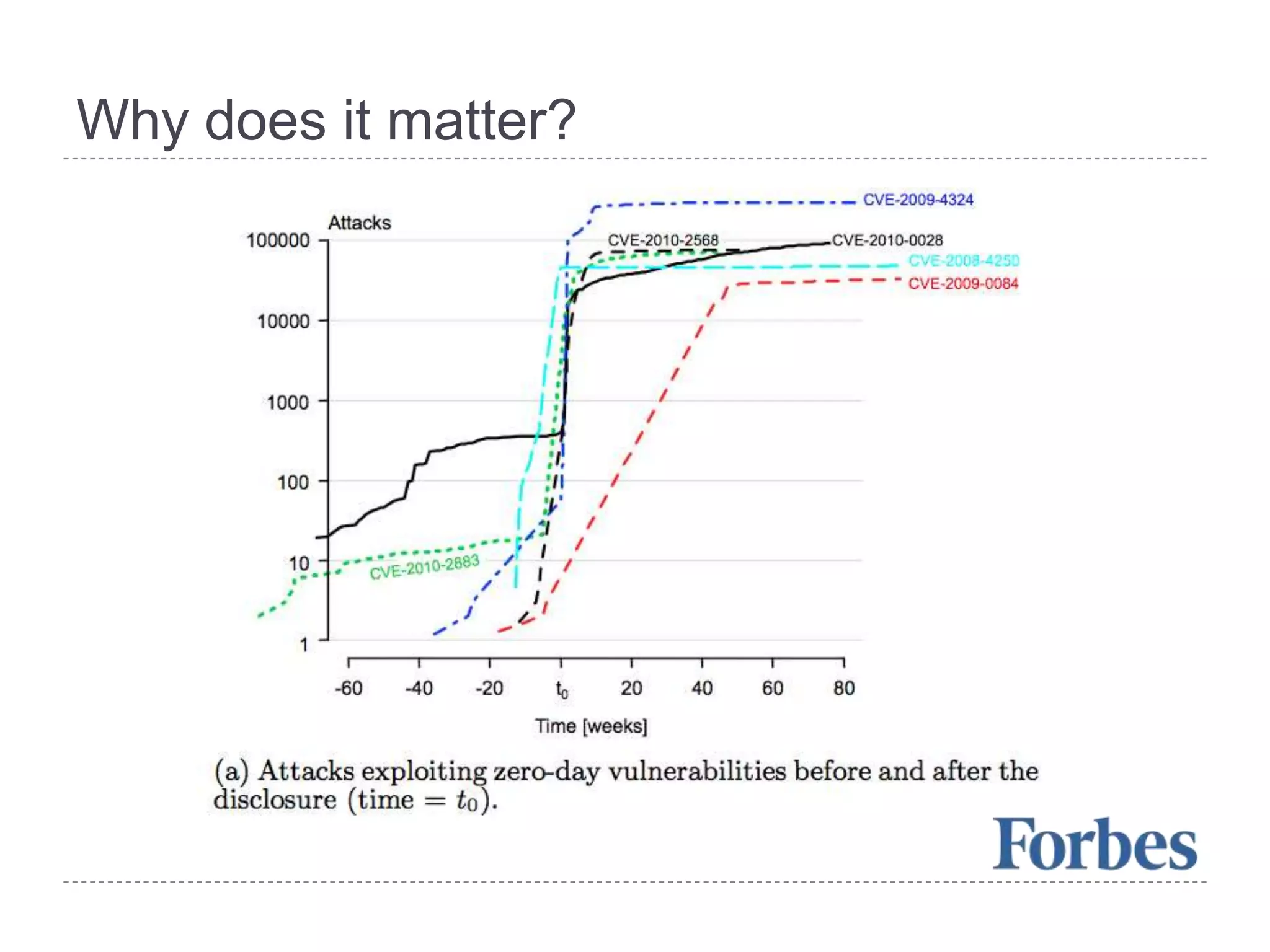
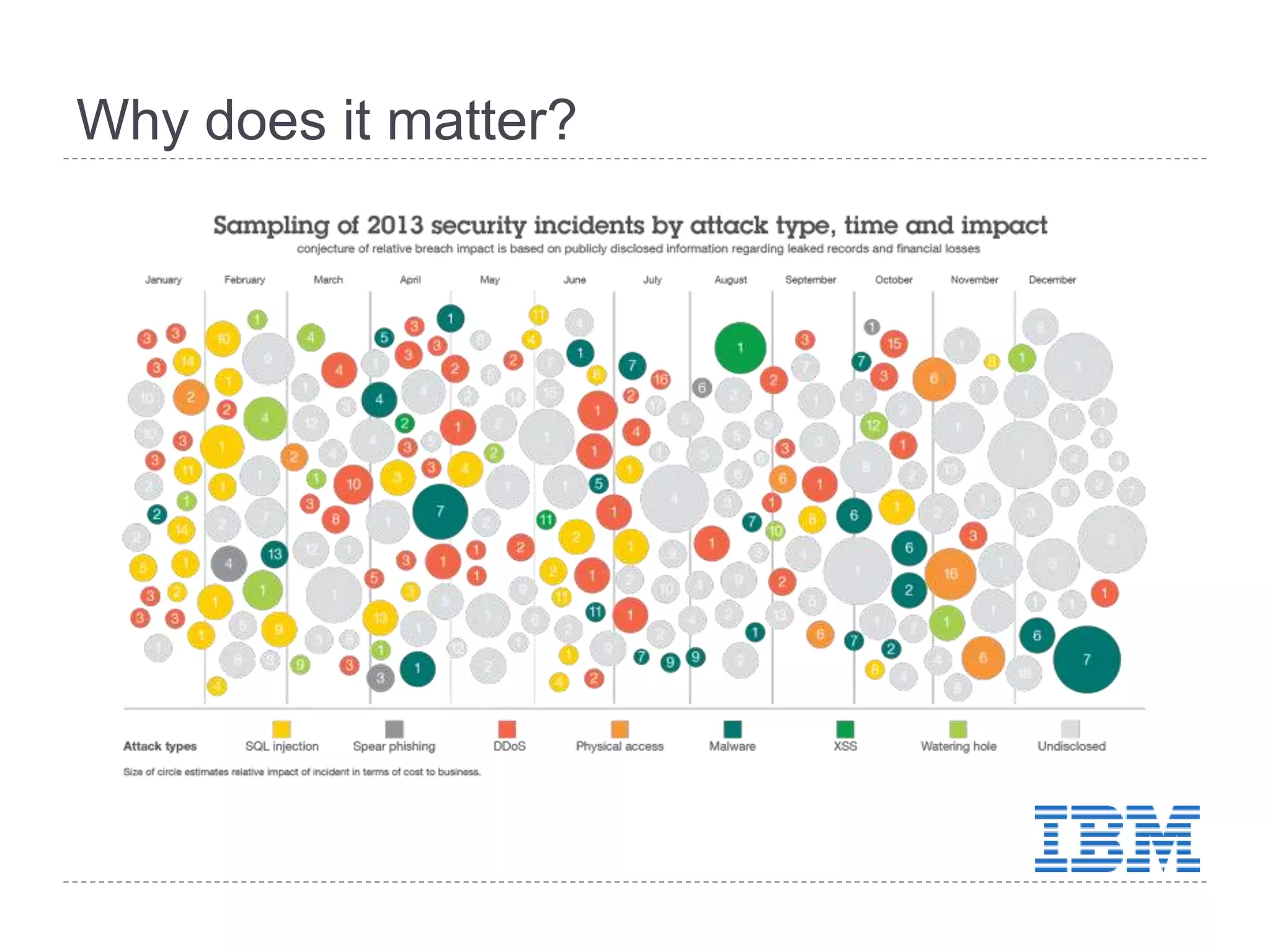
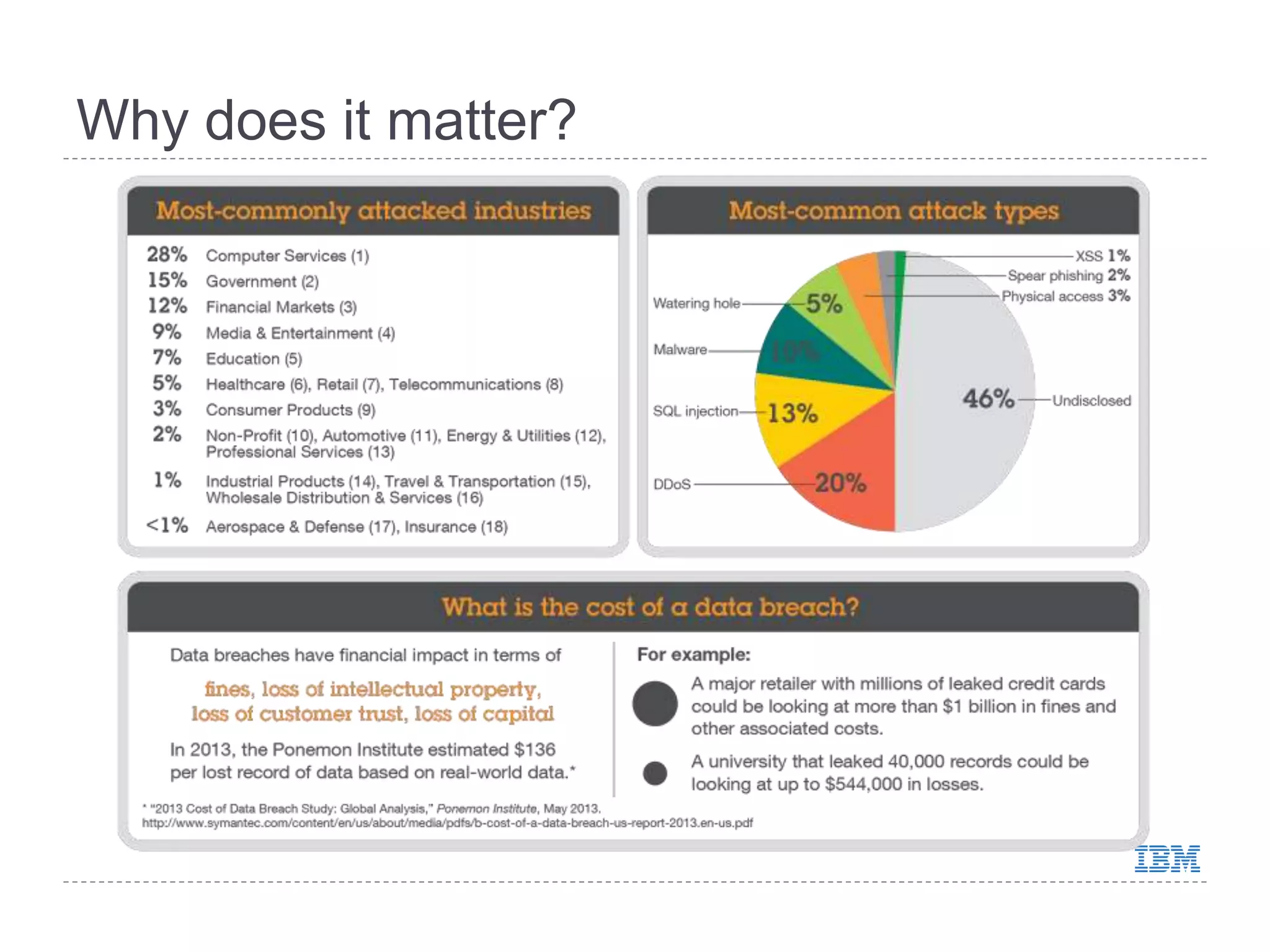
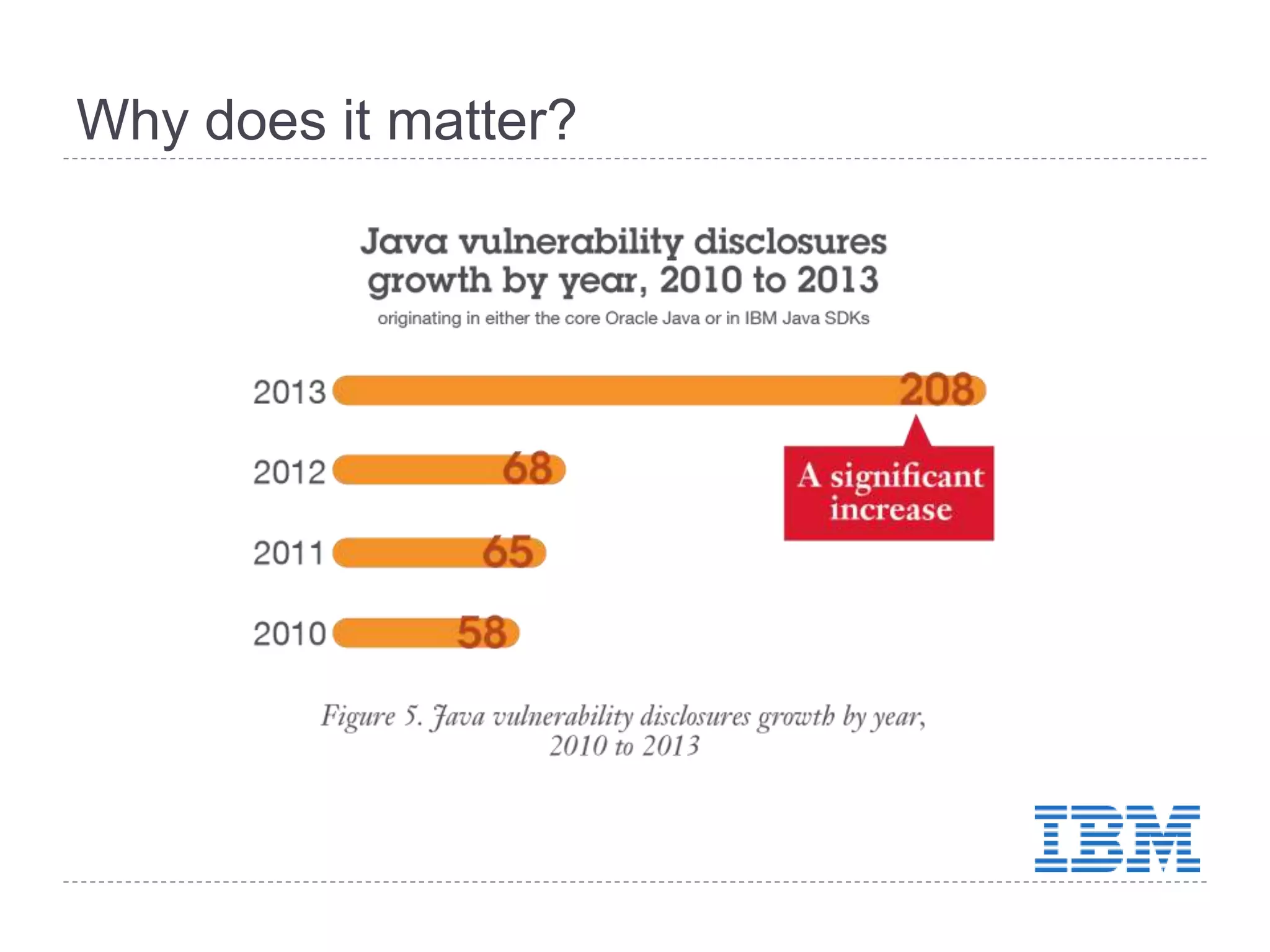
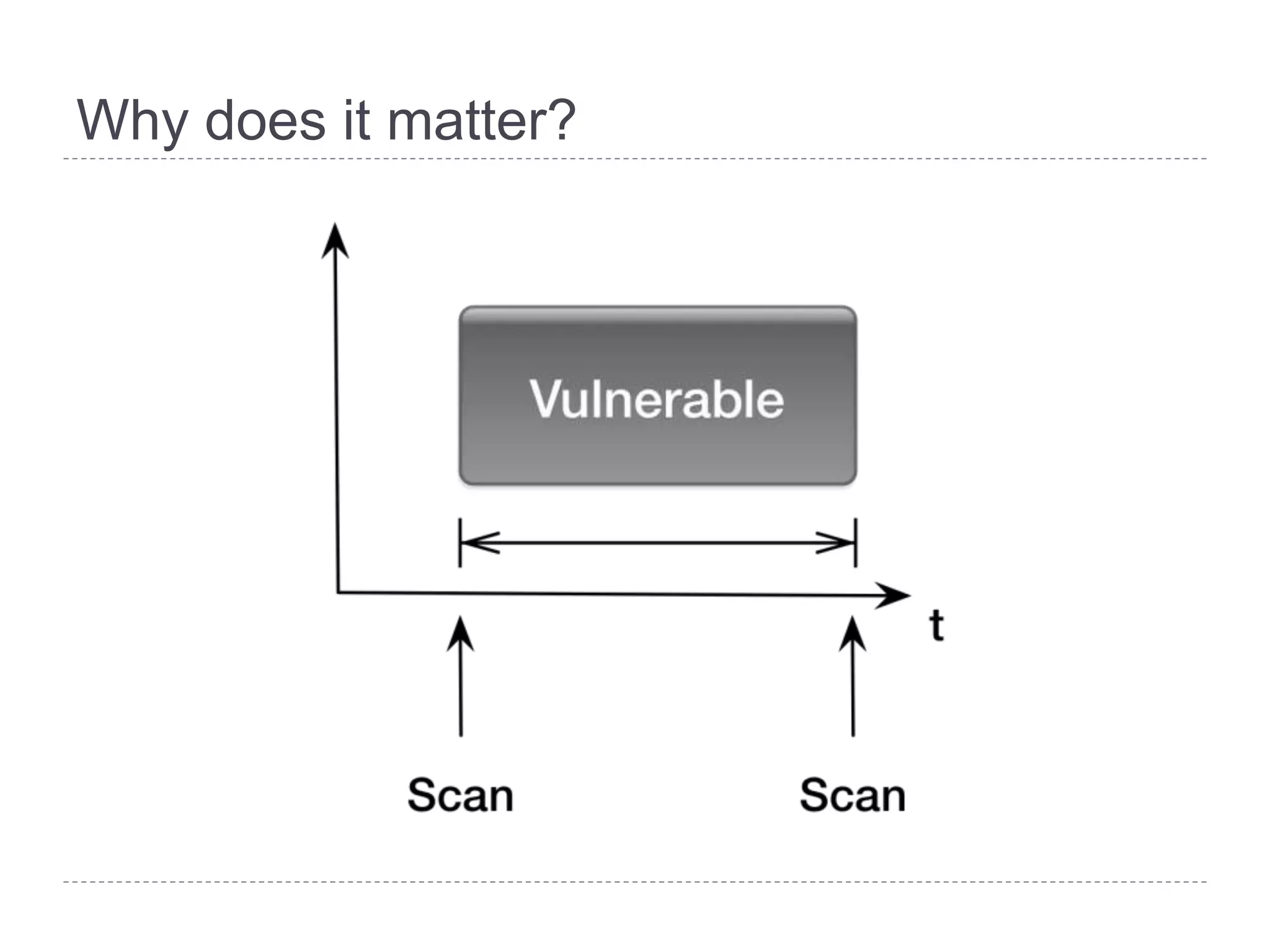
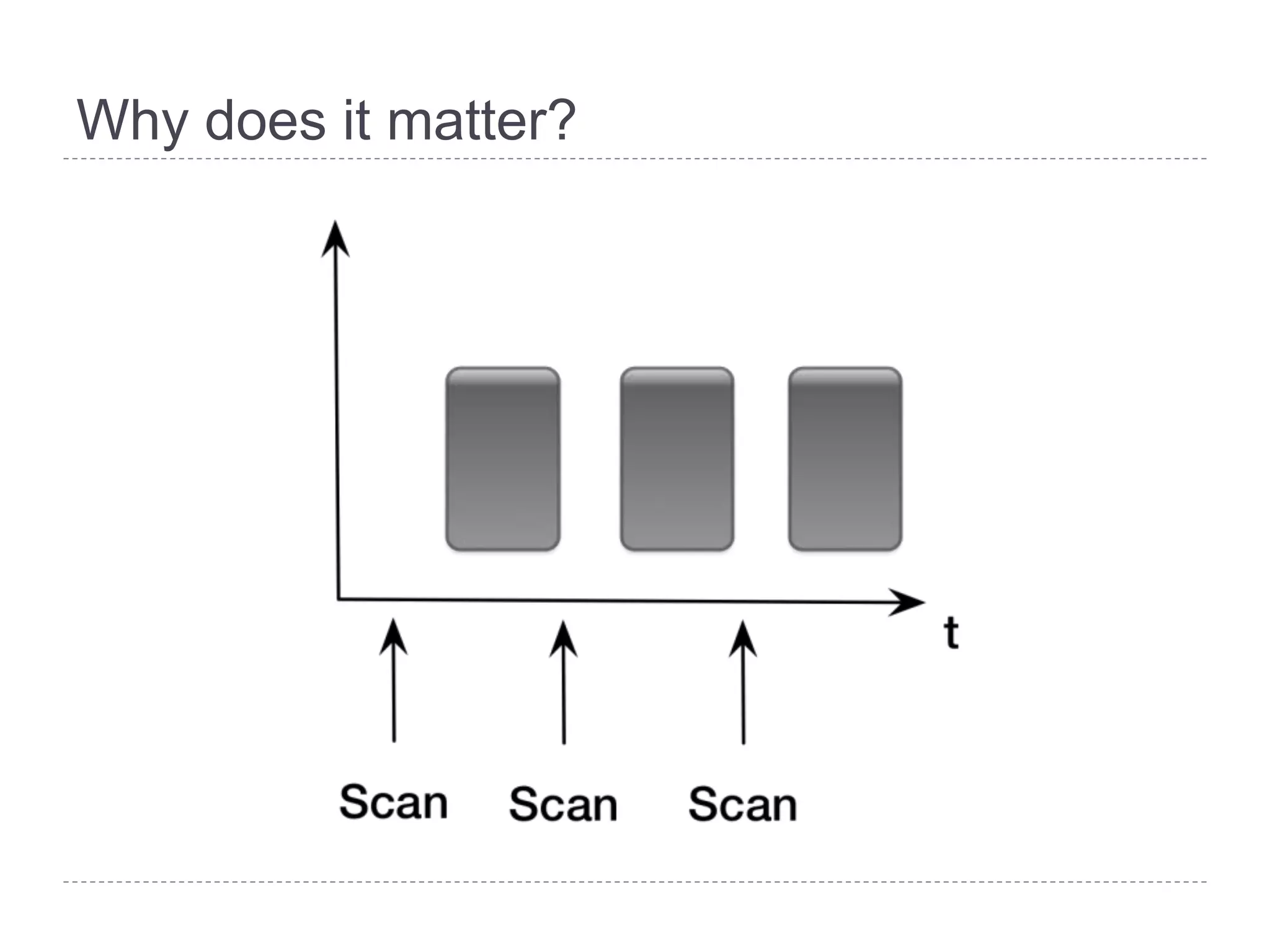
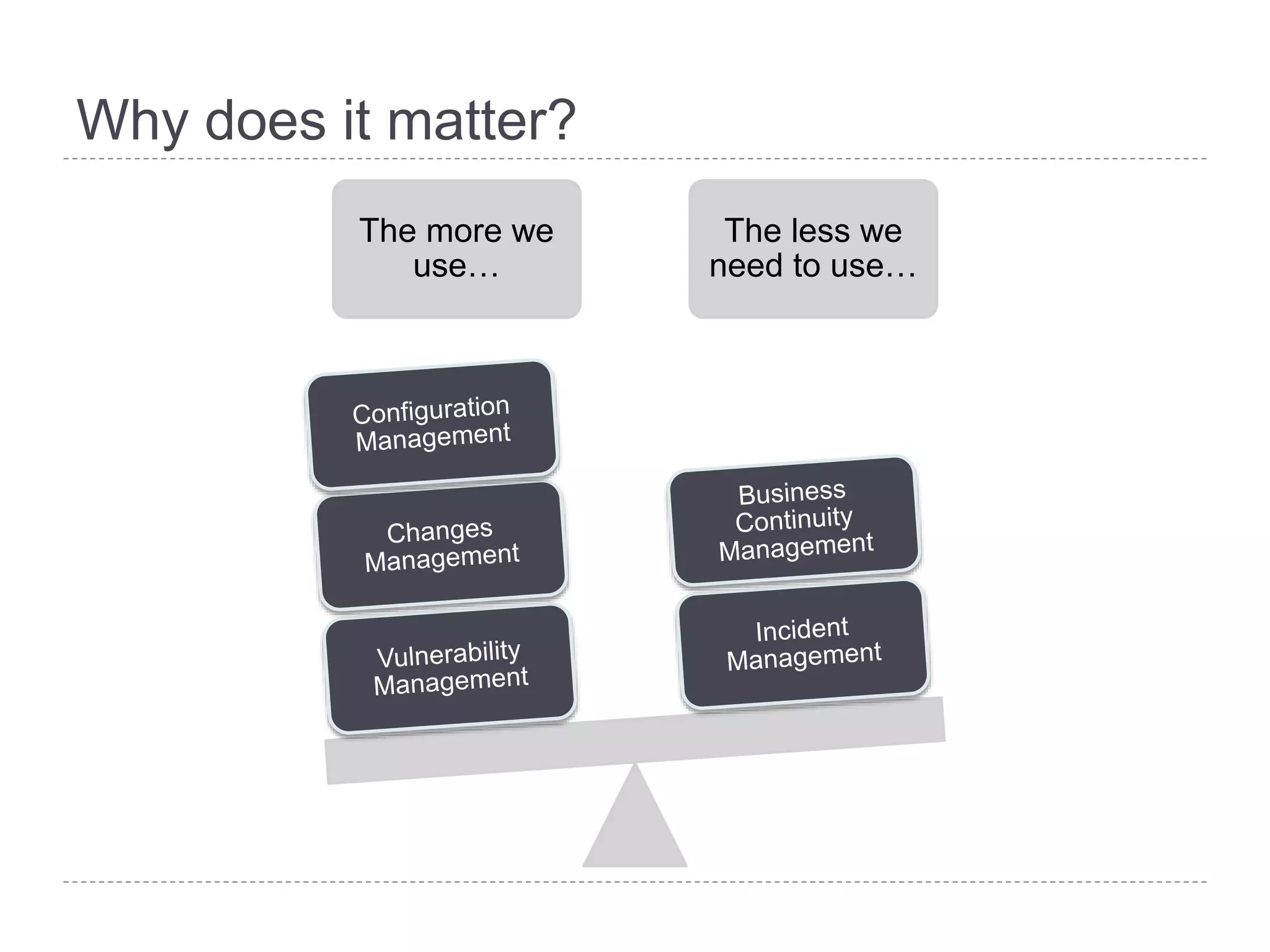
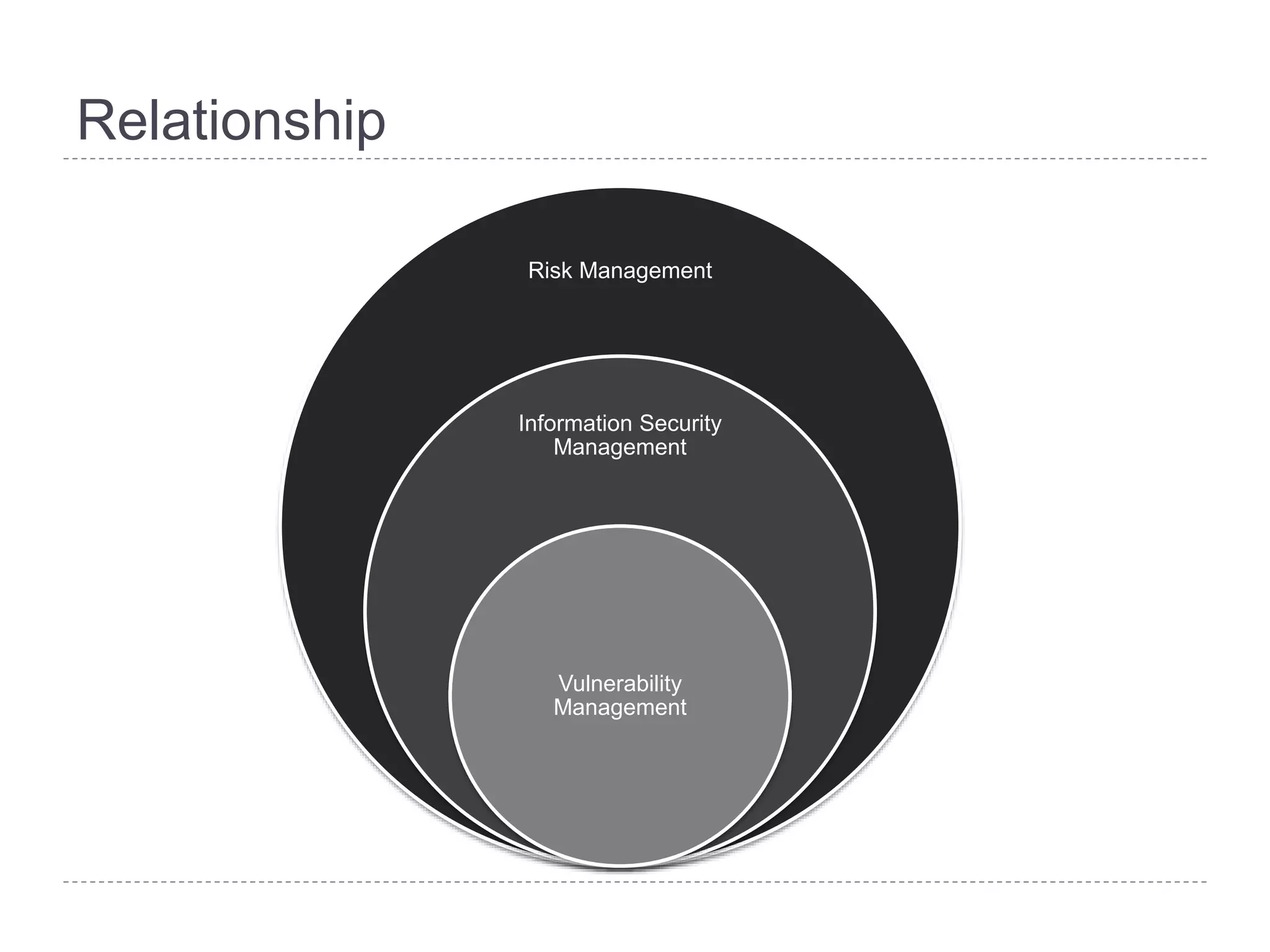
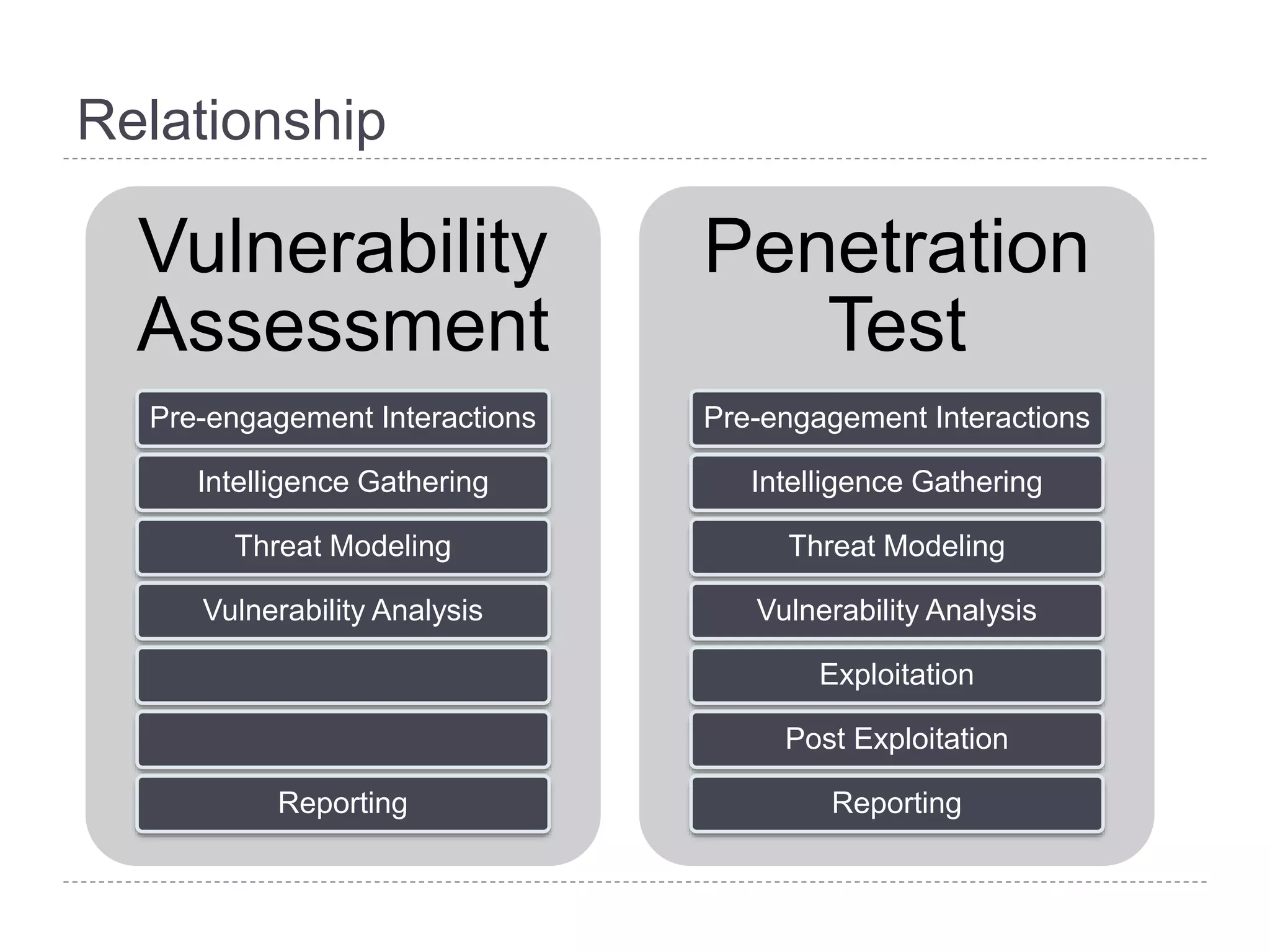
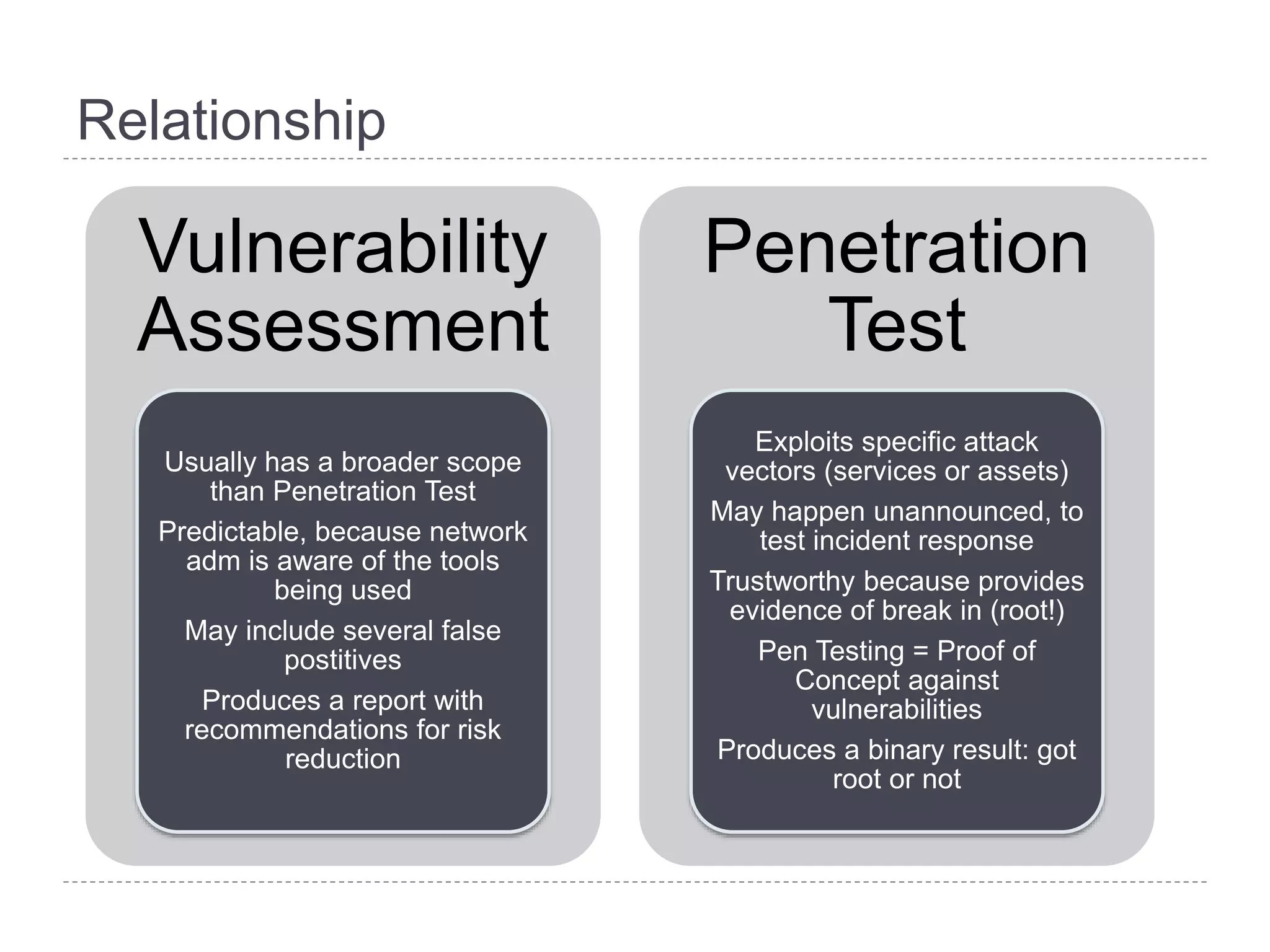
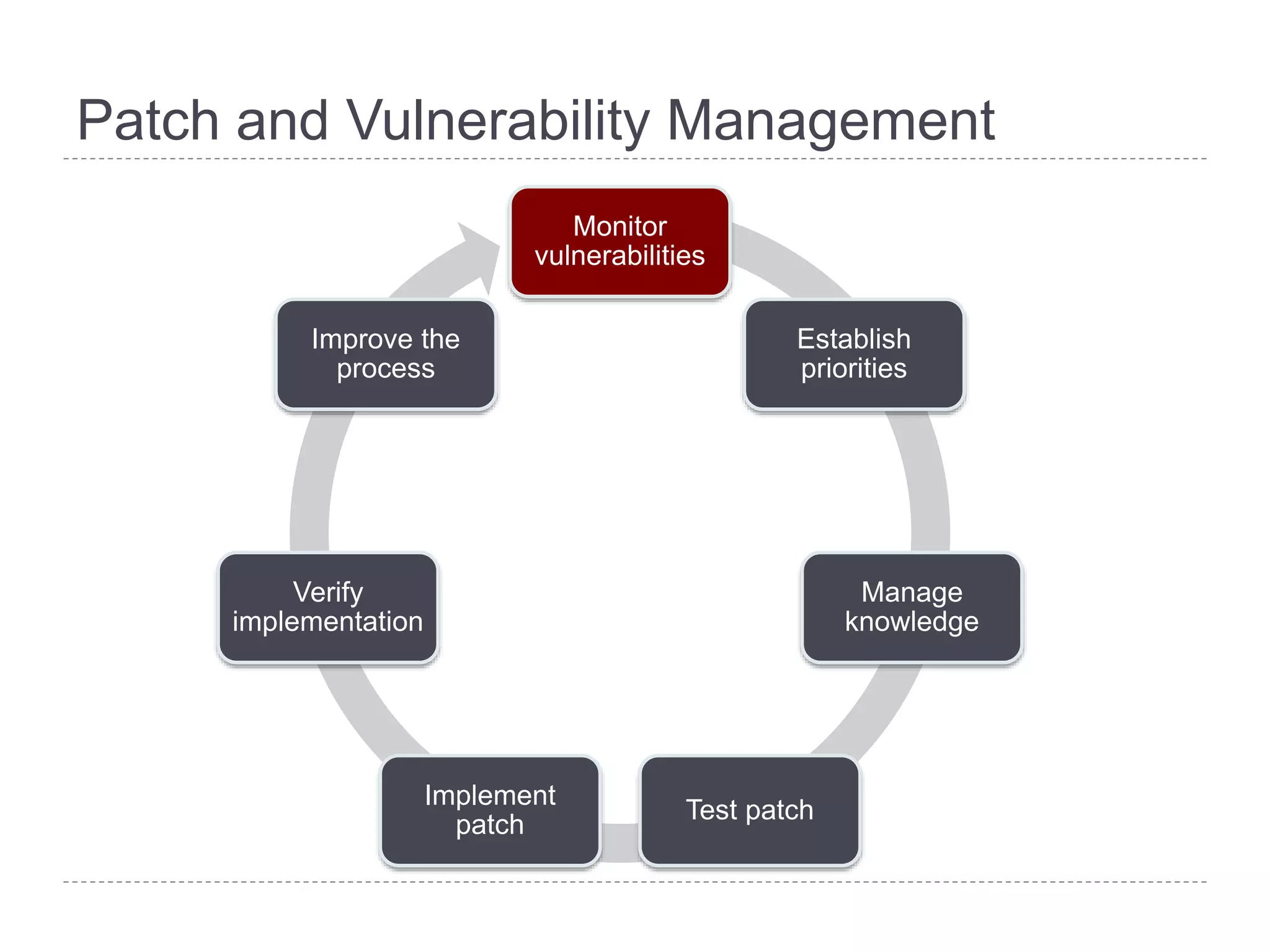
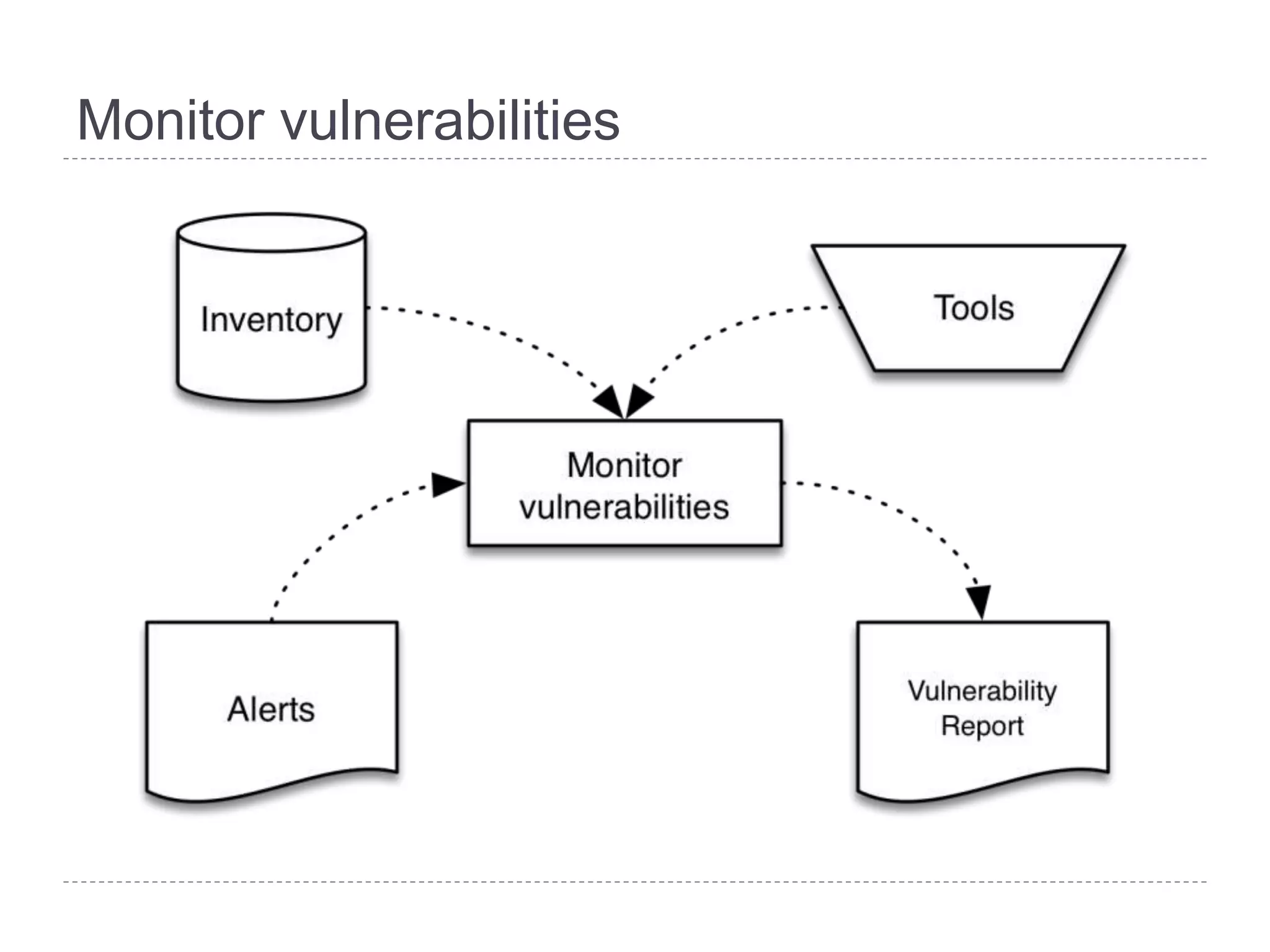
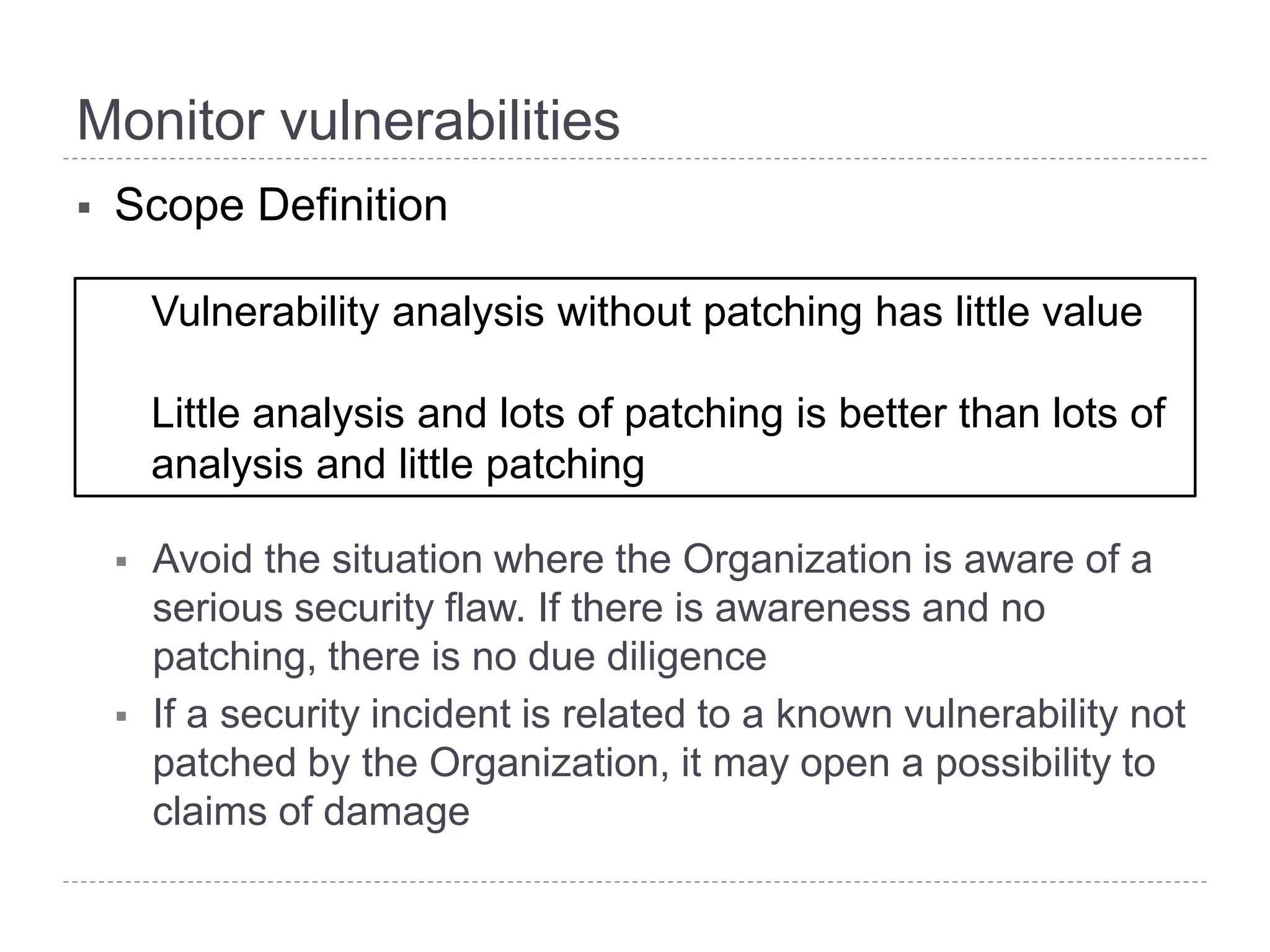
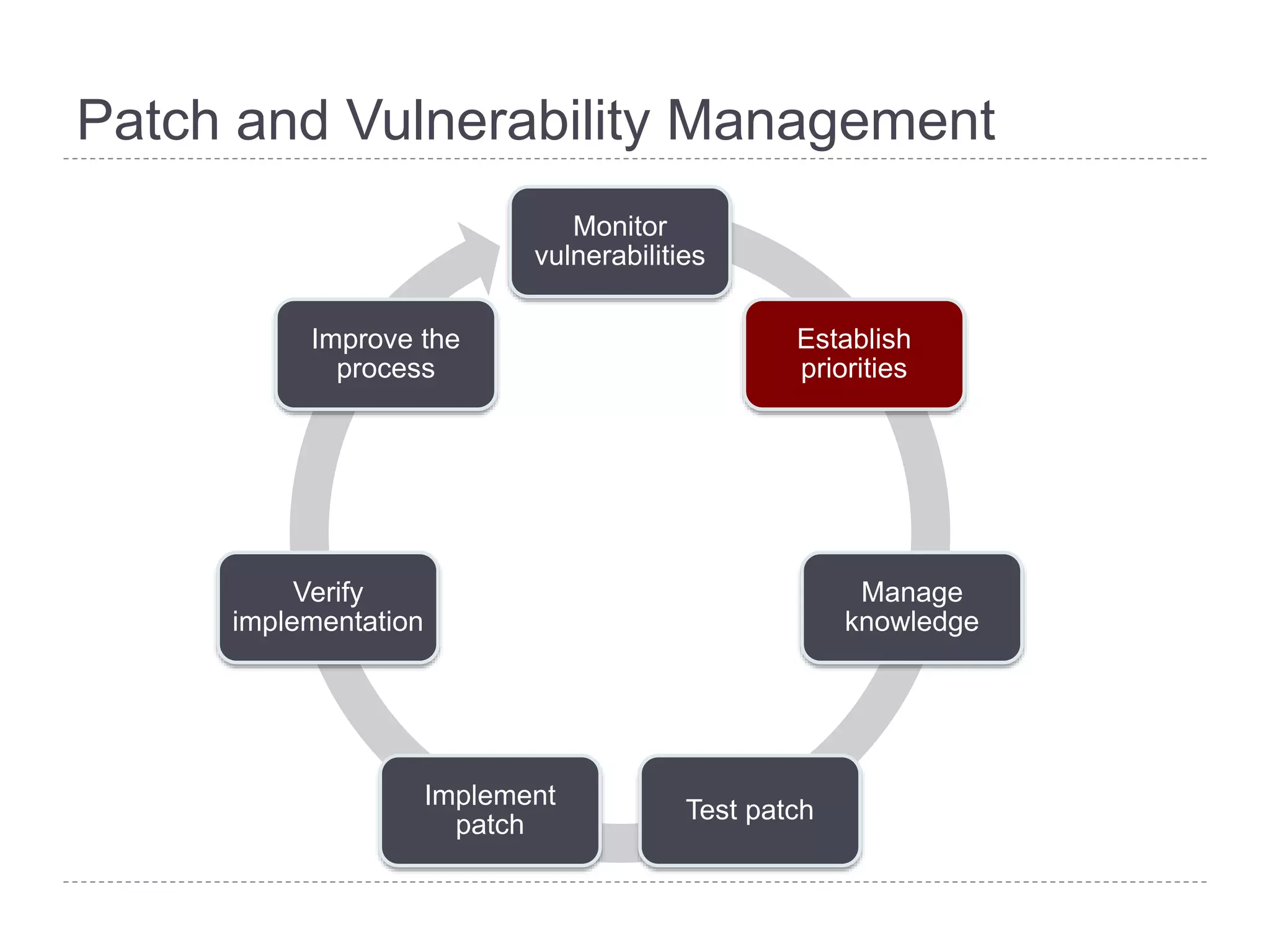
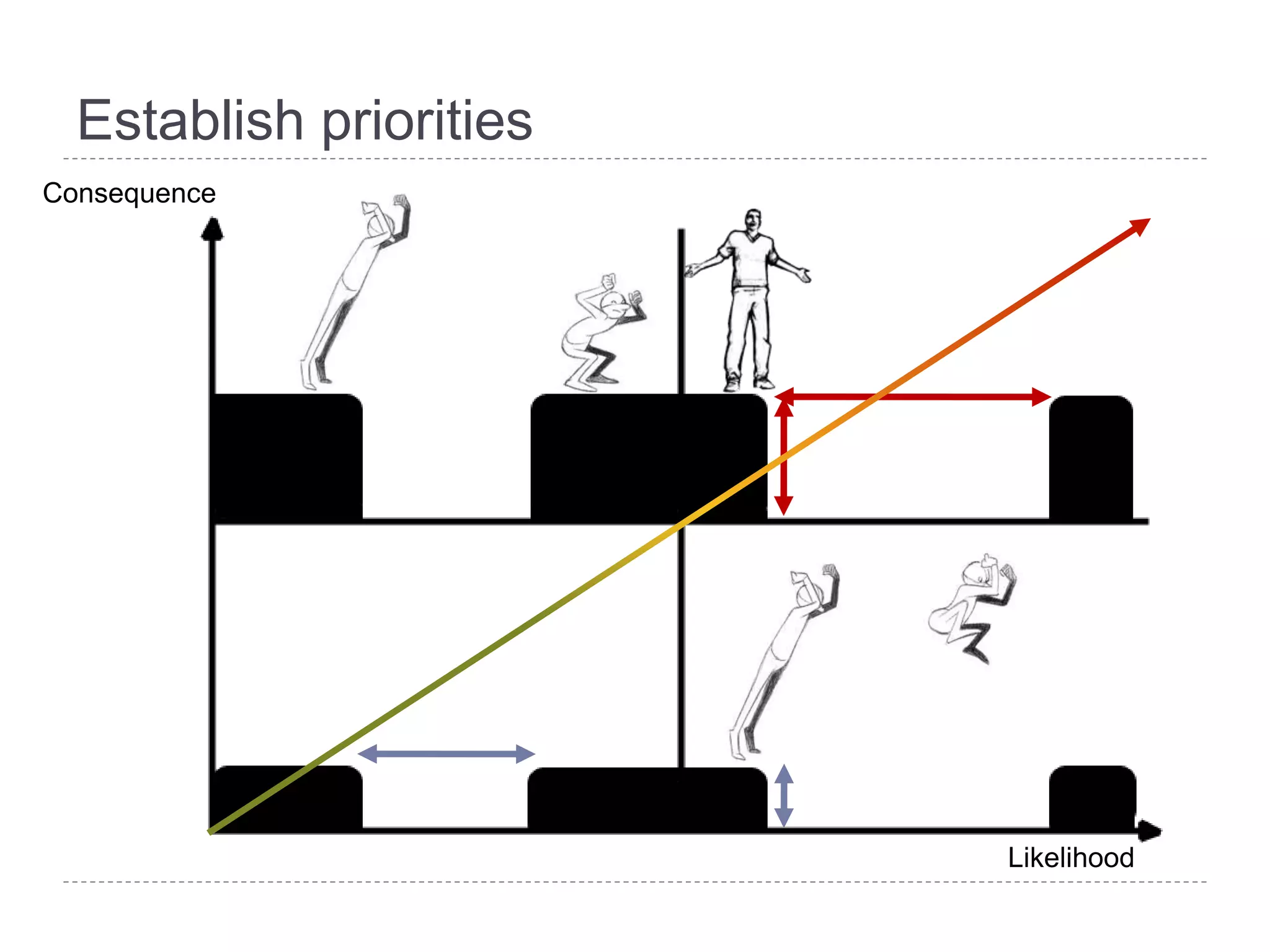
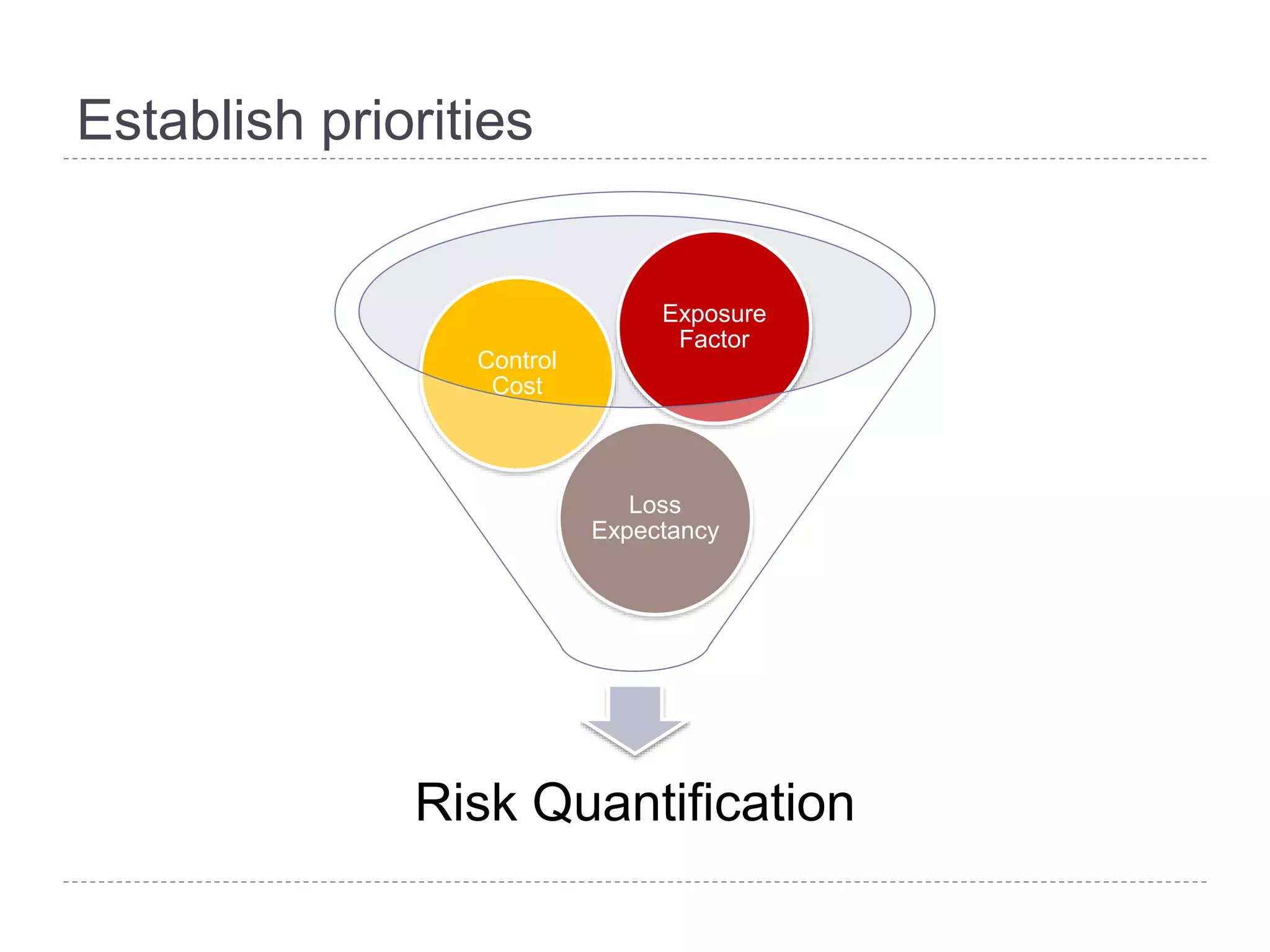
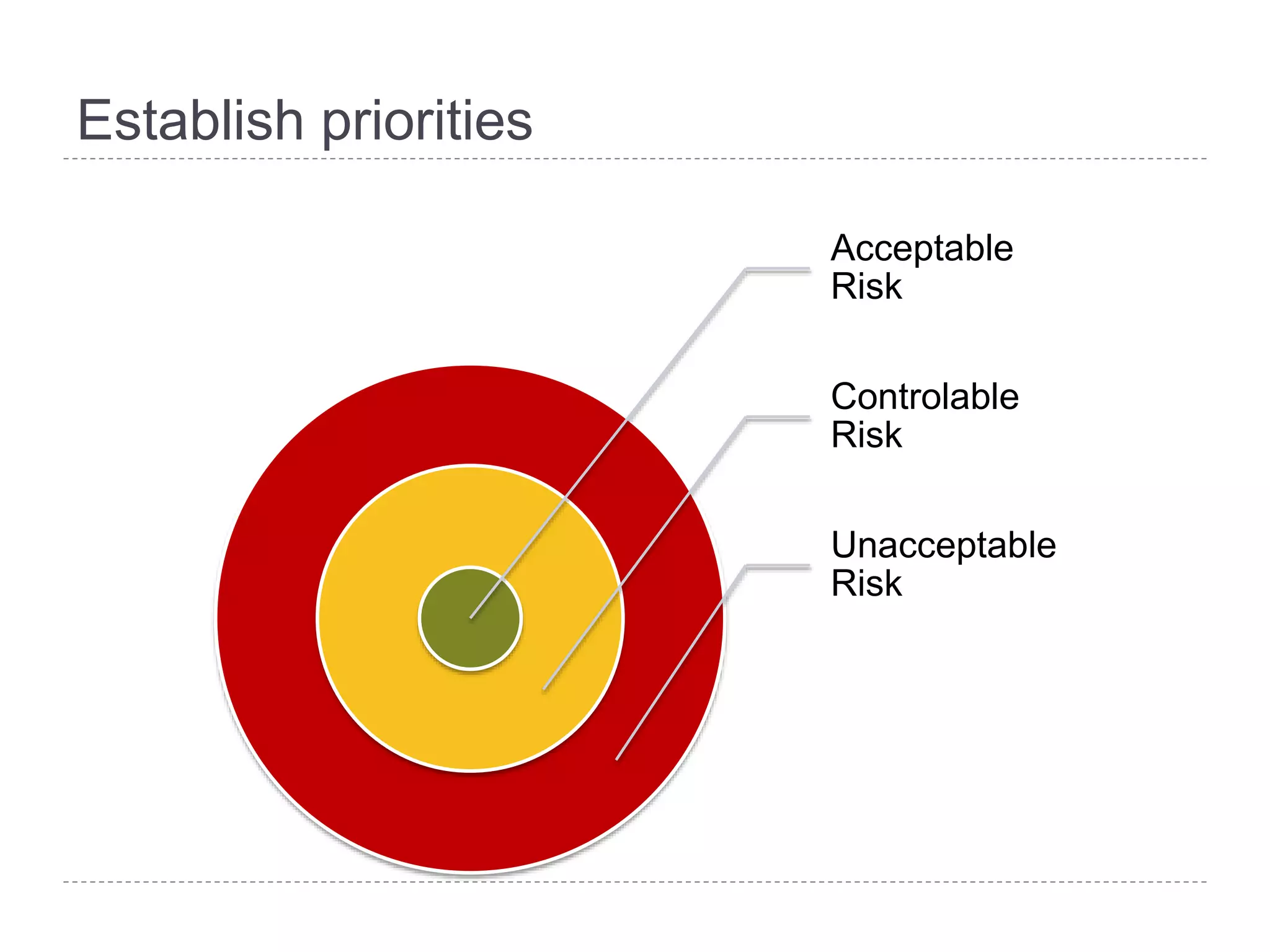
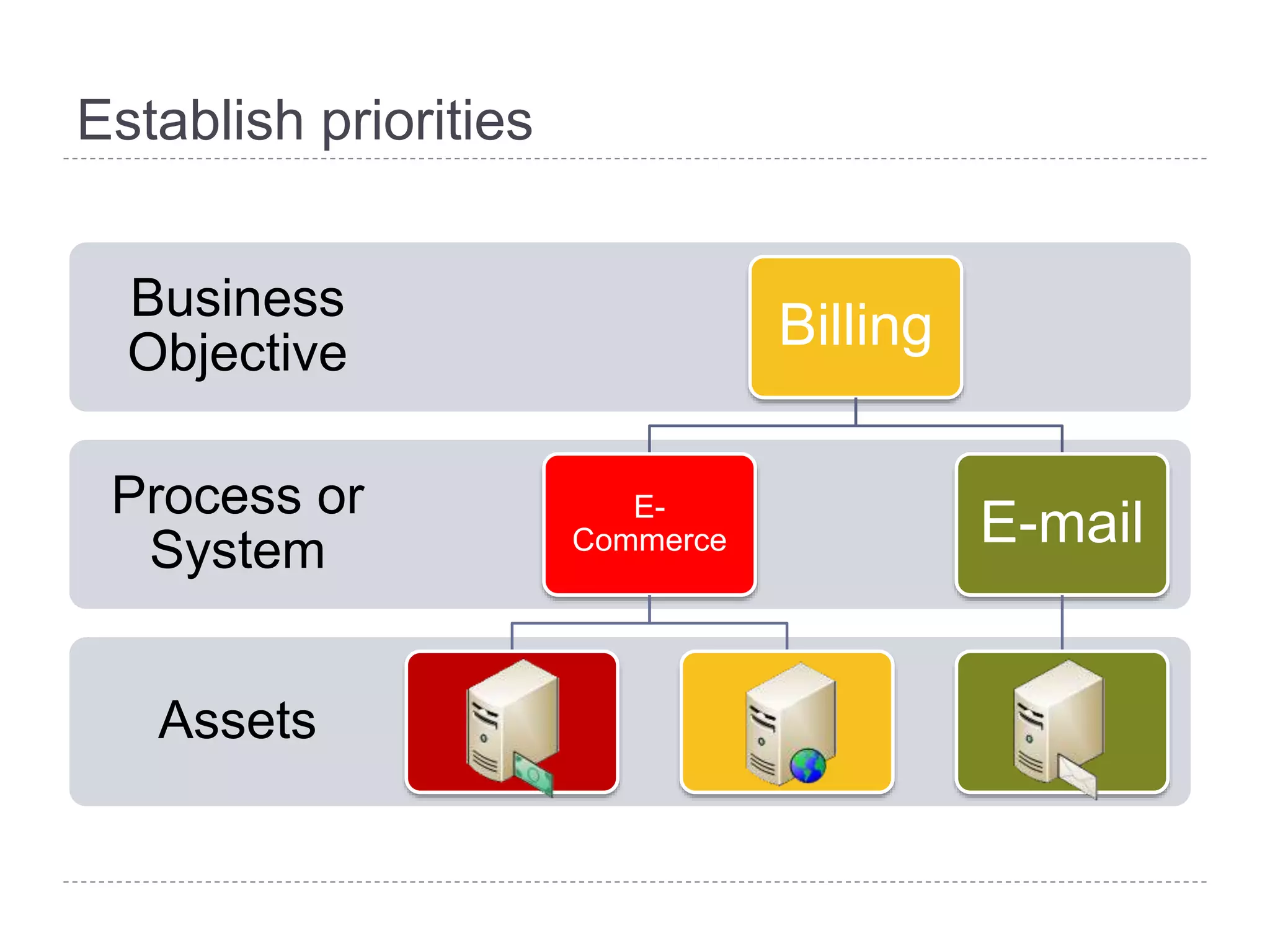
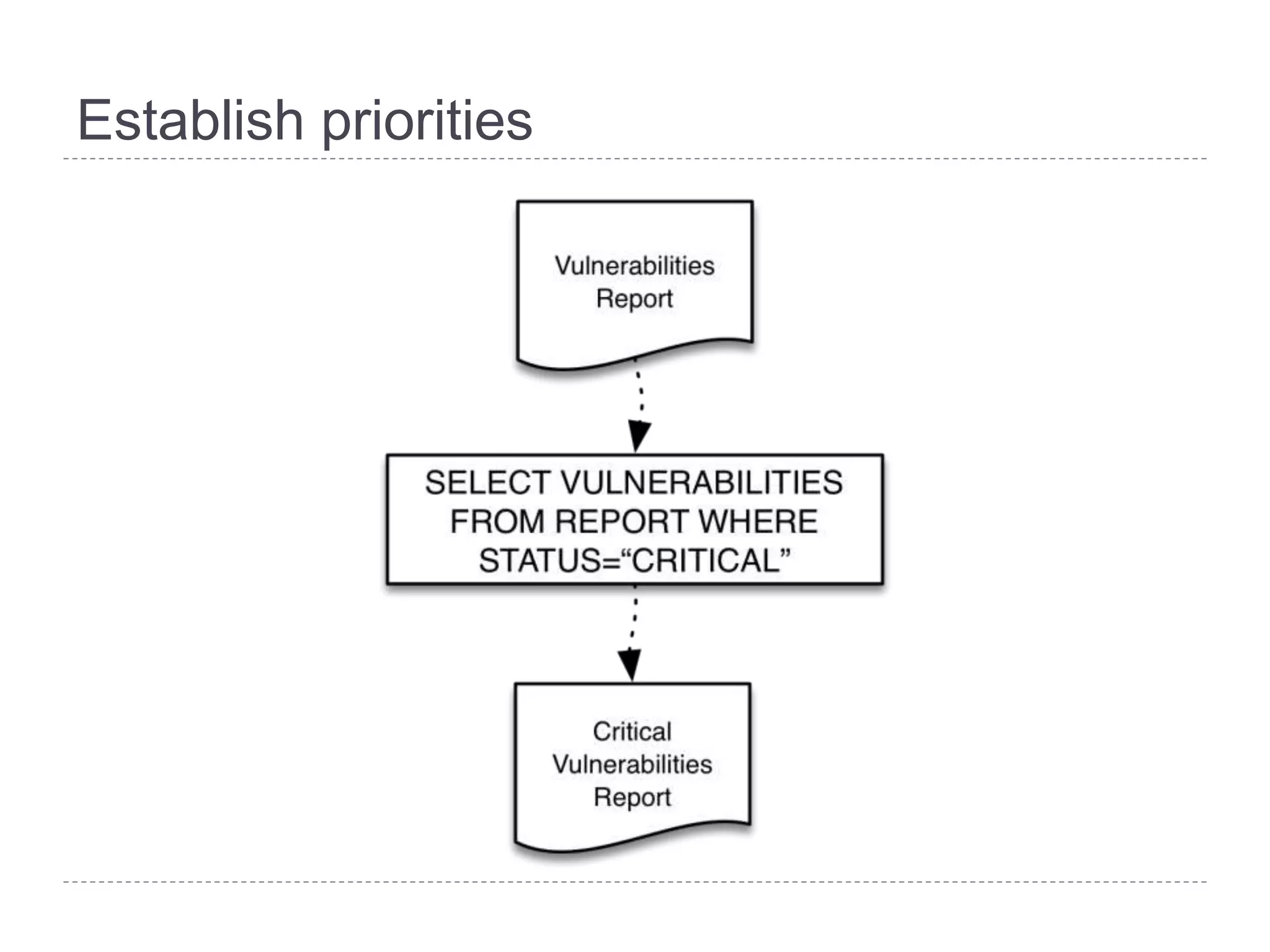
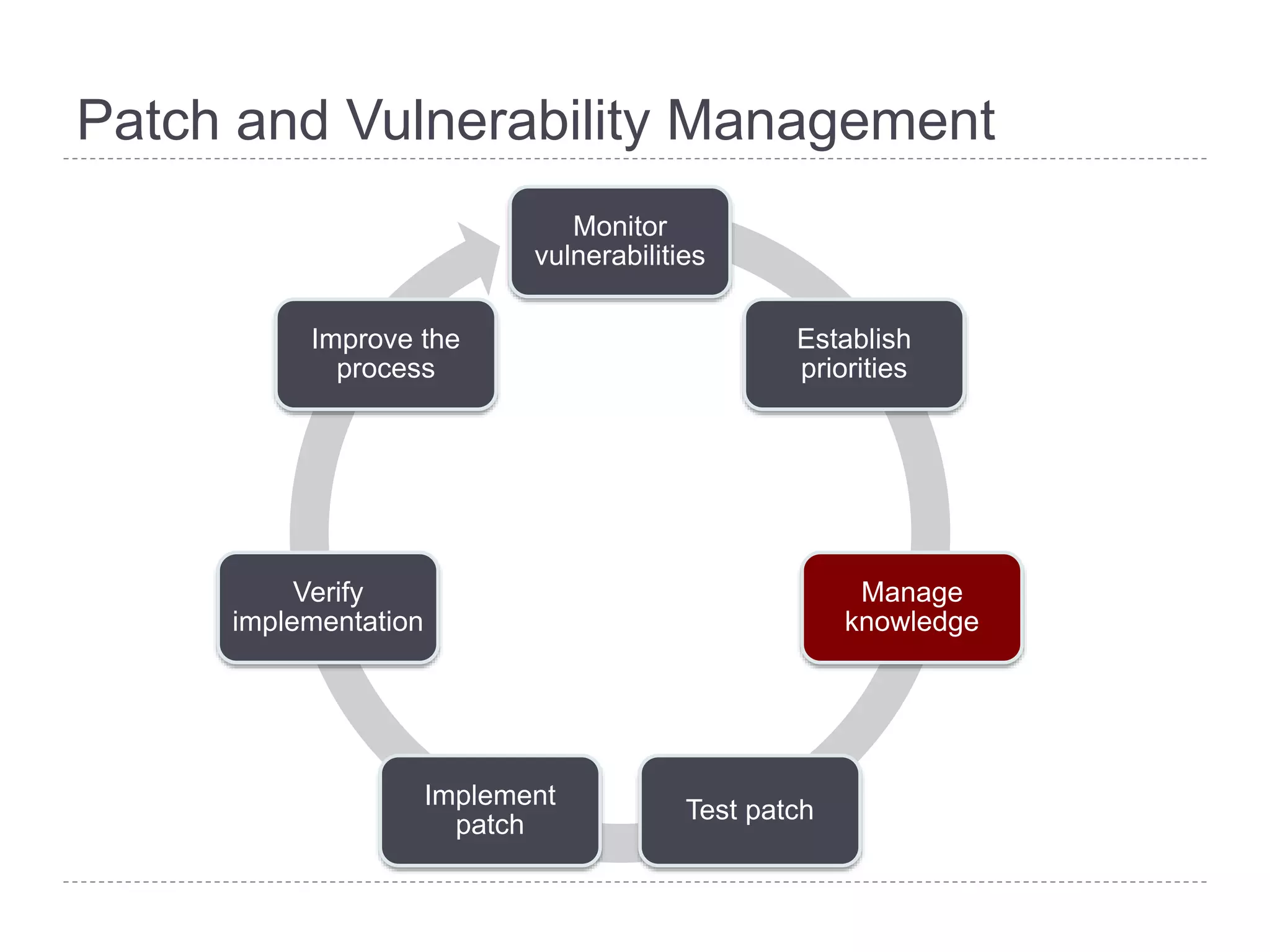
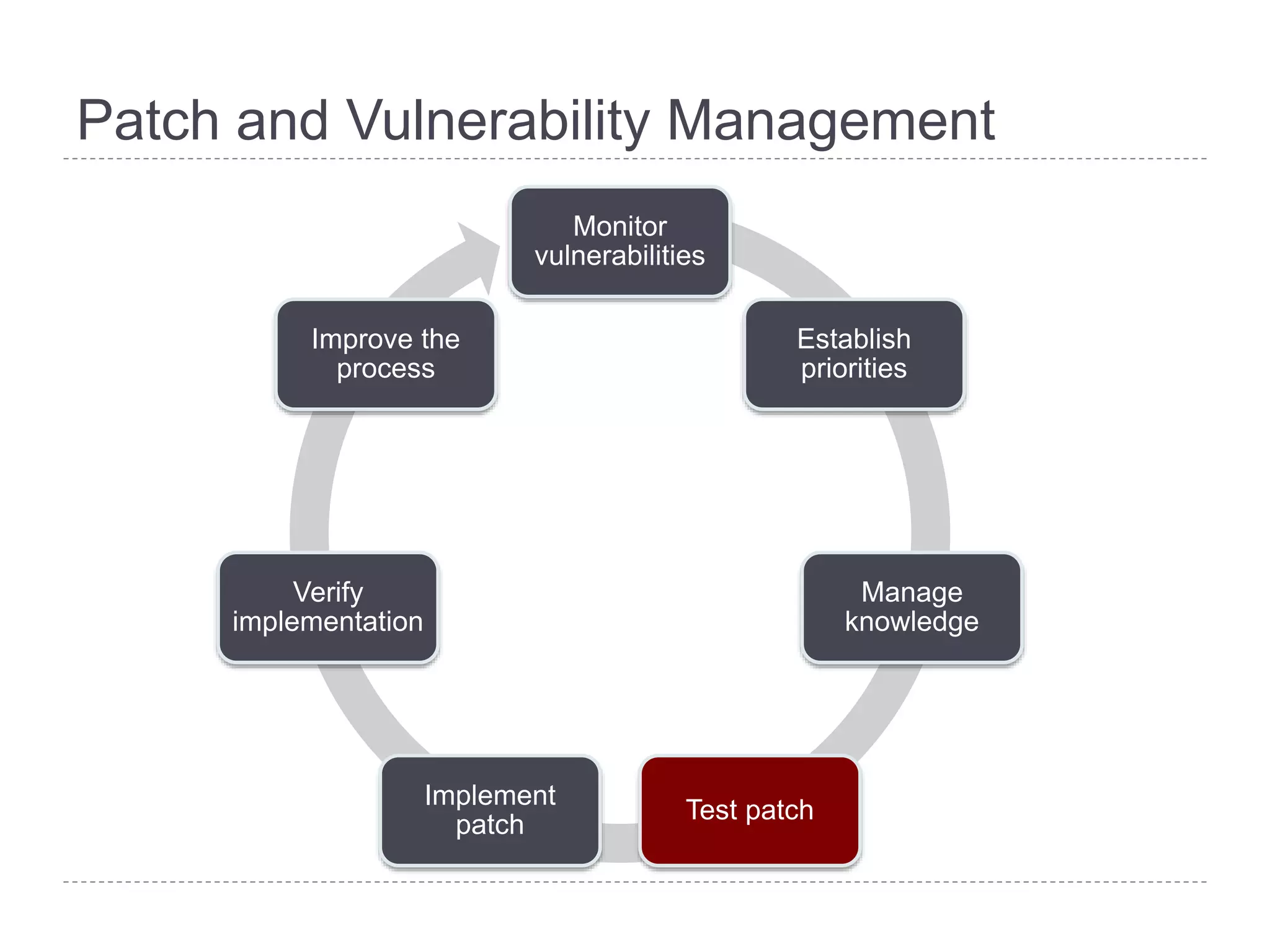
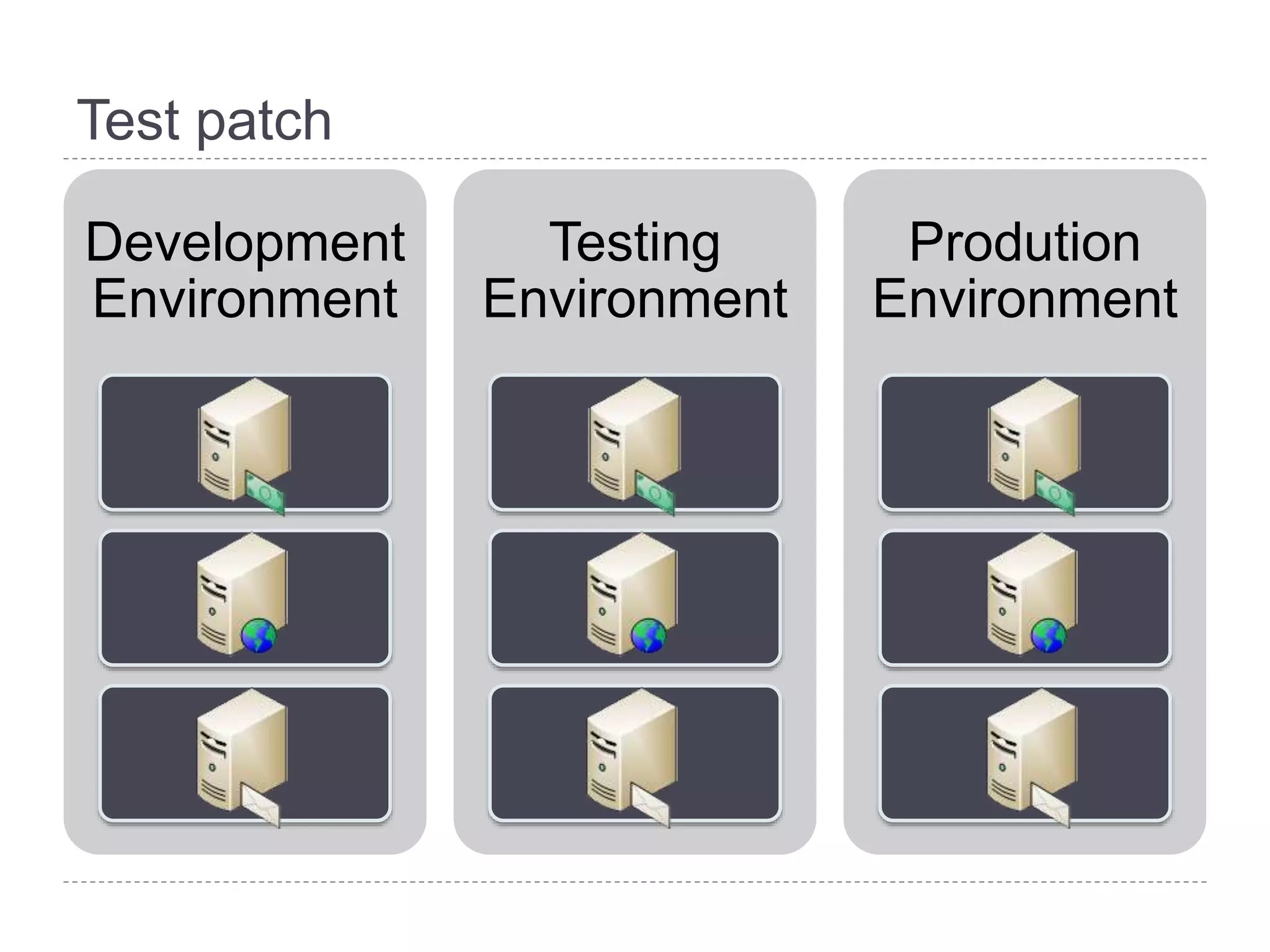
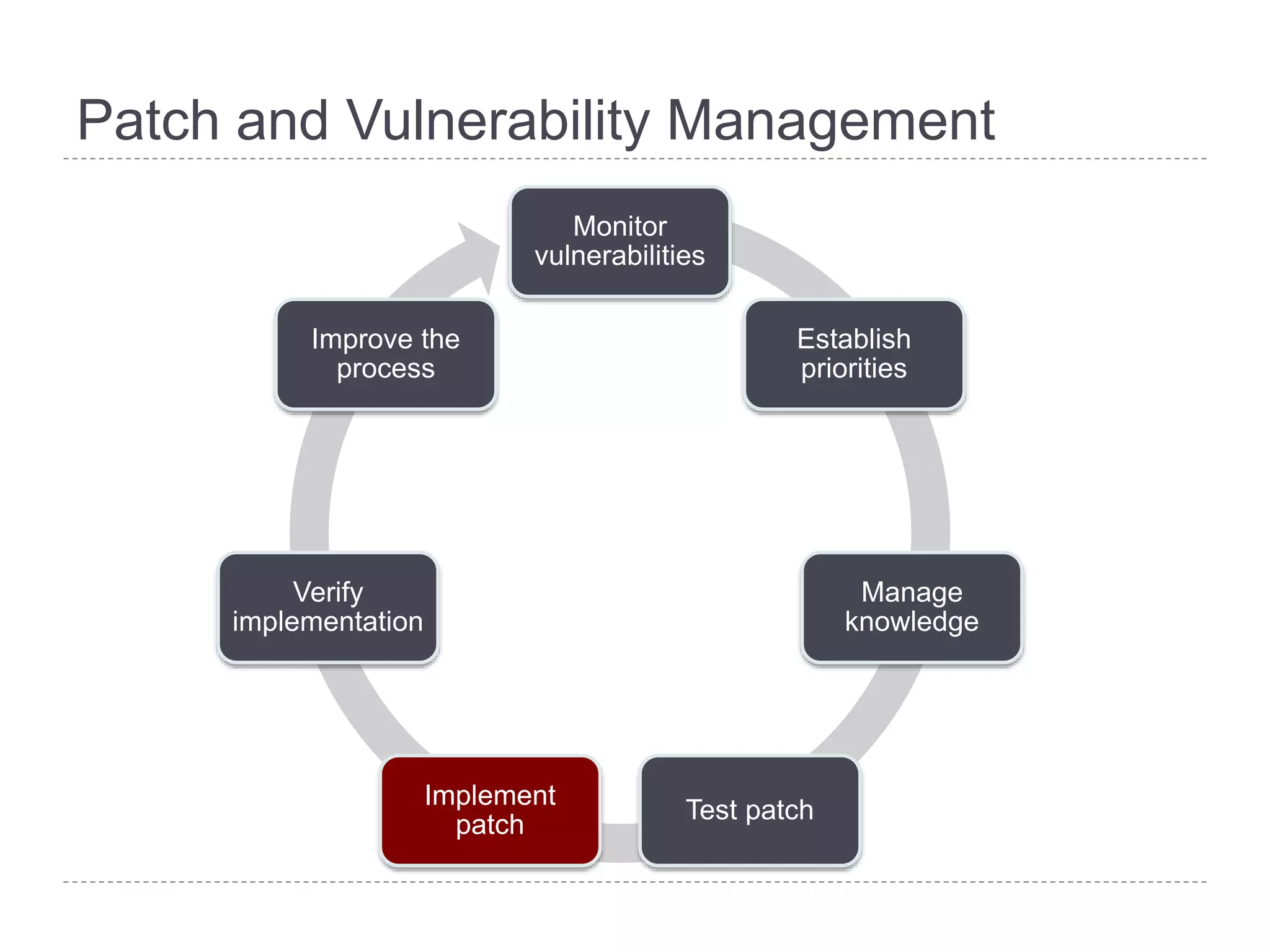
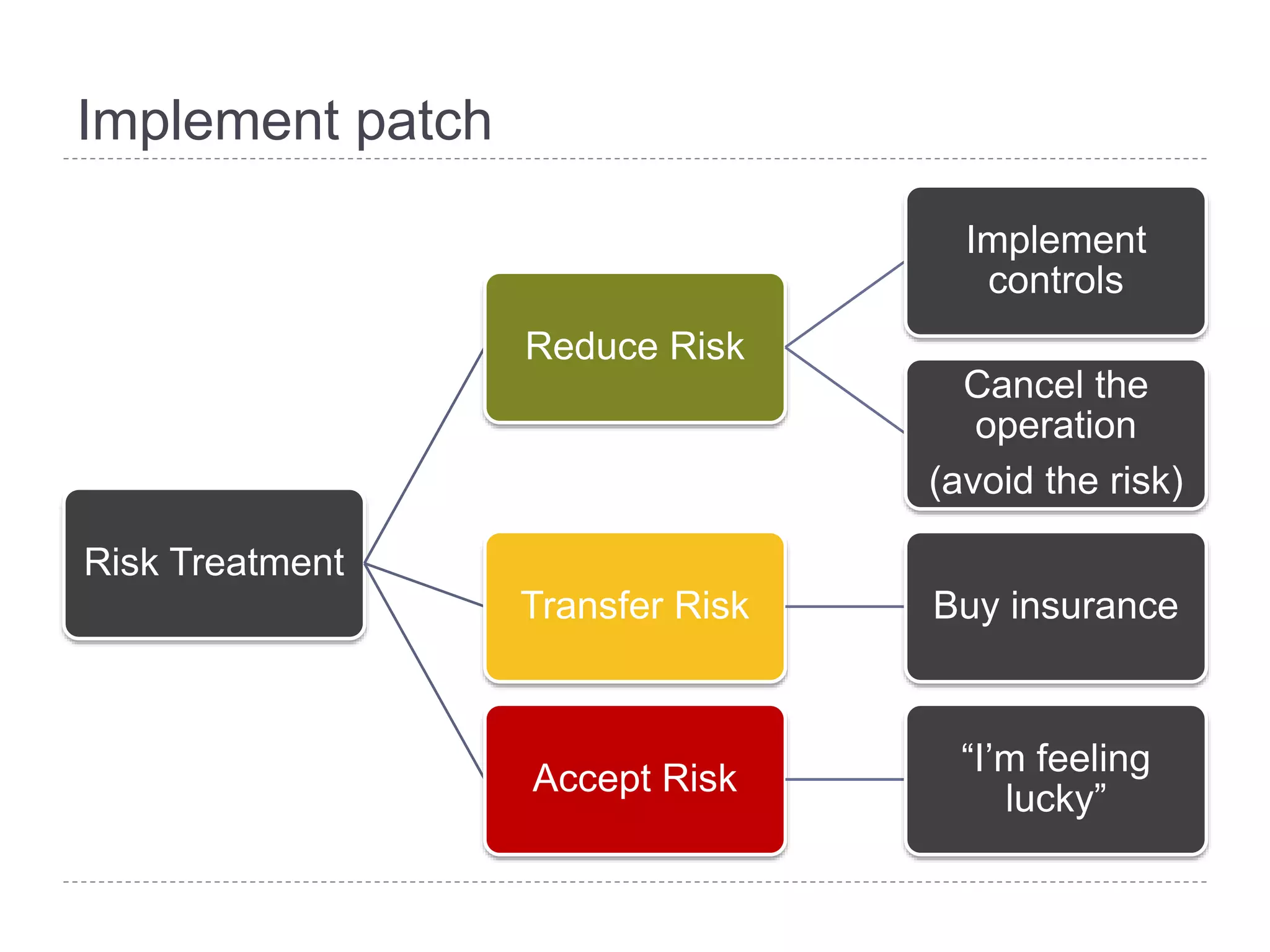
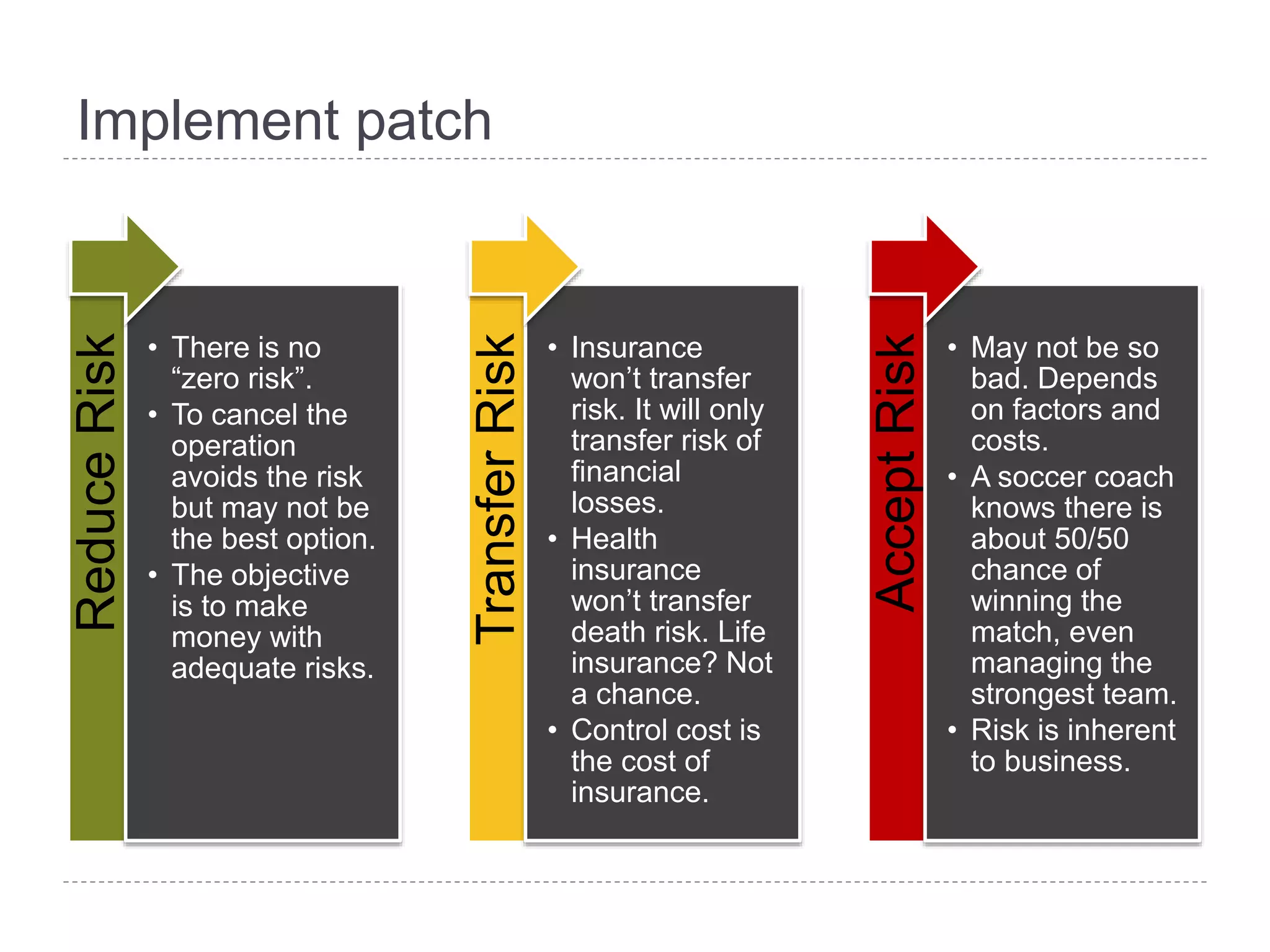
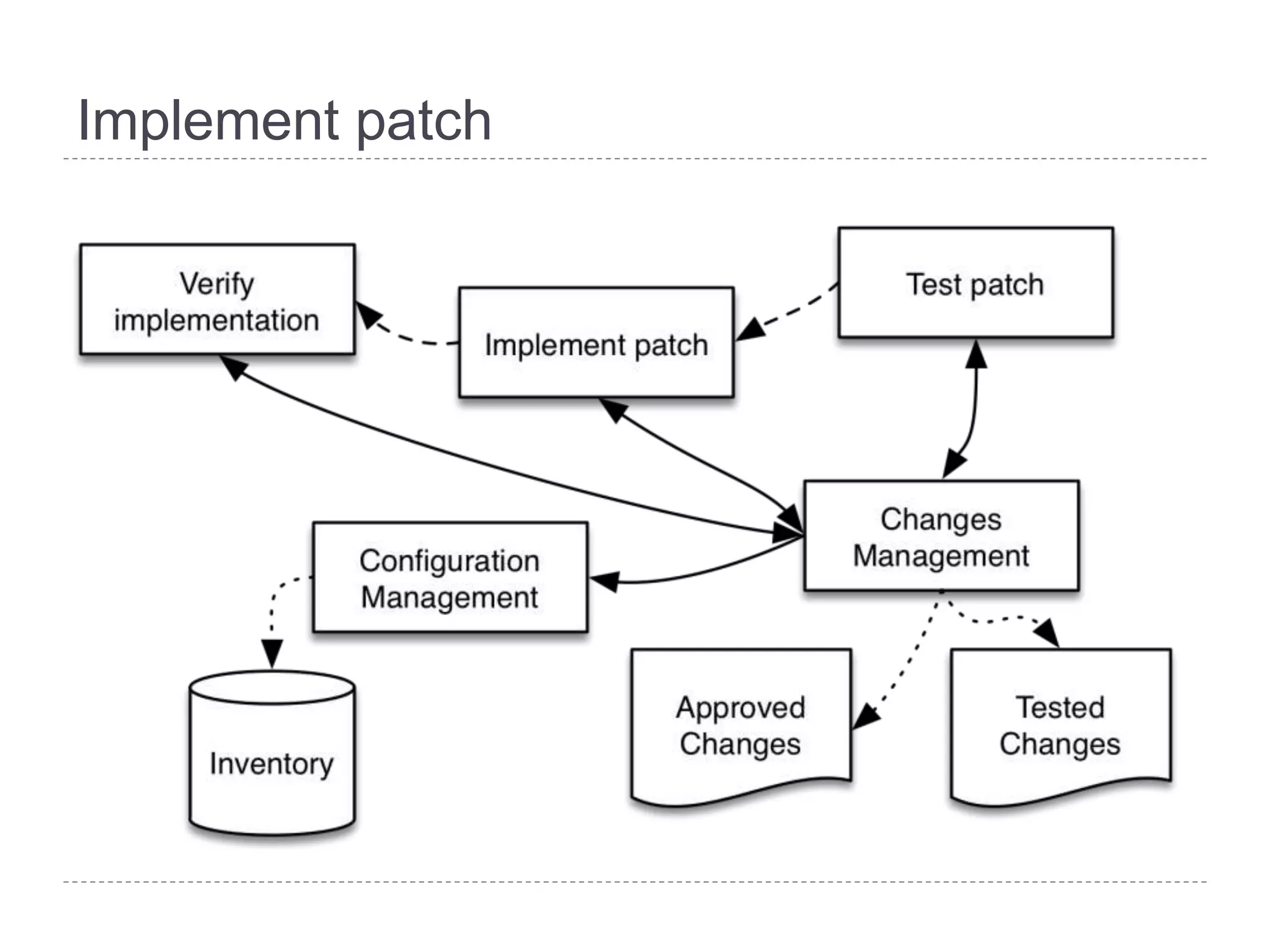
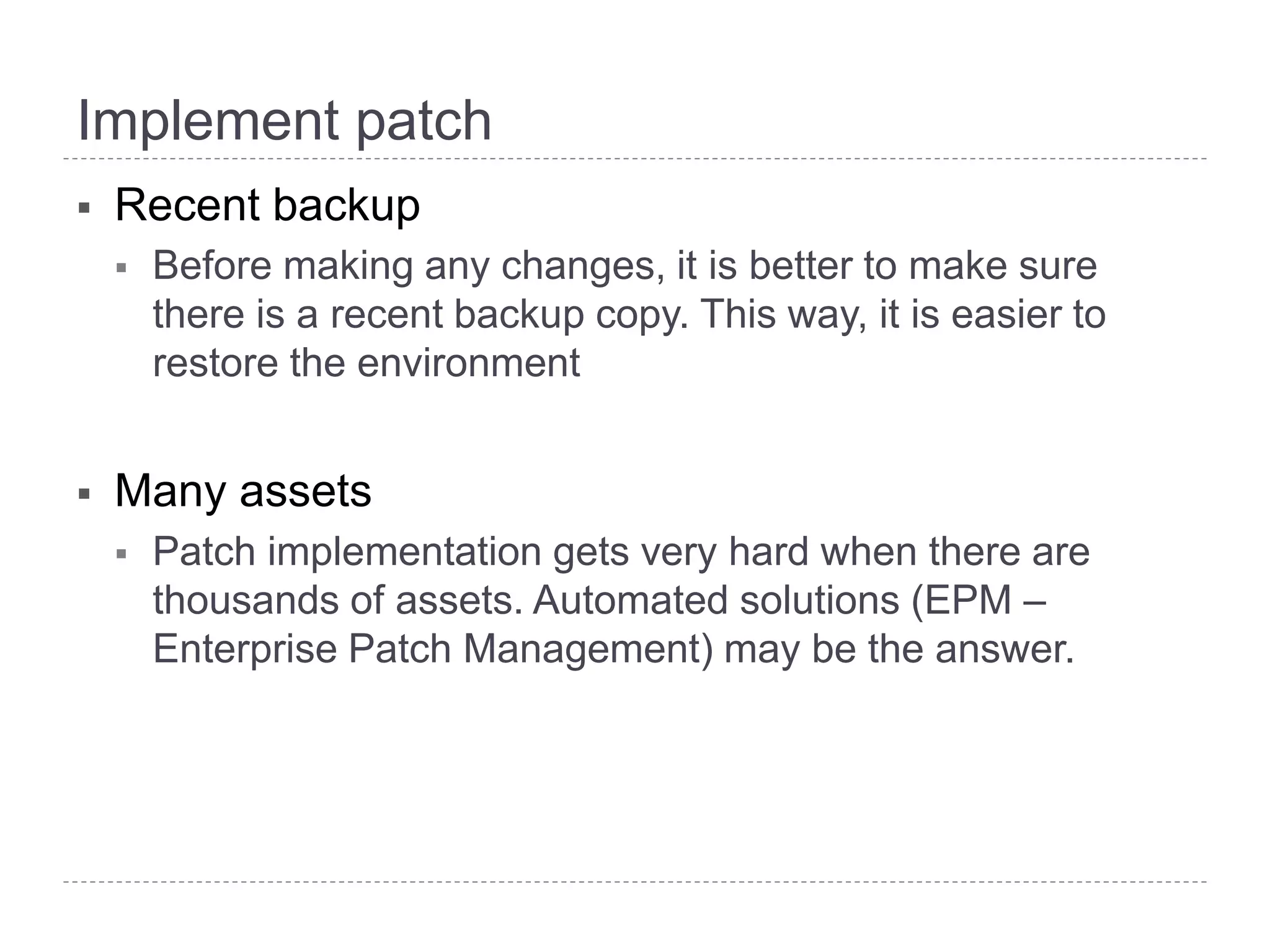
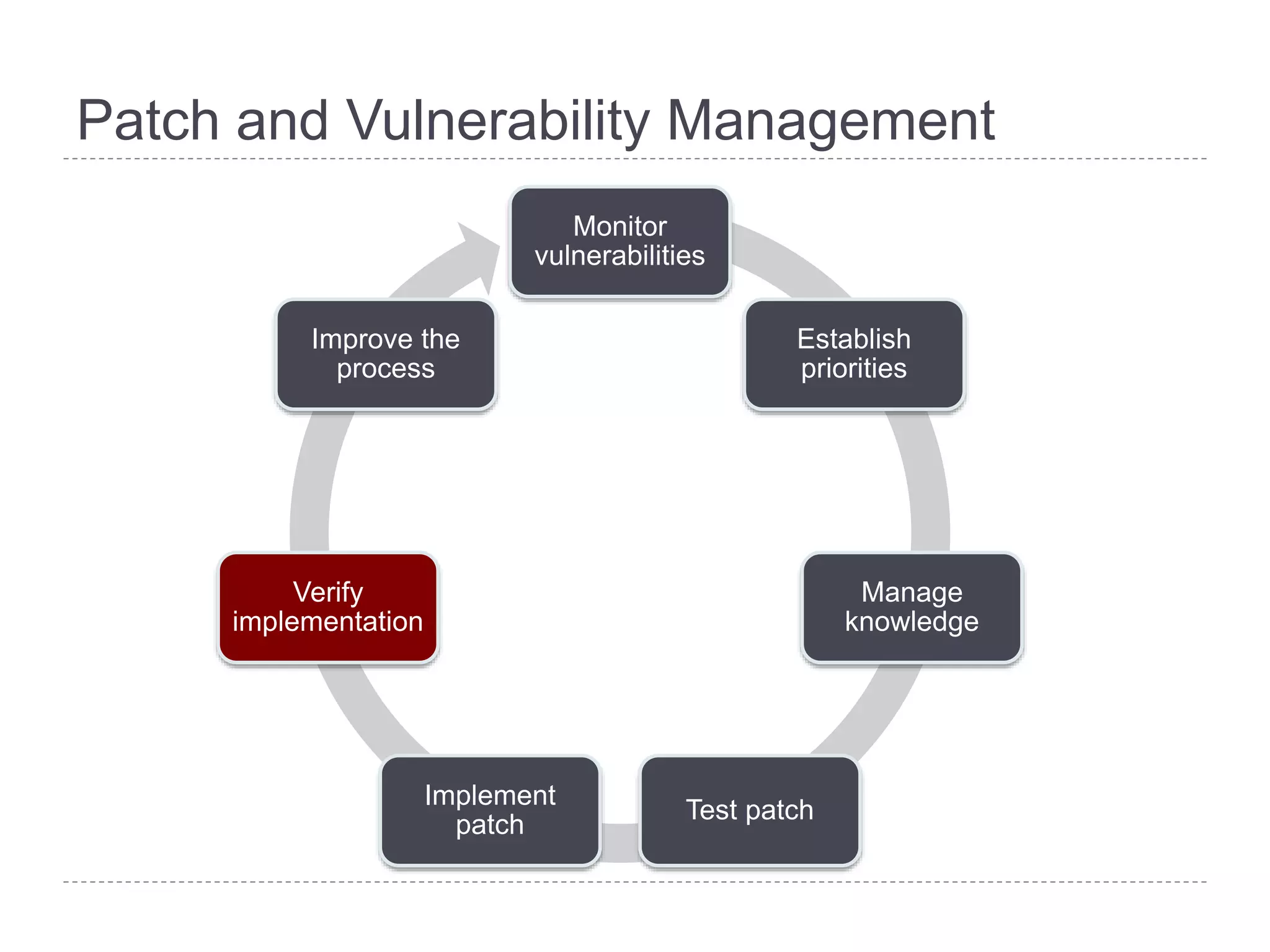
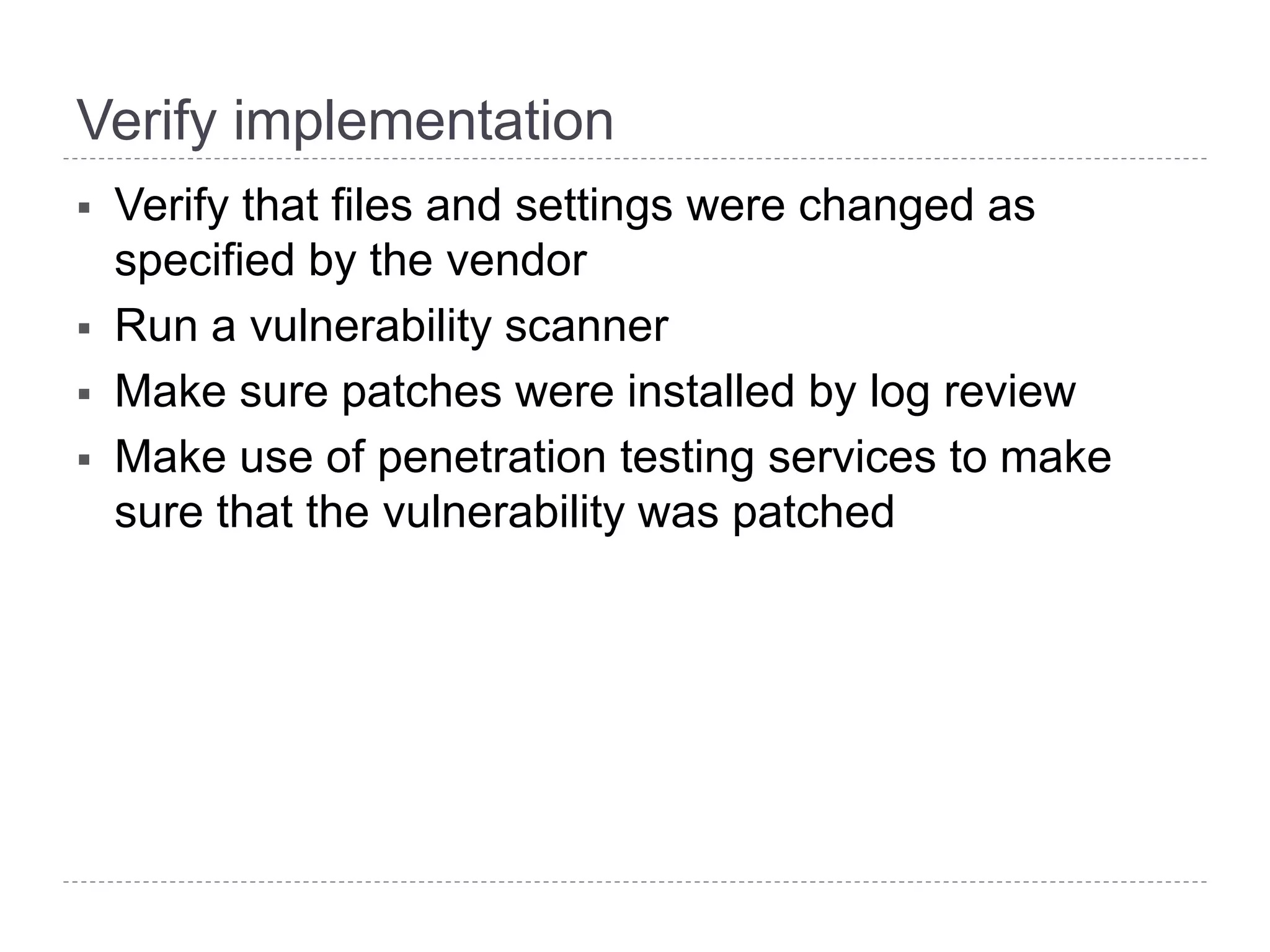
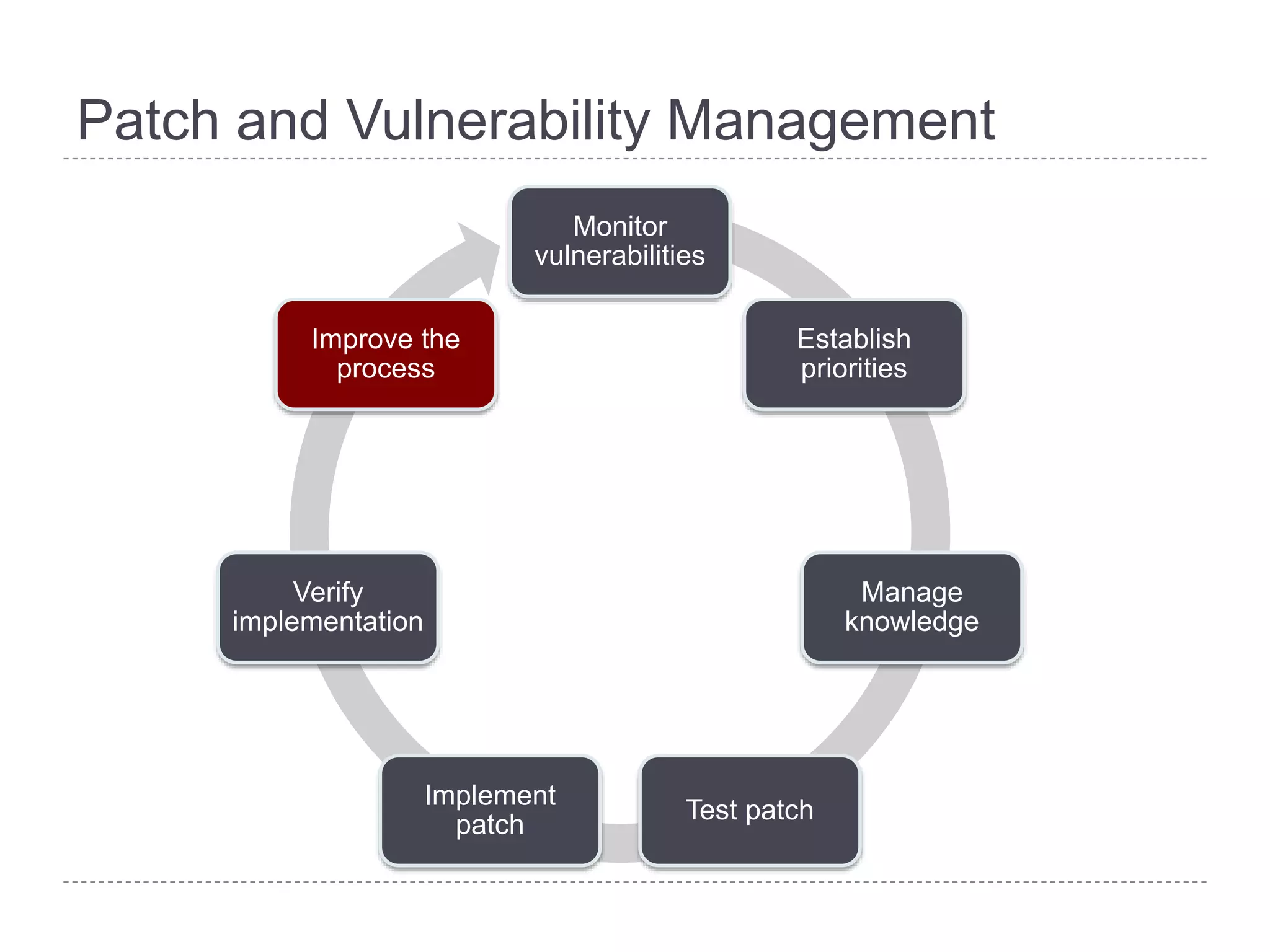
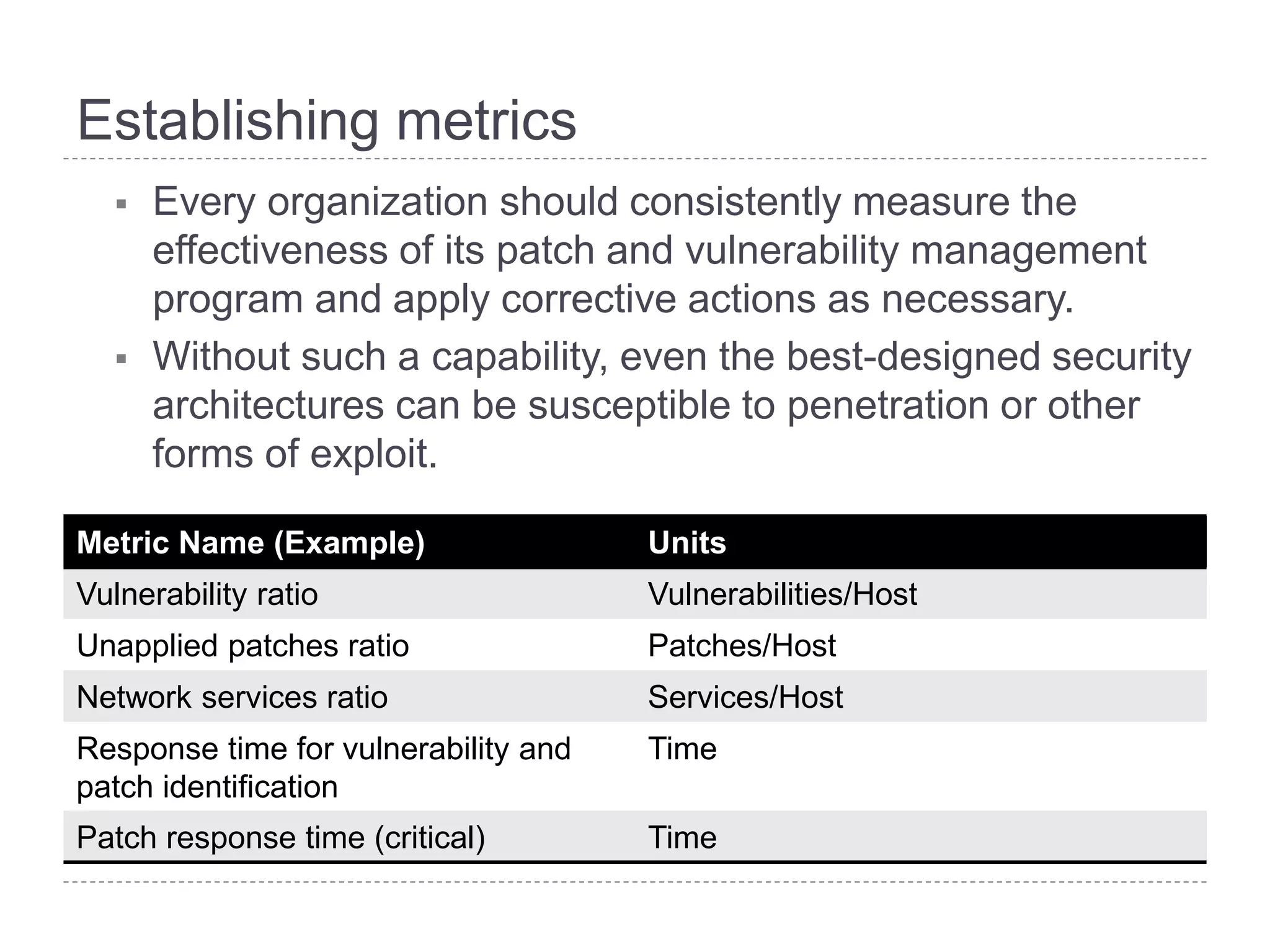
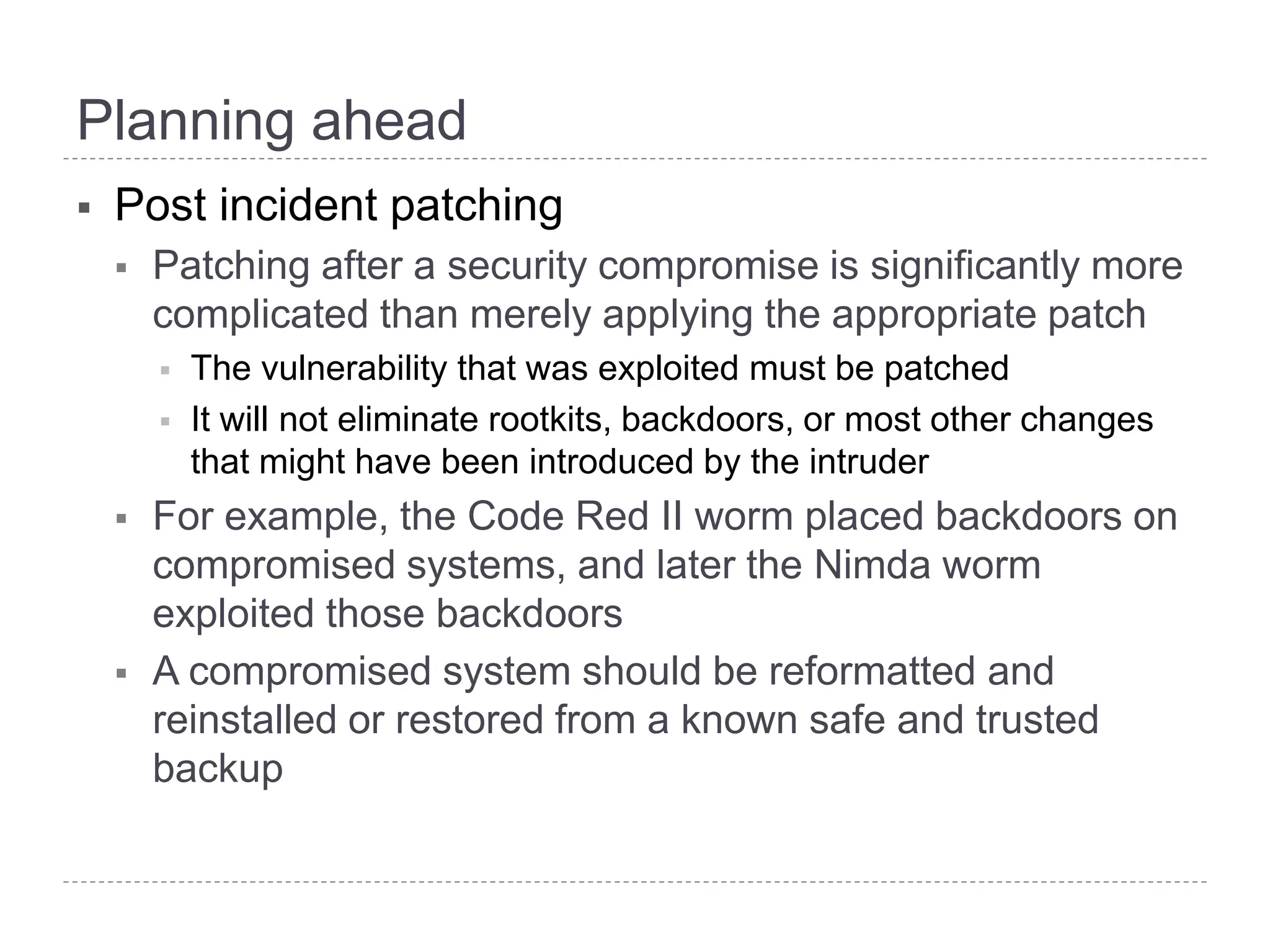
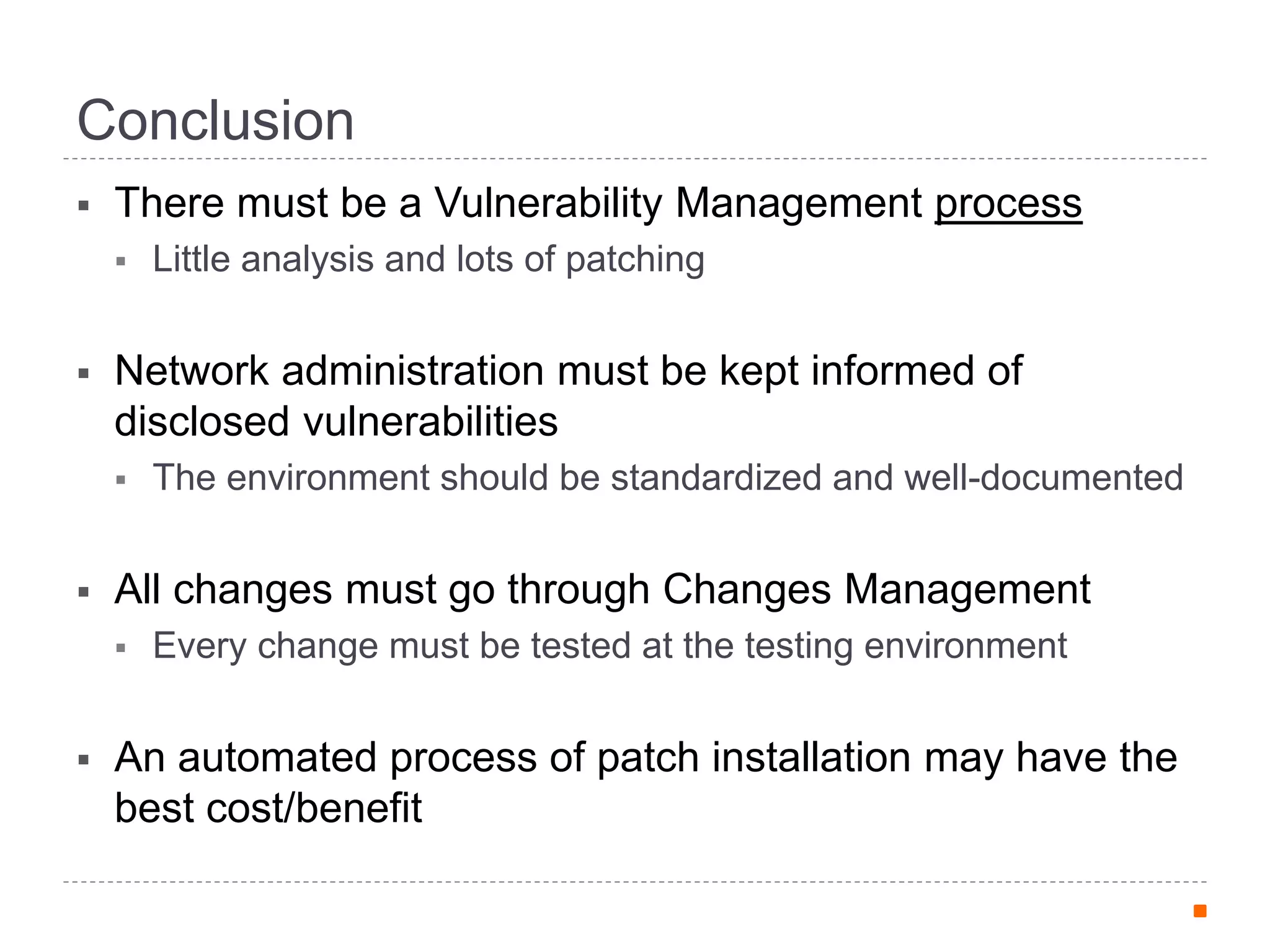
This document discusses patch and vulnerability management. It begins with an agenda that covers why patch management matters, its relationship to risk management and penetration testing, how to implement patch and vulnerability management, establish metrics, plan ahead, and draw conclusions. It then discusses key aspects of patch and vulnerability management including monitoring vulnerabilities, establishing priorities, managing knowledge of vulnerabilities and patches, testing patches, implementing patches, verifying implementation, and improving the process. The goal is to reduce risk by addressing vulnerabilities through a structured patch management program.