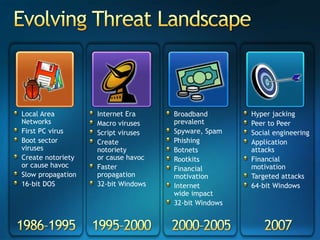
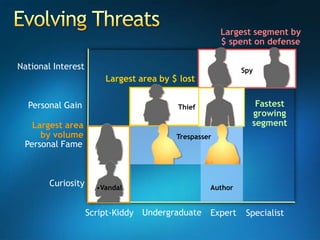
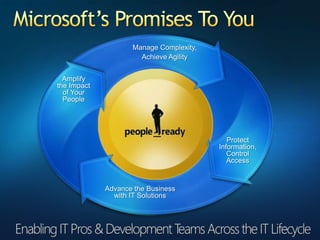
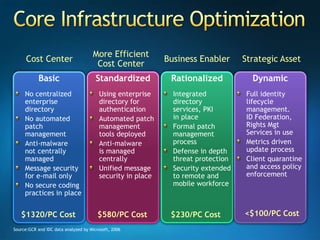
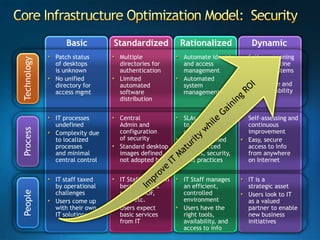
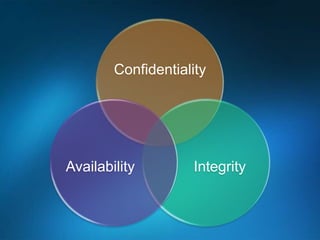
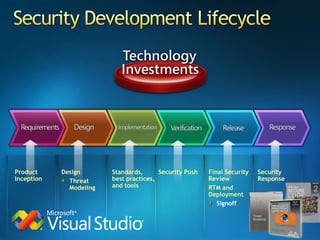
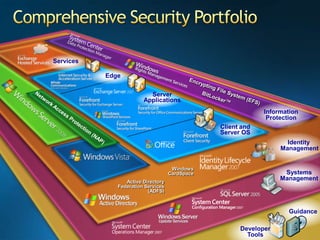
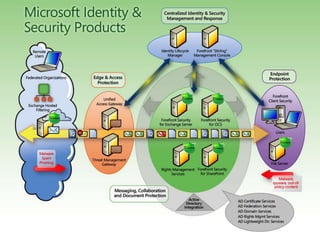
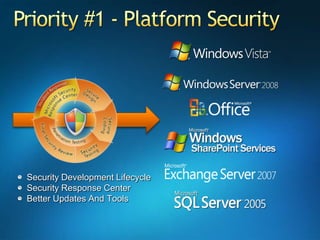
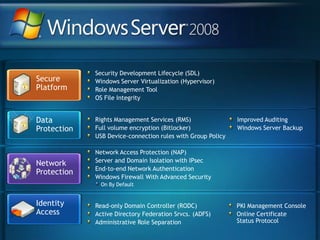
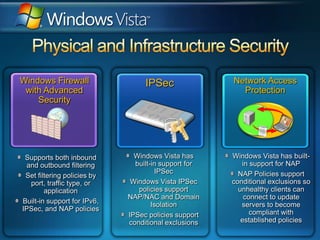
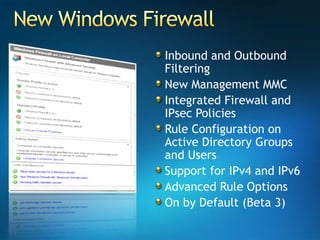
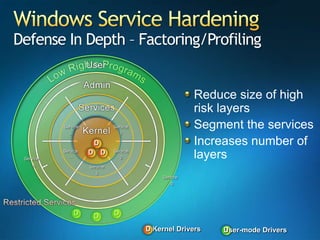
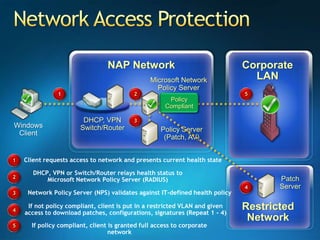
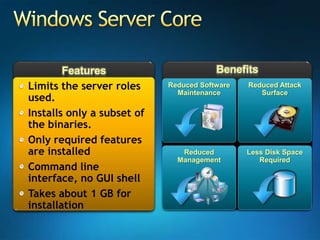
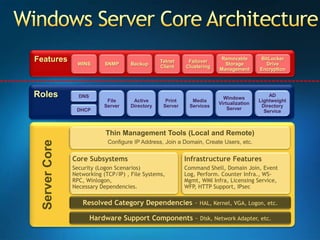
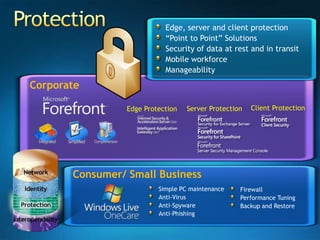
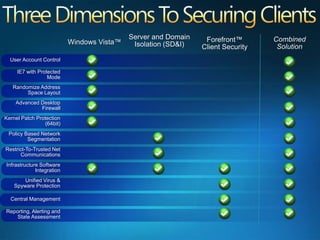
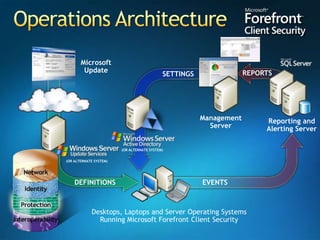
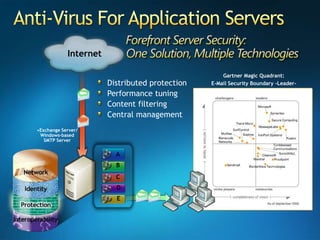
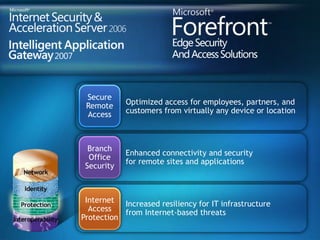
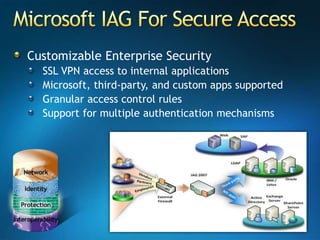
You are attending a workshop on security threats and how to address them, not a training. The presenters introduce themselves and their backgrounds. They discuss how security threats have evolved from viruses in the early internet era to today's more sophisticated targeted attacks. Microsoft's approach to security focuses on technology, processes, and people to manage complexity, protect information, and advance the business with IT solutions. Specific solutions discussed include Windows Firewall, BitLocker, and Network Access Protection.