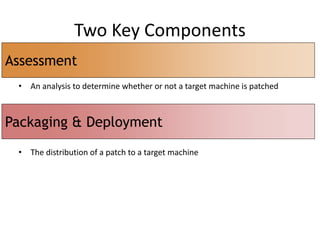
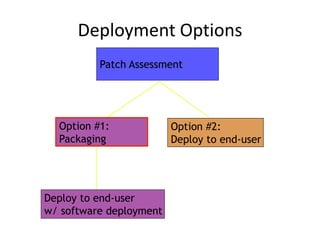
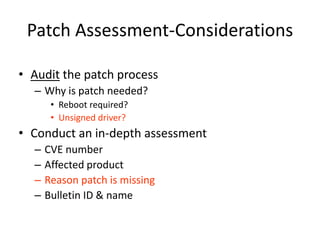
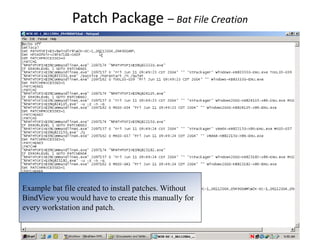
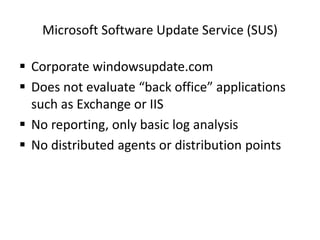
Vulnerability and patch management tools allow organizations to assess and remediate security vulnerabilities across their IT infrastructure. By automating vulnerability scans, patch deployment, and compliance reporting, these tools can help audit 100% of systems on a regular basis, speed remediation times, and reduce business risks and costs associated with security breaches. While native OS tools provide some patching and management capabilities, dedicated vulnerability and patch management solutions offer more comprehensive vulnerability assessments, centralized administration and reporting, and scalability needed for large enterprise environments.