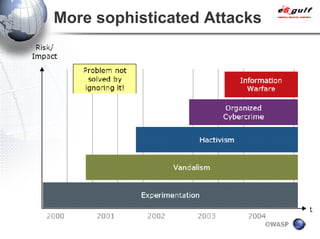
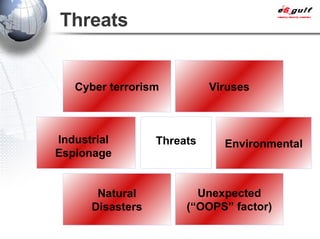
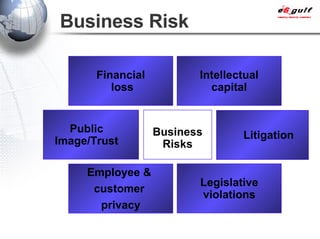
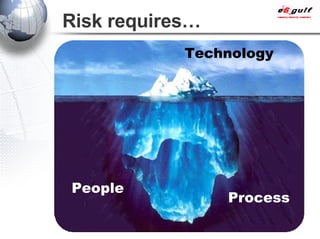
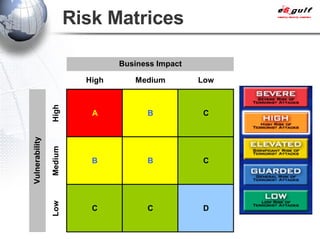
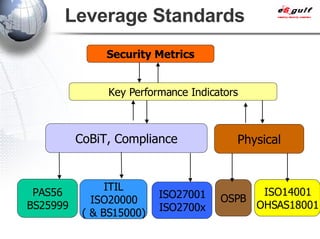
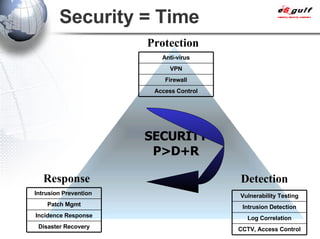
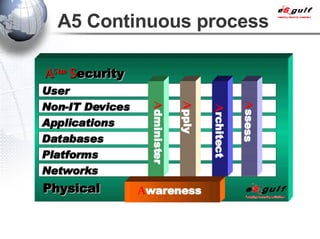
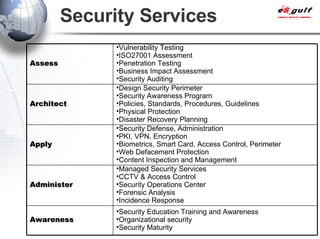
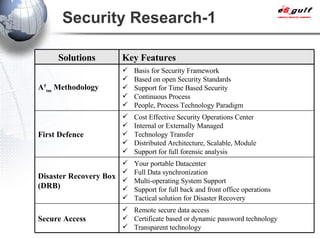
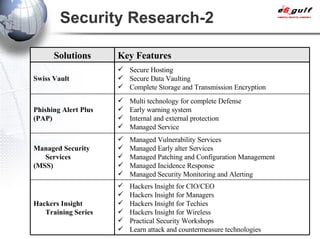
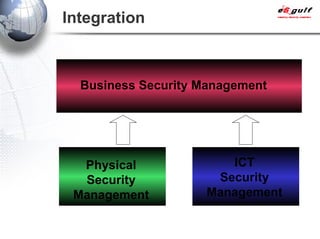
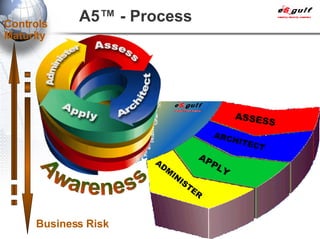
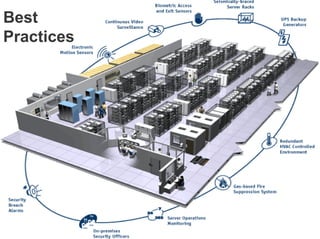
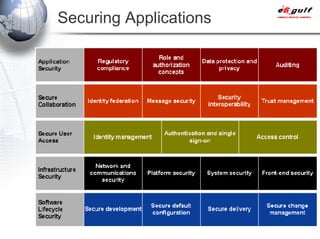
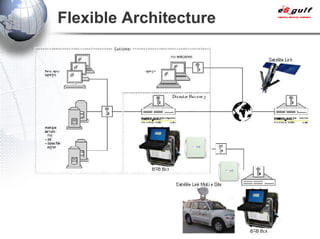
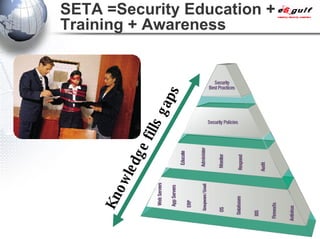
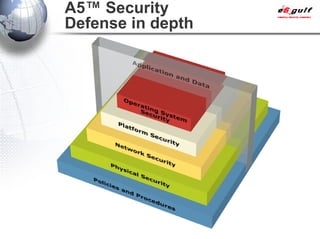
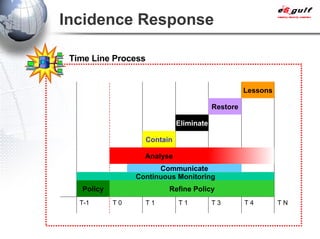
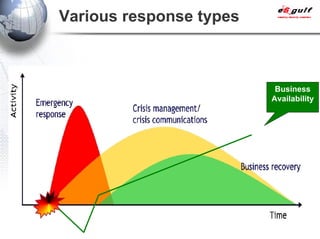
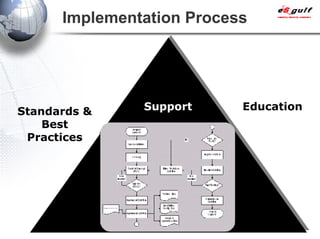
E-Security Gulf Group WLL offers comprehensive security solutions and services across various sectors including physical and cyber security, incident response, and risk management. The company utilizes a proprietary 5TM methodology focused on technology, processes, and people to address security challenges such as industrial espionage and cyber terrorism. Their integrated approach includes managed services, vulnerability assessments, and continuous monitoring, supported by industry best practices and standards.
![E-Security Gulf Group WLL Corporate Profile [email_address] www.esgulf.com http://4sec.blogspot.com/](https://image.slidesharecdn.com/esguf-profile-short-v34-1200592908363231-3/85/Esguf-Profile-Short-V34-1-320.jpg)