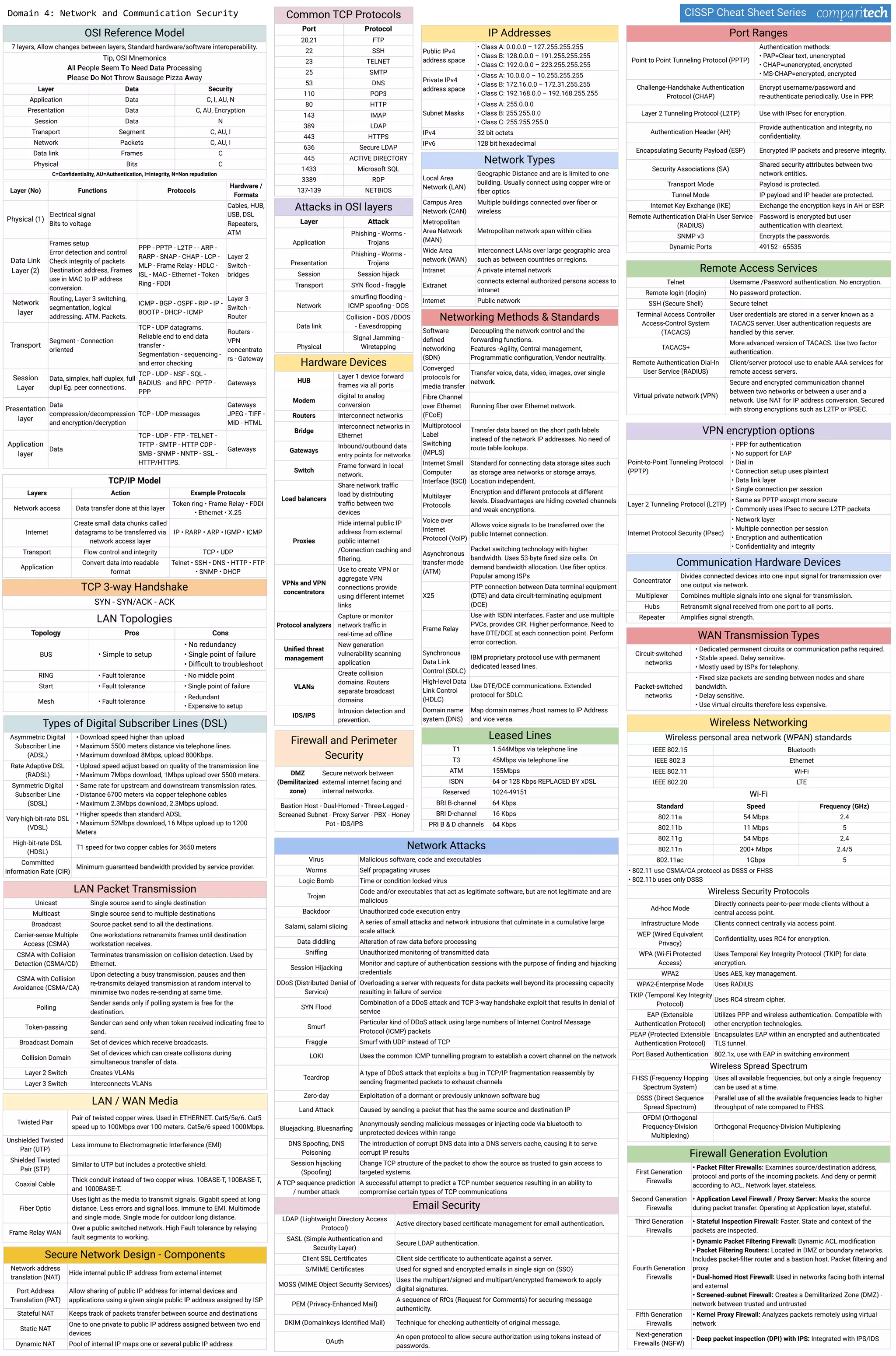
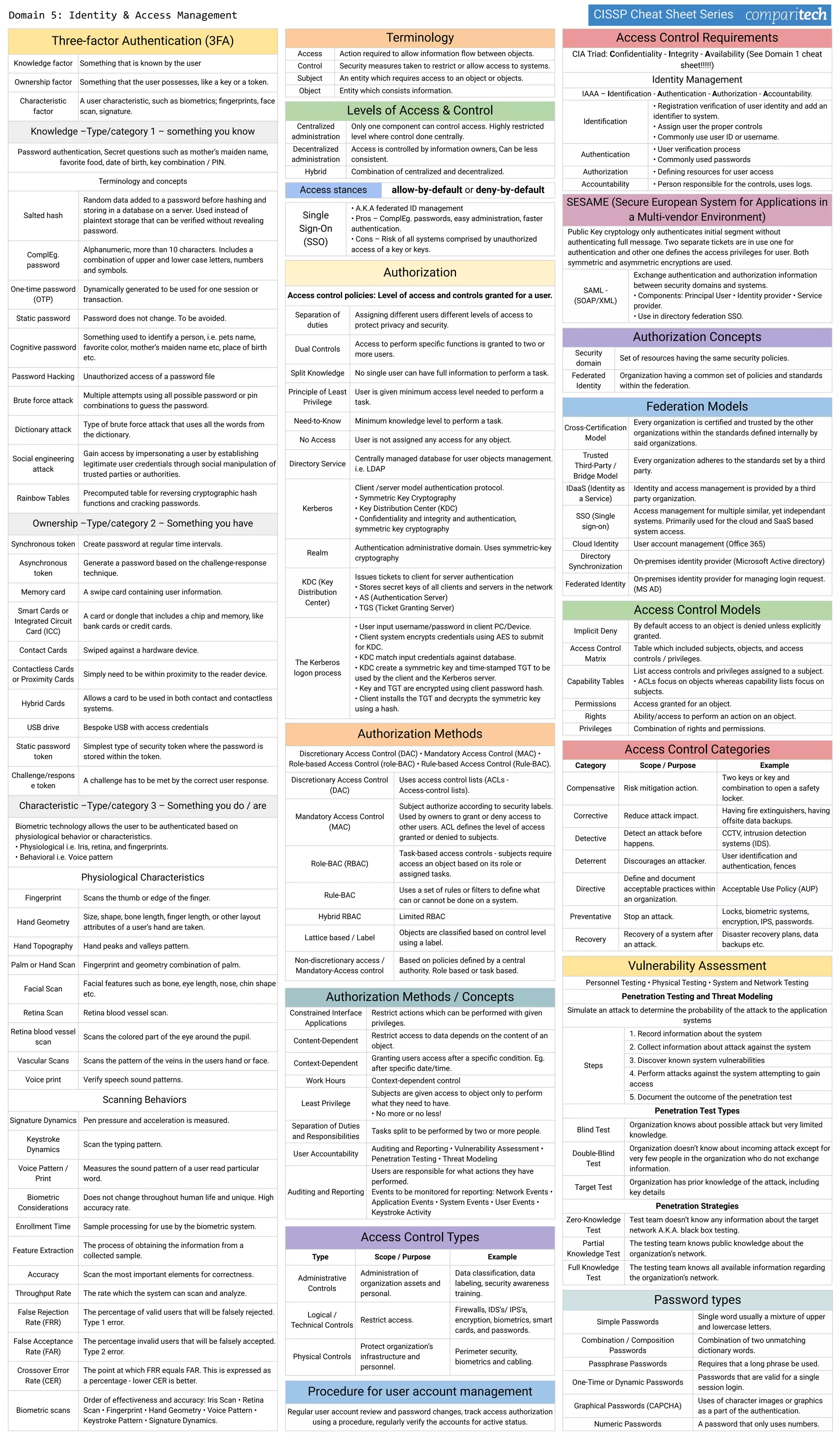
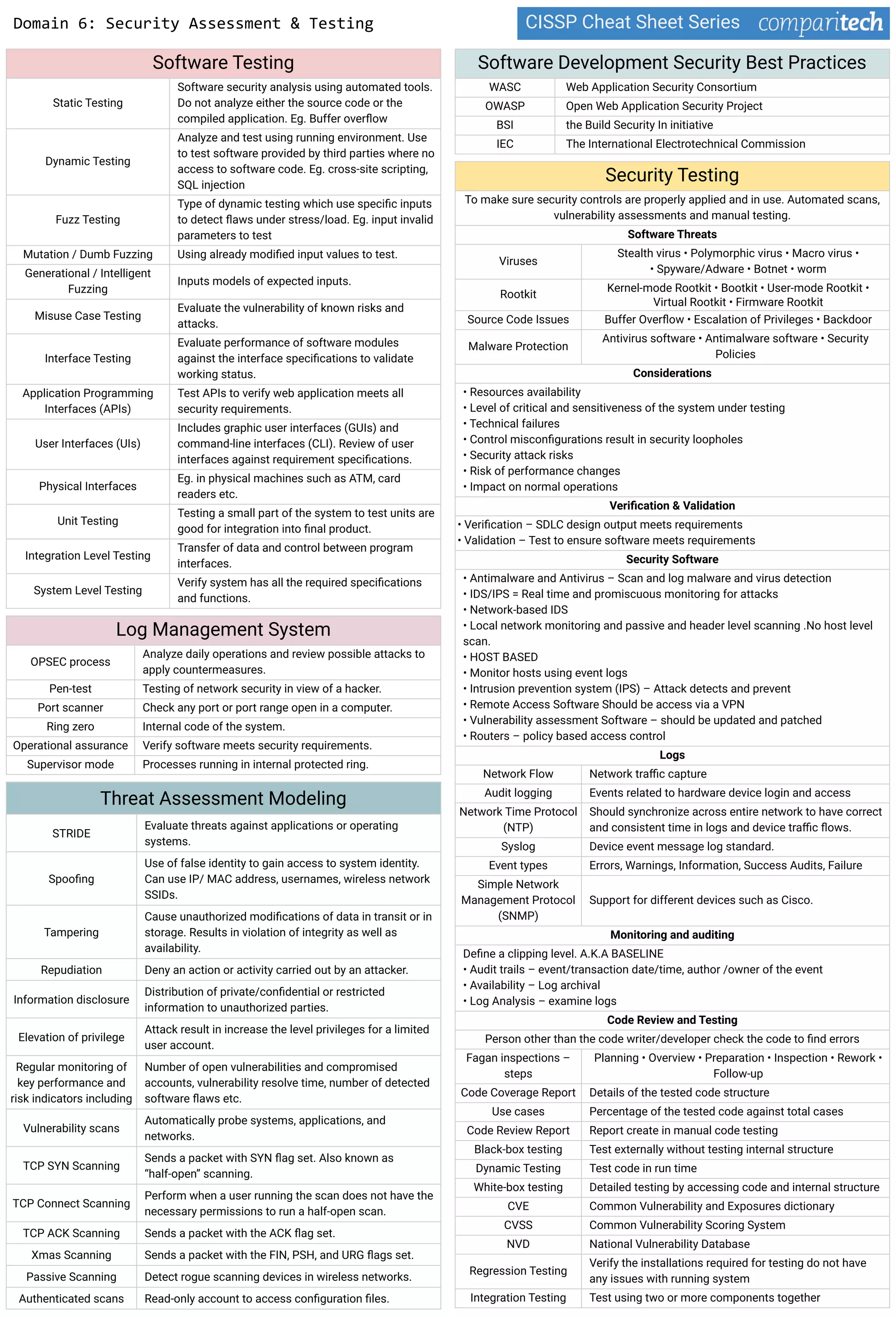
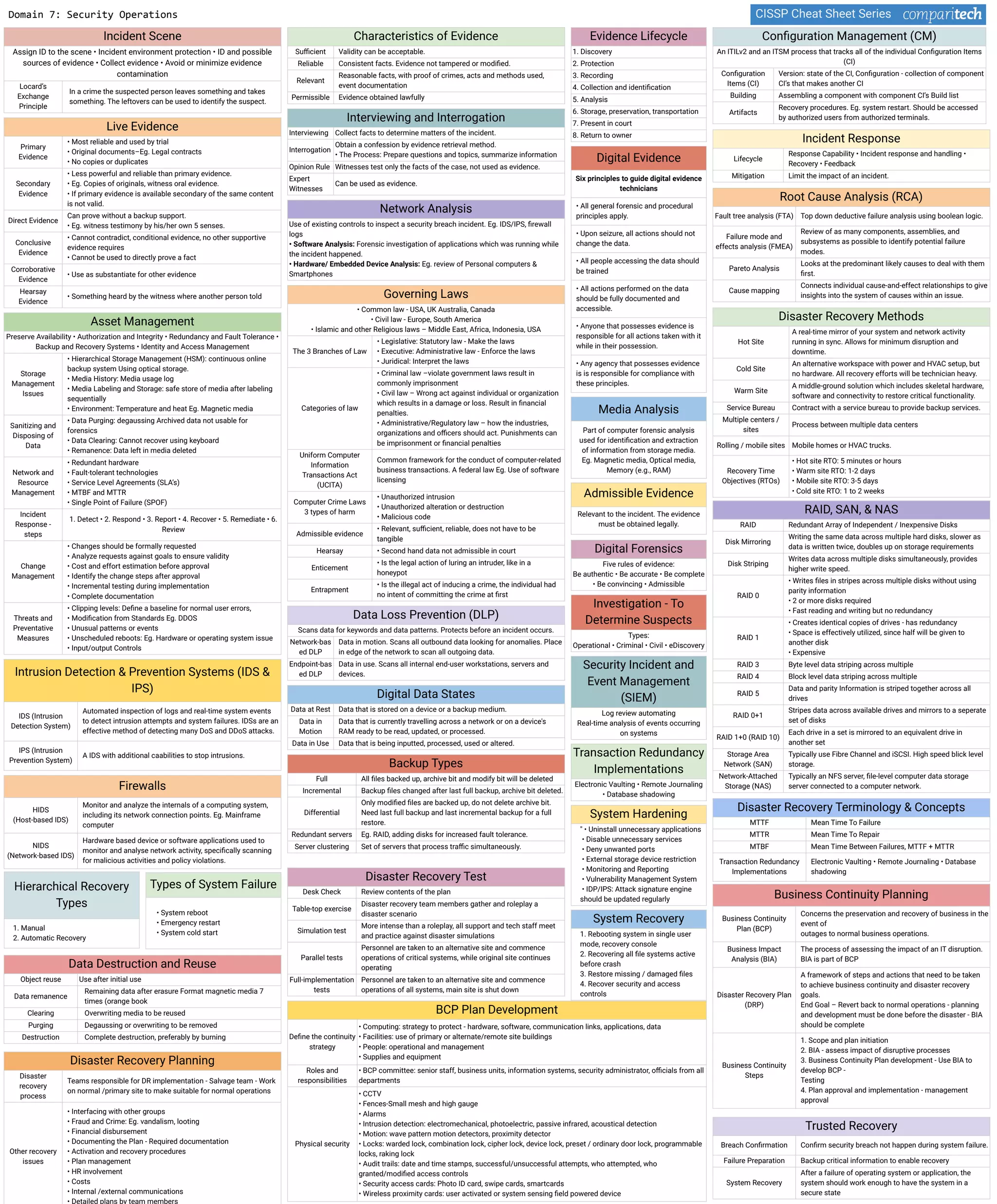
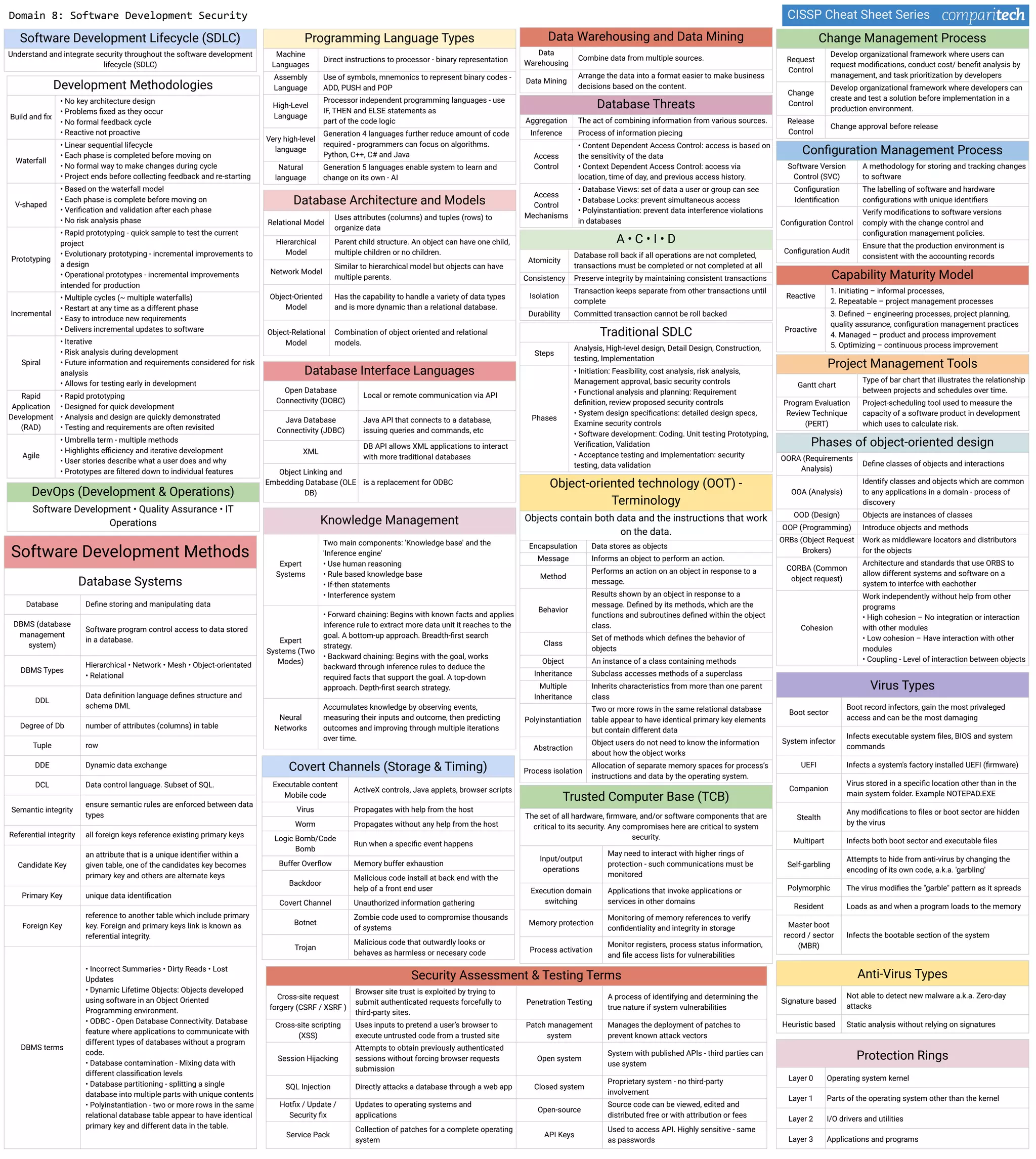
The document discusses several key concepts in information security including:
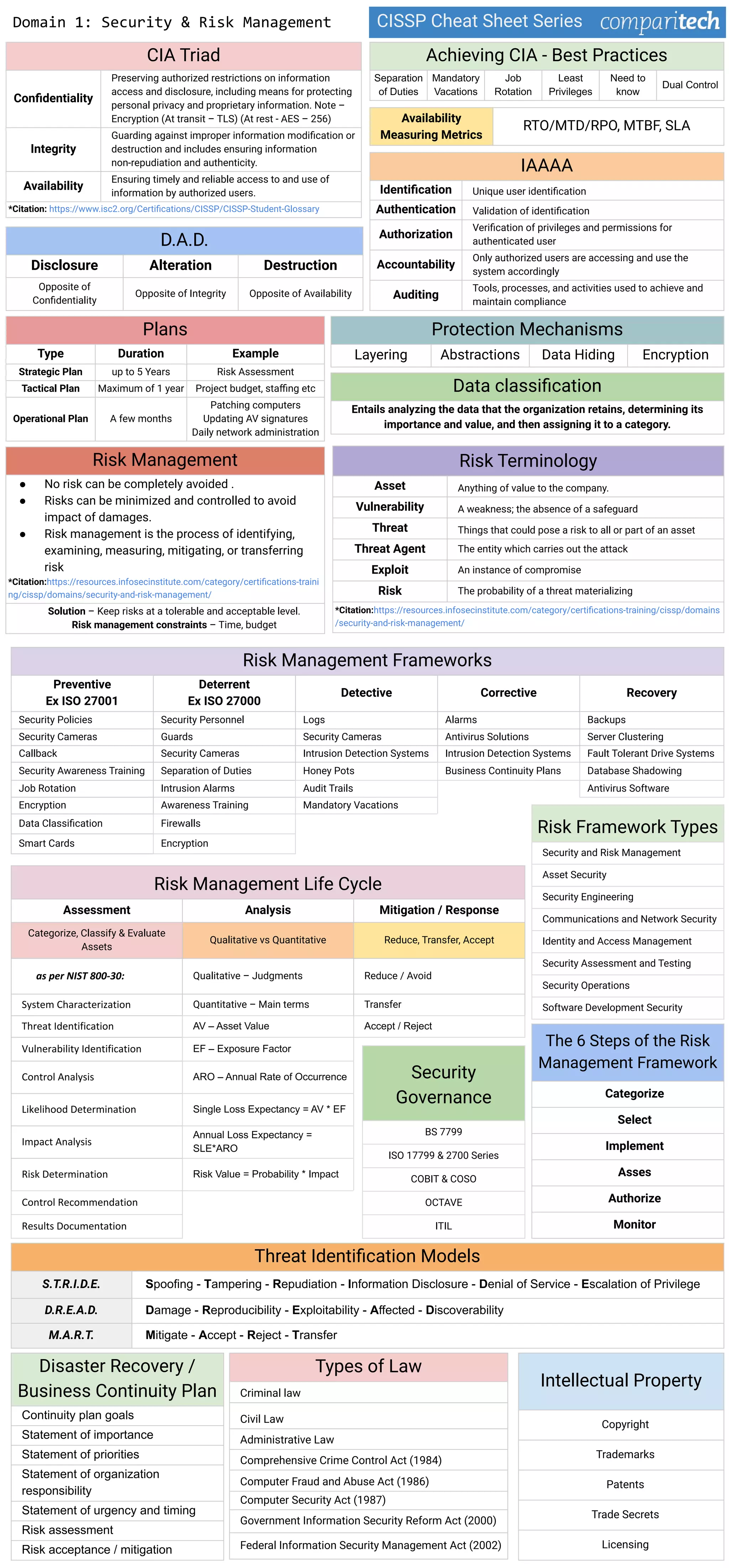
1. The CIA triad of information security - confidentiality, integrity, and availability. It provides definitions and examples of encryption techniques to achieve each.
2. Common risk management frameworks and methodologies like NIST, ISO 27000, and COBIT. It also outlines the six steps in the typical risk management framework.
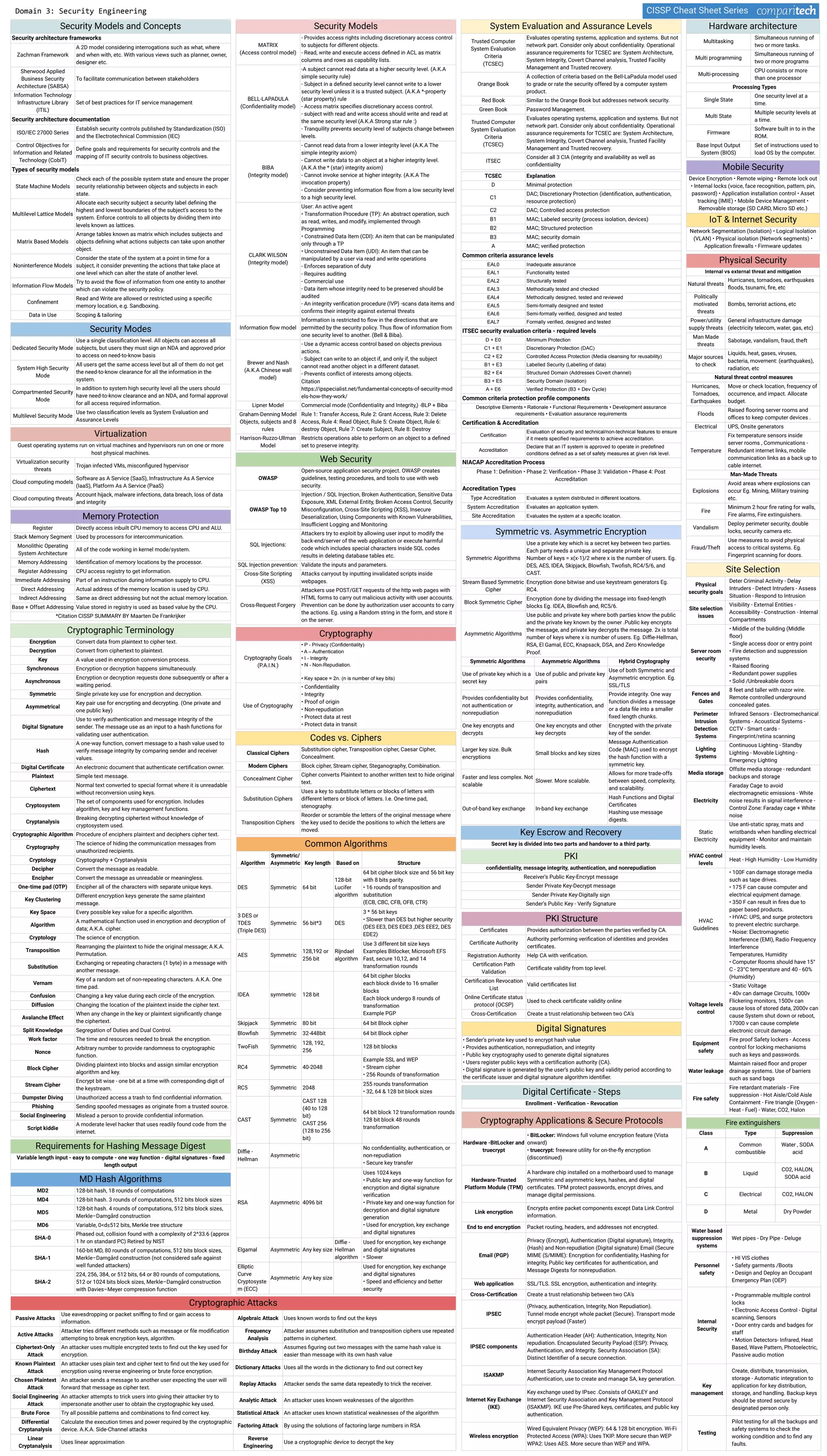
3. Several security models and concepts used in system and information security engineering like state machine models, multilevel lattice models, and information flow models.
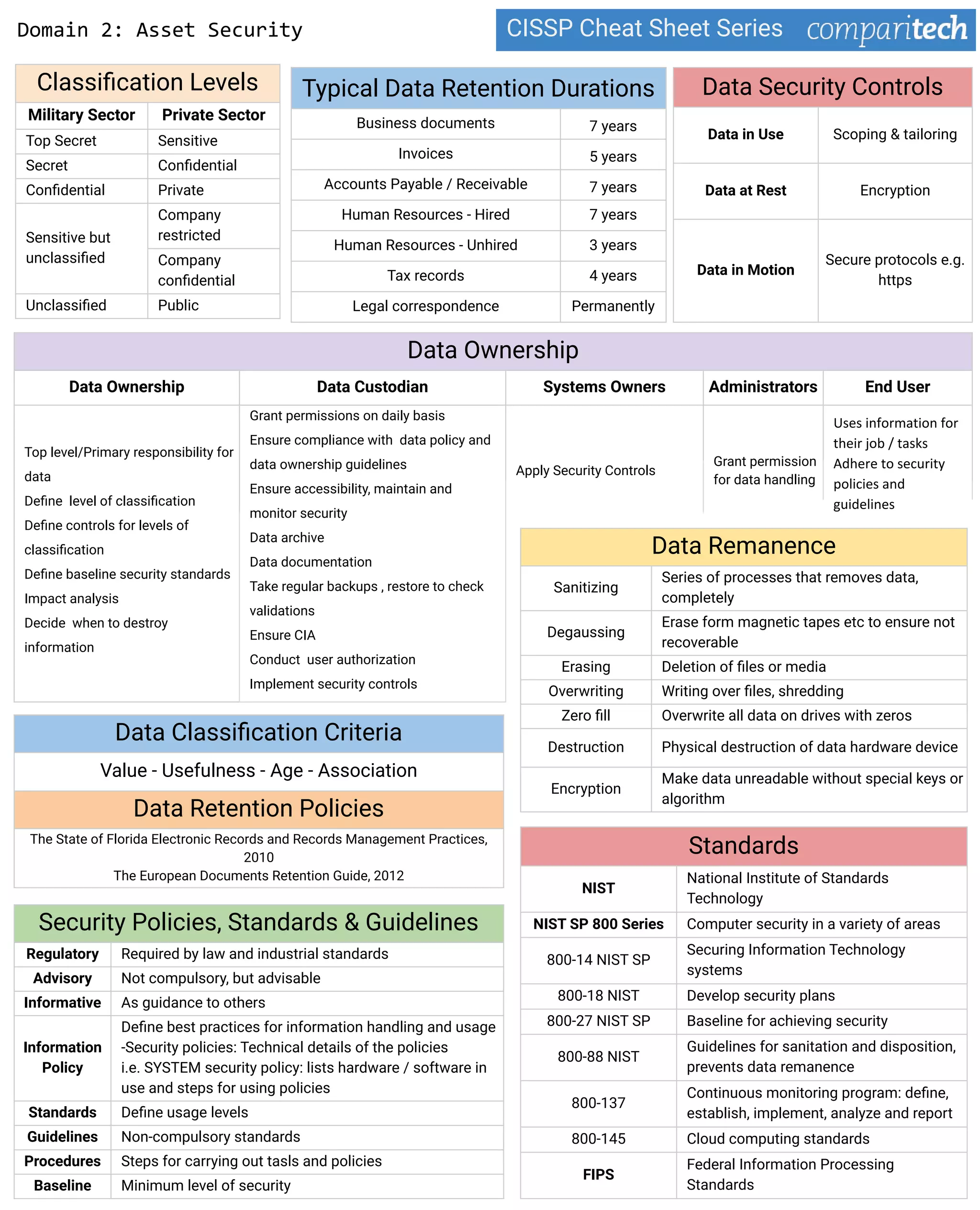
4. Data security controls and best practices for data classification, retention, and sanitization to preserve confidentiality. This includes policies, standards, and guidelines.