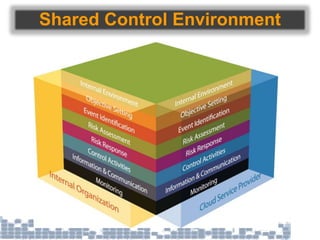
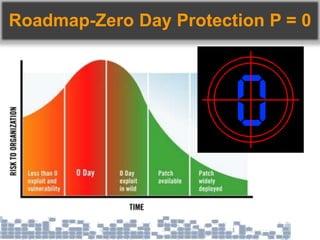
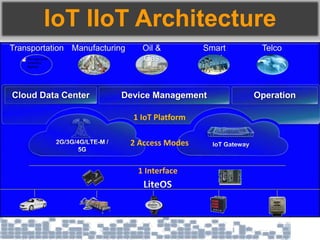
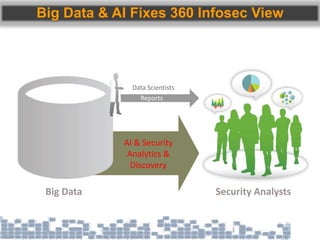
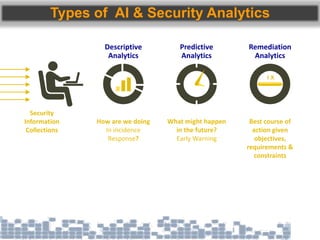
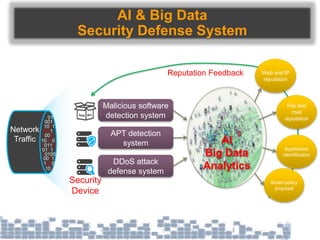
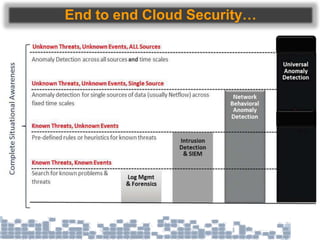
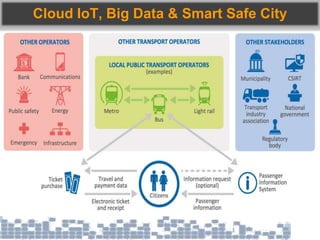
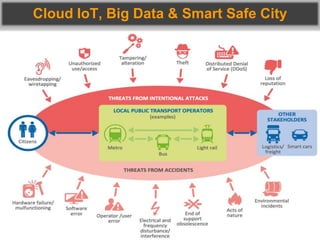
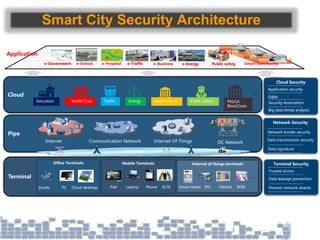
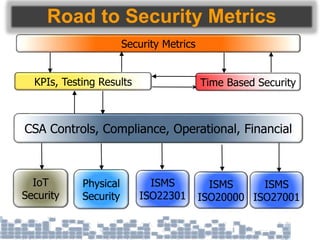
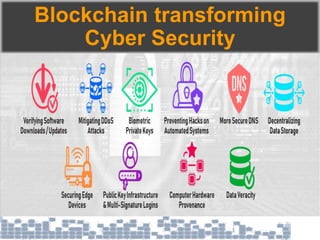
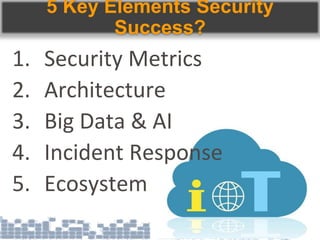
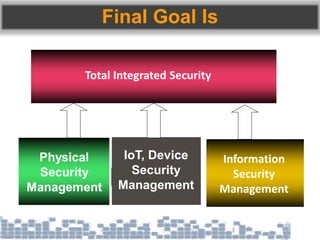
This document discusses cybersecurity threats in cloud and IoT environments and proposes approaches to address them. It notes that cloud and IoT security is different than traditional approaches due to shared environments, zero-day exploits, and outdated assumptions. Effective countermeasures require an integrated security approach leveraging big data, AI, blockchain, and metrics to provide comprehensive protection across physical, network, and cloud layers. The goal is a total, integrated security solution for modern, interconnected systems.