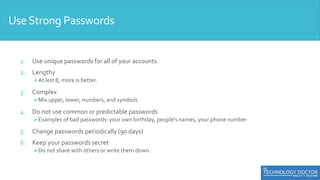
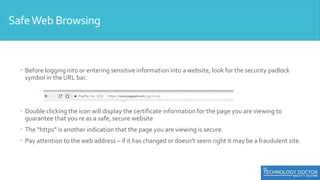
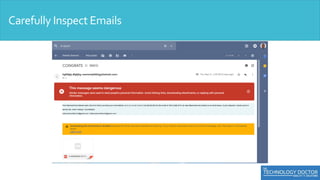
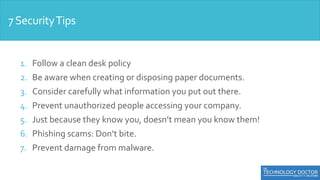
This document provides an overview of security awareness training. It discusses the importance of security awareness and outlines best practices for using strong passwords, safe web browsing, email security, mobile device security, physical security, and protecting against social engineering. Specific tips are provided in each area, such as using unique, complex passwords and changing them periodically; verifying website security before logging in; being wary of suspicious emails and not using personal email for work. The importance of physical access control, locking screens, and securing documents is also covered.